当前位置:网站首页>Horizontal ultra vires and vertical ultra vires [easy to understand]
Horizontal ultra vires and vertical ultra vires [easy to understand]
2022-07-02 19:22:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
lateral ultra vires : Horizontal ultra vires refers to the attacker's attempt to access the resources of the user with the same permissions Vertical ultra vires : Vertical override refers to a low-level attacker trying to access the resources of a high-level user
How to prevent horizontal ultra vires loopholes :
- By establishing the binding relationship between users and operable resources , When users operate on any resource , Ensure that the resource is owned by the user through the binding relationship .
- Indirect mapping of key parameters in the request , Avoid using the original key parameter name , For example, using index 1 Instead of id value 123 etc.
How to prevent vertical ultra vires loopholes :
It is recommended to use role-based access control mechanism to prevent vertical over authority attacks , That is, define different permission roles in advance , Assign different permissions to each role , Each user belongs to a specific role , I.e. I have a fixed authority , When a user performs an action or produces an action , Determine whether the action or action is allowed by the user's role .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/148590.html Link to the original text :https://javaforall.cn
边栏推荐
- SIFT特征点提取「建议收藏」
- Digital scroll strip animation
- Binary operation
- R language dplyr package filter function filters dataframe data. If the name of the data column (variable) to be filtered contains quotation marks, you need to use!! SYM syntax processing, otherwise n
- Develop fixed asset management system, what voice is used to develop fixed asset management system
- How to print mybats log plug-in using XML file
- MySQL高级(进阶)SQL语句
- FastDFS安装
- Progress progress bar
- 预处理和预处理宏
猜你喜欢

云呐|为什么要用固定资产管理系统,怎么启用固定资产管理系统

STM32G0 USB DFU 升级校验出错-2

注解开发方式下AutowiredAnnotationBeanPostProcessor的注册时机

How can retail enterprises open the second growth curve under the full link digital transformation
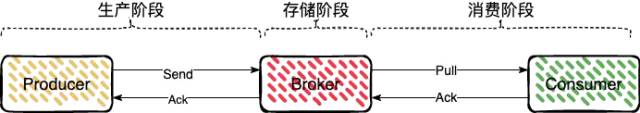
消息队列消息丢失和消息重复发送的处理策略
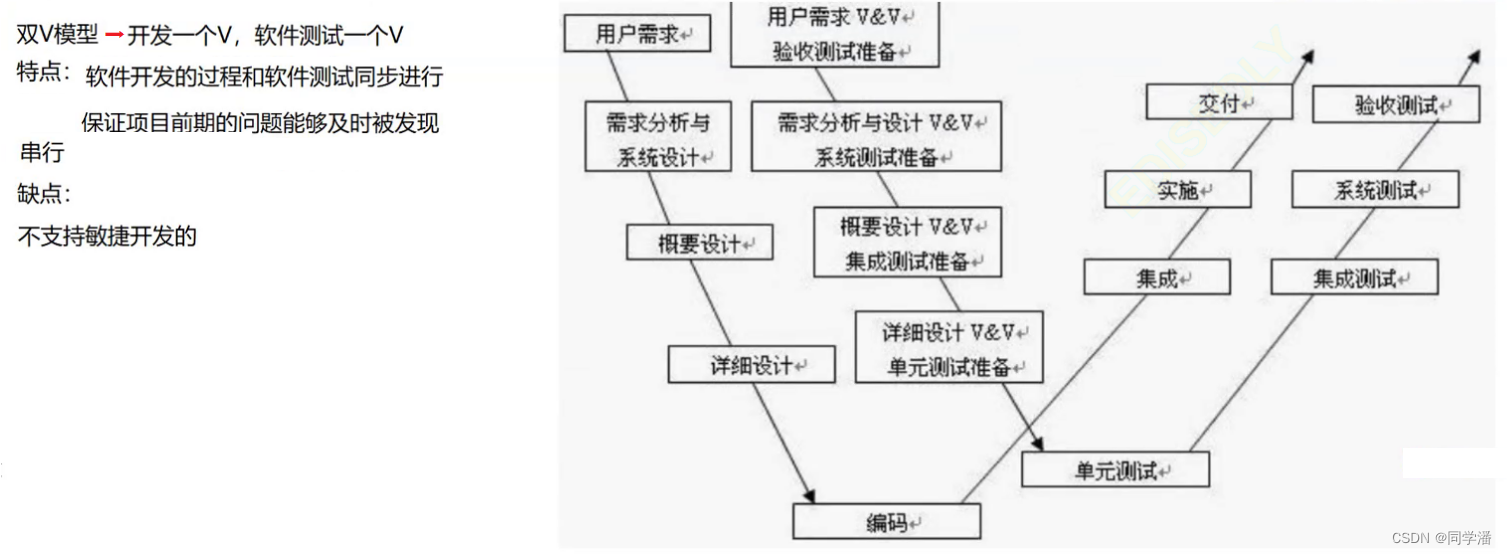
【测试开发】软件测试—概念篇

