当前位置:网站首页>The programmer resigned and was sentenced to 10 months for deleting the code. Jingdong came home and said that it took 30000 to restore the database. Netizen: This is really a revenge
The programmer resigned and was sentenced to 10 months for deleting the code. Jingdong came home and said that it took 30000 to restore the database. Netizen: This is really a revenge
2022-07-07 00:13:00 【QbitAl】
Dream morning Xiao Xiao From the Aofei temple
qubits | official account QbitAI
The programmer “ Delete the library and run away ” The topic of is on the hot search again , More than 100 million views .
however , This time, the database is not deleted , But myself Code written by yourself !
The client is a 29 Year old programmer , Developed for JD home platform 3 Month code .
The day of leaving , He deleted a series of codes written by himself , Including platform coupons 、 Budget system and subsidy rules .
Take a closer look. , The programmer's departure time happens to be 6 month 18 Japan On the day of jd.com promotion .

In recent days, , The programmer was sentenced to imprisonment ten months .
In addition to these dramatic details , Many onlookers also expressed concern about the extreme behavior when leaving 、 Code permission management and other topics are discussed .
Let's see what's going on .
Private login control platform delete code
According to the criminal judgment of Shanghai Yangpu District People's court ,2021 year 3 month ,29 A year old programmer was recruited Beijing An information technology Co., Ltd , Responsible for the code research and development of JD home platform .
2021 year 6 month 18 Japan , Record a resignation .
On the day of leaving , He has no permission , Log in to the code control platform with your own account ( The server is located in Shanghai ), Send the coupons of jd.com home platform that you wrote during your employment 、 Codes such as budget system and subsidy rules Delete , As a result, relevant projects were forced to postpone .
2021 year 9 month 23 Japan , Lu was caught by the police .

