当前位置:网站首页>Arm GIC (IV) GIC V3 register class analysis notes.
Arm GIC (IV) GIC V3 register class analysis notes.
2022-07-07 08:33:00 【Galloping tortoise】
Catalog
Life cycle disruption
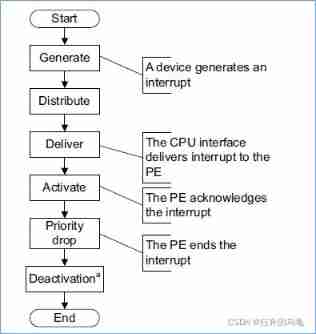
- generate: The peripheral initiates an interrupt
- distribute:distributor Arbitrate the received interrupt source , And then send it to the corresponding cpu interface
- deliver:cpu interface Send interrupt to core
- activate:core By reading the GICC_IAR register , To acknowledge the interruption
- priority drop: core By writing GICC_EOIR register , To achieve priority heavy
- deactivation:core By writing GICC_DIR register , To invalidate the interrupt
The whole interruption life cycle ,distribute and deliver The distribution mechanism depends on interrupt configuration , from activate To deactivation Are the working contents of interrupt processing function . The last few blog posts have introduced in detail GIC Infrastructure . Next, try to decompose from the source code and register manual TF-A GIC V3 Driver source code , Further understanding arm gic Interrupt the whole process of the life cycle .
GIC register
gicv3 in , Many more registers , And for registers , Provides 2 Access mode , One is memory-mapped The interview of , The other is system register access :
memory-mapped Registers accessed :
- GICC: cpu interface register
- GICD: distributor register
- GICH: virtual interface Control register , stay hypervisor Mode access
- GICR: redistributor register
- GICV: virtual cpu interface register
- GITS: ITS register
Register accessed by system register :
- ICC: Physics cpu interface System register
- ICV: fictitious cpu interface System register
- ICH: fictitious cpu interface Control system register
The picture below is gicv3 in , Each register , Where it is .

For system register access gic register , It is realized in core Inside . and memory-mapped How to access gic register , Is in gic Inside .
gicv3 Architecture , There is no coercion , Register of system register access mode , It can't go through memory-mapped Way to visit . That is to say ICC, ICV, ICH register , It can also be realized in gic Inside , adopt memory-mapped Way to visit . But in general implementation , There is no such implementation .
The picture below is ICC The system register of , and memory-mepped Part of the correspondence of the mode register , Check more gicv3 Of spec.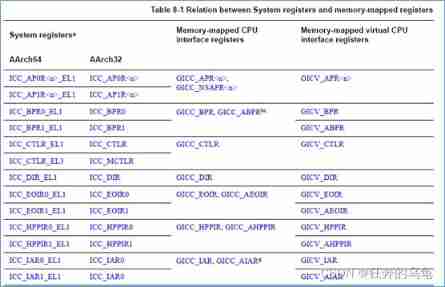
that , The problem is coming. ,gicv3 in , Why choose to cpu interface, from gic Middle detachment , Realize in core Inside ? Why would you cpu interface The register of , Add system register access mode , Realize in core Internal ? To do so , What are the benefits ?
In my submission ,gicv3 The above arrangement , The first is to make software writing simple , Universal ; The second is to make the interrupt response faster .
First of all, understand , stay gic In the register of , Which registers , Will be frequently core Visited , Which registers , Will not be frequently core Visited . without doubt ,cpu interface The register of , Will be frequently core Visited , because core Need to access cpu interface The register of , To acknowledge the interruption , To interrupt completion , To invalid interrupt . Other registers , The configuration is interrupted , Only in core When you need to configure interrupts , Only by visiting . With this understanding , Then understand what I'm talking about , It's easier .
stay gicv2 in ,cpu interface The register of , It is realized in gic Inside , So when core When an interrupt is received , Will pass axi Bus ( hypothesis memory The bus is axi Bus ), To visit cpu interface The register of . And interrupt in a soc In the system , It will happen frequently , That means ,core Will visit frequently gic The register of , This will occupy axi Bandwidth of the bus , In general, it will affect the real-time response of interrupts , and core adopt axi Bus to access cpu interface register , Delay , It's bigger .
