当前位置:网站首页>【SQL注入】联合查询(最简单的注入方法)
【SQL注入】联合查询(最简单的注入方法)
2022-07-03 04:33:00 【黑色地带(崛起)】
目录
一、介绍:
是最简单的一种注入方法
联合查询注入 报错查询注入 布尔型注入 延时注入 堆叠查询注入
二、原理:
就是可合并多个查询的结果的合集,顾名思义,就是将一个表追加到另一个表后,从而实现查询结果组合在一起。
在URL的参数位置中,将构造的语句注入到参数位置中
select (原始查询内容) union select (构造的内容)
三、前提条件
①存在注入点,即未被过滤
②有显示位,即能回显结果
③两表列数相同,即order by 或union select 去判断列 数
④数据类型相同
四、利用过程
1、判断是否存在注入点
(1)在参数位置修改参数值,eg:id=1修改为2后是否数据改变
(2)插入单、双引号的检测方法(常用),未闭合的单引号会引起SQL语句单引号未闭合的错误提示
2、判断注入点还是整形或字符型
(1)数字型:通过and 1=1
(2)字符串型:闭合单引号测试语句'and'1'='1进行判断
3、判断查询列数
order by 或 union select
4、判断显示位
报错回显,用不存在的id=-1加上union select……
或者and1=2加上union select……
下面的就都是通过报错后,在显示位构造要查找的信息
5、获取所有数据库名
6、获取数据库所有表名
