当前位置:网站首页>Network security - vulnerabilities and Trojans
Network security - vulnerabilities and Trojans
2022-07-03 01:42:00 【One of IT guys】
The goal is :
Restore the scene through the classic Trojan attack , To make a Trojan horse , And the implementation of the implanted Trojan to fully control the target host .

Trojan overview :
- Trojans are often called hacker programs , Malicious code , Also known as Trojans
- Hacker tools based on remote control
The characteristics of Trojans :
- Concealment
- Latency
- Regeneration
The composition of the Trojan :
- Client program
The client program is installed on the attacker ( hackers ) Fang's console , It's in charge of remote control command
- Server program
The server program is a Trojan horse program , It is hidden installed in the attacked ( Victimization ) Fang's computer , The target host is also called broiler
The harm of Trojans :
- Embezzle user information
Such as : Online game account 、 Online banking information 、QQ Password etc.
- Spread the virus
- Occupy system resources , Reduce computer performance
- Use this machine as a tool to attack other devices
Signs of being hit by a Trojan :
- The hard disk keeps reading and writing
- The mouse and keyboard don't work
- The window suddenly closes
- The new window opened inexplicably
Trojans spread through :
- When browsing a web page, exploit the browser vulnerability or the browser plug-in (flash、 Thunderbolt etc. ) Loophole
- adopt QQ、MSN And other instant messaging software , Send malicious links or Trojan files
- Use U Disk and other removable storage media
- Open a strange email , Through malicious code in email or attachments containing trojan virus
- Application software disguised as multimedia audio-visual file or implanted Trojan , utilize P2P Platform and website dissemination
- Take advantage of operating system vulnerabilities or weak passwords to directly put them remotely
- Download programs from unknown sources
Introduction to the environment :
Virtual machine software :VMWare
virtual machine :
Windows10- Simulated hacker attack machine
windowsserver 2008 - Simulation is controlled by Trojan
Tools :
Grey dove software
NTscan
Experimental process :
Turn on two virtual machines :
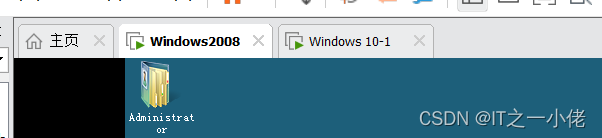

