当前位置:网站首页>Research: data security tools cannot resist blackmail software in 60% of cases
Research: data security tools cannot resist blackmail software in 60% of cases
2022-07-05 12:46:00 【Open source China Information】
Data security provider Titaniam Released a 《 Data leakage and extortion status report 》 Pointed out that , Although more than 70% Our organization has an existing set of prevention 、 Detection and backtracking solutions , But it's close 40% Our organization has been attacked by blackmail software in the past year .
The results show that , Traditional data security tools , Such as security backup and recovery tools 、 Provide static and transmission encryption solutions 、 Tokenization and data masking , stay 60% Can't protect the enterprise's data from the threat of blackmail software . The study emphasizes , The most important thing is that organizations cannot only rely on traditional data security tools to defend against data leakage and double extortion software attacks ; They also need to be able to Encrypt the data in use , To stop the trace of malicious actors .
The problem with traditional data security tools is not that they do not have strong security measures , Instead, attackers can bypass these controls by stealing credentials , To gain privileged access to key data assets .Titaniam Founder and CEO Arti Raman call , These traditional tools have no effect on blackmail software and blackmail behavior , Because the most common attack is not an attacker " intrusion ", Instead, the attacker uses stolen credentials " Sign in ". When that happens , Traditional security tools treat attackers as effective users .
“ under these circumstances , When an attacker moves in the network , They can use their credentials to decrypt like legitimate users or administrators in their daily work 、 Disassembling and uncovering data . Once the data is decrypted , The attacker will reveal it , And use it as a means of extortion .”