MySQL advanced learning summary 7: MySQL data structure - Comparison of hash index, AVL tree, B tree and b+ tree
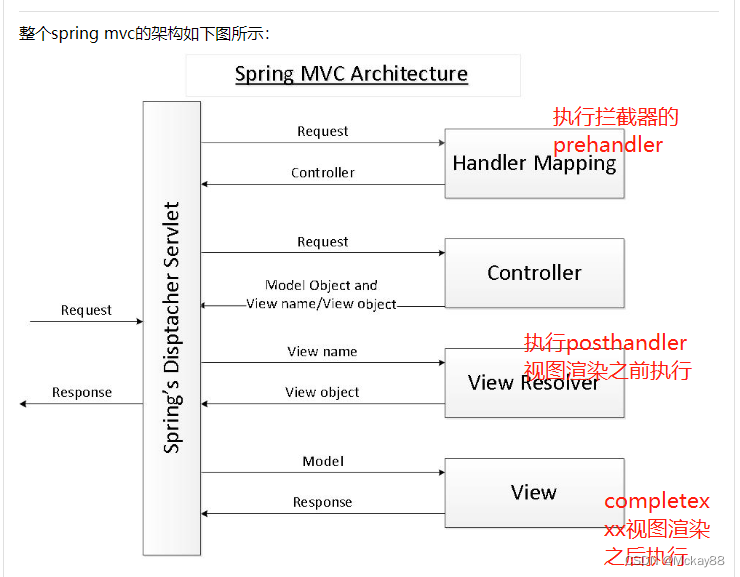
拦截器与过滤器的区别

Why should we build an enterprise fixed asset management system and how can enterprises strengthen fixed asset management
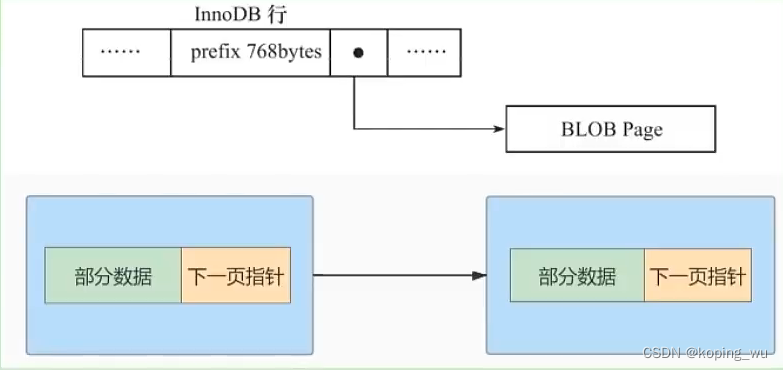
MySQL advanced learning summary 8: overview of InnoDB data storage structure page, internal structure of page, row format
随机推荐
二进制操作
虚拟机初始化脚本, 虚拟机相互免秘钥
Emmet基础语法
Introduction to the paper | application of machine learning in database cardinality estimation
Page title component
以太网PHY层芯片LAN8720A简介
Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5
R language dplyr package filter function filters dataframe data. If the name of the data column (variable) to be filtered contains quotation marks, you need to use!! SYM syntax processing, otherwise n
FastDFS安装
R language uses the lsnofunction function function of epidisplay package to list all objects in the current space, except user-defined function objects
[error record] problems related to the installation of the shuttle environment (follow-up error handling after executing the shuttle doctor command)
【测试开发】一文带你了解什么是软件测试
Hospital online inquiry source code hospital video inquiry source code hospital applet source code
The mybatieshelperpro tool can be generated to the corresponding project folder if necessary
[0701] [论文阅读] Alleviating Data Imbalance Issue with Perturbed Input During Inference
数据降维——主成分分析
高级性能测试系列《24. 通过jdbc执行sql脚本》
[paper reading] Ca net: leveraging contextual features for lung cancer prediction
High frequency interview questions
2022软件工程期末考试 回忆版