当前位置:网站首页>Redis6 transaction and locking mechanism
Redis6 transaction and locking mechanism
2022-07-05 13:40:00 【Do you know what a code monster is?】
Catalog
Redis Three characteristics of transaction
Business
Redis A transaction is a separate isolation operation : All commands in the transaction are serialized 、 To execute in order . Transaction is in the process of execution , Will not be interrupted by command requests from other clients .
Redis The main function of a transaction is to concatenate multiple commands to prevent other commands from queuing .
Basic operation
multi Command to form a team , The next input instructions will enter the command queue in turn , But will not execute , Until input exec after ,Redis The previous commands in the command queue will be executed successively .
As shown below :
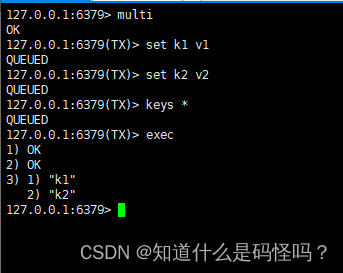
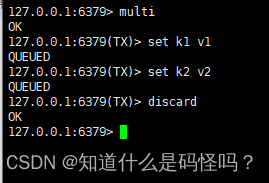
If you want to give up forming a team , Just input discard that will do .
Error mechanism
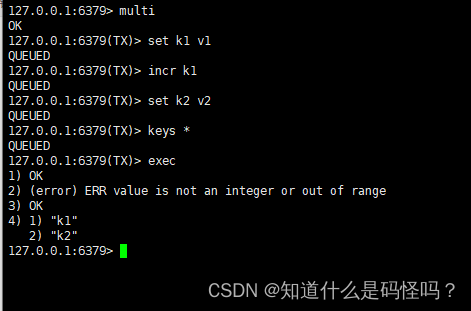
An error occurred while forming a team , All tasks will be canceled during execution .
As shown below :

An error occurred while executing , Only commands that report errors will not be executed , Other commands will be executed , No rollback .
As shown below :
Pessimistic locking
Every time Lock the data every time you get it , In this way, when others take the data, it will block until it is unlocked . There are many lock mechanisms used in traditional relational databases , For example, line locks. , Table lock, etc. , Read the lock , Write locks, etc. , It's all locked before the operation .
Optimism lock
It will not be locked every time you take data , But when updating, we will judge whether others have updated this data during this period , You can use mechanisms such as version numbers to control . Optimistic lock is suitable for multi read applications , This can improve throughput .Redis It's using this check-and-set The mechanism implements the .
monitor key
In execution multi Before , Execute first watch key1 [key2], You can watch one ( Or more ) key , If you're in business This before execution ( Or these ) key Altered by other orders , Then the business will be interrupted .
watch <key>Cancel surveillance
Cancel watch Command to all key Surveillance .
If in execution watch After the command ,exec Order or discard If the order is executed first , Then there's no need to execute unwatch 了 .
unwatchExample :
We are connecting number one and number two at the same time k1 To monitor , And all open transactions . In connection 1, add 100 The operation of , You can find , Connection 1 was successfully executed , Return results :200, Then add... In the second connection 200 The operation of , The result is nil, The reason is because k1 The data of has been modified , Cause the transaction to be interrupted .


Redis Three characteristics of transaction
Separate isolation operation : All commands in the transaction are serialized 、 To execute in order . Transaction is in the process of execution , Will not be interrupted by command requests from other clients .
There is no concept of isolation level : Commands in the queue will not be executed until they are submitted , Because no instruction is actually executed before the transaction is committed .
There is no guarantee of atomicity : If a command fails in a transaction , Subsequent orders will still be executed , No rollback .
Second kill case
Oversold problem
When shopping websites conduct commodity spike activities , In the case of concurrency , Locks need to be set to avoid oversold . for instance , A commodity has 1000 Pieces of , Yes 10000 A person is doing a second kill ,10000 Requests without lock , There will be oversold problems , The inventory of final goods is negative .
Solution
Use optimistic locks to limit , When the inventory of goods changes , Transaction execution failed .
Connection timeout problem
Many users send seckill requests at the same time , There will be a request timeout problem , You need to set the timeout .
Solution
Use connection pool to solve .
Inventory remaining problems
The optimistic lock is used to eliminate the oversold problem , But when a user succeeds in seckill , Someone who kills at the same time as this user , And the people who have succeeded in the second kill in the program due to the change of inventory information , Transactions do not execute . Although this part of people occupy the quota of second kill , But in fact, I didn't buy any goods , Inventory of goods has not decreased , But it took up the number of seconds .
Solution
Use LUA Script , Will be complex or multi-step redis The operation is written as a script , Submit to redis perform , Reduce repeated connections redis The number of times , Lifting performance . also LUA Scripts have a certain atomicity , Will not be interrupted by other orders . Use LUA Scripts solve problems , It's actually redis Take advantage of its single threaded feature , The problem of multi task concurrency is solved by using task queue .
边栏推荐
- 网络安全-HSRP协议
- 私有地址有那些
- TortoiseSVN使用情形、安装与使用
- Aspx simple user login
- Cloudcompare - point cloud slice
- jenkins安装
- Parsing XML using Dom4j
- Aikesheng sqle audit tool successfully completed the evaluation of "SQL quality management platform grading ability" of the Academy of communications and communications
- restTemplate详解
- 使用Dom4j解析XML
猜你喜欢
不知道这4种缓存模式,敢说懂缓存吗?

Summit review | baowanda - an integrated data security protection system driven by compliance and security
Jenkins installation
![[深度学习论文笔记]UCTransNet:从transformer的通道角度重新思考U-Net中的跳跃连接](/img/b6/f9da8a36167db10c9a92dabb166c81.png)
[深度学习论文笔记]UCTransNet:从transformer的通道角度重新思考U-Net中的跳跃连接
What is a network port
Win10 - lightweight gadget
When using Tencent cloud for the first time, you can only use webshell connection instead of SSH connection.
一文详解ASCII码,Unicode与utf-8

Could not set property 'ID' of 'class xx' with value 'XX' argument type mismatch solution
C object storage
随机推荐
Matlab paper chart standard format output (dry goods)
Godson 2nd generation burn PMON and reload system
Address book (linked list implementation)
Write API documents first or code first?
运筹说 第68期|2022年最新影响因子正式发布 快看管科领域期刊的变化
【Hot100】34. 在排序数组中查找元素的第一个和最后一个位置
Summit review | baowanda - an integrated data security protection system driven by compliance and security
How to choose note taking software? Comparison and evaluation of notion, flowus and WOLAI
“百度杯”CTF比赛 九月场,Web:SQL
[深度学习论文笔记]使用多模态MR成像分割脑肿瘤的HNF-Netv2
What happened to the communication industry in the first half of this year?
华为推送服务内容,阅读笔记
The development of speech recognition app with uni app is simple and fast.
go 数组与切片
Can and can FD
JS to determine whether an element exists in the array (four methods)
【MySQL 使用秘籍】一網打盡 MySQL 時間和日期類型與相關操作函數(三)
CAN和CAN FD
leetcode 10. Regular Expression Matching 正则表达式匹配 (困难)
Rocky basic command 3