当前位置:网站首页>How does the server build a virtual host?
How does the server build a virtual host?
2022-07-26 00:05:00 【qq392465929】
Virtual host or shared host , Also called virtual server , On a single host or host group , Achieve more
Method of domain service , Technology that can run multiple websites or services . Virtual hosts are completely independent , And can be managed by users themselves , Virtual does not mean that there is no , It means that the space is extended from the server of the entity , Its hardware system can be based on server group , Or a single server . Now there are many server management tools , Use management tools , Can quickly build a virtual host . The implementation of virtual host is generally divided into URL name correspondence 、IP Address correspondence and Port The port number corresponds to .
One 、 be based on IP Methods :
Bind multiple on the server IP, Then configure WEB The server , Bind multiple websites to different IP On . Browse different IP, You can see different websites .
Two 、 Port based approach :
One IP Address , Visit different websites through different ports .
3、 ... and 、 Host name based method :
Equipped with multiple domain names A Record , Let them resolve to the same IP Address , That is, on the same server . And then , Install... On the server WEB Server side , Add multiple websites , Draw up a host name on each website . because HTTP The protocol access request contains the hostname information , When WEB When the server receives an access request , Will visit different websites according to different host names .
Virtual host technology is an Internet server technology to save the cost of server hardware , Virtual host technology is mainly used in HTTP(Hypertext Transfer Protocol, Hypertext transfer protocol ) service , Logically divide one or all services of a server into multiple service units , The external representation is multiple servers , So as to make full use of server hardware resources .
Virtual host uses special software and hardware technology , Divide a real physical server host into multiple logical storage units . Every logical unit has no physical entity , But every logical unit can work on the network like a real physical host , Have a separate IP Address ( Or shared IP Address )、 Independent domain name and complete Internet The server ( Support WWW、FTP、E-mail etc. ) function .
The key technology of virtual host is , Even on the same hardware 、 On the same operating system , Running different server programs for multiple users , They don't interfere with each other . Each user has its own part of the system resources (IP Address 、 Document storage space 、 Memory 、CPU etc. ). Each virtual host is completely independent , To the outside world , Each virtual host performs exactly the same as a separate host . Therefore, this virtualized logical host is vividly called “ Virtual host ”.
边栏推荐
- 二叉树——700.二叉搜索树中的搜索
- 本轮牛市还能持续多久?|疑问解答 2021-05-11
- Security document archiving software
- Observer model of behavioral model
- [learning notes] unreal 4 engine introduction (III)
- Firewall command simple operation
- LeetCode高频题66. 加一,给你一个数组表示数字,则加1返回结果
- Pyqt5 rapid development and actual combat.pdf sharing
- How to use yolov5 as an intelligent transportation system for red light running monitoring (1)
- SIGIR‘22 推荐系统论文之图网络篇
猜你喜欢

Leetcode200 - find detailed explanation of the number of islands

SIGIR‘22 推荐系统论文之图网络篇

Binary tree - 530. Minimum absolute difference of binary search tree

Binary tree -- 104. Maximum depth of binary tree

痞子衡嵌入式:MCUXpresso IDE下将源码制作成Lib库方法及其与IAR,MDK差异

Solve the problem of rapid index bar extrusion
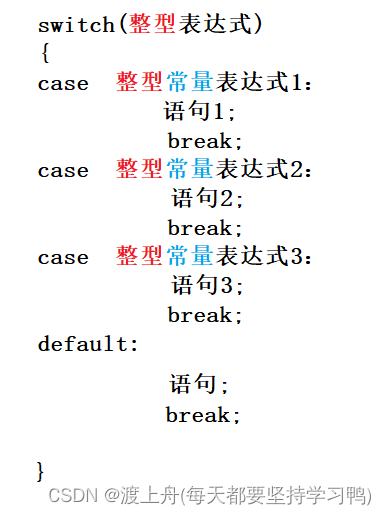
初阶C语言 - 分支语句(if、switch)
Program environment and pretreatment

二叉树——257. 二叉树的所有路径

Binary tree -- 111. Minimum depth of binary tree
随机推荐
Exercise (1) create a set C1 to store the elements "one", "two", "three"“
Cherish time and improve efficiency
回溯——77. 组合
Binary tree -- 257. All paths of binary tree
[brother hero July training] day 24: linear tree
二叉树——101. 对称二叉树
Binary tree - 404. Sum of left leaves
二叉树相关知识
“群魔乱舞”,牛市是不是结束了?2021-05-13
Security document archiving software
行为型模式之责任链模式
Detailed explanation of kubernetes network plug-ins - calico chapter - Overview
07_ue4进阶_发射火球扣mp值和攻击扣血机制
Chapter 64: error lnk2019: unresolved external symbol cvround
06_ue4进阶_使用地形工具设置大地图
栈与队列——347. 前 K 个高频元素
Module II operation
Binary tree -- 700. Search in binary search tree
Stack and queue - 239. Sliding window maximum
LeetCode 沙胡同系列 -- 63. 不同路径 II