当前位置:网站首页>Si4432 RF chip scheme typical application of data transmission of wireless communication module of Internet of things
Si4432 RF chip scheme typical application of data transmission of wireless communication module of Internet of things
2022-06-11 22:55:00 【Chengdu yibaite Electronic Technology Co., Ltd】
Si4432 yes Silicon labs The company's RF chip , It is a highly integrated 、 low power consumption 、 Multi band EZRadioPRO Series wireless transceiver chip . Its working voltage is 1.9~3.6V, Can work in 315/433/868/915MHz Four bands ; Internal integrated diversity antenna 、 power amplifier 、 Wake up timer 、 Digital modem 、64 Byte sending and receiving data FIFO And configurable GPIO etc. .
Si4432 The chip requires very few external components in use , Only required 1 individual 30MHz The crystal of 、 Several capacitors and inductors can form a highly reliable transceiver system , Design simple , And the cost is low .Si4432 The receiving sensitivity reaches -117dB, It can provide excellent link quality , Minimize power consumption while expanding transmission range ; The minimum filter bandwidth is 8kHz, Excellent channel selectivity ; stay 240~960MHz In the frequency band , The maximum output power without power amplifier can reach +20dBm, When the design is good, the farthest distance between transmitter and receiver can reach 2km.
Si4432 Make it Wireless communication module Widely applied , It can be applied to wireless data communication 、 Wireless remote control system 、 Small wireless networks 、 Small wireless data terminal 、 Wireless meter reading 、 Access control system 、 Wireless remote sensing monitoring 、 Hydrometeorological monitoring 、 Robot control 、 wireless RS485/RS232 Data communication and many other fields .
At present, most intelligent access control systems are based on wired communication . as everyone knows , Wired communication has security 、 Good stability 、 Easy to implement, etc ; But at the same time, the wired communication mode has high initial installation cost 、 Construction time is long 、 Cannot move 、 Little room for change 、 Maintenance costs are high 、 Small coverage 、 Expansion difficulties and other defects . With the development of communication technology , Wireless communication network has entered a new world . Strong function 、 Easy to install 、 Flexible networking 、 Plug and play network connection 、 Strong mobility and other advantages , The wireless network provides unlimited applications . Therefore, the radio frequency access control system can not only improve the security and reliability , And compared with the traditional fitting mechanism , The radio frequency access control system has less wear and consumption , Long service life , It can effectively reduce the replacement of access control equipment , Of ebat E27-433M20S The module is small , Low power consumption , Under the current trend of advocating environmental protection and energy conservation , Undoubtedly of great significance .
The hardware of wireless access control system mainly includes main control equipment 、 Electric lock 、 Power Supply 、 Speech compression / Control platform 、 Wireless transmission platform , Other peripheral equipment consists of several parts , The overall architecture of the system is shown in the figure .
When the authorized user swipes the card to open the door , The card reader sends a certain frequency RF signal through the transmitting antenna , When the RF card enters the working area of the transmitting antenna, an induced current is generated , The RF card gets energy and is activated , The RF card sends its own coding and other information through the card's built-in transmission antenna , The system receiving antenna receives the modulated signal sent from the RF card , It is transmitted to the card reader through the antenna regulator , The card reader demodulates and decodes the received signal, and then sends it to the main control equipment for related processing ; The main control system judges the legitimacy of the card according to the logic operation , Make corresponding processing and control according to different settings , Send command signal to control the action of actuator , If the authorized user forgets to bring the card , You can also enter the password through the external keyboard of the system to open the door .