After the incident , In order to ensure the smooth operation of the system , Hire a third-party company to restore the database The total expenditure is about 3 Ten thousand yuan .
And with the help of his family members , compensate for 3.5 Ten thousand yuan and get understanding .
The verdict shows , The defendant recorded a violation of state regulations , Delete the data stored in the computer information system , The consequences are serious , His behavior has constituted Crime of destroying computer information system .
However, after recording someone to the case, he truthfully confessed his crime and voluntarily pleaded guilty , A lighter punishment can be given according to law .
at present , Lu was sentenced to fixed-term imprisonment ten months , The sentence starts with 2021 year 9 month 23 From to 2022 year 7 month 22 Japan .
According to the enterprise investigation , Shanghai Jingdong jiayuanxin Information Technology Co., Ltd. does have a wholly-owned subsidiary in Beijing , Its name is Beijing Daguan Information Technology Co., Ltd .
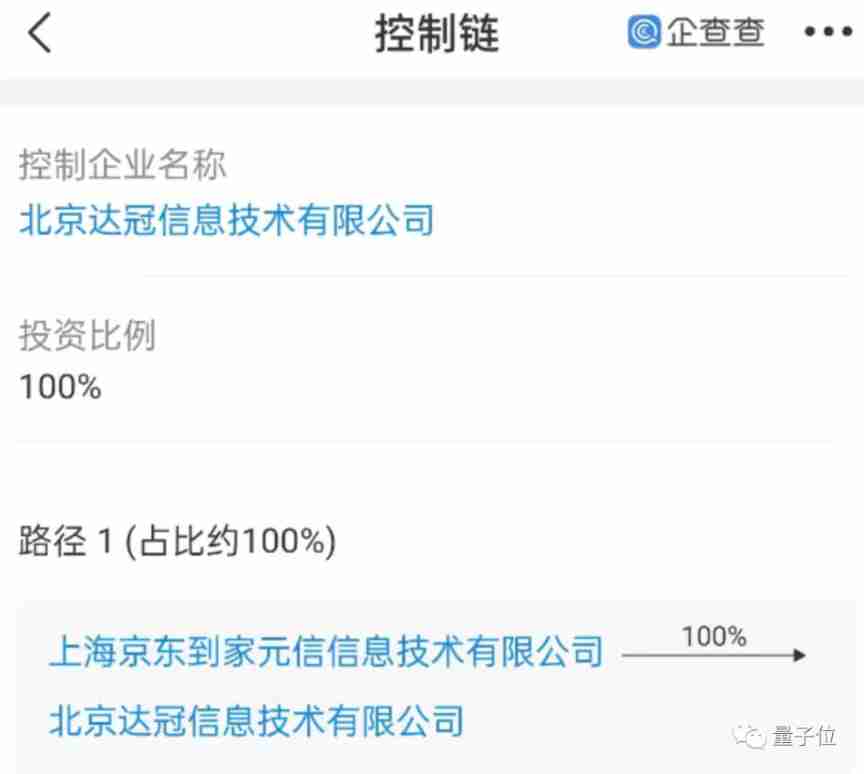
△ Figure source enterprise check
You can see from Liepin , This company is recruiting JD home's back-end development engineers , Responsible for fast iteration of coupon and other systems .
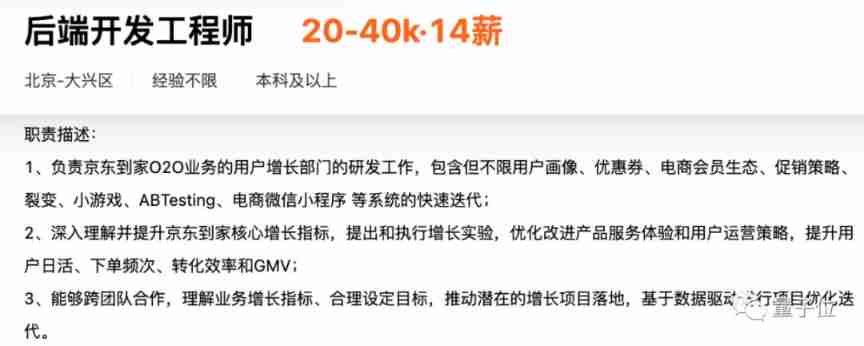
△ Tuyuan Liepin
This case has also triggered a lot of heated discussion among netizens .
Hot discussion among netizens : There are still doubts
It can be seen that , Compared with the previous database deletion and running , This case is somewhat different .
What the defendant recorded was not the production data in the database , It's the code you write during your work .
I understand IT Netizens in the industry found problems from the details , I think there are still some unclear explanations based on the existing information .
such as , What code is deleted .
If it is the code of the production environment , Reasonably speaking, large companies will have strict management methods for code launching , It needs to be reviewed by the same level and superior before it can be merged into the main branch .
Why does this person have so much authority to record someone ?
If it is the code of the development environment , An important function of the code control platform is version management , Whether it's Git It's still a little older SVN Have backup function , You can rollback the deletion .
So why does the company spend 3 Ten thousand yuan, please ask a third party to recover the data ?
in any case , This case reminds you again , The labor achievements during the work period belong to the company according to the contract .
Even the code written by yourself cannot be deleted on impulse , Otherwise, it will only make life more and more critical .
10 Months in prison plus compensation , Leaving a record will have an impact on finding a job in the future , It's not worth .
in addition , There is also an account in the judgment , The defendant can truthfully confess his crime after recording someone in the case , Compensate the victims and obtain understanding , A lighter punishment can be given according to law .
10 Six months in prison , Compared with similar cases that caused a sensation before , It's really light .
Say, say, make, make , Criminal law is no joke
Delete the library and run away , In the early years, it was more a joke of the programmer circle .
The joke is that after deleting the database due to operational errors and other reasons, you can only run away .
Every time “rm -rf /*” As soon as this mysterious code appears , Old drivers will smile .

