当前位置:网站首页>Easy to understand SSO
Easy to understand SSO
2022-07-07 08:12:00 【Extraordinary~】
One 、cookie And session
Before you know it , Let's first understand the following knowledge :「cookie And session」
See this introduction for details
Two 、 Common login authentication mechanism
The process of ordinary login authentication mechanism :
- Users access a system , This system requires login , Then send a login request to the background server ;
- The database judges according to the user name and password sent by the user , Complete login authentication after judging success , Login authentication successful , The server writes the user's login information to session;
- The server generates a cookie, Go back and write to the browser ;
- The next time , When the user accesses the system again , The request will be accompanied by this cookie, The server will follow this cookie Find the corresponding session, adopt session To determine whether this user has logged in .

If there is only one or two systems , This common login authentication mechanism can still meet the needs , however , If in a multi system environment , When operating different systems , You need to log in multiple times , This way becomes very inconvenient , And when clicking login is to solve this situation .
3、 ... and 、 What is? SSO?
Single sign on ( English :Single sign-on, Abbreviation for SSO), Single check in , One for many interrelated , But they are independent software systems , Provide access control properties . When you have this property , When the user logs in , You can get access to all systems , You don't have to log in to every single system .
The short answer is , In a multi system environment , Users only need to log in once , You can log in and access other mutually trusted systems at the same time .
Four 、SSO The advantages of
Benefits of using single sign on :
- Reduce the risk of visiting third-party websites ( User passwords are not stored or externally managed );
- Reduce password fatigue from different combinations of user names and passwords ;
- Reduce the time it takes to re-enter the same identity with the password ;
- Reduce IT Reduce the cost appropriately IT Help desk calls about password ;
- SSO All other applications and systems in the collection , Used for authentication of the authentication server , It is combined with technology to ensure that users do not have to actively enter credentials more than once .
5、 ... and 、 Single sign on in different scenarios
5.1 Sympatric SSO
At this time, both systems are under the same domain name , Differentiate different systems through secondary domain names . For example, there is a domain named :jd.com, At the same time, there are two application systems, namely :a.jd.com and b.jd.com.
As shown in the figure below cookie + redis Single sign on 
5.2 Cross domain SSO
Suppose there are three websites , We need to be in the system xiadan And system zhifu Single sign on is realized between the two websites .
xiadan System :www.xiadan.com
zhifu System :www.zhifu.com
SSO System :www.sso.com
SSO The specific process of ( The following steps are consistent with those in the figure )
- The user accesses the system for the first time xiadan,xidan The system needs to log in , But the user is not logged in right now ; Because the user is not logged in , therefore xiadan Server return http Redirect , The redirection of url yes SSO The address of the server , meanwhile url Of query The parameter indicates that after the login is successful , Jump back to xiadan The page of ;
- SSO The server judges that the user is not logged in , Show the user the unified login interface . The user is in SSO Fill in the user name and password on the page of , Log in ;
- SSO After the system is successfully authenticated ,SSO The server creates an authorization token (token), At the same time return to a http Redirect , The browser redirects to the system xiadan:www.xiadan.com. At this point, the redirection of url It's carrying SSO Authorization token generated by the server .
- System xiadan Get the authorization token , towards SSO The server sends the request , Verify whether the token is valid ;
- After successful verification ,xiadan The server knows that the user is already SSO Log on to the , therefore xiadan Server build user login session, Write it down as xiadan session, And will cookie Write to browser ;
- After that, users visit zhifu,zhifu The system is not logged in ; Because the user is not logged in , therefore zhifu Server return http Redirect , The redirection of url yes SSO The address of the server ;
- The browser asks the user in SSO Login status in ,SSO According to the authorization token, the server determines that the user is already SSO Logged in ,SSO The server returns a http Redirect , Carry authorization token , Jump to the system zhifu:www.zhifu.com;
- System zhifu Get the authorization token , towards SSO The server sends the request , Verify whether the token is valid , After successful verification ,zhifu The server knows that the user is already SSO Log on to the , therefore zhifu Server build user login session, Write it down as zhifu session, And will cookie Write to browser .
such ,zhifu The system does not need to enter user name and password for login process , It's login . Then when the user visits xiadan perhaps zhifu after , I'll carry it directly xiadan cookie / zhifu cookie, You don't have to ask SSO Confirmed. .
