当前位置:网站首页>Remote upgrade afraid of cutting beard? Explain FOTA safety upgrade in detail
Remote upgrade afraid of cutting beard? Explain FOTA safety upgrade in detail
2022-07-05 05:19:00 【Sauce sauce】
01 OTA Technology is introduced
The Internet of things OTA Upgrade technology refers to various IOT terminals downloading upgrade packages on remote servers through the network , And complete the upgrading of IOT terminal system or application software to the new version of end cloud integration technology . Overall speaking OTA The technical system includes software version management 、 Task release management 、 Connect the download pipeline 、 End to side upgrade capability 、 Ensure safety and stability and upgrade interactive experience .
The system has OTA Upgrade capability , It can help customers speed up the product launch in the process of project progress , It is convenient to repair functional defects and optimize product performance after product release , New functions can also be imported in time during subsequent maintenance , Enhance the product experience , Reduce operation and maintenance costs while improving after-sales efficiency .
about OTA For remote upgrade , On the basis of ensuring the success rate of upgrading , The most important thing is to ensure the security of the upgrade ,OneOS OTA The upgrade ensures the integrity of the firmware and the non repudiation of the sender by means of digital signature . below Let's learn more about it !
OTA From the upgrade target classification can be divided into FOTA and SOTA.FOTA Firmware upgrade , Upgrade the main program firmware , Generally, you need to restart the system to enter Bootloader Re write the application firmware to APP Partition .SOTA Upgrade for app , It mainly upgrades software applications running on the operating system , Need the support of software architecture and operating system , The upgrade process does not require system restart . The main analysis of this paper OneOS FOTA Security upgrade capability .
02 OneOS FOTA Design framework
OneOS Security FOTA The design framework is as follows chart 1 Shown , Design includes development platform 、FOTA Cloud platform 、 Dense pipe system 、 File servers and terminals equipment Five modules .
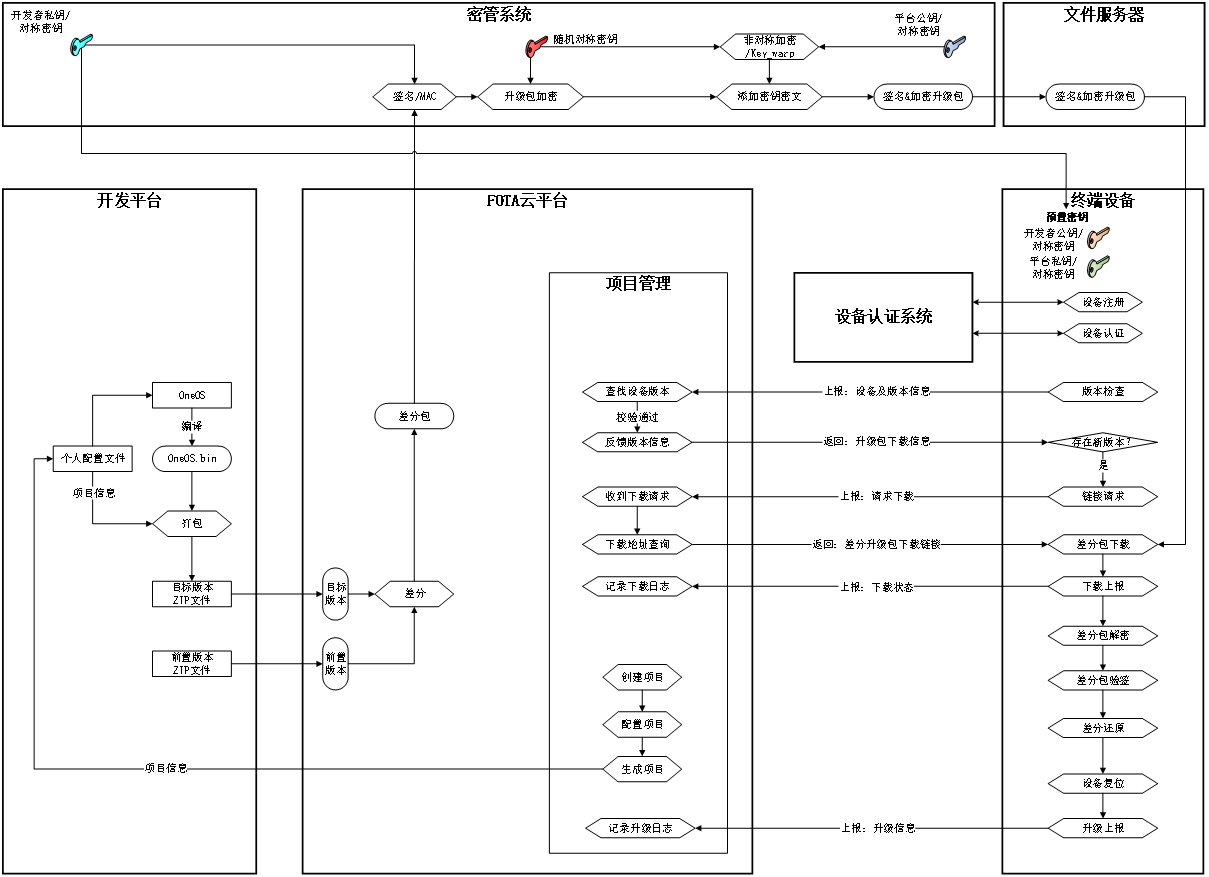
chart 1 FOTA2.0 Design frame
03 OneOS FOTA Details of upgrade steps
Step1 Firmware development
The user is in FOTA Platform creation and upgrade project , adopt menuconfig Write platform project information into the project , Bind the relationship between firmware and project through compilation .
