当前位置:网站首页>Network foundation (1)
Network foundation (1)
2022-07-07 11:06:00 【Exy-】
Catalog
6. Network communication protocol
8. The transport layer TCP And UDP agreement
One . Network development background
1. Switch :
According to the record of the connected computer mac( Physical network card address ), Data exchange .
shortcoming : It is impossible to send to which host you want .
2. Router
A function is added to the technology of data exchange --- Network identification , For every piece of data in the network , Choose a suitable path , Send to the target host , It has realized the function of sending it to whoever you want , The router will recognize the network choice of the destination host sent to .( Path selection , Data forwarding )
3. Division of network
LAN ( The coverage is 1000m)
Metropolitan area network ( The coverage is 20km)
Wide area network ( Greater than 20km)
The Internet we usually use / The Internet belongs to a larger international wide area network , It is a complex star network , More disaster tolerant .
Ethernet / Token ring network is a networking method
4.IP Address
uint32_t --- Unsigned 4 Byte integer
As the unique identification of the host in the network --- Location between hosts in the network ( Which host communicates with which host )-- adopt IP Address identification
Every data in the network will contain Source side IP Address / To the end IP Address
ipv4: uint32_t( Less than 43 Billion , It's not enough ) ipv6:uint8_t addr[16]-- The promotion degree is very low
DHCP: Dynamic address assignment -> Who surf the Internet to whom IP Address NAT: stay DHCP after , There are still many people , Let many people use the same IP Address to surf the Internet
5. Port number
uint16_t Unsigned 2 An integer of bytes
Uniquely identify a process on a host , When writing communication programs , You have to tell the computer , Which port should I handle the data sent to
A port can only be occupied by one process , However, a process can use multiple ports
Every piece of data in network communication contains --- Source port and peer port --- It means which process this data is sent from , Which process should be handed over to handle
6. Network communication protocol
Data format convention in network communication
Follow the unified communication protocol standard , To achieve substantial communication , Realize network interconnection .
There are many communication protocols in the whole network communication environment --- Each protocol deals with different communication scenarios
Protocol layer : According to different communication scenarios , The services are different , The protocols used are divided into different levels
Typical protocol layering :
OSI Seven layer reference model : application layer / The presentation layer / The session layer / Transport layer / The network layer / The link layer / The physical layer
TCP/IP Five layer model : application layer / Transport layer / The network layer / The link layer / The physical layer
application layer : Responsible for how to communicate between applications ;HTTP/FTP/DNS/DHCP......
Transport layer : Responsible for data transmission between processes ;TCP/UDP
The network layer : Responsible for address management and routing ;IP; Router
The link layer : Responsible for data transmission between adjacent devices ; Ethernet protocol ; Switch
The physical layer : Responsible for the transmission of physical photoelectric signals ; Ethernet protocol ; A hub
7. Network byte order
Byte order :cpu The access order of data in bytes in memory
Host byte order : The size of a host byte order depends on cpu framework
Byte order is divided into big end byte order and small end byte order ; Big endian byte order : The low address stores the high address ; Small endian byte order : The low address stores the low address
The communication between hosts with different host byte order is easy to cause data ambiguity , Byte order standard in network communication ( Convert the byte order of your own data into standard byte order before transmission ) To avoid data ambiguity caused by different byte order
8. The transport layer TCP And UDP agreement
TCP--- Transmission control protocol --- Connection oriented , Reliable transmission , Byte stream oriented
UDP-- User datagram protocol --- There is no connection , unreliable , For datagram
difference :TCP Ensure reliable transmission , But the transmission speed is not UDP fast ;
TCP Applied to high security scenarios ,UDP Applied to scenes with high real-time requirements
边栏推荐
- 中级网络工程师是什么?主要是考什么,有什么用?
- 【安装系统】U盘安装系统教程,使用UltraISO制作U盘启动盘
- What are the test preparation materials and methods for soft exam information processing technicians?
- 深入理解Apache Hudi异步索引机制
- When do you usually get grades in the soft exam? Online pedaling?
