当前位置:网站首页>X.509 certificate based on go language
X.509 certificate based on go language
2022-07-07 00:19:00 【biyezuopinvip】
Resource download address :https://download.csdn.net/download/sheziqiong/85926996
Resource download address :https://download.csdn.net/download/sheziqiong/85926996
One 、X.509 Certificate description
In cryptography ,X.509 Is the format standard of public key certificate , It has been applied in many Internet protocols .X.509 Format of public key certificate , Revocation certificate list (CRLs), The certificate verification path algorithm is specified .
One X.509 The certificate contains its version number , Certificate serial number , Signature algorithm , Issuer , Certificate subject , The period of validity , Public key , Public key and other information . The information in the certificate is used ASN.1 Encoding ,ASN.1 The data in this paper is represented by tag, length , Value . The basic structure of the certificate is RFC 5280 in 4.1 Section has the following provisions :
Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING
}
( Certificate subject , Signature algorithm and signature value )
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,
-- If present, version MUST be v2 or v3
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,
-- If present, version MUST be v2 or v3
extensions [3] EXPLICIT Extensions OPTIONAL
-- If present, version MUST be v3
}
( Certificate subject , Include version number , Serial number , Signature algorithm identification , Signer information , The period of validity , Certificate subject , Certificate public key information , Issuer ID, The main body ID And extension segment )
Version ::= INTEGER { v1(0), v2(1), v3(2) }
( Certificate version , The value can be 0,1,2, Each represents version 1,2,3)
CertificateSerialNumber ::= INTEGER
( Certificate serial number )
Validity ::= SEQUENCE {
notBefore Time,
notAfter Time
}
( The certificate is valid for , It consists of start and end times )
Time ::= CHOICE {
utcTime UTCTime,
generalTime GeneralizedTime
}
UniqueIdentifier ::= BIT STRING
SubjectPublicKeyInfo ::= SEQUENCE {
algorithm AlgorithmIdentifier,
subjectPublicKey BIT STRING
}
( Public key information includes public key algorithm and public key data )
Extensions ::= SEQUENCE SIZE (1..MAX) OF Extension
Extension ::= SEQUENCE {
extnID OBJECT IDENTIFIER,
critical BOOLEAN DEFAULT FALSE,
extnValue OCTET STRING
-- contains the DER encoding of an ASN.1 value
-- corresponding to the extension type identified
-- by extnID
}
AlgorithmIdentifier ::= SEQUENCE {
algorithm OBJECT IDENTIFIER,
parameters ANY DEFINED BY algorithm OPTIONAL
}
Two 、 Read X.509 certificate
Used in the submitted program Go Language writing and reading X.509 The program , Called Go Linguistic encoding/asn1 library ASN.1 Reading of encoded content and crypto/x509/pkix The library reads the issuer and certificate subject information .
In the code, according to the above X.509 The certificate structure defines the following structure for ASN.1 Read :
- CertificateData, Corresponding to Certificate:
type CertificateData struct {
TBSCertificate tbsCertificate
SignatureAlgorithm AlgorithmIdentifier
SignatureValue asn1.BitString
}
- TbsCertificate, Corresponding to TBSCertificate:
type tbsCertificate struct {
Version int `asn1:"optional,explicit,default:0,tag:0"`
SerialNumber *big.Int
Signature AlgorithmIdentifier
Issuer asn1.RawValue
Validity timeSpan
Subject asn1.RawValue
PublicKey publicKeyInfo
UniqueId asn1.BitString `asn1:"optional,tag:1"`
SubjectUniqueId asn1.BitString `asn1:"optional,tag:2"`
Extensions []extension `asn1:"optional,explicit,tag:3"`
}
- timeSpan, Corresponding to the above structure Validity:
type timeSpan struct {
NotBefore, NotAfter time.Time
}
- publicKeyInfo, Corresponding to the above SubjectPublicKeyInfo:
type publicKeyInfo struct {
Algorithm AlgorithmIdentifier
PublicKey asn1.BitString
}
- extension, Corresponding to the above structure Extension
type extension struct {
ExtnID asn1.ObjectIdentifier
Critical bool `asn1:"default:false"`
ExtnValue []byte
}
- AlgorithmIdentifier, Corresponding to the above AlgorithmIdentifier:
type AlgorithmIdentifier struct {
Algorithm asn1.ObjectIdentifier
Parameters asn1.RawValue `asn1:"optional"`
}
3、 ... and 、 Brief description of program structure
The submitted code contains three code files :x509cert/certificate.go It is the definition of the certificate structure and the identification function of the algorithm in the certificate , And define the following certInfo The structure is convenient for other codes to obtain certificate information :
type CertInfo struct {
Version int
Serial *big.Int
Signature AlgorithmIdentifier
Issuer IssuerType
Validity timeSpan
Subject IssuerType
PublicKey publicKeyInfo
UniqueId asn1.BitString
SubjectUniqueId asn1.BitString
Extensions []extension
SignatureAlgorithm AlgorithmIdentifier
SignatureValue asn1.BitString
}
type IssuerType struct {
Country string
Province string
City string
Organization string
Unit string
}
x509cert/static.go The file contains some static data during the certificate reading process, such as the name of the algorithm and oid etc. .
main.go The file contains the main function of the program , Based on the pem Format or DER Read the file in format and print the certificate information to standard output .