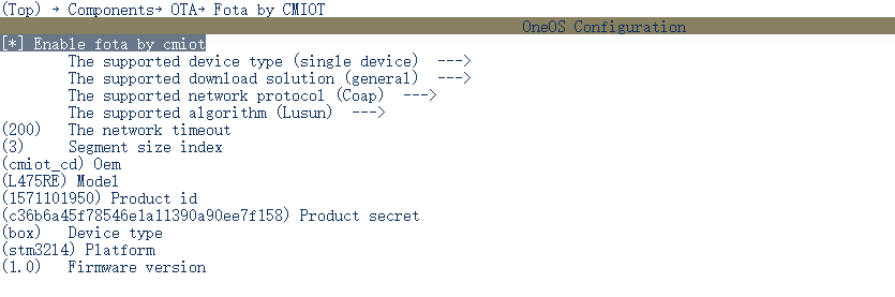
chart 2 Write project information
After compiling , Generate projects by packaging instructions info file , take bin Document and info File packaging output target version ZIP file , Such as chart 3 Shown , Firmware packaging instructions such as chart 4 Shown ( The address of the packaging software is modified according to the actual situation ).
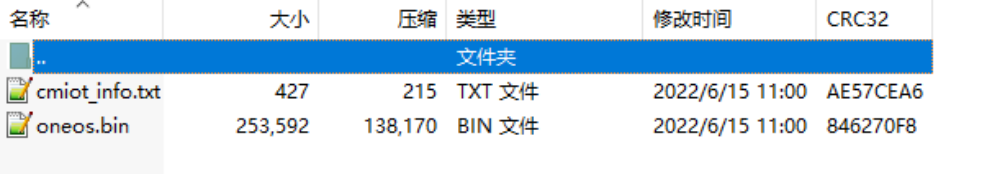
chart 3 ZIP The contents of the document
chart 4 Firmware packaging
Step2 Safety reinforcement
FOTA The platform makes a difference between the pre version and the target version firmware , Get differential firmware , Upload the differential firmware to the dense tube system , Call the developer's private key to sign the differential firmware , Get its signature value Signature; Then use the random symmetric key to encrypt the differential firmware , Get the ciphertext of differential firmware Palyload; Finally, the random symmetric key is encrypted with the symmetric key , Get the ciphertext of the random symmetric key EncKey.
Step3 Security protocols
In obtaining Signature、EncKey、Palyload in the future , Package , Ciphertext for differential firmware Palyload Add protocol header .Header contain General area、Secure area and Padding In the third part of .
General area from Header magic、 Load size Palyload size、 Safety count Sec_cnt( Anti rollback )、 Protocol header size Header size( instructions Header area size )、 Signature algorithm sign_alg( Indicates the differential firmware Signature Algorithm )、 encryption algorithm enc_alg form ( Indicates the algorithm for encrypting differential firmware ).
Secure area from Signature( Signature value ) and EncKey( Symmetric key ciphertext ) Two parts . Finally, for fill alignment Padding part ,32 Byte alignment .
