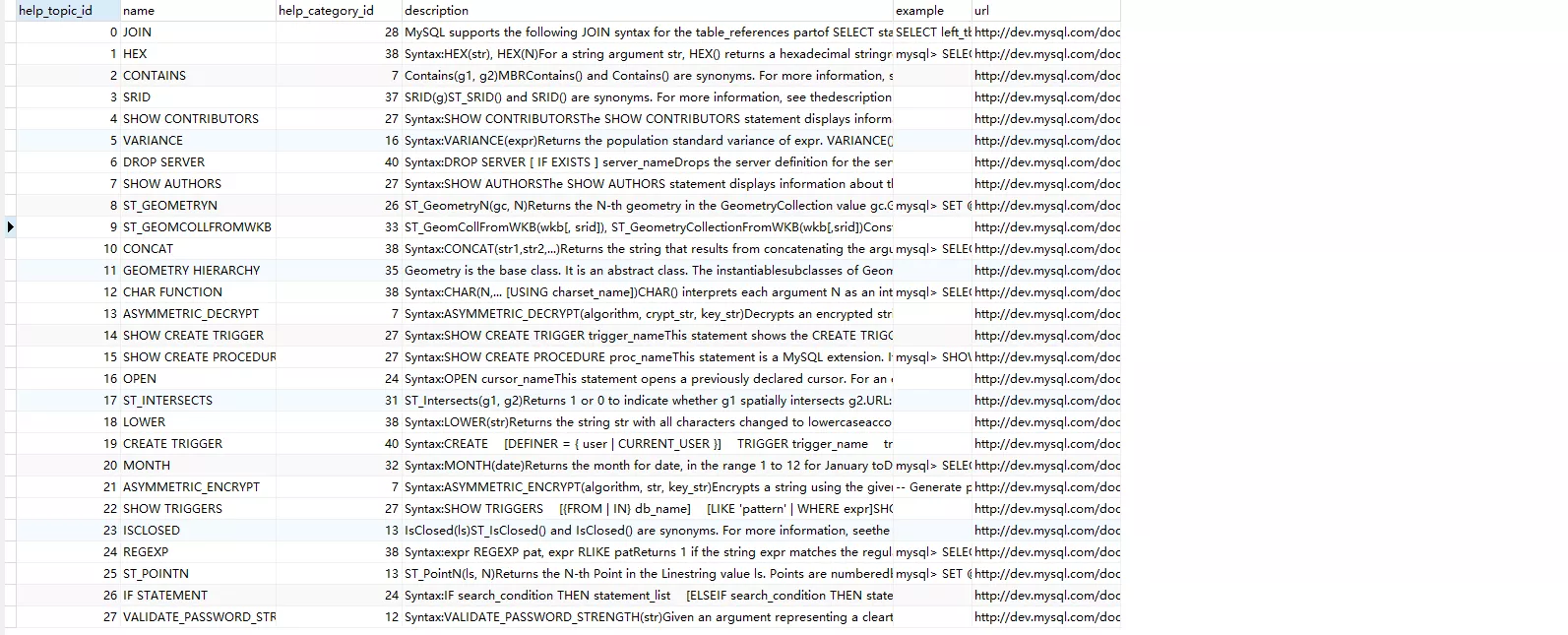
当前位置:网站首页>Design of short chain
Design of short chain
2022-07-06 23:34:00 【OoZzzy】
At present, in many scenarios , All need short chains , Especially involving some URL The logic of distribution . I used to be a pony AI Class business , The link sent by sales through SMS is a short chain . Why need a short chain ? Consider a URL There are path、query Equal parameter , Various parameters are spliced together to form a long string .
List of articles
1. Short chain composition
agreement + domain name + path, The agreement can be directly ignored . Domain name is a must ( crap ), And short enough , Otherwise, it will become a long short chain ( It's silly ). Last path Is the key , It seems to be a 6 A string of characters , And the range of characters is upper and lower case letters + Numbers .
2.Path Generation
2.1 The hash algorithm
Path One of the ways is to calculate by hash algorithm . Common hash functions are MD5、SHA1 And other common cryptographic hash algorithms , Also have HighwayHash、MurmurHash And other non encrypted hash functions . With MurmurHash For example , It has been iterated to MurmurHash 3, Capable of producing 32bit and 128 bit Hash value of , And for those with strong regularity key, The characteristics of random distribution are very good .