Four 、 Program compilation run results
Program usage go Compile , Execute the command under the code directory go build –o x509 It can be compiled and generated and named x509 The executable of . The submitted bin The folder already contains the use go1.11.1 Compiled Windows,MacOS as well as Linux The executable under .
The use method of the program is :
./x509 [--DER] filename
If DER Options , Then the program will use DER Way to read the certificate , If not specified, the program will use PEM Way to read the certificate .
The certificate used in the test run is openssl Generate self signed root certificate , The order is as follows :
openssl req -new -x509 -days 365 -keyout rsa.key -out rsa.pem
After the command is executed, you need to enter the certificate subject information :

Using this command will use RSA The validity period of algorithm signature generation is 365 Root certificate of days , Use the certificate tool provided by the system to view the certificate information as follows :
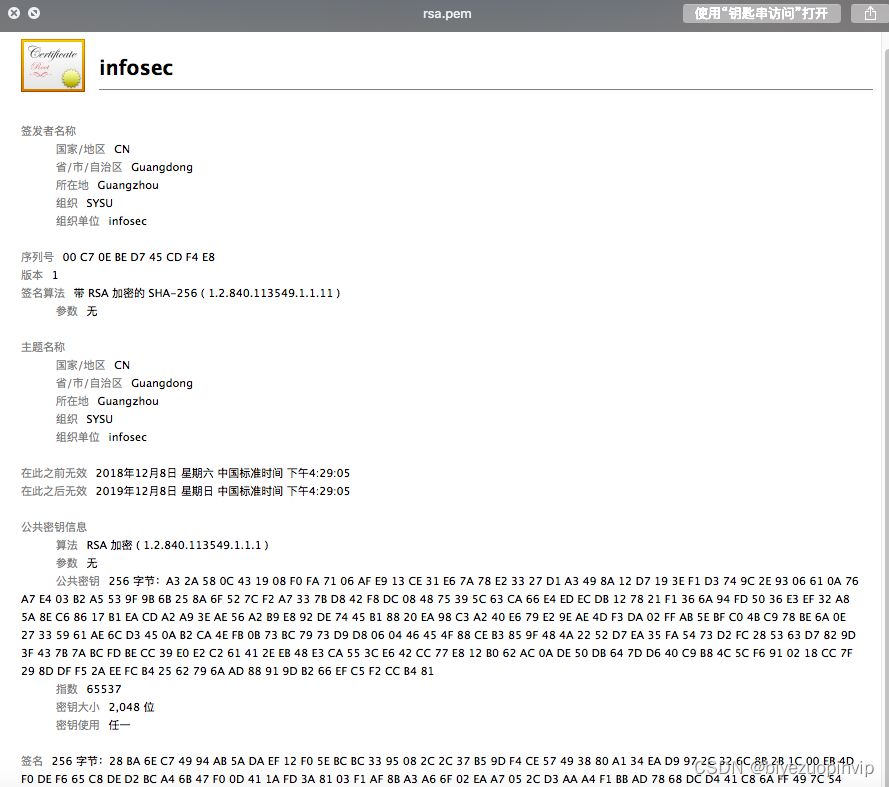
Use the following command to generate pem Certificate to DER Certificate for testing :
openssl x509 -in rsa.pem -outform der -out rsa.crt
Generated after conversion rsa.crt Certificate file , The viewing result is the same as the original certificate .