Raman Pointed out that , The shift to data leakage occurred in 2020 About the middle and late years of the year , At that time, cyber criminals began to integrate data leakage , In order to use backup and recovery solutions to gain greater influence on victims .
The only way to defend against typical intrusions of modern ransomware attacks is for organizations to deploy data security solutions that use encryption . Encryption in use can help hide data , It cannot be stolen by an attacker who has privileged access to enterprise resources .
The demand for enhanced data protection has driven the significant growth of the data encryption market , Researchers at 2020 The market was valued at 94.3 Billion dollars , And expect 2030 The market value will reach 423 Billion dollars .Gartner It is also expected , Data encryption will become more and more popular in the future ; Expect to 2023 year ,40% Your enterprise will have multiple sites 、 Mixed and multicolor data encryption strategies , And in the 2020 This proportion is less than 5%.
边栏推荐
- Learning items
- Simply take stock reading notes (3/8)
- Just a coincidence? The mysterious technology of apple ios16 is actually the same as that of Chinese enterprises five years ago!
- ZABBIX 5.0 - LNMP environment compilation and installation
- Principle of universal gbase high availability synchronization tool in Nanjing University
- JDBC exercise - query data encapsulated into object return & simple login demo
- Distance measuring sensor chip 4530a used in home intelligent lighting
- Rasa Chat Robot Tutorial (translation) (1)
- Common commands and basic operations of Apache Phoenix