But in recent years , The same story as this kind of story , It often happens in reality .
The most influential , is 2020 E-commerce at the beginning of the year SaaS Micro League programmers delete libraries , Cause the company's server to fail for as long as 8 God , exceed 300 Merchants were affected , The market value evaporated in just one day 10 $ .
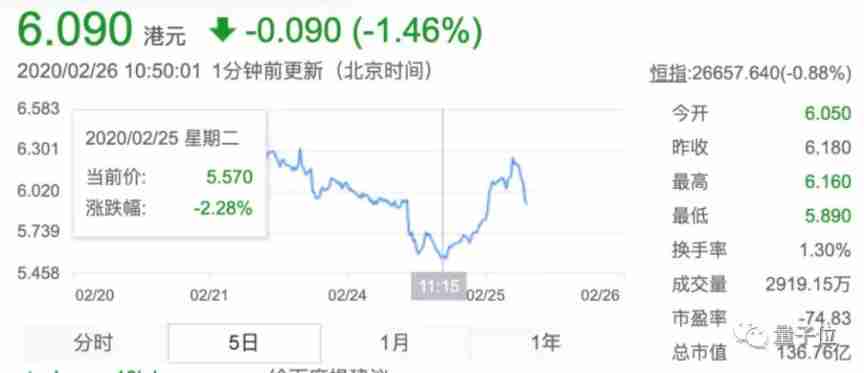
The defendant he in this case finally committed the crime of destroying computer information system , Sentenced to fixed-term imprisonment 6 year .
After this , And then there is 40 Year old chain home program delete their own 9TB The database was judged 7 year , It is also the crime of destroying computer information system .
Crime of destroying computer information system , It is stipulated in Article 286 of our criminal law , Including three crimes .
The first paragraph is about the regulation of destroying the system itself .
Violation of state regulations , Delete the function of computer information system 、 modify 、 increase 、 interfere , Causes the computer information system to be unable to operate normally , With serious consequences , He shall be sentenced to fixed-term imprisonment of not more than five years or criminal detention ; Especially serious , Sentenced to more than five years' imprisonment .
The second paragraph is for data .
Violation of state regulations , Storage in computer information system 、 Delete data and applications processed or transferred 、 modify 、 Added operations , With serious consequences , Punishment in accordance with the provisions of the preceding paragraph .
The last one is destructive programs such as viruses .
Make deliberately 、 Spread computer viruses and other destructive programs , Affect the normal operation of the computer system , With serious consequences , To punish according to the first paragraph .
Besides deleting the code 、 Except for cases such as database deletion , Recently, a developer, Zhang Mou, and his gang were sentenced for remotely punching cards on nails, which also attracted a lot of attention .
Daniel assistant developed by Zhang APP It can destroy the function of the nailing system to obtain the user's real geographical location , And it's paid software , Monthly subscription 25 element , Baonian 89 element .
As of the crime, there are 10 Million users , Benefit about Five million yuan .
The court ruled that Zhang's behavior was in line with the crime of destroying computer information systems “ Make deliberately 、 Spread computer viruses and other destructive programs ”, And the consequences are serious , The First Instance sentenced him to fixed-term imprisonment 5 year 6 Months .
The court of second instance held that “ Daniel's assistant ” Not in criminal law “ destructive program ”, But Zhang still constitutes the crime of destroying computer information system , Change the sentence to fixed-term imprisonment Four years .
in addition , Develop with Daniel's assistant “ plugin ” Similar game plug-ins , You will also get the crime of destroying computer information system .
last year 12 End of month , The defendant Zhou 、 Mr. Sun 、 Yao provided 《 Protogod 》 Game plug-in profit 199.488 Ten thousand yuan , Sentenced separately 4 year 、3 year 10 Months 、1 year 6 Months .
These examples can be seen , Destroy the computer information system , The consequences are quite serious .
As the netizen said , Don't be impulsive , Take the ridicule seriously .
First instance verdict :
http://www.hshfy.sh.cn/shfy/gweb2017/flws_view.jsp?pa=adGFoPaOoMjAyMqOpu6YwMTEw0Myz9TI3usUmd3N4aD0xz
Reference link :
[1]http://www.hshfy.sh.cn/shfy/gweb2017/flws_view.jsp?pa=adGFoPaOoMjAyMaOpu6YwMTA00Myz9TcwObrFJndzeGg9MgPdcssPdcssz
[2]https://weibo.com/7399555658/LeQChtDkM
[3]https://s.weibo.com/weibo?q=%23%E4%BA%AC%E4%B8%9C%E5%88%B0%E5%AE%B6%E7%A8%8B%E5%BA%8F%E5%91%98%E7%A6%BB%E8%81%8C%E5%BD%93%E5%A4%A9%E5%88%A0%E5%BA%93%E8%B7%91%E8%B7%AF%23&Refer=top
[4]https://www.liepin.com/job/1939418135.shtml
边栏推荐
- 【精品】pinia 基于插件pinia-plugin-persist的 持久化
- Unity color palette | color palette | stepless color change function
- Use Yum or up2date to install the postgresql13.3 database
- 2022年PMP项目管理考试敏捷知识点(9)
- Interface joint debugging test script optimization v4.0
- 48页数字政府智慧政务一网通办解决方案
- 1000字精选 —— 接口测试基础
- vector的使用方法_vector指针如何使用
- Automatic test tool katalon (WEB) test operation instructions
- okcc呼叫中心的订单管理时怎么样的
猜你喜欢
17、 MySQL - high availability + read / write separation + gtid + semi synchronous master-slave replication cluster