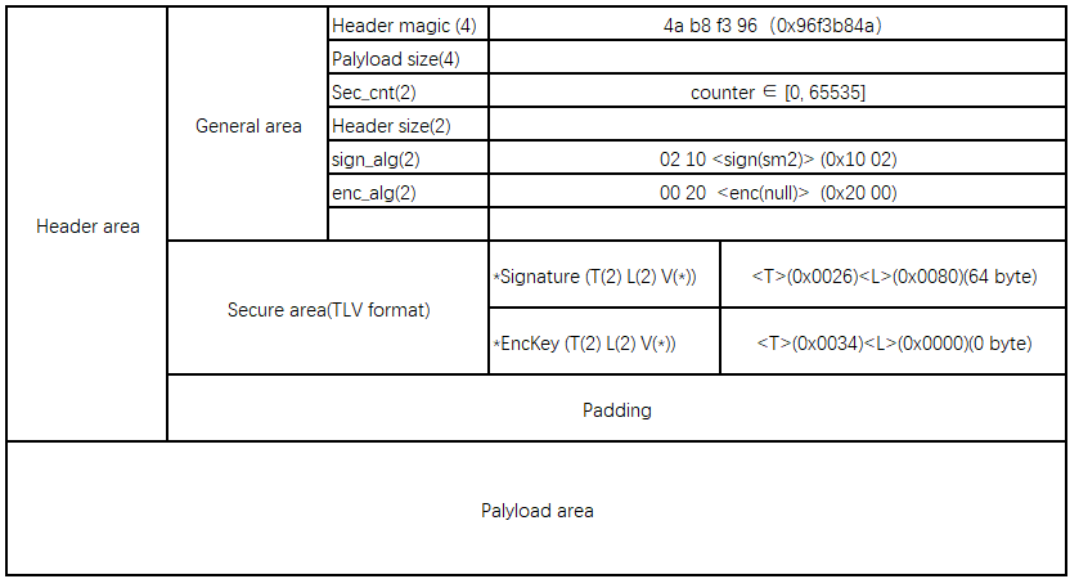
chart 5 Firmware header Protocol
After being packaged and tested, it can be published to the file server , For the terminal to download and upgrade .
Step4 Security upgrade
When burning firmware for the first time , adopt menuconfig Configure the signature verification public key to Bootloader In firmware , And burn it to the end device .

chart 6 Signature verification public key configuration
The end-side firmware triggers the upgrade check by time-sharing polling or manually , towards FOTA The cloud platform initiates an upgrade query , If there are released upgrade firmware , Then download it to the end device .
End side Bootloader The design framework of security upgrade software is as follows chart 7 Shown . The security upgrade module passed fota_update() The only interface to enter ,FOTA The business layer takes SM Kuhe ABUP Library as support ,SM The library provides cryptographic computing capabilities ,ABUP The library provides differential restore capability .
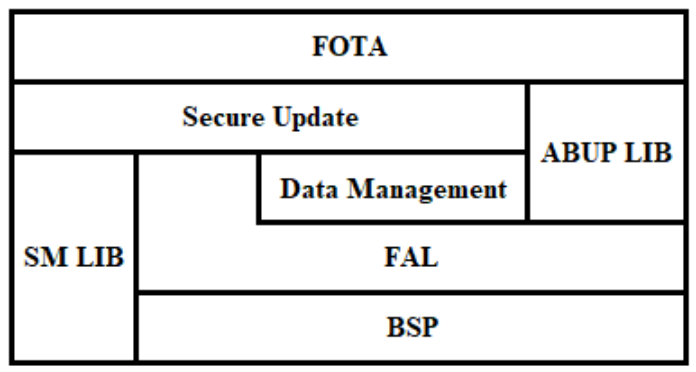
chart 7 bootloader Security upgrade software design framework
When the device restarts ,Bootloader First, check whether the device has firmware to be upgraded ( according to Header_Magic Judge ), If there is , First judge the firmware Header Safety count in Sec_cnt Is it greater than the current firmware security count of the device , If it is , Start the upgrade process , The course is like this chart 8 Shown .
