边栏推荐
- 网络安全-openvas
- C#应用程序界面开发基础——窗体控制(3)——文件类控件
- The difference between tail -f, tail -f and tail
- JUC thread scheduling
- 网络安全-钓鱼
- Mathematical knowledge: Nim game game theory
- PS remove watermark details
- 网络安全-动态路由协议RIP
- CF1617B Madoka and the Elegant Gift、CF1654C Alice and the Cake、 CF1696C Fishingprince Plays With Arr
- Take you ten days to easily complete the go micro service series (I)
猜你喜欢
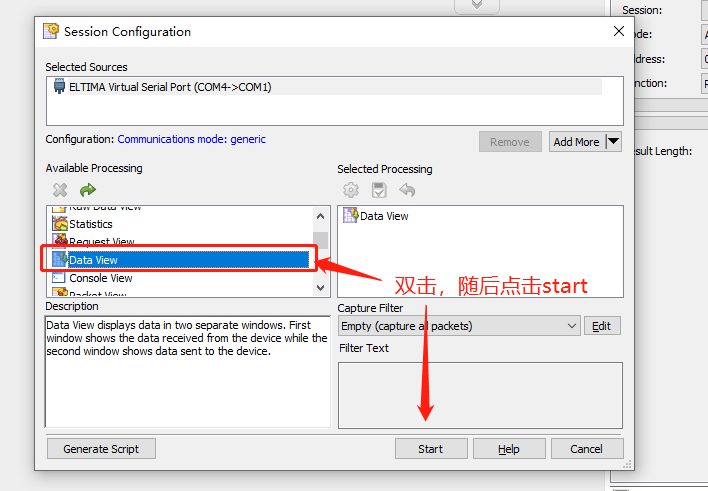
Installation and use of serial port packet capturing / cutting tool

What is tone. Diao's story
![[data mining] task 6: DBSCAN clustering](/img/af/ad7aa523b09884eee967c6773a613f.png)
[data mining] task 6: DBSCAN clustering
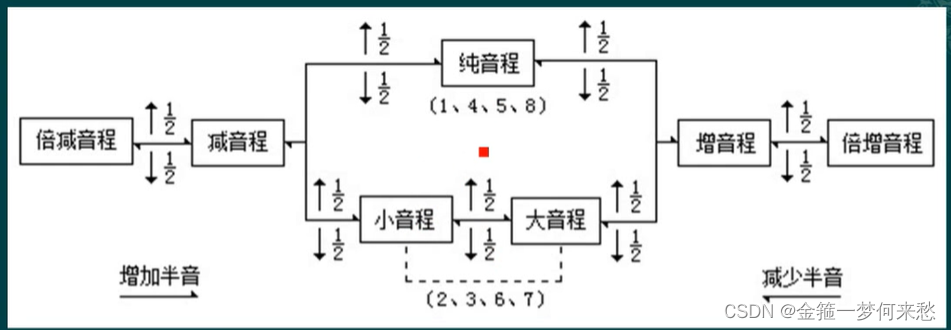
音程的知识的总结
![[error record] the shutter component reports an error (no directionality widget found. | richtext widgets require a directionality)](/img/3c/93ef853784d4e7cef63f30be0b0bf2.jpg)
[error record] the shutter component reports an error (no directionality widget found. | richtext widgets require a directionality)

C application interface development foundation - form control (2) - MDI form

STM32 - vibration sensor control relay on

Using tensorboard to visualize the model, data and training process
![[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio](/img/32/fa1263d9a2e5f77b0434fce1912cb2.gif)
[shutter] animation animation (animatedbuilder animation use process | create animation controller | create animation | create components for animation | associate animation with components | animatio
![[error record] an error is reported in the fluent interface (no mediaquery widget ancestor found. | scaffold widgets require a mediaquery)](/img/fd/d862412db43a641537fd67f7910741.jpg)
[error record] an error is reported in the fluent interface (no mediaquery widget ancestor found. | scaffold widgets require a mediaquery)
随机推荐
Mathematical knowledge: Nim game game theory
What are the trading forms of spot gold and what are the profitable advantages?
Cloud native topic sorting (to be updated)
Openresty cache
After reading this article, I will teach you to play with the penetration test target vulnhub - drivetingblues-9
Mathematical knowledge: step Nim game game game theory
¢ growth path and experience sharing of getting an offer
leetcode刷题_两数之和 II - 输入有序数组
函数的定义和调用、this、严格模式、高阶函数、闭包、递归
[QT] encapsulation of custom controls
Force buckle 204 Count prime
【数据挖掘】任务5:K-means/DBSCAN聚类:双层正方形
[principles of multithreading and high concurrency: 2. Solutions to cache consistency]
SSL flood attack of DDoS attack
How is the mask effect achieved in the LPL ban/pick selection stage?
简易分析fgui依赖关系工具
[error record] the shutter component reports an error (no directionality widget found. | richtext widgets require a directionality)
Mathematical Knowledge: Steps - Nim Games - Game Theory
Pytest learning notes (12) -allure feature · @allure Step () and allure attach
Network security - man in the middle attack