Use the following command to generate ECDSA The certificate of the signing algorithm is used for testing :
openssl ecparam -name secp256k1 -genkey -param_enc explicit -out ecparam.pem
openssl req -new -x509 -key ecparam.pem -out ec.pem -days 365
Enter the certificate subject information to generate a certificate :
The effect of using the written program to execute under the certificate directory is shown in the figure :
- rsa.pem
./…/bin/x509-darwin-amd64 rsa.pem
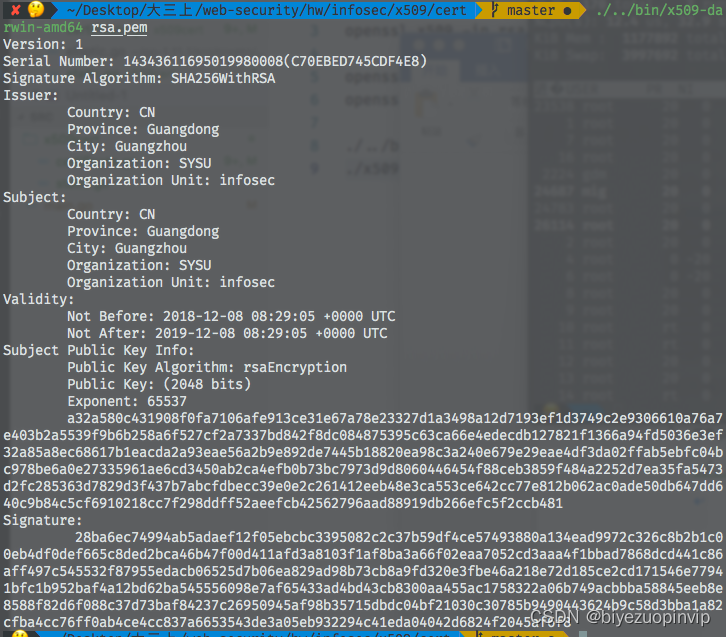
The program displays the version number of the certificate , Serial number , Signature algorithm , Issuer , The main body , The period of validity , Public key information ,RSA Public key data and certificate signature , The content of the certificate displayed by the system tool is the same .
- Use DER The result of reading the certificate file is shown in the figure :
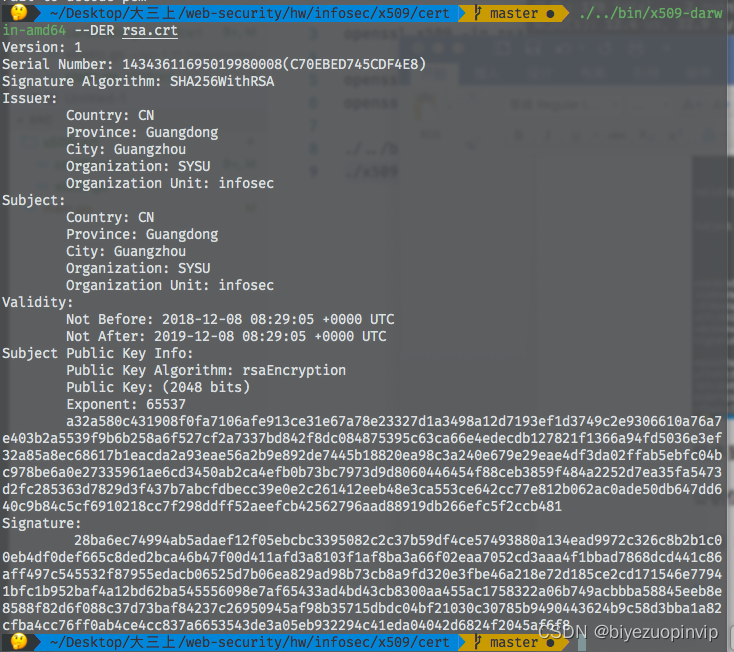
And PEM The result of certificate reading in mode is the same .
- Read ecdsa The encrypted certificate results are as follows :
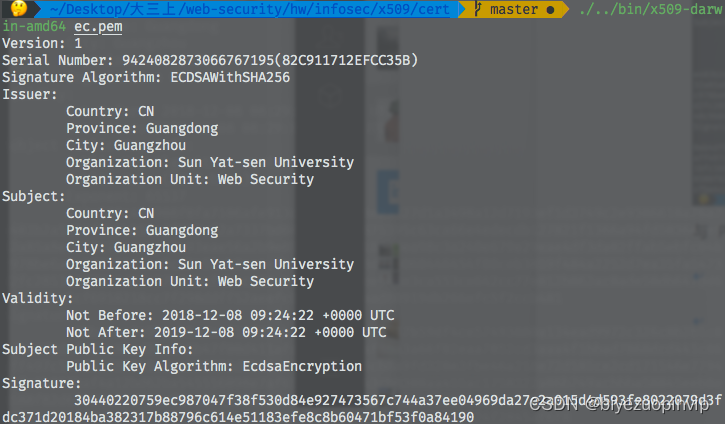
The same information as when generating the certificate .
Resource download address :https://download.csdn.net/download/sheziqiong/85926996
Resource download address :https://download.csdn.net/download/sheziqiong/85926996
边栏推荐
- Liuyongxin report | microbiome data analysis and science communication (7:30 p.m.)