边栏推荐
- [quickstart to Digital IC Validation] 15. Basic syntax for SystemVerilog Learning 2 (operator, type conversion, loop, Task / Function... Including practical exercises)
- 2022 Inner Mongolia latest advanced fire facility operator simulation examination question bank and answers
- Qinglong panel - today's headlines
- The zblog plug-in supports the plug-in pushed by Baidu Sogou 360
- Li Kou interview question 04.01 Path between nodes
- 复杂网络建模(三)
- ZCMU--1492: Problem D(C语言)
- 云原生存储解决方案Rook-Ceph与Rainbond结合的实践
- 运放电路的反馈电阻上并联一个电容是什么作用
- Recursive method constructs binary tree from middle order and post order traversal sequence
猜你喜欢
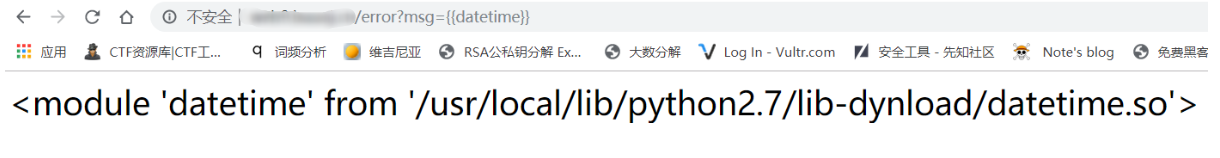
Vulnerability recurrence easy_ tornado

快解析内网穿透为文档加密行业保驾护航
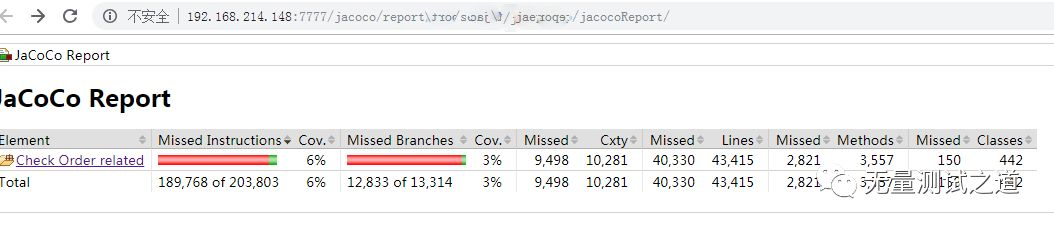
Quickly use Jacobo code coverage statistics

LeetCode简单题之找到一个数字的 K 美丽值
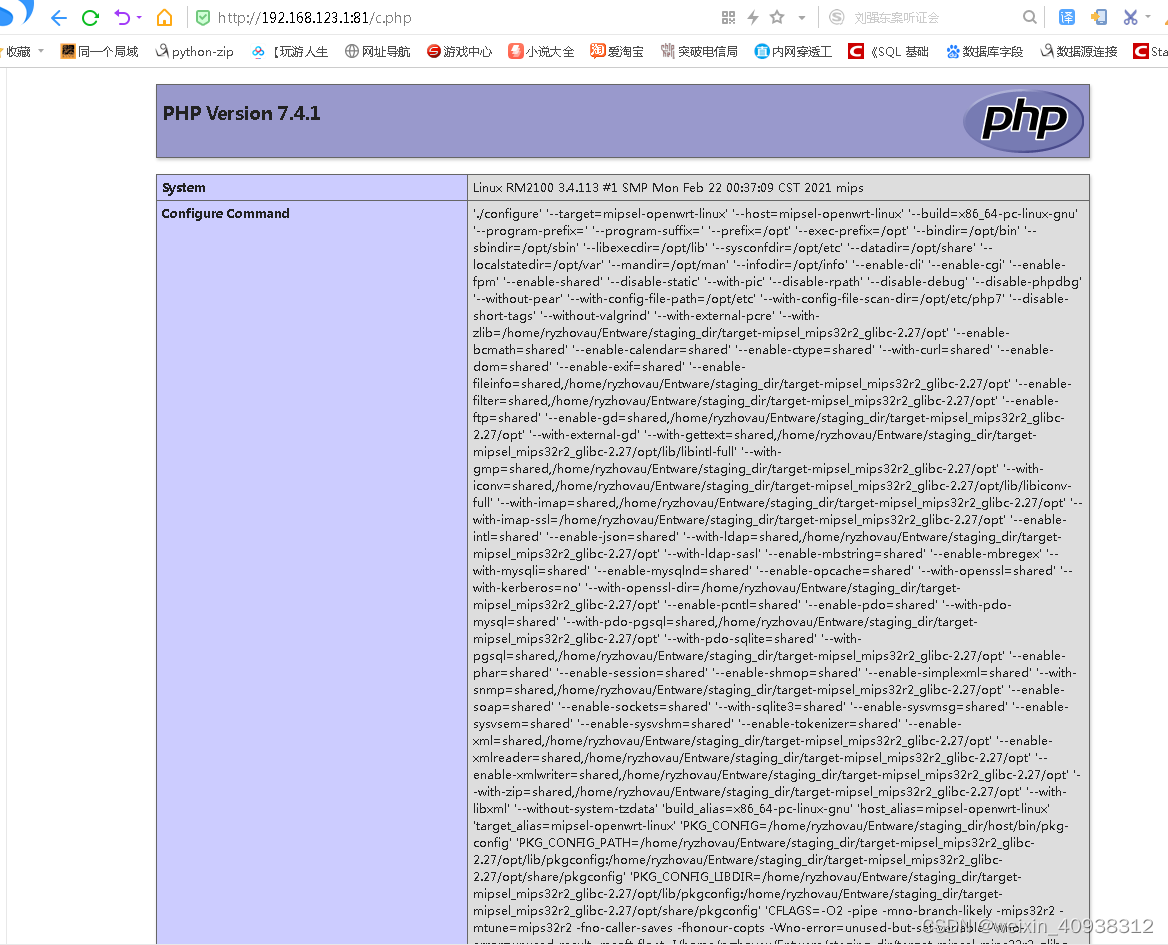
Padavan manually installs PHP