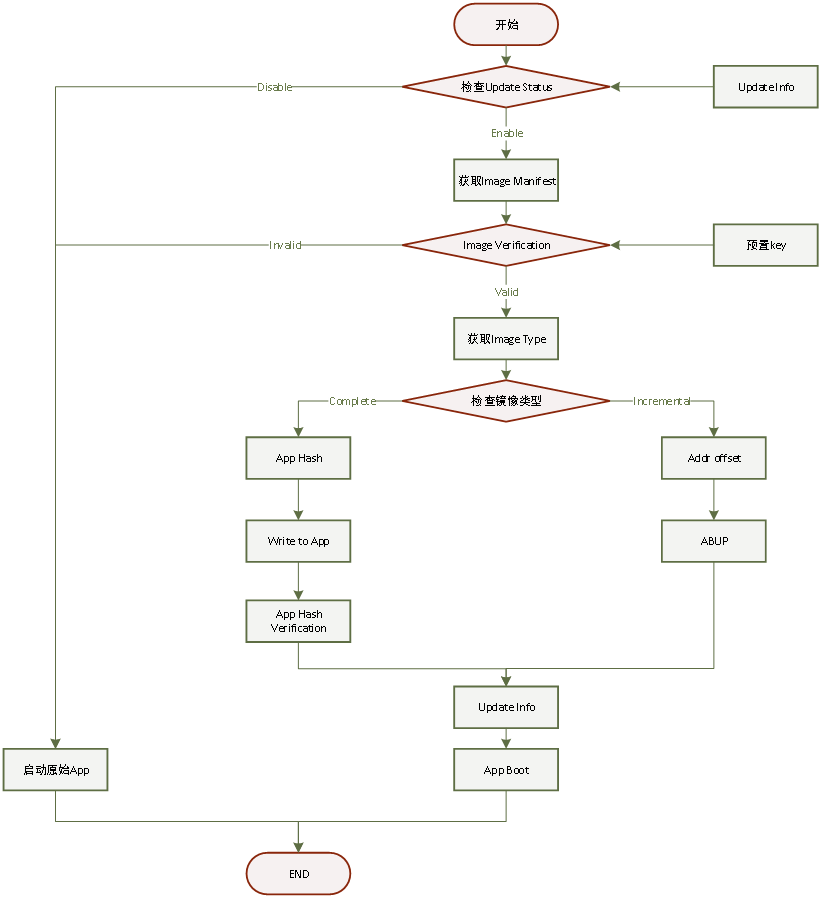
chart 8 Security upgrade process
By presetting in bootloader Decrypt ciphertext with symmetric key in Enc_Key, Get the symmetric key of firmware encryption , And pass Header_enc_alg Get the decryption algorithm to decrypt the firmware ciphertext , Get firmware plaintext , Replace firmware ciphertext stored in nonvolatile memory with firmware plaintext .
After decryption , Use preset in Bootloader The public key in and the decrypted firmware plaintext , To verify Header_Signature Is the signature value in correct .
During firmware verification , If the validation fails , Then determine that the firmware is illegal , Abandon this upgrade , And report to FOTA Cloud platform . After the verification is passed , We can know from the information obtained from the cloud platform when downloading , The current firmware is full firmware or differential firmware . If it is complete firmware , Directly use the target firmware to upgrade the device firmware ; If it is differential firmware , You need to call abup_fotapatch_procedure()(ABUP Differential reduction algorithm ) Interface or ota_start_up()( Self developed difference algorithm ) Restore the differential firmware , Use differential firmware to directly upgrade device firmware .
Through the above verification process, the security in the upgrade process can be greatly guaranteed . After the upgrade process is completed , The system jumps to the upgraded system and starts , The device actively reports the upgrade , Complete the whole upgrade process .
The end of this paper ~
边栏推荐
- Haut OJ 1357: lunch question (I) -- high precision multiplication
- Cocos create Jiugongge pictures
- 2022上半年全国教师资格证下
- 发现一个很好的 Solon 框架试手的教学视频(Solon,轻量级应用开发框架)
- Download and use of font icons
- Embedded database development programming (zero)
- To be continued] [UE4 notes] L4 object editing
- 小程序直播+電商,想做新零售電商就用它吧!
- [to be continued] I believe that everyone has the right to choose their own way of life - written in front of the art column
- Unity enables mobile phone vibration
猜你喜欢
随机推荐
Animation
[sum of two numbers] 169 sum of two numbers II - enter an ordered array
YOLOv5添加注意力機制
Learning notes of "hands on learning in depth"
Reverse one-way linked list of interview questions
UE4/UE5 虚幻引擎,材质篇,纹理,Compression and Memory压缩和内存
A preliminary study of sdei - see the essence through transactions
Research on the value of background repeat of background tiling
Stm32cubemx (8): RTC and RTC wake-up interrupt
Lua GBK and UTF8 turn to each other
[trans]: spécification osgi
Optimization scheme of win10 virtual machine cluster
Shell Sort
Vs2015 secret key
Unity find the coordinates of a point on the circle
Kali 2018 full image download
Embedded database development programming (zero)
win10虚拟机集群优化方案
UE4/UE5 虚幻引擎,材质篇(三),不同距离的材质优化
Heap sort summary