7、获取字段名
8、获取字段中的数据
边栏推荐
- GFS分布式文件系统(光是遇见已经很美好了)
- 重绘和回流
- The simple problem of leetcode: dismantling bombs
- [literature reading] sparse in deep learning: practicing and growth for effective information and training in NN
- Interface in TS
- 使用BENCHMARKSQL工具对KingbaseES执行测试时报错funcs sh file not found
- Mongodb slow query optimization analysis strategy
- 使用BENCHMARKSQL工具对KingbaseES预热数据时执行:select sys_prewarm(‘NDX_OORDER_2 ‘)报错
- 使用BENCHMARKSQL工具对kingbaseES执行灌数据提示无法找到JDBC driver
- vulnhub HA: Natraj
猜你喜欢
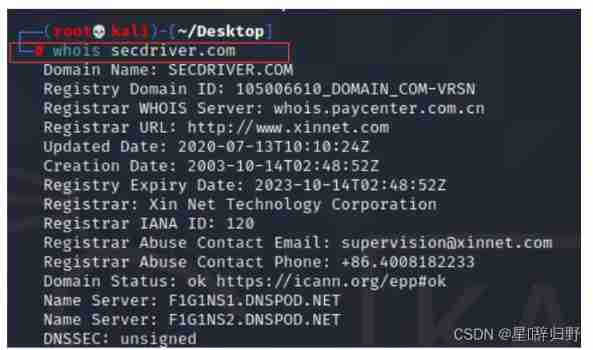
Web - Information Collection
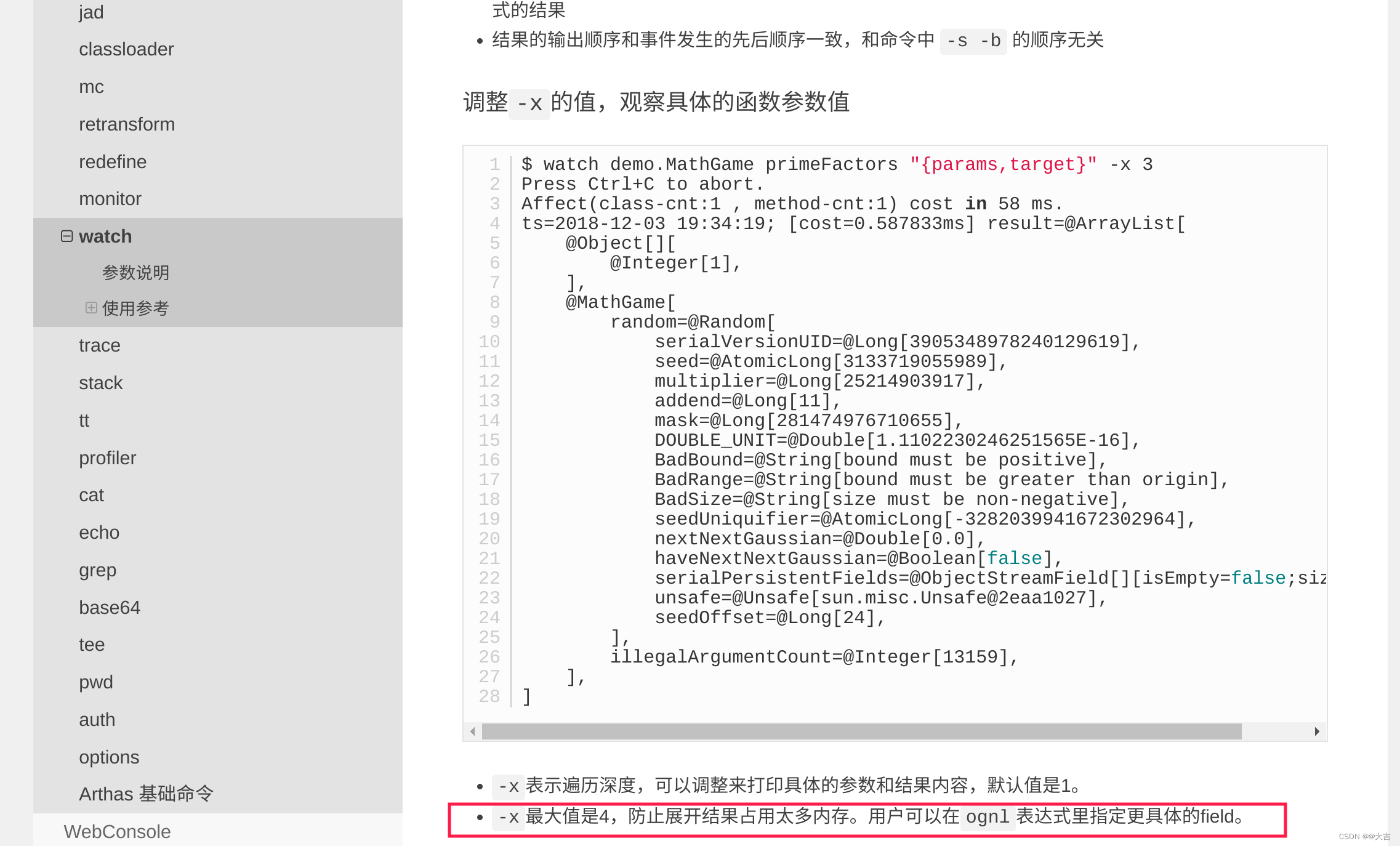
arthas watch 抓取入参的某个字段/属性