- Still cannot find RPC dispatcher table failed to connect in virtual KD
- [untitled]
- Bookmarking - common website navigation for programmers
- 【OneNote】无法连接到网络,无法同步问题
- 2022.7.6DAY598
猜你喜欢
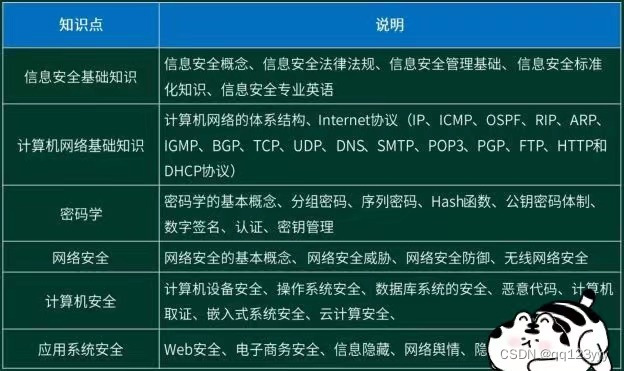
I plan to take part in security work. How about information security engineers and how to prepare for the soft exam?
![[untitled]](/img/15/3db921703147afdf58dfffe532a19b.jpg)
[untitled]
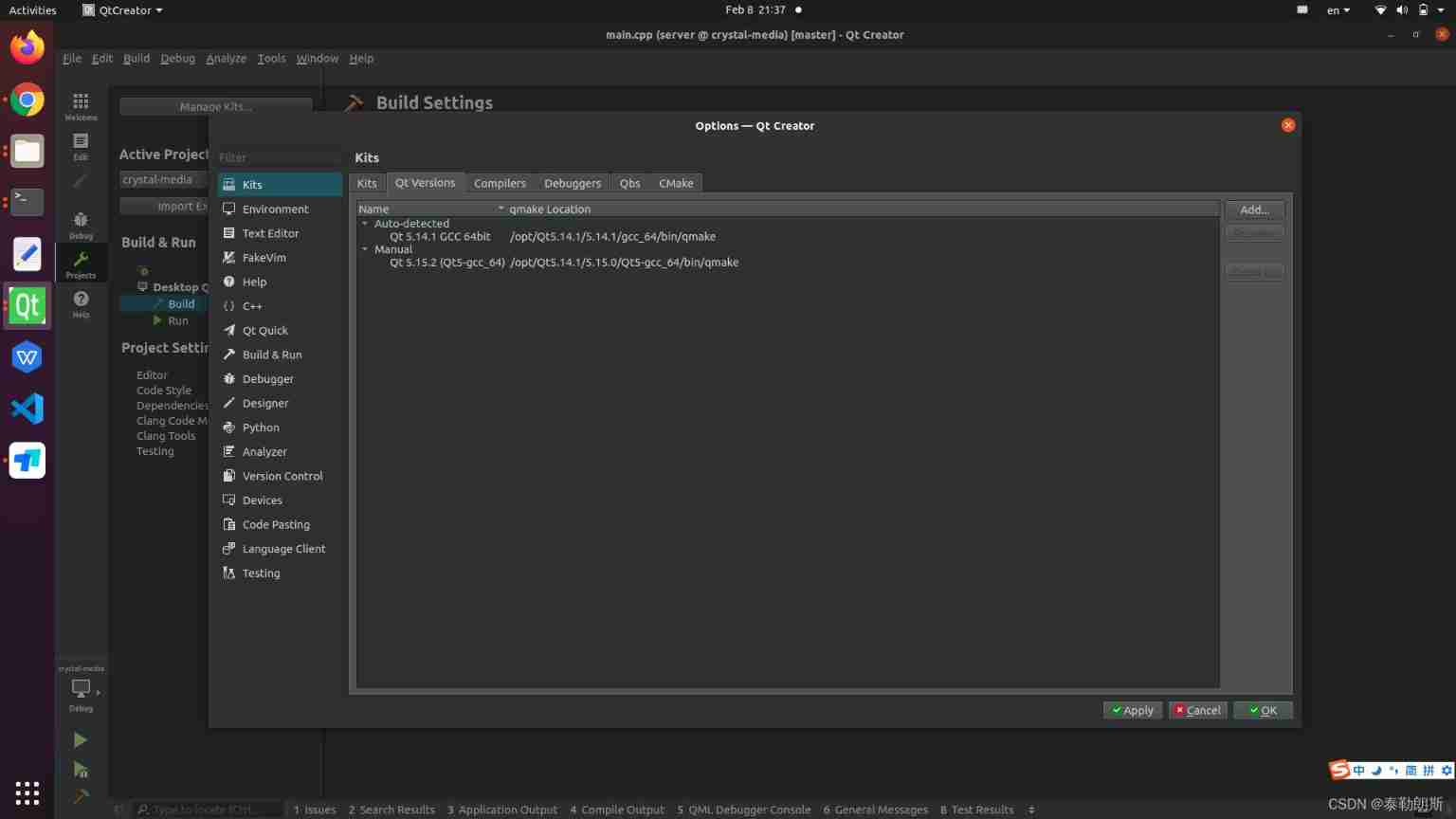
Qtcreator sets multiple qmake
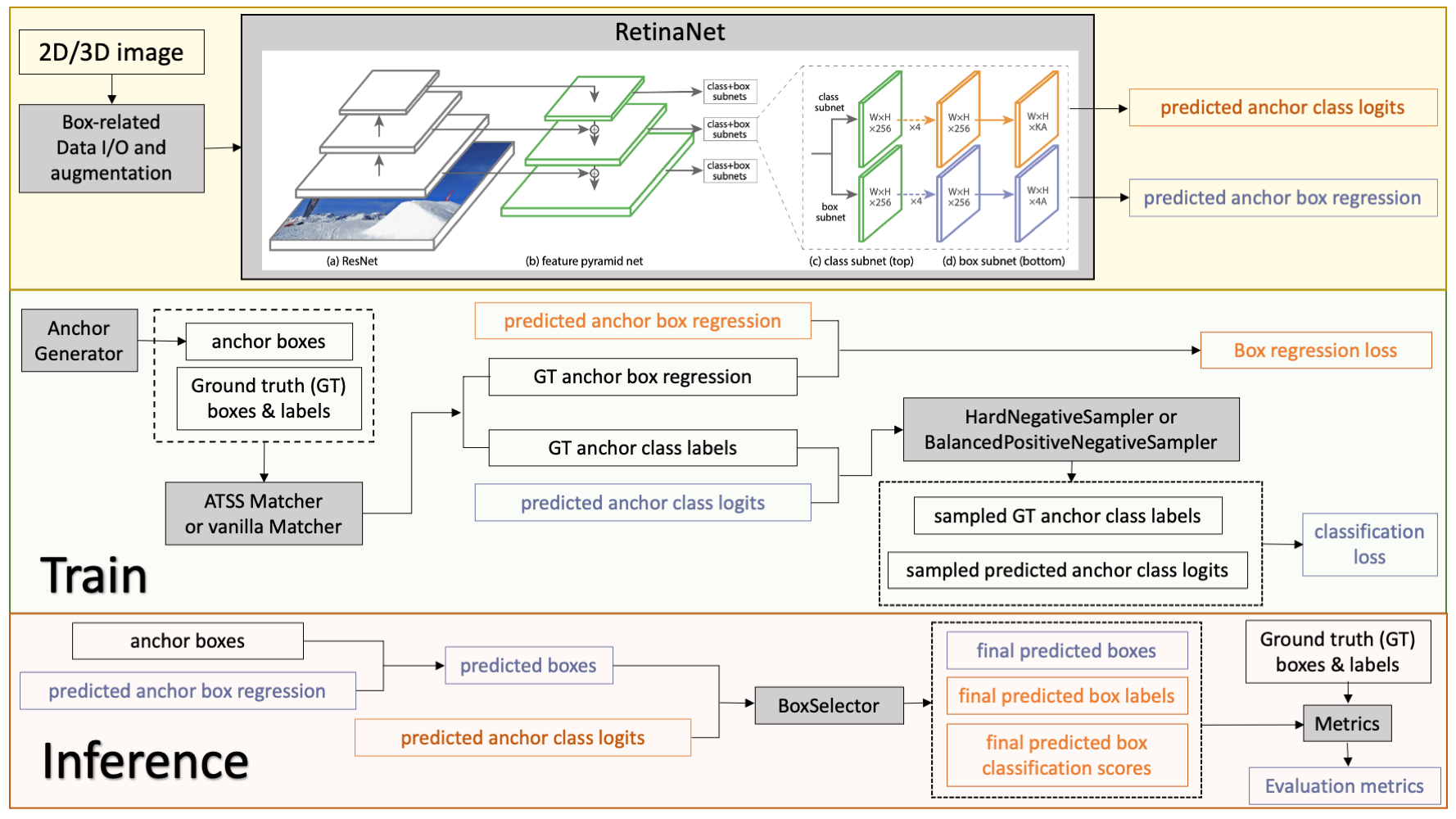
Monai version has been updated to 0.9. See what new functions it has