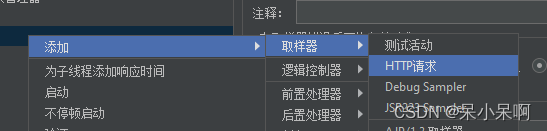
Use of JMeter
game攻防世界逆向
漏洞複現-Fastjson 反序列化
Main window in QT learning 27 application

Interactive book delivery - signed version of Oracle DBA work notes
随机推荐
Example of file segmentation
Bugku CTF daily one question chessboard with only black chess
提高企业产品交付效率系列(1)—— 企业应用一键安装和升级
Yugu p1020 missile interception (binary search)
Hisense TV starts the developer mode
JS复制图片到剪切板 读取剪切板
使用 Nocalhost 开发 Rainbond 上的微服务应用
Padavan manually installs PHP
Linux server development, MySQL transaction principle analysis
buureservewp(2)
Vulnerability recurrence easy_ tornado
OpenVSCode云端IDE加入Rainbond一体化开发体系
B. Value sequence thinking
Network learning (III) -- highly concurrent socket programming (epoll)
Linux server development, MySQL cache strategy
青龙面板-今日头条
Bayes' law
Content of string
Application of slip ring of shipborne radar antenna
Chip information website Yite Chuangxin