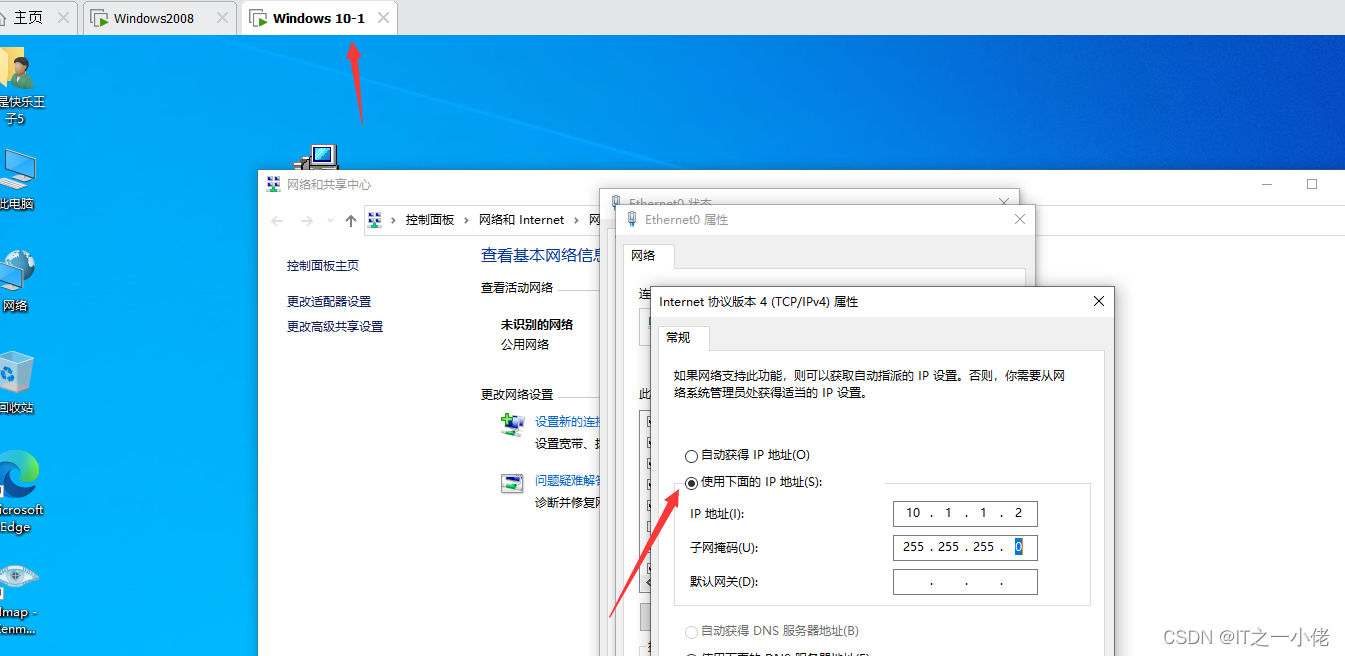
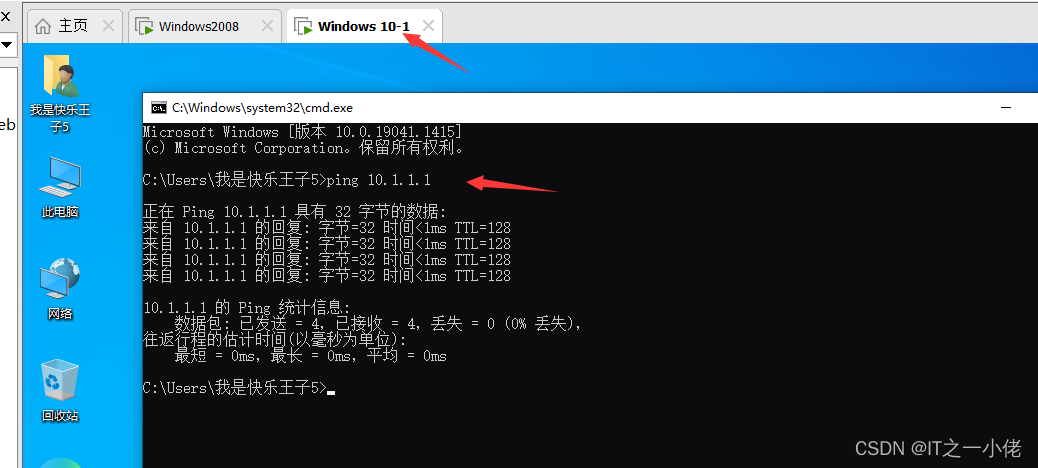
Configure two computers IP And test connectivity :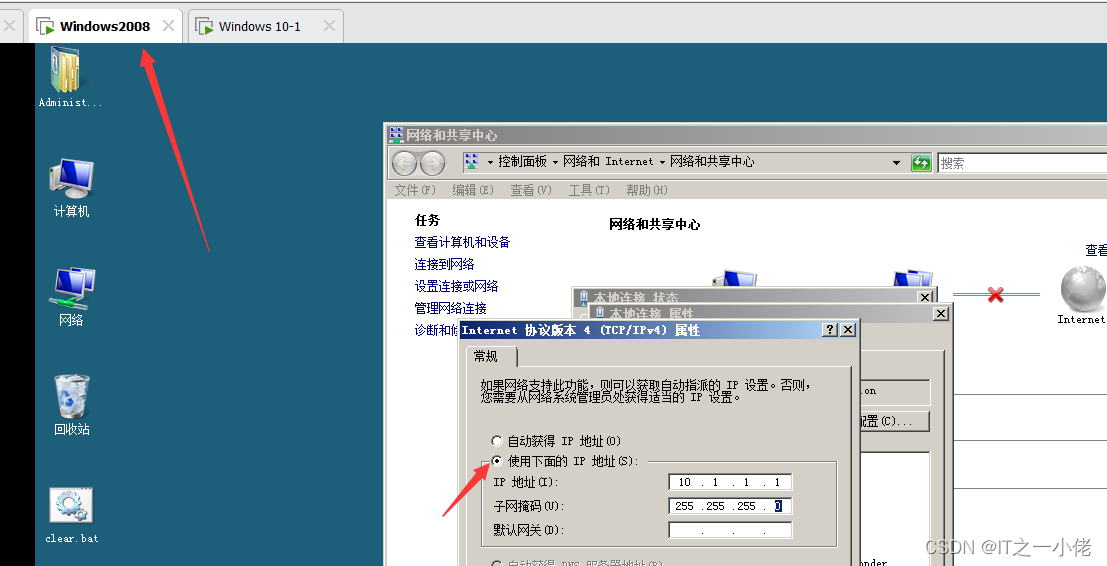
Make a Trojan :
Use grey dove Trojan horse to make software