P35-P41 fourth_ context

Learning practice: comprehensive application of cycle and branch structure (I)
The programmer went to bed at 12 o'clock in the middle of the night, and the leader angrily scolded: go to bed so early, you are very good at keeping fit

After job hopping at the end of the year, I interviewed more than 30 companies in two weeks and finally landed

Leetcode simple question: check whether the array is sorted and rotated

Golang -- realize file transfer
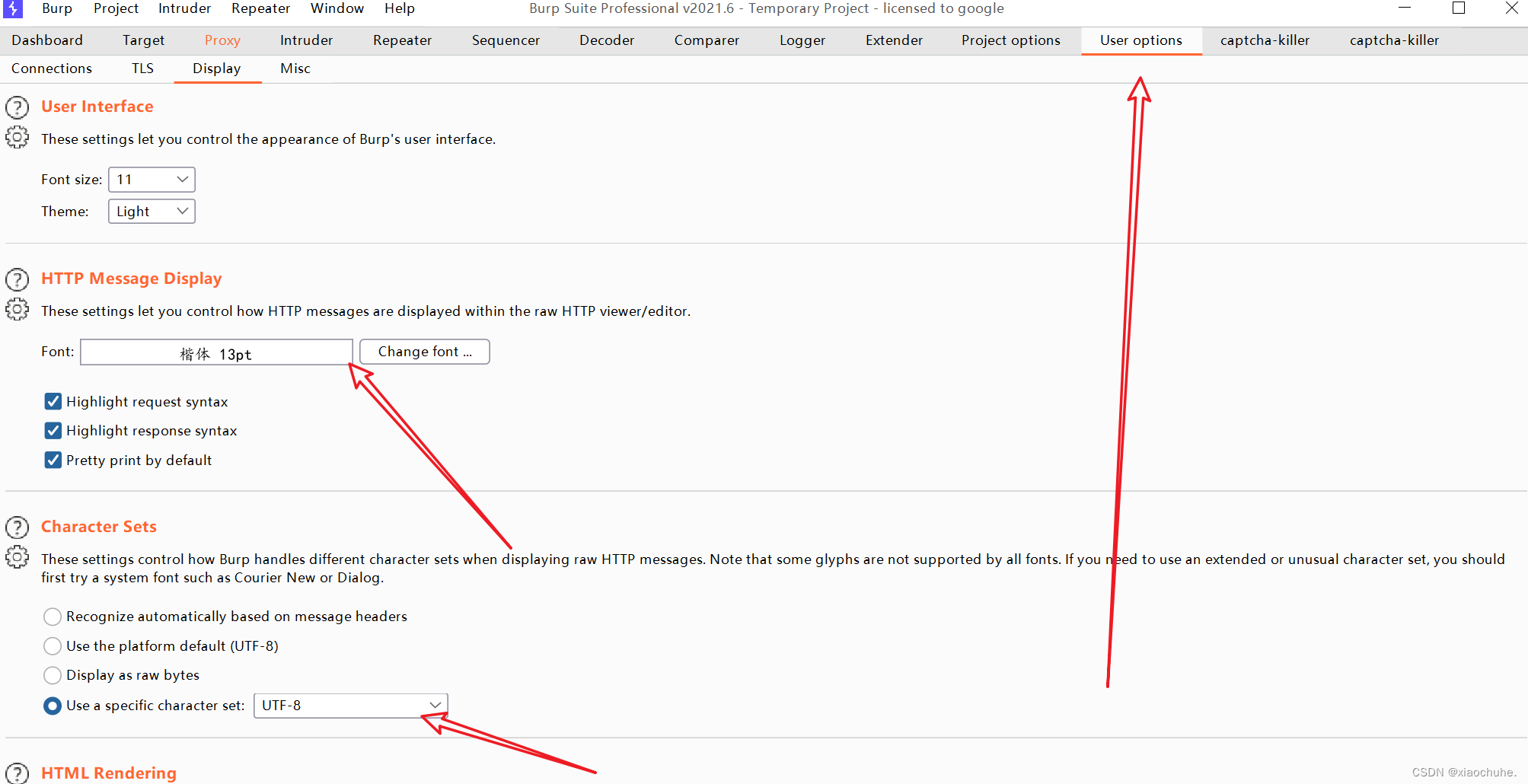
Solve BP Chinese garbled code

2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
随机推荐
[set theory] set operation (Union | intersection | disjoint | relative complement | symmetric difference | absolute complement | generalized union | generalized intersection | set operation priority)
Internationalization and localization, dark mode and dark mode in compose
Introduction of pointer variables in function parameters
Crazy scientist
FISCO bcos zero knowledge proof Fiat Shamir instance source code
Which code editor is easy to use? Code editing software recommendation
多板块轮动策略编写技巧----策略编写学习教材
怎么用Kotlin去提高生产力:Kotlin Tips
PostgreSQL database high availability Patroni source code learning - etcd class
Redis persistence principle
FFMpeg filter
Web security - CSRF (token)
2.14 summary
When using the benchmarksql tool to test the concurrency of kingbasees, there are sub threads that are not closed in time after the main process is killed successfully
Matplotlib -- save graph
金仓数据库KingbaseES 插件kdb_date_function
[set theory] ordered pair (ordered pair | ordered triple | ordered n ancestor)
[set theory] binary relationship (binary relationship notation | binary relationship from a to B | number of binary relationships | example of binary relationship)
[fairseq] 报错:TypeError: _broadcast_coalesced(): incompatible function arguments
Arthas watch grabs a field / attribute of the input parameter