当前位置:网站首页>Five core elements of architecture design
Five core elements of architecture design
2022-07-07 05:40:00 【Qin Tian】
Catalog
1、web Front end performance optimization
2、 Application server performance optimization
3、 Database layer optimization
4、 An indicator of website performance
1、 Security system architecture
Five important core indicators in the architecture : They are performance 、 Usability 、 Scalability 、 Scalability and security .
One 、 performance
Performance is one of the core elements , Otherwise, why do I design architecture ? Casually, a very low It's good to have your system online . Therefore, performance optimization is a barrier that many small companies cannot overcome . Of course, there are many ways to optimize website performance
1、web Front end performance optimization
1) Browser access optimization
Including browser cache 、 Page compression transmission 、 Reasonable layout of pages 、 Reduce Cookie transmission .
- Reduce http request . Avoid setting up too many communication links . take js、css、 Picture files should be merged as much as possible . Avoid too many requests . meanwhile , The back-end request of the system should also be reasonably designed as far as possible , To avoid too much interaction .
- Use the browser's cache .http Head set Cache-Control and Expires.js For example, the file name can be time stamped . Once there is an update, update the timestamp , Otherwise cache ; At the same time, try to avoid updating a large number of static resources at the same time .
- Compress static resources .
- css Place at the top of the page ,js At the bottom . In advance css Rendering . Also avoid js Page blocking . But it needs specific analysis of specific problems . Like pages dom Nodes need to rely on js Generate , Then change the file location according to the situation .
- Reduce cookie transmission . At the same time, let static resources have independent domain names , Do not send static resource requests cookie. So as to reduce the transmission cost .cookie Can pass document.cookie obtain .
2)CDN Speed up
Cache pictures 、 file 、CSS as well as script Script . however pc Upper CDN The acceleration effect is better than that of the mobile terminal . After investigation, we found that ,last-mile The higher the delay ,CDN The worse the relative effectiveness of .
“ Last mile ” It is a term used by the communication and technology industry to describe the technology and steps of connecting end users to the communication network .
3) Reverse proxy
It can provide seven layers of load balancing (http Request balancing strategy ), And it can provide the cache of static resources , Request forwarding , Prevent network attacks, etc . The more popular ones are nginx.
2、 Application server performance optimization
If the request static interface is not stuck , But dynamic data is still a card , explain MySQL Too many requests to process , You can use server local cache and distributed cache , You can also speed up the response through asynchronous operation , In the case of highly concurrent requests , Multiple application servers can form a cluster to serve the public , Improve the overall processing capacity , improve performance .
1) Distributed cache
Website performance optimization law : Priority is given to using cache to optimize performance
- Generally speaking , Deposit in cache The reading and writing ratio of data is 2:1 above , And it should be hot data .
- It is necessary to consider the possible data inconsistency in the short term if caching is adopted , Or if the cache is updated in real time, it may bring performance and resource overhead .
- You need to consider cache Once it fails , A large number of requests may bring an avalanche of service performance . So you can be right cache Adopt cluster deployment , In order to avoid the sudden increase of service pressure caused by the loss of too much data .
- Consider warm-up loading of cache for hot data . For example, before the peak , First, store the hot data into the cache in advance . So as to improve the service performance during peak periods .
- To avoid malicious attacks , always query Nonexistent data , Lead to cache Frequent visits DB, Non existing data can also be cached and cleaned up regularly . At the same time, there is a mechanism to identify and block malicious requests .
- Distributed cache should be decentralized and centrally managed . Scalability is ensured through non communication and isomorphism between different instances , And reduce the complexity of the system .
2) Asynchronism
Anything that can be done later should be done later , It feels like lazy loading
Peak shaving is achieved through distributed message queues . Solve problems through business cooperation technology . such as 12306 The line up .
3) colony
Adopting cluster is also an embodiment of service virtualization . To avoid single point problems , At the same time, it provides higher availability , High performance services .
4) Code optimization
- In a multithreaded , If it is intensive computing , The number of threads should not exceed CPU Check the number . If it is IO Handle , Number of threads =[ Task execution time /( Task execution time -IO Waiting time )] * CPU Check the number . besides , We should design objects as stateless objects , More local objects , Refine the lock properly .
- Reuse resources . For example, using singleton mode , For example, use connection pool .
- Setting up reasonable JVM Parameters , Avoid unreasonable full gc.
5) Storage performance optimization
The index of relational database adopts B+ Tree implementation . And many nosql The database uses LSM Tree for storage .LSM Keep the data added, deleted, modified and queried in memory , Until the memory cannot be put down , And the next level of disk LSM The tree goes on merge. So there are many write operations , The read operation is more about querying the recently written data , Its performance is much higher than b+ Trees ; use HDFS combination map reduce Massive data storage and analysis . It can automatically perform concurrent access and redundant backup , With high reliability . It is equivalent to achieving RAID( Independent redundant disk array ) The function of .