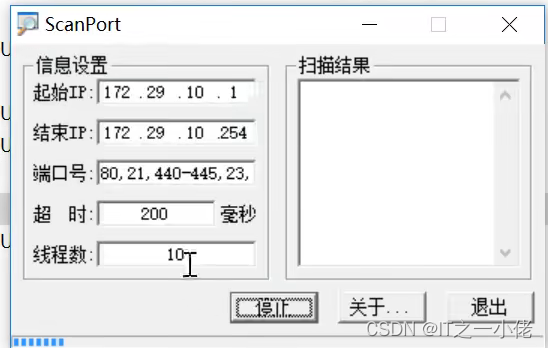
Brute force :
Aim to get the other party's account and password


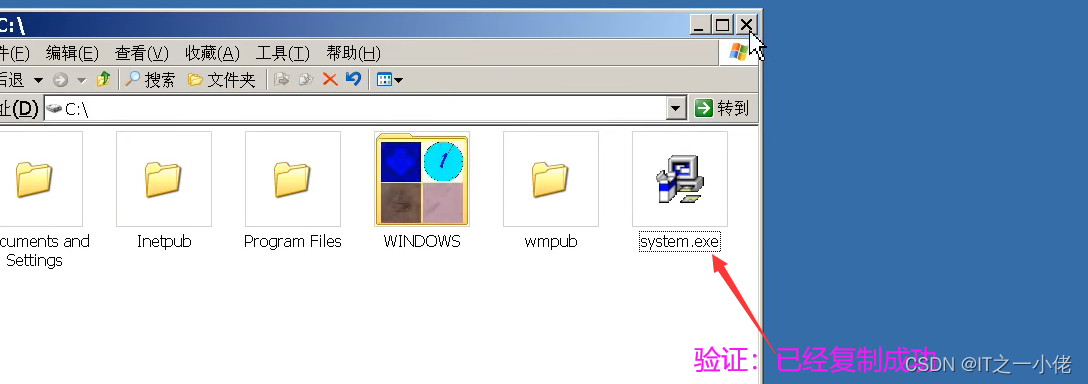
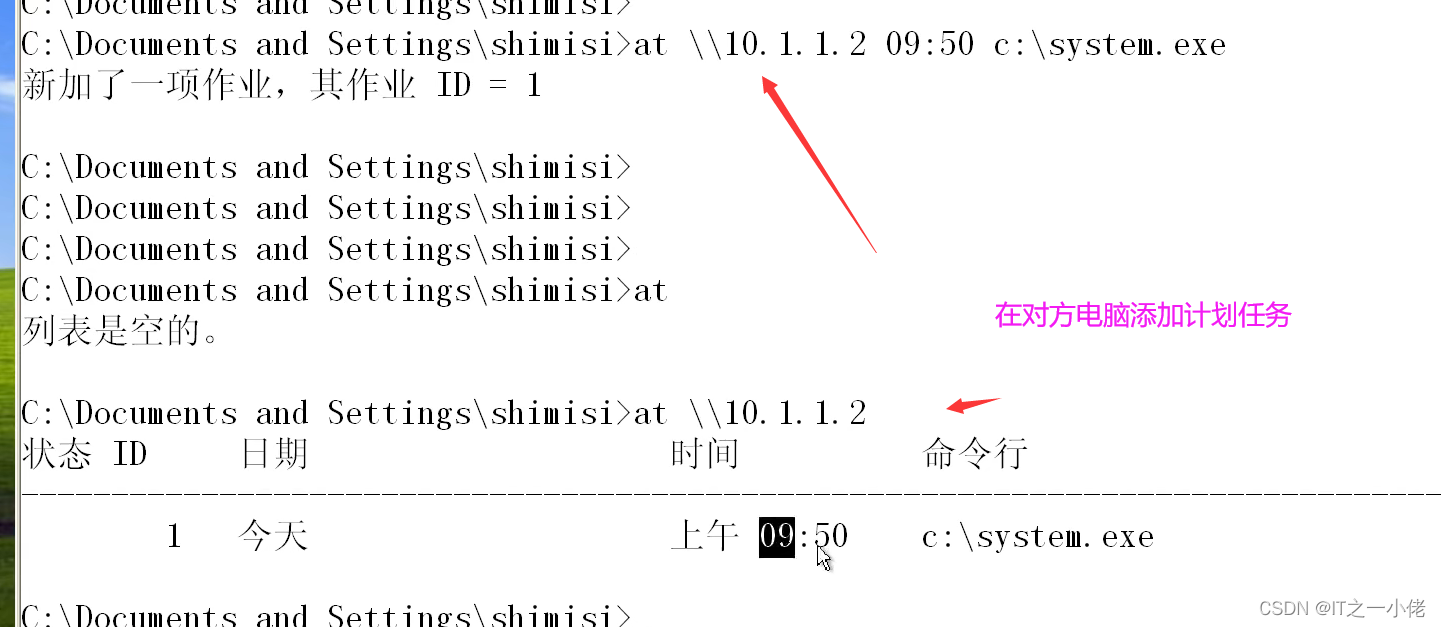
Successful control of target host :
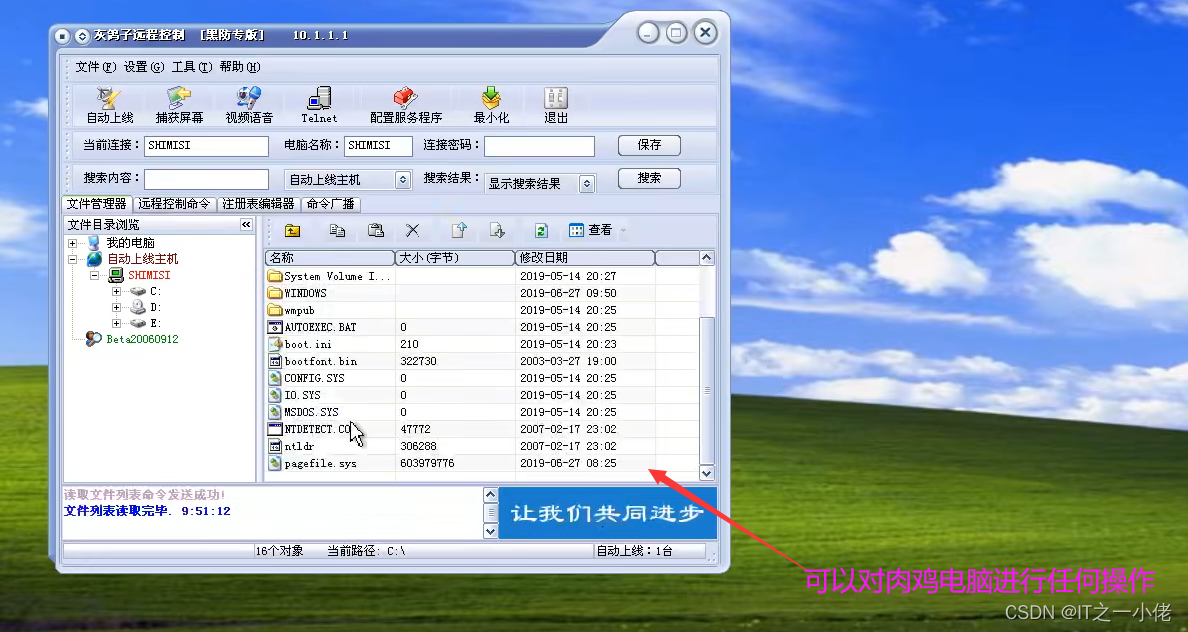
Reference video :
边栏推荐
- [Appendix 6 Application of reflection] Application of reflection: dynamic agent
- Take you ten days to easily complete the go micro service series (II)
- How is the mask effect achieved in the LPL ban/pick selection stage?
- 串口抓包/截断工具的安装及使用详解
- Mathematical knowledge: step Nim game game game theory
- [shutter] animation animation (basic process of shutter animation | create animation controller | create animation | set value listener | set state listener | use animation values in layout | animatio
- 【数据挖掘】任务1:距离计算
- High-Resolution Network (篇一):原理刨析
- 网络安全-病毒
- Mathematical Knowledge: Steps - Nim Games - Game Theory
猜你喜欢

SSL flood attack of DDoS attack
Smart management of Green Cities: Digital twin underground integrated pipe gallery platform

Leetcode skimming questions_ Sum of two numbers II - enter an ordered array

Tâche 6: regroupement DBSCAN

【数据挖掘】任务3:决策树分类
![[interview question] 1369 when can't I use arrow function?](/img/7f/84bba39965b4116f20b1cf8211f70a.png)
[interview question] 1369 when can't I use arrow function?

