当前位置:网站首页>Central South University | through exploration and understanding: find interpretable features with deep reinforcement learning
Central South University | through exploration and understanding: find interpretable features with deep reinforcement learning
2022-07-03 16:28:00 【Zhiyuan community】
【 title 】Understanding via Exploration: Discovery of Interpretable Features With Deep Reinforcement Learning
【 The author team 】Jiawen Wei, Zhifeng Qiu, Fangyuan Wang, Wenwei Lin, Ning Gui, Weihua Gui
【 Date of publication 】2022.6.28
【 Thesis link 】https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9810174
【 Recommended reasons 】 Understanding the environment through interaction has become one of the most important intellectual activities for human beings to master unknown systems . as everyone knows , Deep reinforcement learning (DRL) In many applications, effective control is achieved through human like exploration and utilization . However , Deep neural network (DNN) The opacity of often hides the key information related to control , This is essential for understanding the target system . This paper first proposes a new online feature selection framework , That is, attention feature selection based on two worlds (D-AFS) , To identify the contribution of input to the whole control process . With most DRL The world used in is different ,D-AFS It has both the real world and the distorted virtual world . Newly introduced attention based assessment (AR) The module realizes the dynamic mapping from the real world to the virtual world . The existing DRL The algorithm needs only a little modification , You can learn in the dual world . Through analysis DRL Response in two worlds ,D-AFS It can quantitatively identify the importance of each feature to control .
边栏推荐
- June to - -------
- How to set up SVN server on this machine
- How to use AAB to APK and APK to AAB of Google play apps on the shelves
- SVN使用规范
- 斑马识别成狗,AI犯错的原因被斯坦福找到了
- Q2 encryption market investment and financing report in 2022: gamefi becomes an investment keyword
- Initial test of scikit learn Library
- QT串口ui设计和解决显示中文乱码
- Why does the std:: string operation perform poorly- Why do std::string operations perform poorly?
- Alibaba P8 painstakingly sorted it out. Summary of APP UI automated testing ideas. Check it out
猜你喜欢

【LeetCode】94. Middle order traversal of binary tree
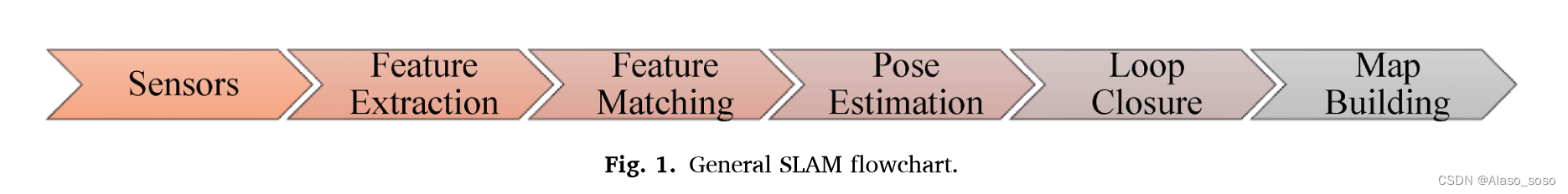
关于视觉SLAM的最先进技术的调查-A survey of state-of-the-art on visual SLAM
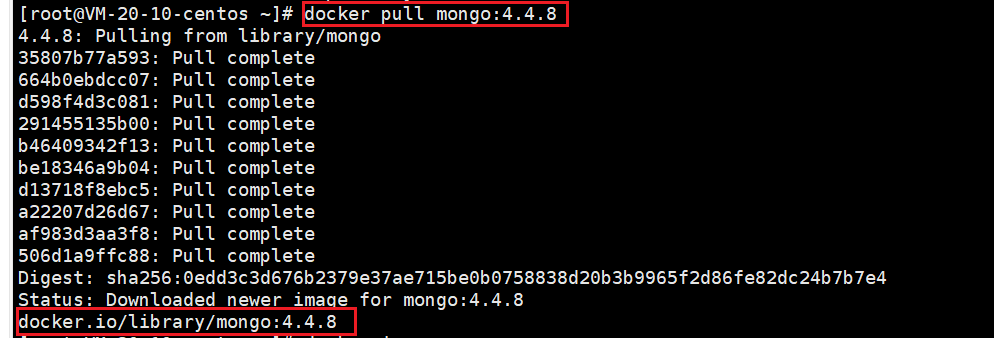
Mongodb installation and basic operation
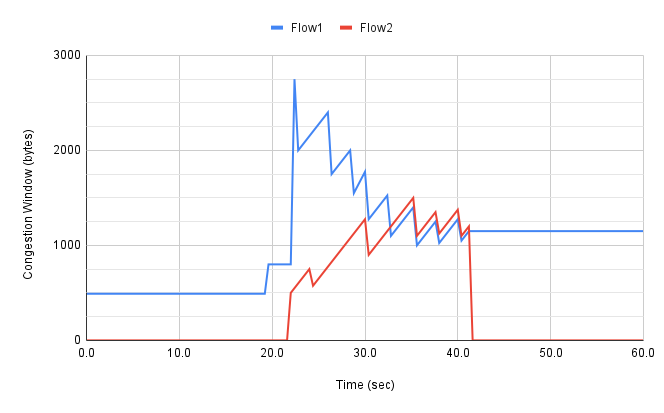
TCP拥塞控制详解 | 3. 设计空间

