当前位置:网站首页>Leetcode ransom letter C # answer
Leetcode ransom letter C # answer
2022-07-04 19:20:00 【charlsdm】
- Ransom letter
Here are two strings :ransomNote and magazine , Judge ransomNote Can it be done by magazine The characters inside make up .
If possible , return true ; Otherwise return to false .
magazine Each character in can only be in ransomNote Used once in .
Example 1:
Input :ransomNote = “a”, magazine = “b”
Output :false
Example 2:
Input :ransomNote = “aa”, magazine = “ab”
Output :false
Example 3:
Input :ransomNote = “aa”, magazine = “aab”
Output :true
Tips :
1 <= ransomNote.length, magazine.length <= 105
ransomNote and magazine It's made up of lowercase letters
Pass times 193,359 Submit the number 306,645
Below is my AC Code
public partial class Solution
{
public static bool CanConstruct(string ransomNote, string magazine)
{
char[] ramchars = ransomNote.ToCharArray();
char[] magachars = magazine.ToCharArray();
List<char> listram = ramchars.ToList<char>();
List<char> listmaga = magachars.ToList<char>();
int CountA = listmaga.Count;
int CountB = listram.Count;
for (int i = 0; i < CountA; i++)
{
char c = listmaga[i];
if (listram.Contains(c))
{
listram.Remove(c);
}
}
if (listram.Count > 0)
{
return false;
}
return true;
}
}
边栏推荐
- Wanghongru research group of Institute of genomics, Chinese Academy of Agricultural Sciences is cordially invited to join
- Go微服务(二)——Protobuf详细入门
- 更安全、更智能、更精致,长安Lumin完虐宏光MINI EV?
- 2022年字节跳动日常实习面经(抖音)
- Using SSH
- sqlserver的CDC第一次查询的能读取到数据,但后面增删改读取不到,是什么原因
- A method of using tree LSTM reinforcement learning for connection sequence selection