How is the mask effect achieved in the LPL ban/pick selection stage?
看完这篇 教你玩转渗透测试靶机Vulnhub——DriftingBlues-9
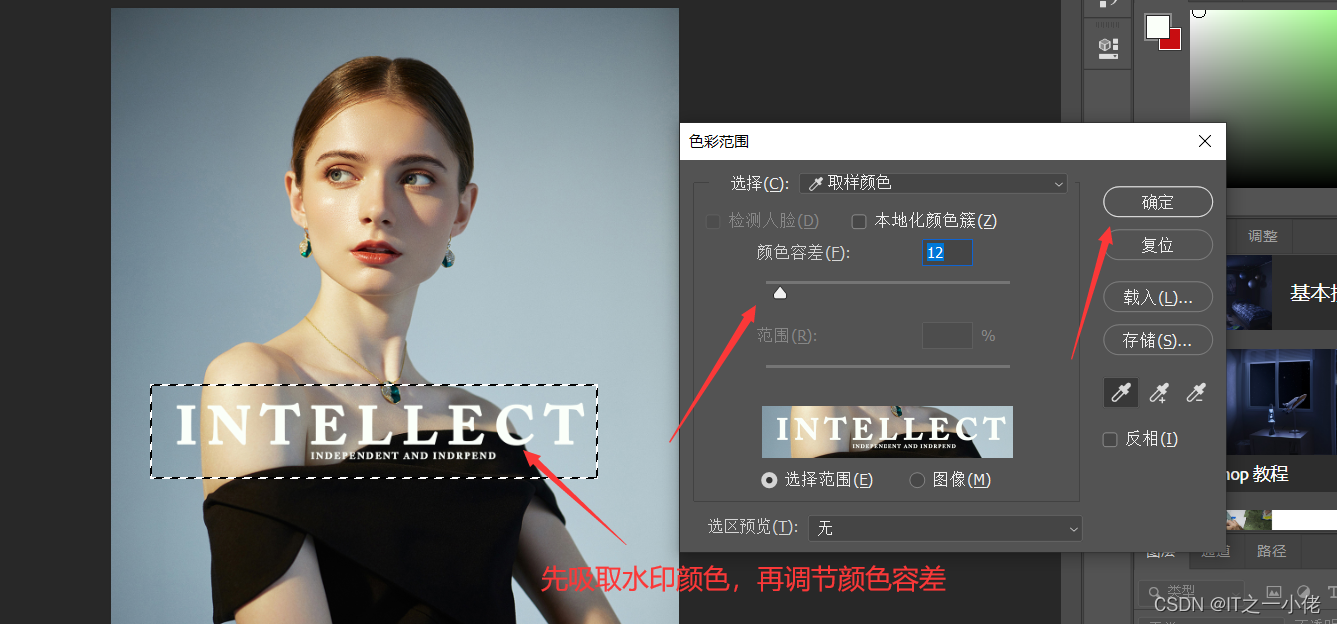
PS去除水印详解
![[Appendix 6 Application of reflection] Application of reflection: dynamic agent](/img/e7/0ee42902b178b13e9a41385267e7b6.jpg)
[Appendix 6 Application of reflection] Application of reflection: dynamic agent
随机推荐
The thread reuse problem of PageHelper using ThreadLocal, did you use it correctly?
Expérience de recherche d'emploi d'un programmeur difficile
Vant 实现简单的登录注册模块以及个人用户中心
The difference between tail -f, tail -f and tail
[principles of multithreading and high concurrency: 2. Solutions to cache consistency]
网络安全-漏洞与木马
View of MySQL
[QT] encapsulation of custom controls
Arduino dy-sv17f automatic voice broadcast
云原生题目整理(待更新)
Virtual list
C language course information management system
【数据挖掘】任务1:距离计算
CF1617B Madoka and the Elegant Gift、CF1654C Alice and the Cake、 CF1696C Fishingprince Plays With Arr
网络安全-扫描
C application interface development foundation - form control (1) - form form
力扣 204. 计数质数
C application interface development foundation - form control (2) - MDI form
High resolution network (Part 1): Principle Analysis
String splicing function of MySQL