当前位置:网站首页>Moxa NPort device flaw could expose critical infrastructure to devastating attack
Moxa NPort device flaw could expose critical infrastructure to devastating attack
2022-07-31 02:46:00 【Network Research Institute】

Two potentially critical vulnerabilities that could allow threat actors to wreak havoc have been discovered in widely used industrial connected devices manufactured by Moxa.
The Taiwan-based provider of industrial networking and automation solutions has addressed these deficiencies.
The two security vulnerabilities, tracked as CVE-2022-2043 and CVE-2022-2044, rated "High Severity", affect Moxa's NPort 5110 device server, which is designed to connect serial devices toto the Ethernet network.A remote attacker could exploit these vulnerabilities to put a target device into a Denial of Service (DoS) state.
Moxa and the U.S. Cybersecurity and Infrastructure Security Agency ( CISA ) have issued advisories for these vulnerabilities.Moxa said only firmware version 2.10 was affected, and instructed customers to contact their technical support for assistance.CISA asked affected organizations to contact Moxa for security patches.
Moxa and CISA both praised Jens Nielsen, a researcher at Danish industrial cybersecurity firm En Garde Security, for reporting the vulnerabilities.
In a blog post published this week, En Garde Security owner Mikael Vingaard said his company's research department discovered the vulnerabilities in the first half of March 2022, when a proof-of-concept (PoC) was made available to the vendor.) script and a video showing the exploit.
Vingaard told us that while Moxa NPort devices should not be exposed to the Internet, many devices are actually accessible over the network.A Shodan search revealed over 5,000 devices, and while there may be some honeypots, they can't all be honeypots.

He said that exploiting the two flaws only requires a network connection to the target device.Exploits can be executed "in seconds" and can be automated over the internet.
Affected NPort devices are used worldwide, including in critical infrastructure sectors such as energy, critical manufacturing and transportation systems.There were reports that these types of equipment were targeted for sabotage in an attack on Ukraine's power grid in 2015, causing severe power outages.
Exploiting the vulnerabilities discovered by En Garde researchers could disrupt critical services in these sectors, Vingaard described vulnerable Moxa devices as "a small fraction of our society's vital infrastructure services."
He explained that the first DoS vulnerability could allow an attacker to make a target device stop responding to legitimate commands.
“The only way to regain control of the equipment is to have staff power off/on the equipment, which requires someone to be physically present,” “This can often cause problems in remote areas where it can take a significant amount of time to get people on site, andNot ideal in situations where time to regain control may be important."
The second vulnerability is an out-of-bounds issue where an attacker can access and/or overwrite elements on the device, resulting in data corruption or corruption.This renders the system inoperable and in some cases may cause permanent damage to the device.


边栏推荐
- 【shell基础】判断目录是否为空
- Detailed explanation of STP election (step + case)
- Software accumulation -- Screenshot software ScreenToGif
- Real-time image acquisition based on FPGA
- The simulation application of common mode inductance is here, full of dry goods for everyone
- The Sad History of Image Processing Technology
- 1. Non-type template parameters 2. Specialization of templates 3. Explanation of inheritance
- mmdetection trains a model related command
- 关于 mysql8.0数据库中主键位id,使用replace插入id为0时,实际id插入后自增导致数据重复插入 的解决方法
- 开题报告之论文框架
猜你喜欢
Installation, start and stop of redis7 under Linux
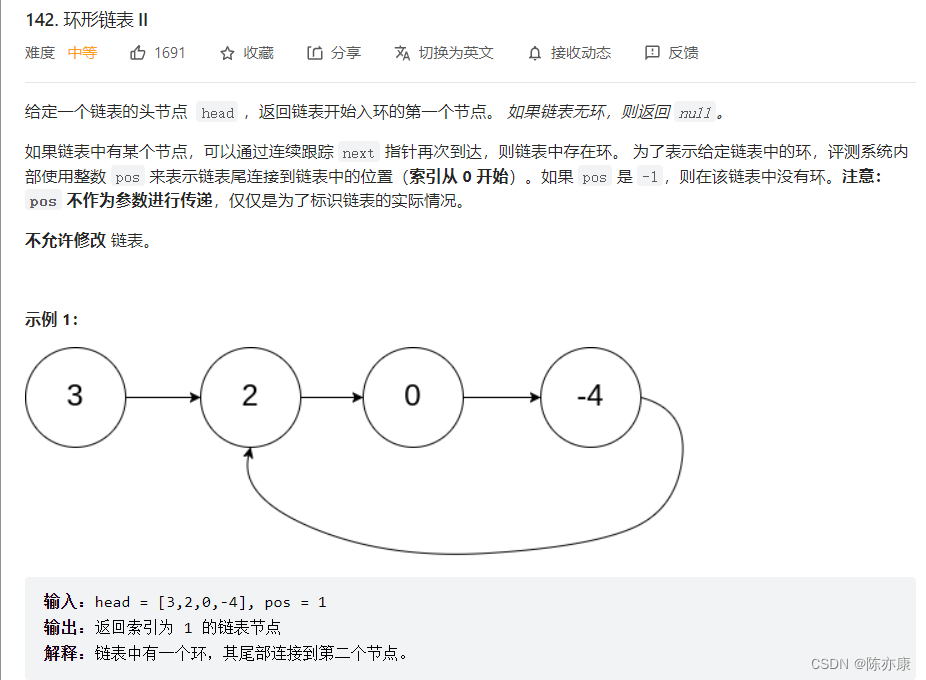
数学解决——环形链表问题
YOLOV5学习笔记(二)——环境安装+运行+训练

学习DAVID数据库(1)
![LeetCode 1161 The largest element in the layer and the LeetCode road of [BFS binary tree] HERODING](/img/56/fcc8ee6f592abf0a374fc950a3362f.png)
LeetCode 1161 The largest element in the layer and the LeetCode road of [BFS binary tree] HERODING
什么是分布式锁?实现分布式锁的三种方式

php 网站的多语言设置(IP地址区分国内国外)

Basic learning about Redis related content

Why is String immutable?

221. Largest Square
随机推荐
AtCoder Beginner Contest 261 Partial Solution
SQL注入 Less54(限制次数的SQL注入+union注入)
TCP/IP四层模型
CefSharp入门-winform
Project development software directory structure specification
Number 16, top posts
TCP/IP four-layer model
LeetCode 1161 最大层内元素和[BFS 二叉树] HERODING的LeetCode之路
User interaction + formatted output
6. Display comments and replies
[Android] Room - Alternative to SQLite
Multilingual settings of php website (IP address distinguishes domestic and foreign)
Brute Force/Adjacency List Breadth First Directed Weighted Graph Undirected Weighted Graph
Discussion on Service Commitment of Class Objects under Multithreading
mycat的主从关系 垂直分库 水平分表 以及mycat分片联表查询的配置详解(mysql5.7系列)
The principle of complete replication of virtual machines (cloud computing)
JS 函数 this上下文 运行时点语法 圆括号 数组 IIFE 定时器 延时器 self.备份上下文 call apply
Maximum area of solar panel od js
AI在医疗影像设备全流程应用
拒绝加班,程序员开发的效率工具集