NSQ源码安装运行过程
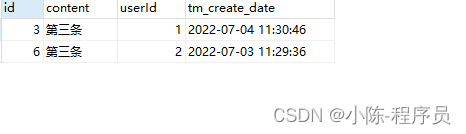
Mysql 单表字段重复数据取最新一条sql语句
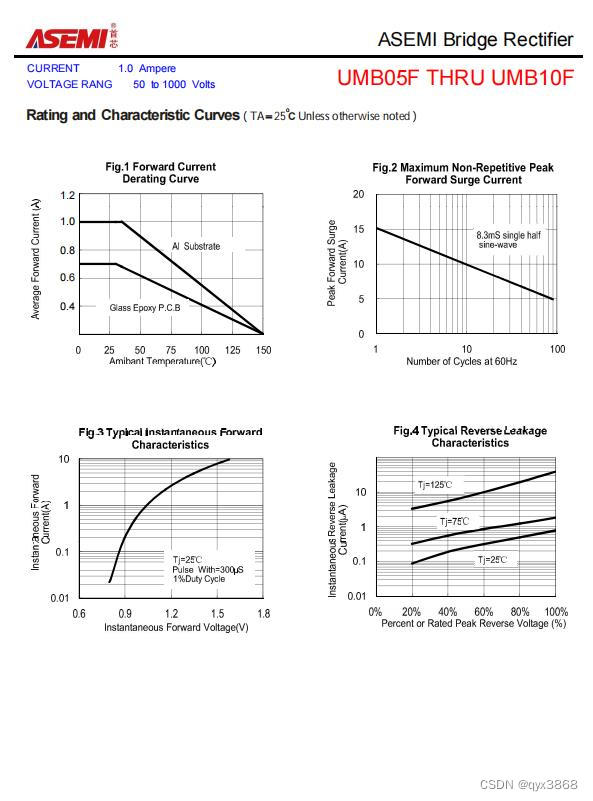
Asemi rectifier bridge umb10f parameters, umb10f specifications, umb10f package

Add color to the interface automation test framework and realize the enterprise wechat test report

Mb10m-asemi rectifier bridge mb10m
为抵制 7-Zip,列出 “三宗罪” ?网友:“第3个才是重点吧?”
随机推荐
切入点表达式
QT串口ui设计和解决显示中文乱码
Netease UI automation test exploration: airtest+poco
Client does not support authentication protocol requested by server; consider upgrading MySQL client
Explore Netease's large-scale automated testing solutions see here see here
Myopia: take off or match glasses? These problems must be understood clearly first
Détails du contrôle de la congestion TCP | 3. Espace de conception
Is it safe to open a stock account by mobile registration? Does it need money to open an account
NFT new opportunity, multimedia NFT aggregation platform okaleido will be launched soon
Develop team OKR in the way of "crowdfunding"
Nifi from introduction to practice (nanny level tutorial) - flow
How can technology managers quickly improve leadership?
斑马识别成狗,AI犯错的原因被斯坦福找到了
PHP CI(CodeIgniter)log级别设置
TCP congestion control details | 3 design space
《天天数学》连载56:二月二十五日
"Remake Apple product UI with Android" (3) - elegant statistical chart
Eleven requirements for test management post
记一次jar包冲突解决过程
面试之 top k问题