当前位置:网站首页>POJ-2499 Binary Tree
POJ-2499 Binary Tree
2022-07-05 12:12:00 【全栈程序员站长】
Binary Tree
Time Limit: 1000MS | Memory Limit: 65536K | |
|---|---|---|
Total Submissions: 5211 | Accepted: 2420 |
Description
Background Binary trees are a common data structure in computer science. In this problem we will look at an infinite binary tree where the nodes contain a pair of integers. The tree is constructed like this:
- The root contains the pair (1, 1).
- If a node contains (a, b) then its left child contains (a + b, b) and its right child (a, a + b)
Problem Given the contents (a, b) of some node of the binary tree described above, suppose you are walking from the root of the tree to the given node along the shortest possible path. Can you find out how often you have to go to a left child and how often to a right child?
Input
The first line contains the number of scenarios. Every scenario consists of a single line containing two integers i and j (1 <= i, j <= 2*10 9) that represent a node (i, j). You can assume that this is a valid node in the binary tree described above.
Output
The output for every scenario begins with a line containing “Scenario #i:”, where i is the number of the scenario starting at 1. Then print a single line containing two numbers l and r separated by a single space, where l is how often you have to go left and r is how often you have to go right when traversing the tree from the root to the node given in the input. Print an empty line after every scenario.
Sample Input
3
42 1
3 4
17 73Sample Output
Scenario #1:
41 0
Scenario #2:
2 1
Scenario #3:
4 6 1 /*
2 题意:根(a,b),则左孩子为(a+b,b),右孩子为(a,a+b)
3 给定(m,n),初试根为(1,1),从(1,1)到(m,n)需要往左子树走几次,
4 往右子树走几次。
5 思路:逆向思维,从(m,n)到(1,1)。
6 给定(m,n),求其父亲,如果m>n,则他父亲是(m-n,n),
7 否则(m,n-m)。
8 代码一: ----TLE
9 #include <iostream>
10
11 using namespace std;
12
13 int main()
14 {
15 int T, a, b, lcnt, rcnt;
16 cin >> T;
17 for(int i = 1; i <= T; ++i)
18 {
19 cin >> a >> b;
20 lcnt = rcnt = 0;
21 while(a != 1 || b != 1)
22 {
23 if(a >= b)
24 {
25 ++lcnt;
26 a -= b;
27 }
28 else
29 {
30 ++rcnt;
31 b -= a;
32 }
33 }
34 cout << "Scenario #" << i << ':' << endl;
35 cout << lcnt << ' ' << rcnt << endl <<endl;
36 }
37 return 0;
38 }
39
40 代码二:
41 用除法代替减法,得到的商即为往左走的次数,最后的m=m%n。
42 n>m时情况类推。
43 需要特别注意的是:
44 如果m>n,m%n == 0 怎么办?因为根(1,1)不可能有0存在,所以特殊处理一下:
45 次数:m/n-1;m=1
46 */
47 #include <iostream>
48
49 using namespace std;
50
51 int main()