stay gicv3 in , take cpu interface from gic Take it out , Realize in core Inside , But not in gic in .core Yes cpu interface The interview of , Access through system registers , That is to use msr,mrs visit , that core Yes cpu interface Register access , It accelerates , And it doesn't occupy axi Bus bandwidth . such core Interrupt handling , It accelerates .
cpu interface And gic Between , Through dedicated AXI-stream Bus , To transmit information , This will not occupy AXI Bandwidth of the bus .
TF-A Interrupt configuration source code analysis
TF-A Interrupt processing source code analysis
边栏推荐
- XCiT学习笔记
- Laravel8 uses passport login and JWT (generate token)
- JS copy picture to clipboard read clipboard
- One click deployment of highly available emqx clusters in rainbow
- 下载和安装orcale database11.2.0.4
- Composer change domestic image
- Full text query classification
- 基本数据类型和string类型互相转化
- Kotlin combines flatmap for filtering and zip merge operators
- 雅思考试自己的复习进度以及方法使用【日更版】
猜你喜欢
The truth of robot education in hands-on practice
DeiT学习笔记
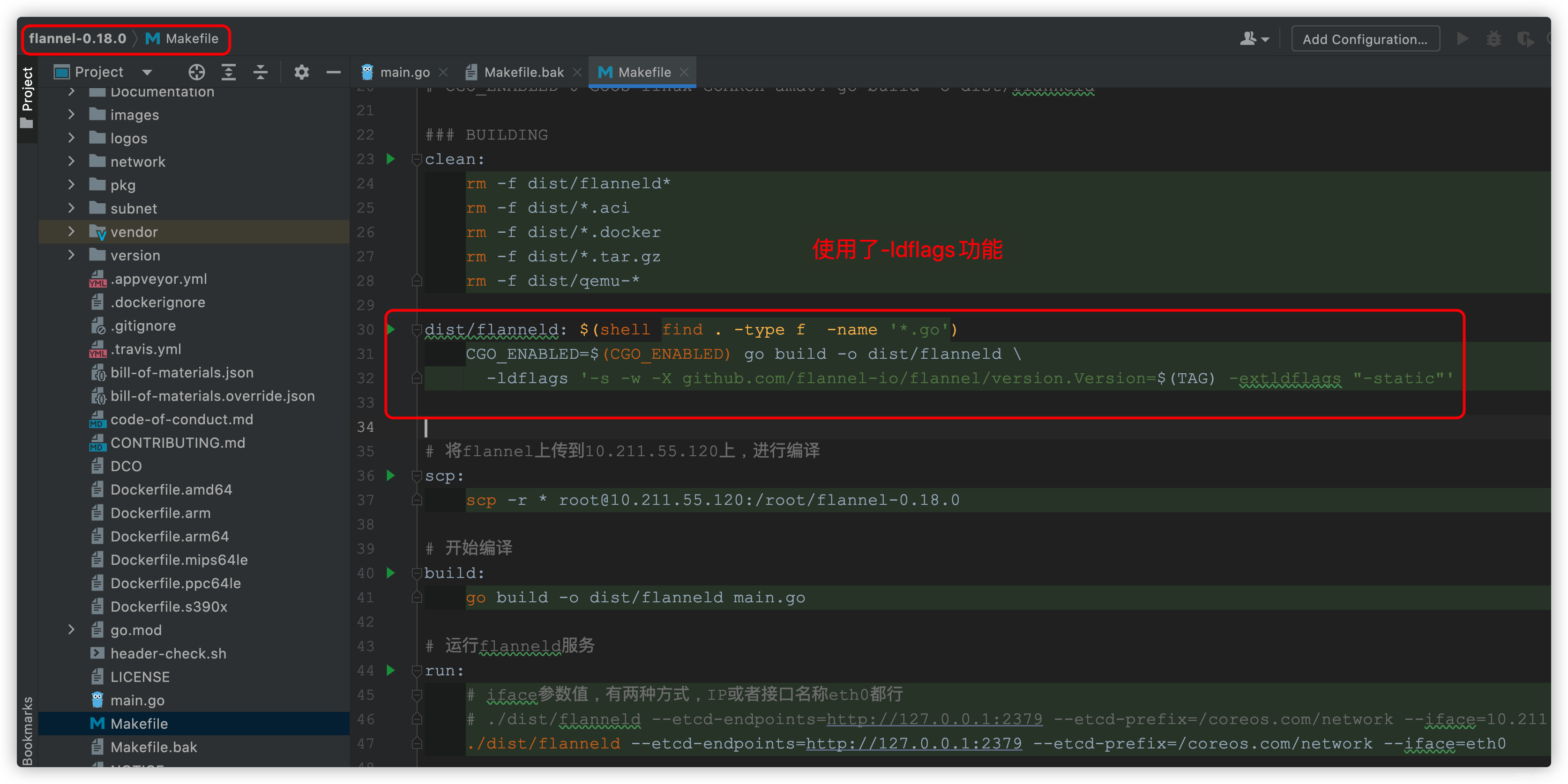
Golang compilation constraint / conditional compilation (/ / +build < tags>)

Give full play to the wide practicality of maker education space