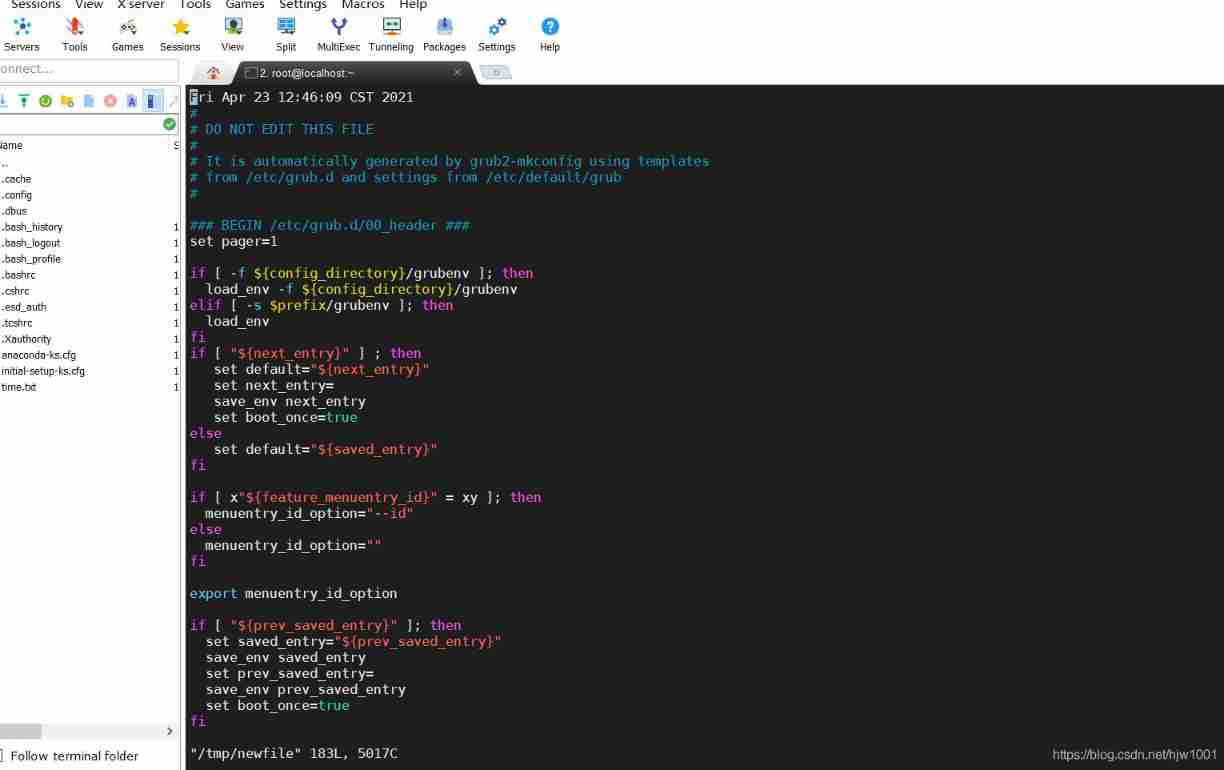
2021-04-23
![[recommendation system 02] deepfm, youtubednn, DSSM, MMOE](/img/d5/33765983e6b98235ca085f503a1272.png)
[recommendation system 02] deepfm, youtubednn, DSSM, MMOE
VR development optimization
![[untitled]](/img/c7/b6abe0e13e669278aea0113ca694e0.jpg)
[untitled]
SQL Server knowledge gathering 9: modifying data
![1324: [example 6.6] integer interval](/img/5d/29db4d51ec7a2685f8aeffe5be68da.png)
1324: [example 6.6] integer interval
随机推荐
[untitled]
uniapp 在onLaunch中跳转页面后,点击事件失效解决方法
The seventh training assignment
Arduino receives and sends strings
书签整理-程序员常用网站导航
1324: [example 6.6] integer interval
seata 1.3.0 四種模式解决分布式事務(AT、TCC、SAGA、XA)
Is the soft test intermediate useful??
Deeply understand the characteristics of database transaction isolation
TypeScript 接口继承
Records on the use of easyflash v3.3
Find the root of equation ax^2+bx+c=0 (C language)
Using tansformer to segment three-dimensional abdominal multiple organs -- actual battle of unetr
The fifth training assignment
2021-04-23
Wallhaven壁纸桌面版
[pro test feasible] error while loading shared libraries solution
变量的解构赋值
China Southern Airlines pa3.1
Cluster task scheduling system lsf/sge/slurm/pbs based on HPC scenario