当前位置:网站首页>Risk planning and identification of Oracle project management system
Risk planning and identification of Oracle project management system
2022-07-06 07:38:00 【Siwicloud】
The beginning of the volume
By defining the scope of the project , The scope of the project can be clarified , Break down the tasks of the project into more specific 、 More manageable , Avoid risks caused by omission .

Program Overview
Project risk management refers to risk identification 、 Risk analysis and risk evaluation to understand the risks of the project , On this basis, we should reasonably use various risk response measures 、 Management methods, techniques and means , Effectively control the risks of the project , Properly handle the adverse consequences caused by risk events , The management work to ensure the realization of the overall objectives of the project at the least cost . By defining the scope of the project , The scope of the project can be clarified , Break down the tasks of the project into more specific 、 More manageable , Avoid risks caused by omission . In the course of the project , Changes are inevitable , Change will bring some new uncertainties , Risk management can be achieved by identifying risks 、 Analyze to evaluate these uncertainties , So as to propose tasks to project scope management .
The business architecture of the risk management module is shown in the figure below :

The risk management module of this system can provide basic risk management , Include : Risk identification , assessment 、 analysis 、 relieve 、 Monitoring etc. .
The risk management in the system is divided into two parts: the establishment of risk base and the quantitative analysis of project stability . The establishment of risk database is the systematic enterprise data , The risk category used to establish the plan identified in advance 、 Risk scoring matrix and other information . Project risk is the risk page in the project module , In this page , Project risks can be identified 、 analysis 、 Relate the work and prepare the corresponding plan .
Risk planning
In the project initiation and implementation stage , Through the analysis of historical data , Understand the main risks faced by this project , And carry out risk planning for .

Risk identification
According to the definition and description of the project 、 The completion plan and individual plan arrangement of the project, as well as various historical information and experience , Use the project risk checklist method 、 Process analysis 、 Expert judgment and meeting discussion , Identify internal and external risks of the project , And analyze the possible consequences . This is a project management work to reduce the possible losses of the project . Decompose the identified risks into WBS In the work package , Make risk management throughout the project .

chart : Risk identification matrix
ORACLE The risk management module can guide risk managers to quickly establish a risk list , Define risk scoring criteria 、 Enter qualitative risk assessment criteria , And link risks with project operations , So as to guide the evaluation of quantitative analysis .
边栏推荐
- 杰理之BLE【篇】
- 【mysql学习笔记30】锁(非教程)
- Typescript function definition
- The way to learn go (I) the basic introduction of go to the first HelloWorld
- Three no resumes in the software testing industry. What does the enterprise use to recruit you? Shichendahai's resume
- CF1036C Classy Numbers 题解
- Le chemin du navigateur Edge obtient
- Memory error during variable parameter overload
- Sharing of source code anti disclosure scheme under burning scenario
- Oracle column to row -- a field is converted to multiple rows according to the specified separator
猜你喜欢

Google可能在春节后回归中国市场。
链表面试题(图文详解)
![[1. Delphi foundation] 1 Introduction to Delphi Programming](/img/14/272f7b537eedb0267a795dba78020d.jpg)
[1. Delphi foundation] 1 Introduction to Delphi Programming
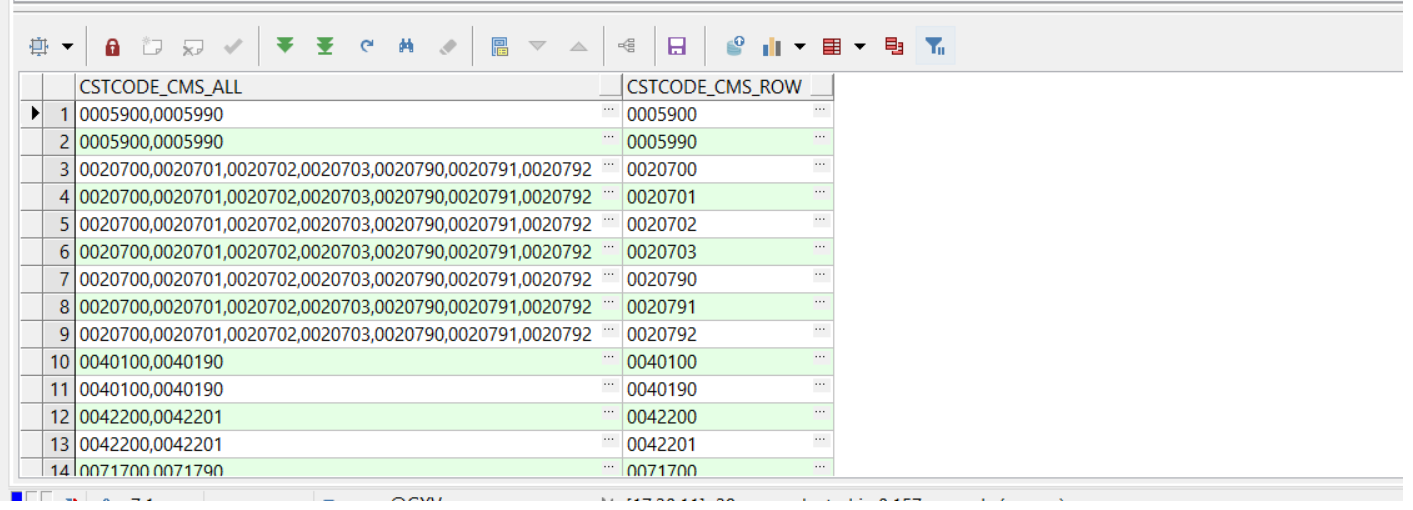
ORACLE列转行--某字段按指定分隔符转多行

数字经济时代,如何保障安全?
![[window] when the Microsoft Store is deleted locally, how to reinstall it in three steps](/img/57/ee979a7db983ad56f0df7345dbc91f.jpg)
[window] when the Microsoft Store is deleted locally, how to reinstall it in three steps

qt颜色与字符串、uint相互转换
![Jerry's ad series MIDI function description [chapter]](/img/28/e0f9b41db597ff3288af431c677001.png)
Jerry's ad series MIDI function description [chapter]
智能终端设备加密防护的意义和措施
Comparison of usage scenarios and implementations of extensions, equal, and like in TS type Gymnastics
随机推荐
Significance and measures of encryption protection for intelligent terminal equipment
杰理之BLE【篇】
leecode-C语言实现-15. 三数之和------思路待改进版
The ECU of 21 Audi q5l 45tfsi brushes is upgraded to master special adjustment, and the horsepower is safely and stably increased to 305 horsepower
Wonderful use of TS type gymnastics string
【mysql学习笔记30】锁(非教程)
Go learning --- use reflection to judge whether the value is valid
Is the super browser a fingerprint browser? How to choose a good super browser?
[online problem processing] how to kill the corresponding process when the MySQL table deadlock is caused by the code
How Navicat imports MySQL scripts
智能终端设备加密防护的意义和措施
Oracle column to row -- a field is converted to multiple rows according to the specified separator
杰理之BLE【篇】
leecode-C語言實現-15. 三數之和------思路待改進版
C # display the list control, select the file to obtain the file path and filter the file extension, and RichTextBox displays the data
Simulation of Michelson interferometer based on MATLAB
Do you really think binary search is easy
Word delete the contents in brackets
Scala language learning-08-abstract classes
Emo diary 1