- 量子时代计算机怎么保证数据安全?美国公布四项备选加密算法
- System activity monitor ISTAT menus 6.61 (1185) Chinese repair
- Imeta | Chen Chengjie / Xia Rui of South China Agricultural University released a simple method of constructing Circos map by tbtools
- vector的使用方法_vector指针如何使用
- Penetration test --- database security: detailed explanation of SQL injection into database principle
- MATLIB reads data from excel table and draws function image
- SuperSocket 1.6 创建一个简易的报文长度在头部的Socket服务器
- Interface joint debugging test script optimization v4.0
- DAY TWO
猜你喜欢
Close unregistering application XXX with Eureka with status down after Eureka client starts
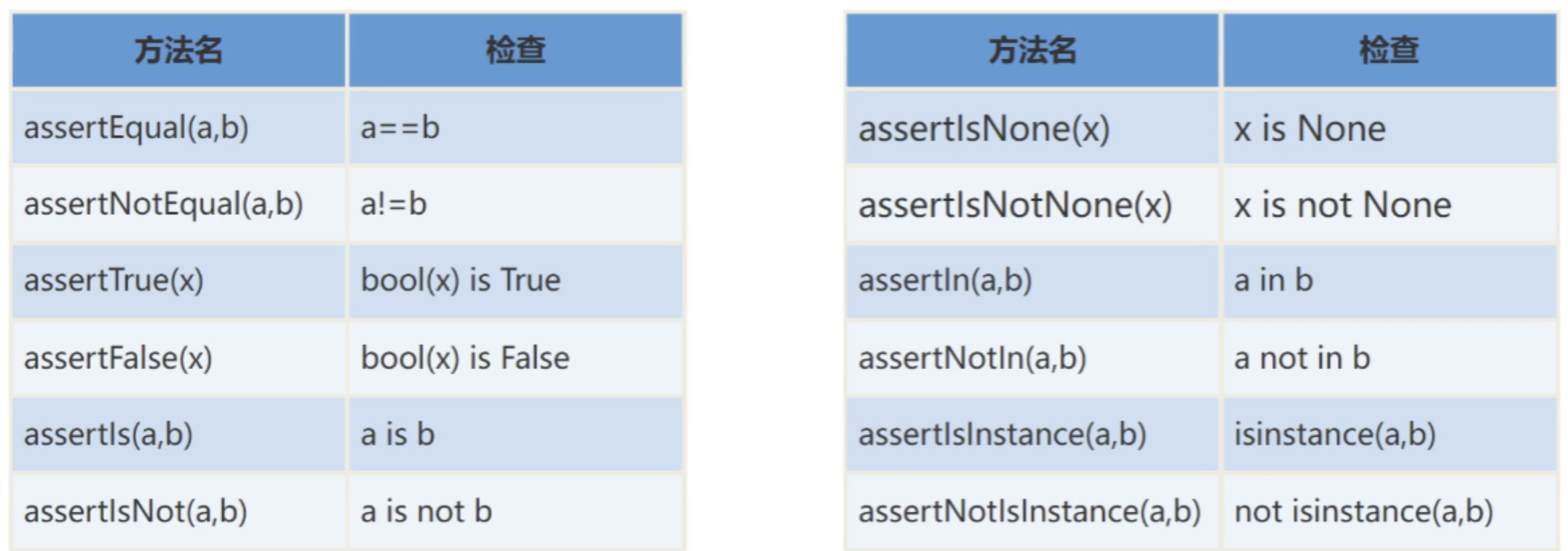
【自动化测试框架】关于unittest你需要知道的事
工程师如何对待开源 --- 一个老工程师的肺腑之言
![[2022 the finest in the whole network] how to test the interface test generally? Process and steps of interface test](/img/8d/b59cf466031f36eb50d4d06aa5fbe4.jpg)
[2022 the finest in the whole network] how to test the interface test generally? Process and steps of interface test

DAY SIX
【精品】pinia 基于插件pinia-plugin-persist的 持久化

37页数字乡村振兴智慧农业整体规划建设方案

48 page digital government smart government all in one solution

What can the interactive slide screen demonstration bring to the enterprise exhibition hall
app通用功能測試用例
随机推荐
GPIO簡介
2022/2/12 summary
DAY FOUR
js导入excel&导出excel
pinia 模块划分
Cas d'essai fonctionnel universel de l'application
C language input / output stream and file operation [II]
Common modification commands of Oracle for tables
Everyone is always talking about EQ, so what is EQ?
ldap创建公司组织、人员
AVL树到底是什么?
Unity color palette | color palette | stepless color change function
Close unregistering application XXX with Eureka with status down after Eureka client starts
What is web penetration testing_ Infiltration practice
Use type aliases in typescript
[vector retrieval research series] product introduction
DAY TWO
Leecode brushes questions to record interview questions 17.16 massagist
DAY FIVE
2022 latest blind box mall complete open source operation source code / docking visa free payment interface / building tutorial