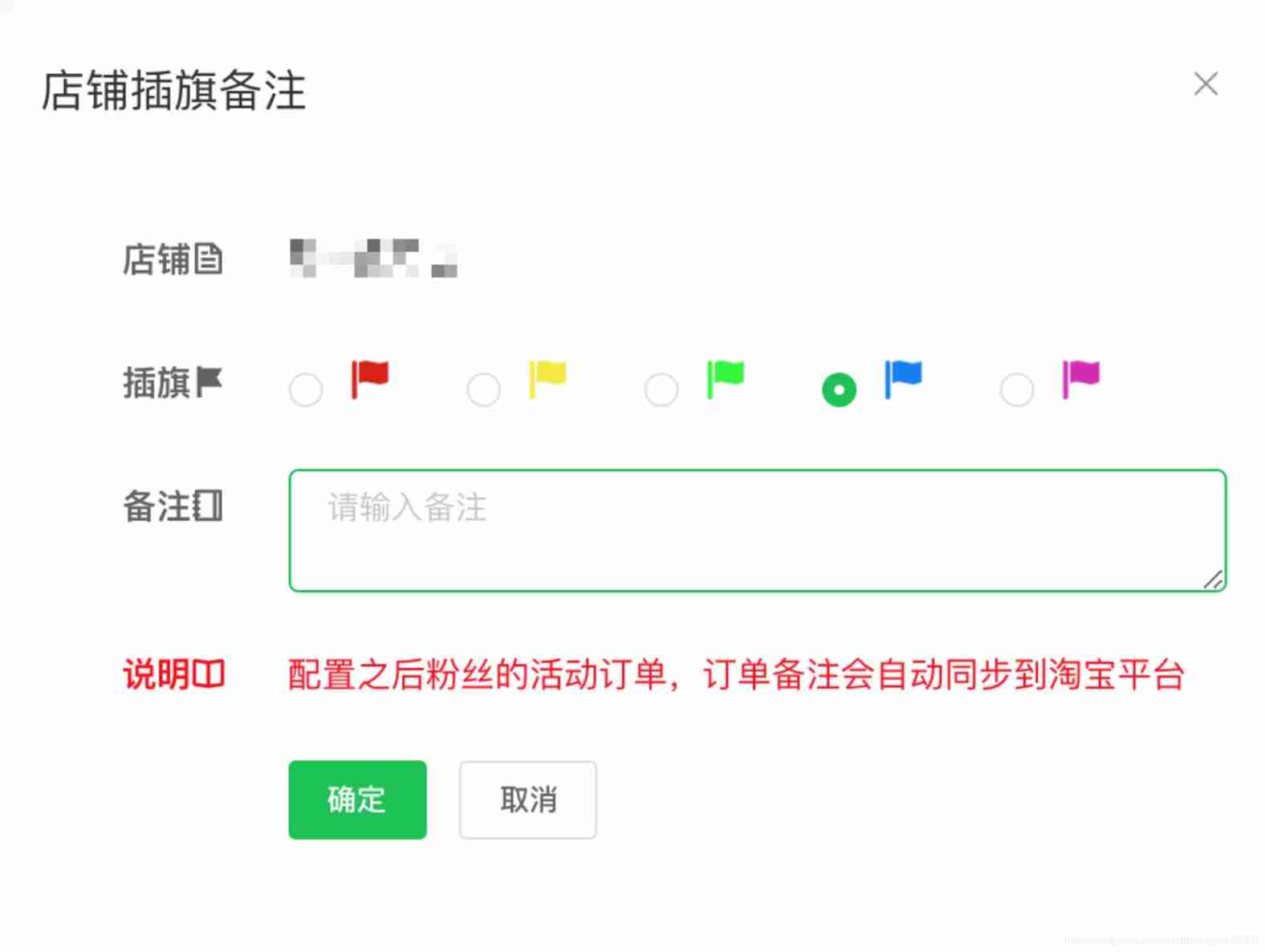
- Taobao flag insertion remarks | logistics delivery interface
猜你喜欢
Resnet+attention project complete code learning
JDBC -- extract JDBC tool classes
Simply take stock reading notes (3/8)
SAP 自开发记录用户登录日志等信息
Taobao flag insertion remarks | logistics delivery interface
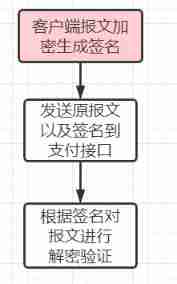
Third party payment interface design
![[figure neural network] GNN from entry to mastery](/img/e2/bb045fb03bc255b8659f9ca7cdd26b.jpg)
[figure neural network] GNN from entry to mastery
![[superhard core] is the core technology of redis](/img/5e/d6438f09031c2acbea17441c316a2b.jpg)
[superhard core] is the core technology of redis
Migrate data from Mysql to neo4j database
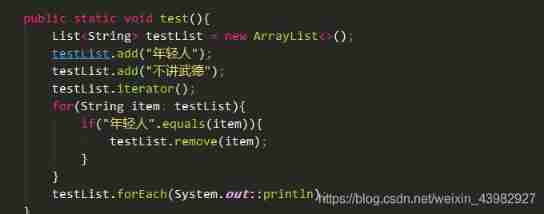
Iterator details in list... Interview pits
随机推荐
Correct opening method of redis distributed lock
Learn the memory management of JVM 03 - Method area and meta space of JVM
How to recover the information server and how to recover the server data [easy to understand]
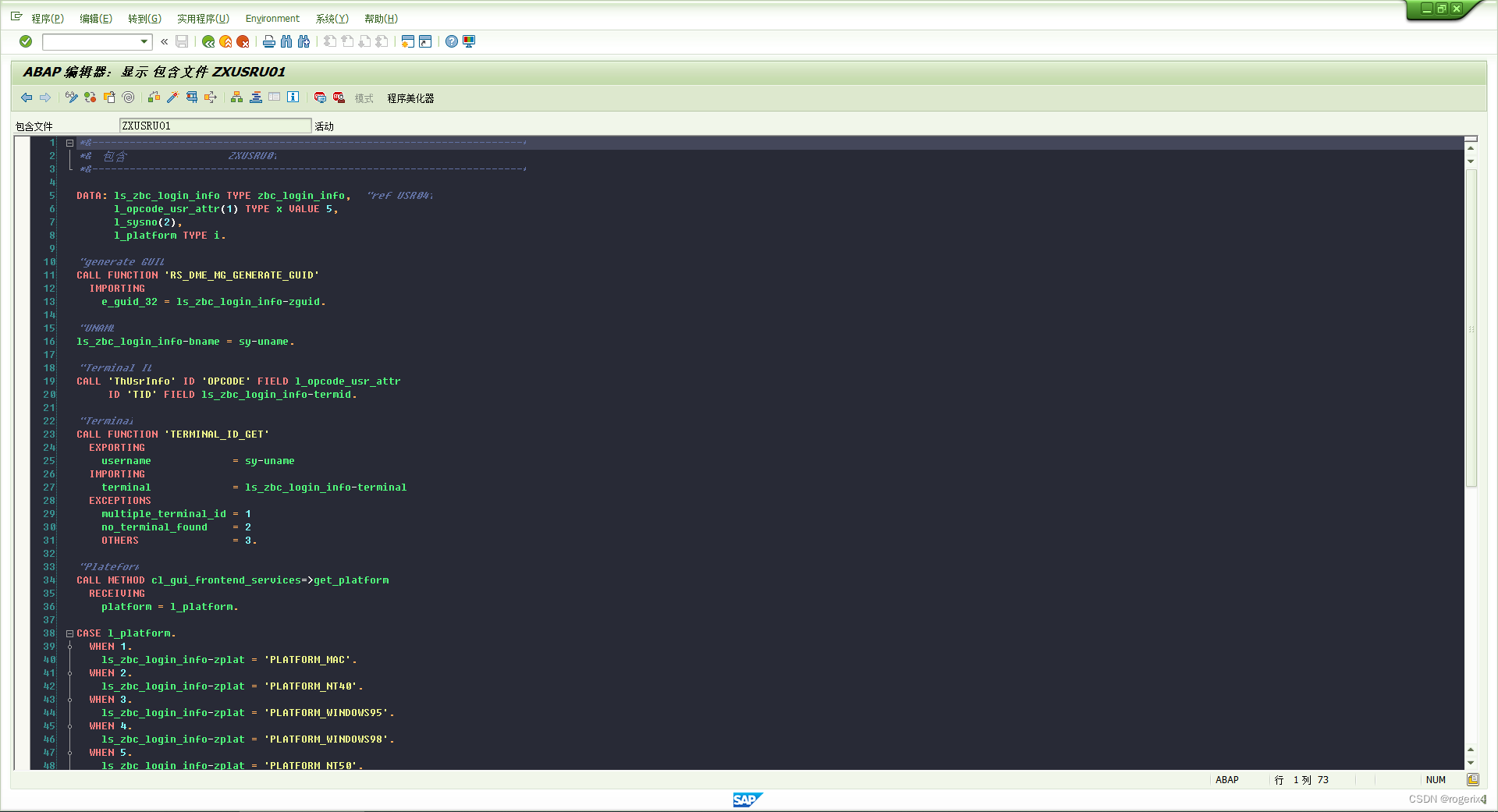
SAP 自开发记录用户登录日志等信息
前几年外包干了四年,秋招感觉人生就这样了..
Full text search of MySQL
Learn memory management of JVM 01 - first memory
Free testing of Taobao tmall API order and flag insertion remark interface
Clear neo4j database data
Learn JVM garbage collection 02 - a brief introduction to the reference and recycling method area
Master-slave mode of redis cluster
GPON other manufacturers' configuration process analysis
Pytoch counts the number of the same elements in the tensor
ZABBIX ODBC database monitoring
Experimental design - using stack to realize calculator
Transactions from December 29, 2021 to January 4, 2022
Cypher syntax of neo4j graph database
Redis's memory elimination mechanism, read this article is enough.
POJ-2499 Binary Tree
Introduction to GNN