For authorized users, access control can be opened by swiping card or entering password , Unauthorized users can send entry requests to residents through the wireless voice system , You can enter the building with permission , When the system is invaded illegally , Be able to actively send an emergency alarm to the security center .
The system has the following advantages :
(1) Security , The system can prevent all unauthorized objects from entering , Ensure the safety of property and life .
(2) reliability , The system can work stably , It can better resist external interference , Ensure the accuracy of actions .
(3) The real time , The system can respond to user objects in real time .
(4) flexibility , The system can be easily extended , Easy to add new users .
(5) confidentiality , The system has strong anti - deciphering ability , Strong protection of user passwords .
边栏推荐
- H. 265 introduction to coding principles
- Bit operation in leetcode
- 【Day11-12 文献精读】On magnitudes in memory: An internal clock account of space-time interaction
- 【Uniapp 原生插件】商米钱箱插件
- FastAPI 5 - 常用请求及 postman、curl 使用(parameters,x-www-form-urlencoded, raw)
- Exercise 9-6 statistics of student scores by grade (20 points)
- 习题8-8 判断回文字符串 (20 分)
- Exercise 6-6 using a function to output an integer in reverse order (20 points)
- 【Day8 文献泛读】Space and Time in the Child‘s Mind: Evidence for a Cross-Dimensional Asymmetry
- 【Day1/5 文献精读】Speed Constancy or Only Slowness: What Drives the Kappa Effect
猜你喜欢

SDNU_ ACM_ ICPC_ 2022_ Weekly_ Practice_ 1st (supplementary question)

【Day13-14 文献精读】Cross-dimensional magnitude interactions arise from memory interference

【Day2 文献精读】Time in the mind: Using space to think about time
6. project launch
16 | 浮点数和定点数(下):深入理解浮点数到底有什么用?
Is the product stronger or weaker, and is the price unchanged or reduced? Talk about domestic BMW X5

The second bullet of in-depth dialogue with the container service ack distribution: how to build a hybrid cloud unified network plane with the help of hybridnet

遇到表格,手动翻页太麻烦?我教你写脚本,一页展示所有数据

The top ten trends of 2022 industrial Internet security was officially released

leetcode 中的位运算
随机推荐
【Day10 文献泛读】Temporal Cognition Can Affect Spatial Cognition More Than Vice Versa: The Effect of ...
Submit task to thread pool
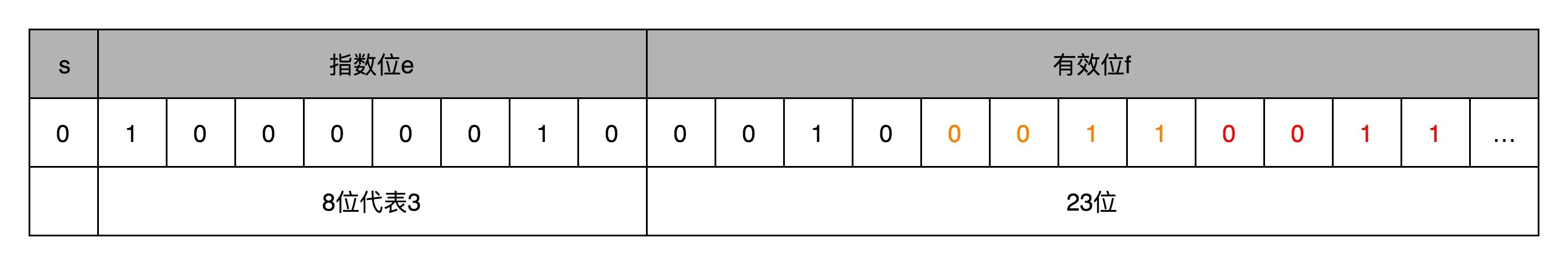
16 | floating point numbers and fixed-point numbers (Part 2): what is the use of a deep understanding of floating-point numbers?
R7-1 列表或元组的数字元素求和
C# List. Can foreach temporarily / at any time terminate a loop?
阿里云服务器mysql远程连接一直连不上
分类统计字符个数 (15 分)
How to do investment analysis in the real estate industry? This article tells you
Point cloud read / write (2): read / write TXT point cloud (space separated | comma separated)
消息队列存储消息数据的 MySQL表
Exercise 9-6 statistics of student scores by grade (20 points)
leetcode 中的位运算
电脑强制关机 oracle登录不上
习题9-1 时间换算 (15 分)
IEEE754标准中的4种舍入模式
【Day1/5 文献精读】Speed Constancy or Only Slowness: What Drives the Kappa Effect
Gcache of goframe memory cache
Lecture de l'article dense Visual SLAM for RGB - D Cameras
Google搜索为什么不能无限分页?
Brief introduction to integrity