48页数字政府智慧政务一网通办解决方案
GPIO簡介

Newsletter L Huobi ventures is in-depth contact with genesis public chain

刘永鑫报告|微生物组数据分析与科学传播(晚7点半)
Clipboard management tool paste Chinese version

What can the interactive slide screen demonstration bring to the enterprise exhibition hall

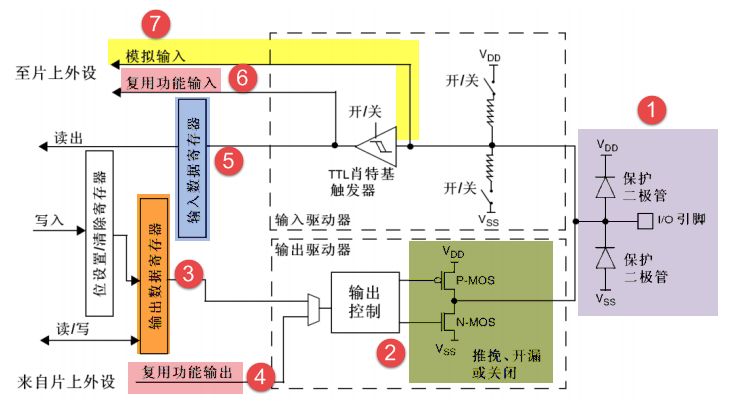
GPIO简介
陀螺仪的工作原理
DAY FOUR
随机推荐
web渗透测试是什么_渗透实战
STM32 enters and wakes up the stop mode through the serial port
三句话简要介绍子网掩码
Do you still have to rely on Simba to shout for a new business that is Kwai?
C语言输入/输出流和文件操作【二】
TypeScript增量编译
Gradle knowledge generalization
Use package FY in Oracle_ Recover_ Data. PCK to recover the table of truncate misoperation
What is AVL tree?
2022/2/11 summary
How to answer the dualistic opposition of Zhihu
Google, Baidu and Yahoo are general search engines developed by Chinese companies_ Baidu search engine URL
Pytest multi process / multi thread execution test case
SQL的一种写法,匹配就更新,否则就是插入
DAY SIX
华为mate8电池价格_华为mate8换电池后充电巨慢
Basic chart interpretation of "Oriental selection" hot out of circle data
C language input / output stream and file operation [II]
js导入excel&导出excel
什么是响应式对象?响应式对象的创建过程?