52 {
53 int T, a, b, lcnt, rcnt;
54 cin >> T;
55 for(int i = 1; i <= T; ++i)
56 {
57 cin >> a >> b;
58 lcnt = rcnt = 0;
59 while(a != 1 || b != 1)
60 {
61 if(a >= b)
62 {
63 if(a % b)
64 {
65 lcnt += a/b;
66 a %= b;
67 }
68 else
69 {
70 lcnt += a/b-1;
71 a = 1;
72 }
73 }
74 else
75 {
76 if(b % a)
77 {
78 rcnt += b/a;
79 b %= a;
80 }
81 else
82 {
83 rcnt += b/a-1;
84 b = 1;
85 }
86 }
87 }
88 cout << "Scenario #" << i << ':' << endl;
89 cout << lcnt << ' ' << rcnt << endl <<endl;
90 }
91 return 0;
92 }发布者:全栈程序员栈长,转载请注明出处:https://javaforall.cn/110203.html原文链接:https://javaforall.cn
边栏推荐
- Understanding the architecture type of mobile CPU
- 15 methods in "understand series after reading" teach you to play with strings
- 【上采样方式-OpenCV插值】
- Redis master-slave mode
- Redis集群(主从)脑裂及解决方案
- pytorch-softmax回归
- liunx禁ping 详解traceroute的不同用法
- Error modulenotfounderror: no module named 'cv2 aruco‘
- Select drop-down box realizes three-level linkage of provinces and cities in China
- Hiengine: comparable to the local cloud native memory database engine
猜你喜欢
全网最全的新型数据库、多维表格平台盘点 Notion、FlowUs、Airtable、SeaTable、维格表 Vika、飞书多维表格、黑帕云、织信 Informat、语雀
网络五连鞭

pytorch-权重衰退(weight decay)和丢弃法(dropout)
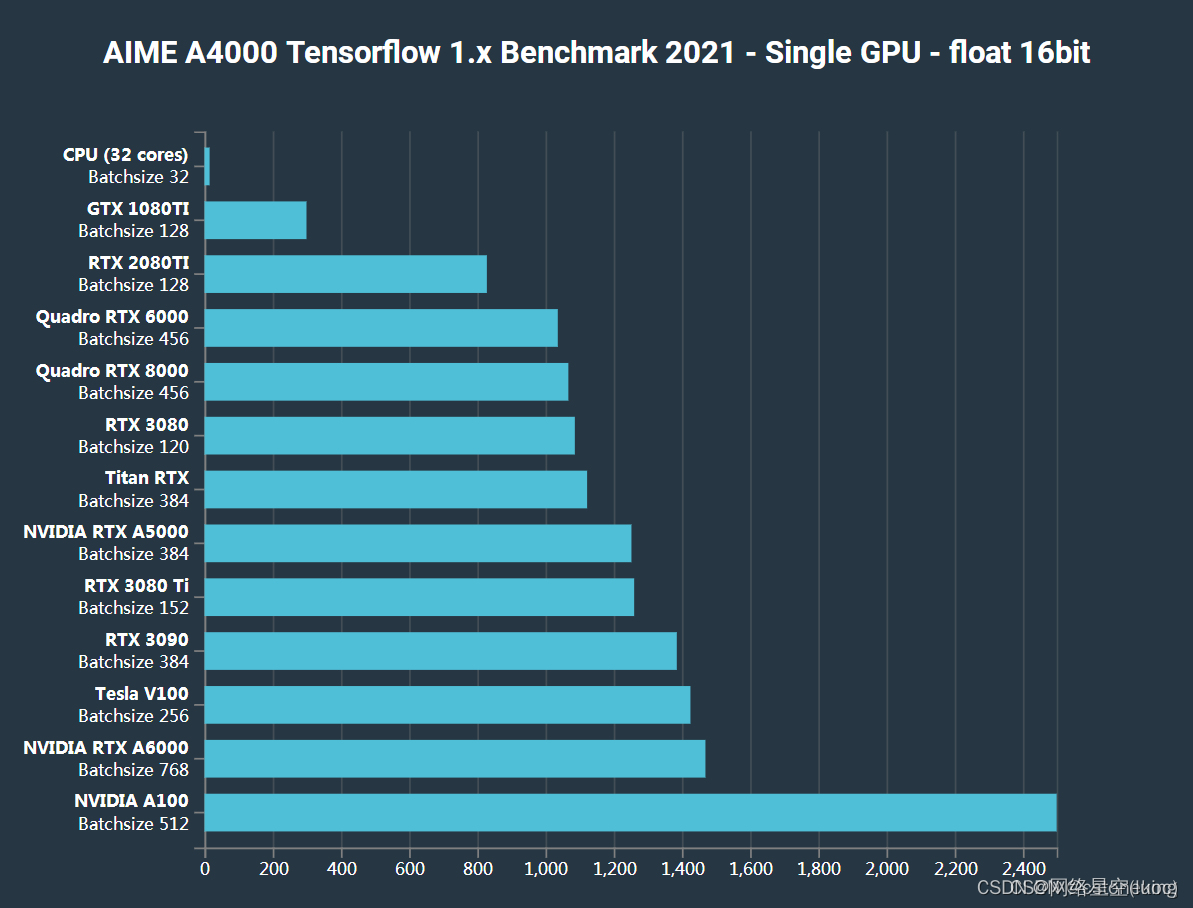
【主流Nivida显卡深度学习/强化学习/AI算力汇总】
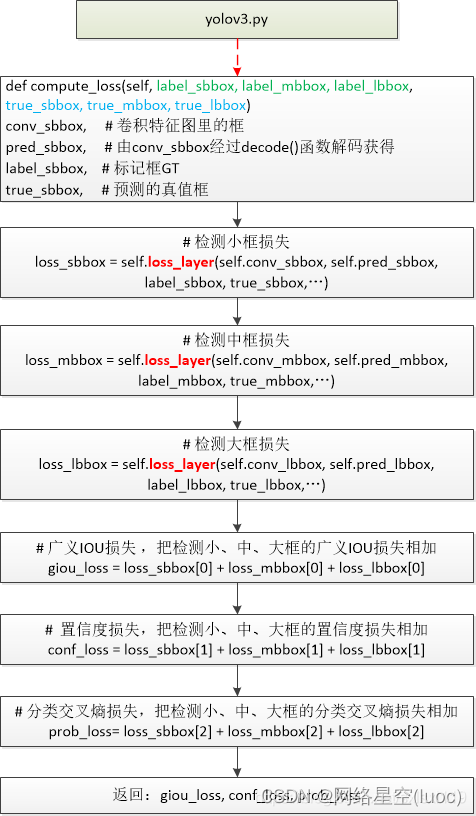
【yolov3损失函数】

Pytorch weight decay and dropout
Select drop-down box realizes three-level linkage of provinces and cities in China
Error modulenotfounderror: no module named 'cv2 aruco‘
mmclassification 训练自定义数据
![[loss functions of L1, L2 and smooth L1]](/img/c6/27eab1175766b77d4f030b691670c0.png)
[loss functions of L1, L2 and smooth L1]
随机推荐
互联网公司实习岗位选择与简易版职业发展规划
【yolov5.yaml解析】
嵌入式软件架构设计-消息交互
Tabbar configuration at the bottom of wechat applet
跨平台(32bit和64bit)的 printf 格式符 %lld 输出64位的解决方式
Xi IO flow
Mmclassification training custom data
语义分割实验:Unet网络/MSRC2数据集
Codeworks 5 questions per day (1700 average) - day 5
[loss functions of L1, L2 and smooth L1]
The solution of outputting 64 bits from printf format%lld of cross platform (32bit and 64bit)
15 methods in "understand series after reading" teach you to play with strings
【上采样方式-OpenCV插值】
[upsampling method opencv interpolation]
mysql拆分字符串做条件查询
1 plug-in to handle advertisements in web pages
报错ModuleNotFoundError: No module named ‘cv2.aruco‘
ABAP table lookup program
12. (map data) cesium city building map
投资理财适合女生吗?女生可以买哪些理财产品?