However, hash conflicts are uncontrollable , Although we have N A way to resolve hash conflicts , But it will increase the overall complexity of the whole system .
2.2 Self increasing ID
You can also maintain one ID Auto generator , For each long chain generation 1、2、3 And so on , Then save the mapping of long chain and serial number in the database , Then get such as https://fake.short/1、https://fake.short/2 Equal short chain . Considering that a single machine is easy to cause a single point of failure , So it is generally distributed ID generator .
- Mysql
- SnowFlake
- UidGenerator Baidu
- Leaf Meituan
2.3 Further shortening
If we get 『1536389934』 This serial number , It still looks a little long , If you want to further shorten , You can convert decimal numbers into 62 Hexadecimal number . Then you get a shorter number than the original ID 了 .
Why use 62 Hexadecimal conversion ?
62 Base conversion is because 62 After binary conversion, only numbers are included + A lowercase letter + Capital . and 64 The base conversion will contain /,+ Such symbols ( It's not normal URL The characters of )encodeURIComponent(‘+’) => %xx
10 Turn into the system 62 Hexadecimal can shorten characters , If we want to 6 Bit words , There has been a 560 Billion combinations .
边栏推荐
- Experiment 5: common automation libraries
- COSCon'22 社区召集令来啦!Open the World,邀请所有社区一起拥抱开源,打开新世界~
- Use mitmproxy to cache 360 degree panoramic web pages offline
- Experiment 4: installing packages from Gui
- AI金榜题名时,MLPerf榜单的份量究竟有多重?
- js对JSON数组的增删改查
- Gradle知识概括
- Where does this "judge the operation type according to the op value and assemble SQL by yourself" mean? It means simply using Flink tab
- Station B Big utilise mon monde pour faire un réseau neuronal convolutif, Le Cun Forward! Le foie a explosé pendant 6 mois, et un million de fois.
- (1)长安链学习笔记-启动长安链
猜你喜欢
Station B Big utilise mon monde pour faire un réseau neuronal convolutif, Le Cun Forward! Le foie a explosé pendant 6 mois, et un million de fois.
Example code of MySQL split string as query condition
【无人机】多无人协同任务分配程序平台含Matlab代码

快手的新生意,还得靠辛巴吆喝?
Modules that can be used by both the electron main process and the rendering process
The intranet penetrates the zerotier extranet (mobile phone, computer, etc.) to access intranet devices (raspberry pie, NAS, computer, etc.)

Station B boss used my world to create convolutional neural network, Lecun forwarding! Burst the liver for 6 months, playing more than one million
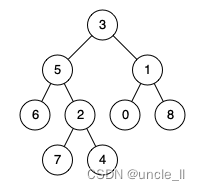
leetcode:236. The nearest common ancestor of binary tree
Résumé des connaissances de gradle
![[communication] optimal power allocation in the uplink of two-layer wireless femtocell network with matlab code](/img/47/741b89d94a2b0003937f32bdedfa19.png)
[communication] optimal power allocation in the uplink of two-layer wireless femtocell network with matlab code
随机推荐
内网穿透zerotier 外网(手机、电脑等)访问内网设备(树莓派、NAS、电脑等)
JDBC programming of MySQL database
Gold three silver four, don't change jobs
Without CD, I'll teach you a trick to restore the factory settings of win10 system
Gradle知识概括
What can be done for traffic safety?
How does crmeb mall system help marketing?
Isomorphism + cross end, knowing applet +kbone+finclip is enough!
Talking about the current malpractice and future development
电脑重装系统u盘文件被隐藏要怎么找出来
Wu Enda 2022 machine learning course evaluation is coming!
leetcode:236. The nearest common ancestor of binary tree
AcWing 4300. Two operations (minimum number of BFS searches)
Realize colorful lines and shape your heart
With the help of this treasure artifact, I became the whole stack
基础图表解读“东方甄选”爆火出圈数据
公链与私链在数据隐私和吞吐量上的竞争
Gpt-3 is a peer review online when it has been submitted for its own research
flinksql select id ,count(*) from a group by id .
食品里的添加剂品种越多,越不安全吗?