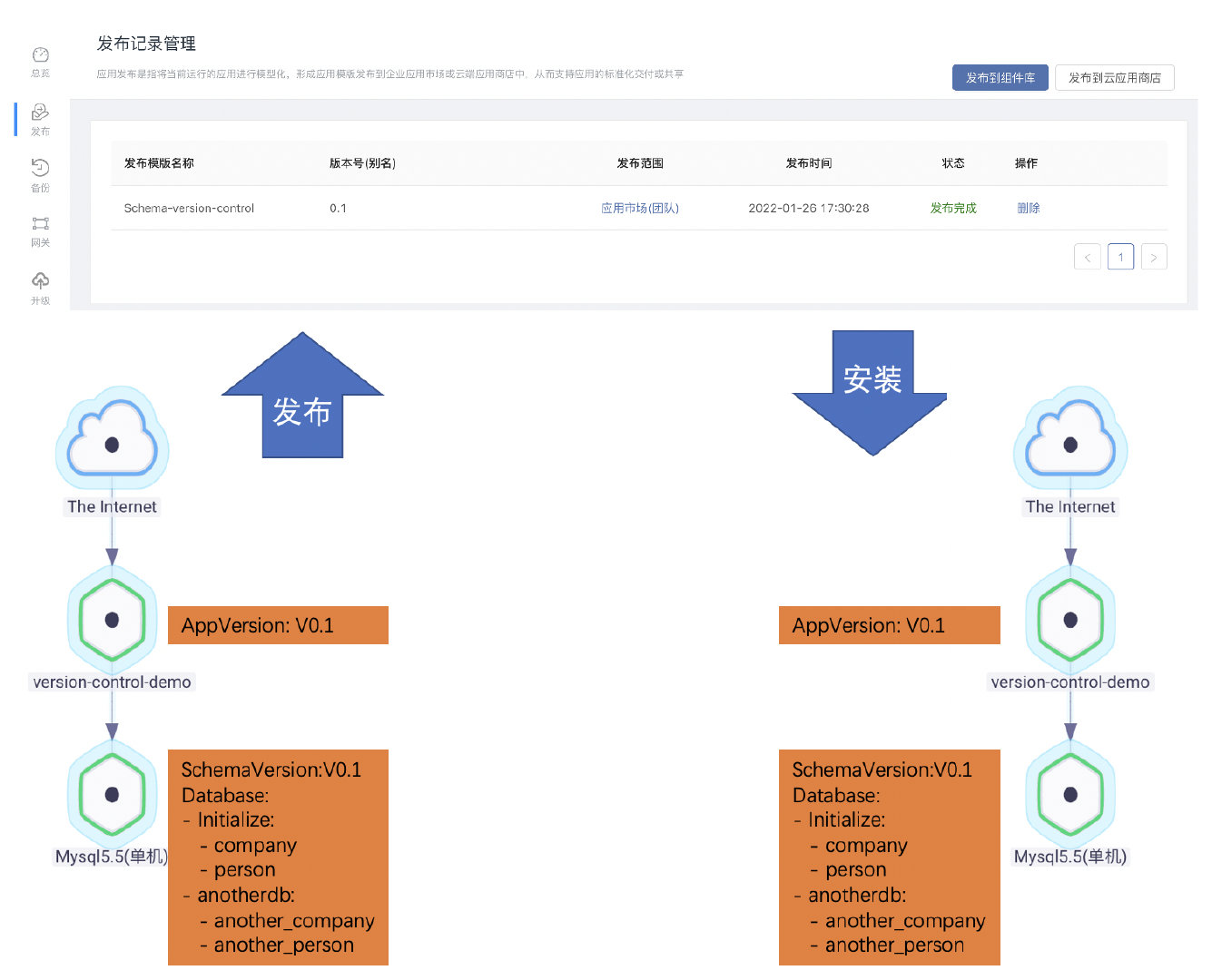
Automatic upgrading of database structure in rainbow
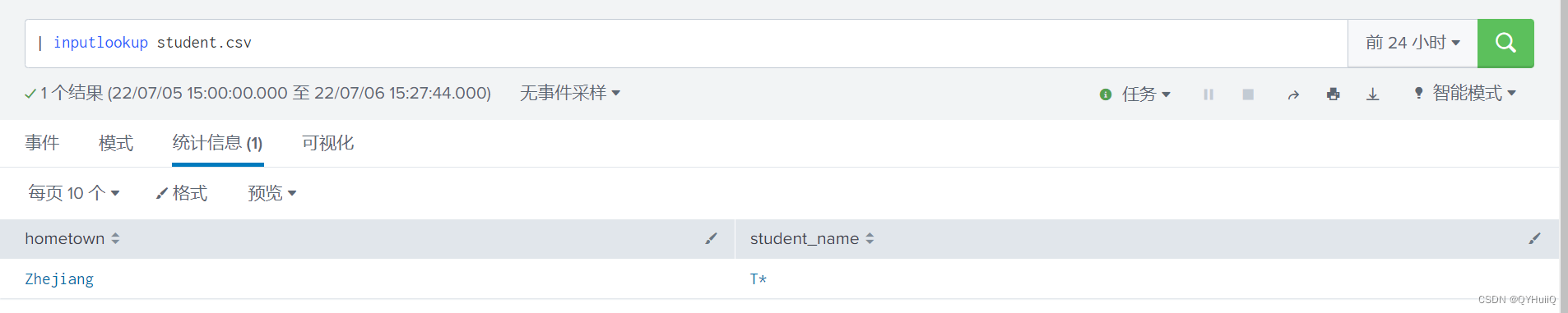
The field value in Splunk subquery fuzzy matching CSV is*
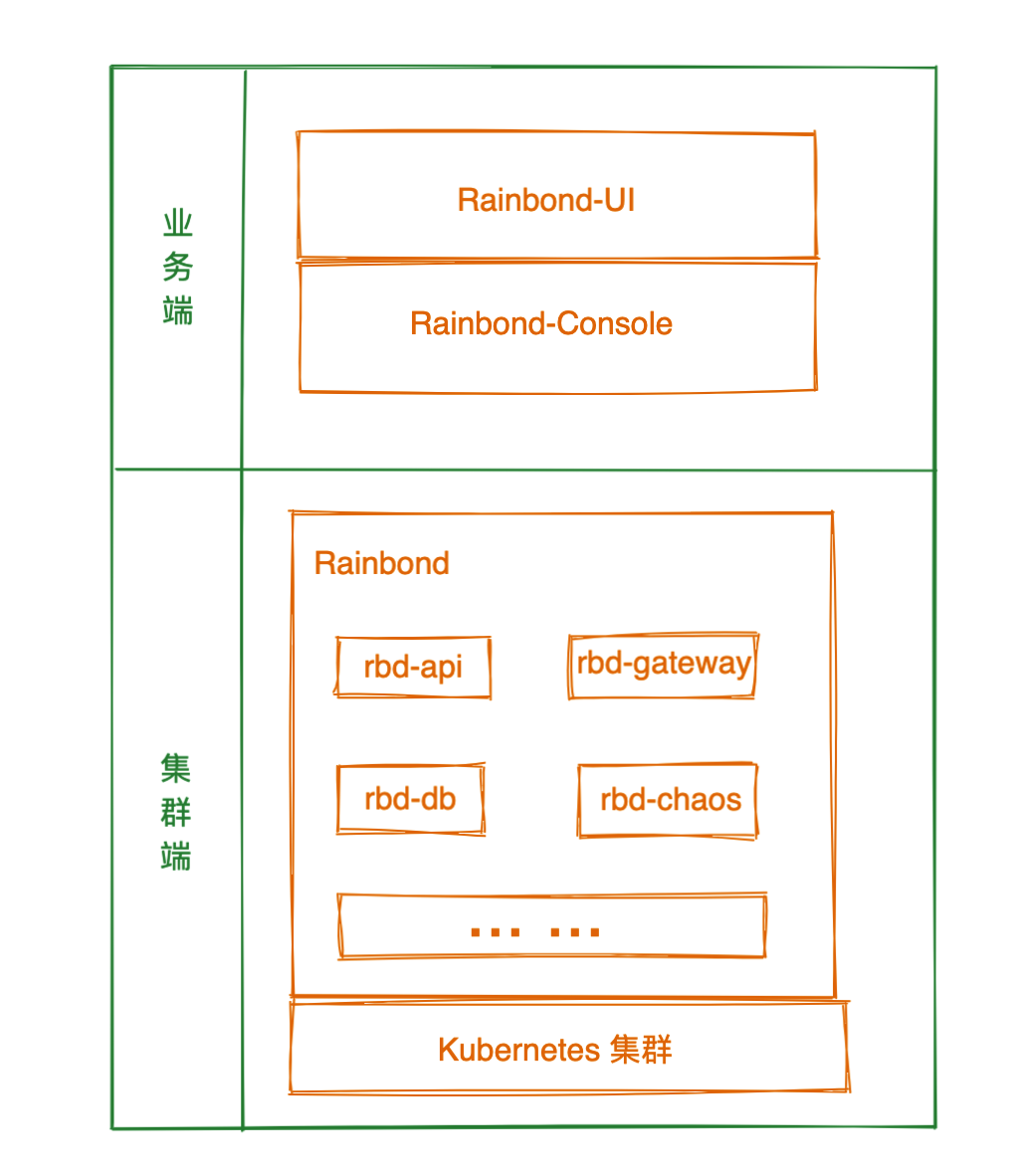
Learn how to compile basic components of rainbow from the source code
Lua 编程学习笔记

发挥创客教育空间的广泛实用性

Implementation of navigation bar at the bottom of applet
随机推荐
2-3 lookup tree
下载和安装orcale database11.2.0.4
Opencv learning notes II - basic image operations
IELTS review progress and method use [daily revision]
PLSQL的安装和配置
opencv学习笔记三——图像平滑/去噪处理
Input of mathematical formula of obsidan
Openvscode cloud ide joins rainbow integrated development system
CCTV is so warm-hearted that it teaches you to write HR's favorite resume hand in hand
BiSeNet的特点
[hard core science popularization] working principle of dynamic loop monitoring system
Data type - integer (C language)
POJ - 3784 running medium
Snyk dependency security vulnerability scanning tool
[IELTS speaking] Anna's oral learning records part2
2 - 3 arbre de recherche
IP guard helps energy enterprises improve terminal anti disclosure measures to protect the security of confidential information
2-3查找树
XCiT学习笔记
Virtual address space