- My colleagues quietly told me that flying Book notification can still play like this
- Nature microbiology | viral genomes in six deep-sea sediments that can infect Archaea asgardii
- Detailed explanation of issues related to SSL certificate renewal
猜你喜欢
英特尔集成光电研究最新进展推动共封装光学和光互连技术进步
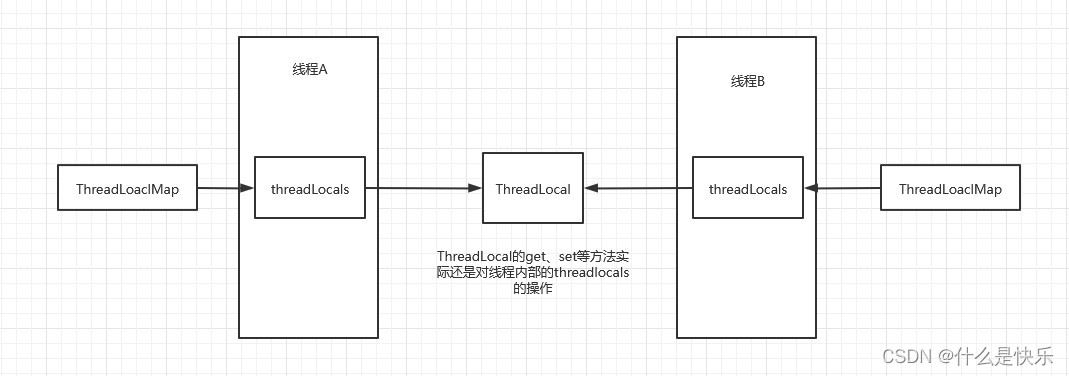
ThreadLocal原理与使用
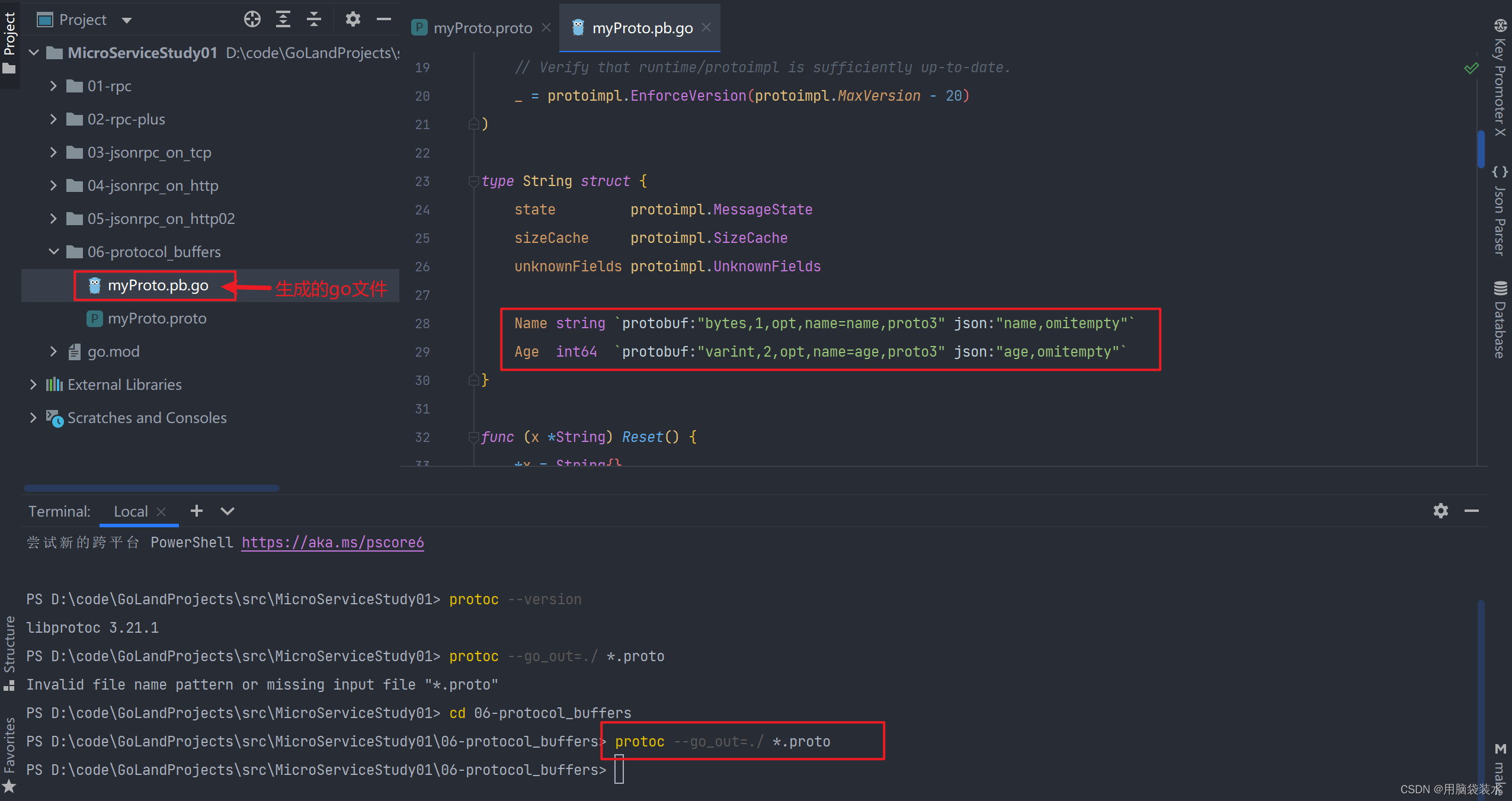
Go microservice (II) - detailed introduction to protobuf

DeFi生态NFT流动性挖矿系统开发搭建
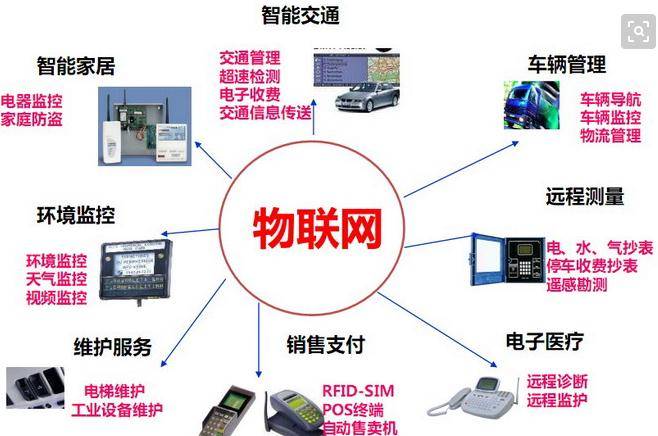
物联网应用技术的就业前景和现状

神经网络物联网是什么意思通俗的解释
Mxnet implementation of googlenet (parallel connection network)
神经网络物联网平台搭建(物联网平台搭建实战教程)
Nebula Importer 数据导入实践
Li Kou brush question diary /day3/2022.6.25
随机推荐
DeFi生态NFT流动性挖矿系统开发搭建
PB的扩展DLL开发(超级篇)(七)
[mathematical basis of machine learning] (I) linear algebra (Part 1 +)
What types of Thawte wildcard SSL certificates provide
数组中的第K个最大元素
2022CoCa: Contrastive Captioners are Image-Text Fountion Models
2019年蜀山区第十五届青少年信息学竞赛
基于unity的愤怒的小鸟设计
How to open an account is safe,
李迟2022年6月工作生活总结
Don't just learn Oracle and MySQL!
Send and receive IBM WebSphere MQ messages
发送和接收IBM WebSphere MQ消息
Installation and use of VMware Tools and open VM tools: solve the problems of incomplete screen and unable to transfer files of virtual machines
奥迪AUDI EDI INVOIC发票报文详解
6.26cf simulation race e: solution to the problem of price maximization
[release] a tool for testing WebService and database connection - dbtest v1.0
Scala基础教程--17--集合
神经网络物联网平台搭建(物联网平台搭建实战教程)
Scala basic tutorial -- 13 -- advanced function