3、 Database layer optimization
The database layer is actually the most vulnerable one , Generally in the application design, the request needs to be intercepted upstream , The database layer only undertakes “ In one's power ” Access requests for , therefore , We introduce queues and caches in the service layer , Let the underlying database rest easy . But if requests surge , There is still a lot of query pressure to MySQL, At this time, we need to find a way to solve it MySQL It's the bottleneck of the market , At this time, you can use the index 、 cache 、SQL Performance optimization and other means , You can also use NoSQL Database to optimize the data model 、 Storage structure, etc .
4、 An indicator of website performance
The important thing is response time 、TPS、 System performance counters, etc , Through these indicators to determine whether the system design has achieved the goal .
1) response time .
2) Concurrency number . If there is no corresponding accurate monitoring for the time being , For different business models , There can be different estimates of concurrency . If our system estimates the peak concurrency , There is a rough calculation , That is, the average number of concurrent requests per second throughout the day * 3. But it also needs specific analysis of specific problems .
3) throughput . The more common ones are QPS( Queries per second )、HPS( Per second http Number of requests ) as well as TPS( Number of transactions processed per second ).
4) Performance counters . Including system load 、 Number of threads 、cpu、 Memory usage, etc .
It can be used top、free、cat /proc/cpuinfo Wait for the order to see . The definition of system load is currently CPU Number of threads executed / Waiting to be CPU Number of bus passes executed . When its value and logic cpu The same number is in good condition , It means that all resources are used to a great extent . But some people think that when the load is 0.7 Multiple logic CPU A few hours is better .
5、 High availability
Including highly available applications 、 Highly available services 、 Highly available data and services and highly available monitoring .
Two 、 Security
The Internet is open , Anyone can visit the website anywhere . The security architecture of the website is to protect the website from malicious access and attack , Protect the important data of the website from being stolen .
Safe 5 Elements : Confidentiality 、 integrity 、 Usability 、 Controllability and auditability .
1、 Security system architecture
- Security service refers to the security protection measures provided by computer network , Including certification services 、 Access control 、 Data confidentiality Services 、 Data integrity services and undeniable Services .
- A specific security mechanism is a mechanism used to implement security services , Including encryption mechanism 、 Data signature mechanism 、 Access control mechanism 、 Data integrity mechanism 、 Authentication exchange mechanism 、 Flow filling mechanism 、 Routing control mechanism and notarization mechanism .
- Universal security mechanisms are not ad hoc for any particular service , It belongs to safety management , Divided into trusted functionality 、 Safety signs 、 Event detection 、 Security audit trail and security recovery .
2、 Level of safety protection
- User independent protection level
- System audit protection level
- Safety mark protection level
- Structured protection level
- Access authentication protection level
The standard to measure the website security architecture is to target all kinds of existing and potential attacks and secret stealing methods , Is there a reliable response strategy .
3、 ... and 、 Usability
High availability , High availability , It refers to shortening the time when the server cannot provide services normally due to failure or other reasons . It is often seen by major cloud manufacturers 6 individual 9,11 individual 9 That's what I'm saying . such as 6 individual 9 Namely 99.9999%, Then the time when the server is unavailable throughout the year is (1-99.9999%)*365*86400=31.5 second . That is to say, in a whole year , Once the server crashes , The recovery time will not exceed 31.5 second .
High availability has high fault tolerance and recoverability .
Measure whether a system architecture design meets the goal of high availability , If one or more servers are down , And all kinds of unexpected problems , Is the overall system still available .
Generally, there are three means 、 redundancy 、 clustering 、 Distributed .
The main means of high availability of websites is redundancy , Applications are deployed on multiple servers to provide services at the same time , Data is stored on multiple servers and backed up with each other , Any server will not affect the overall performance of the application , The usual implementation means is to form a cluster of multiple servers through load balancing devices .
Four 、 Extensibility
Extensibility (Extensibility) When the impact on the existing system is minimal , The ability of a system to continuously expand or enhance its functions . The performance is that the system infrastructure is stable and does not need frequent changes , Less dependency and coupling between applications , When the system adds new functions , No need to modify the structure and code of the existing system . Scalability depends on the good architecture design in the early stage . Reasonable business logic abstraction , level / Vertical cutting, distributed and so on .
The main means of website extensible architecture are event driven architecture and distributed services .
Event driven is usually implemented by message queue , In this way, message production and processing logic are separated .
Server service is to separate business and reusable services , Call through the distributed service framework . The newly added products can realize their own business logic by calling reusable services , Without any impact on existing products .
Regarding this ,《 Scalable art 》 The book proposes a more systematic and extensible model —— AKF Expandable Cube (Scalability Cube). This cube is set to... Along three axes :X、Y、Z.
- X Axis extension —— Pay attention to the level of data and service cloning , That's what I mentioned earlier “ Add machines to solve problems ”
- Y Axis extension —— Focus on the division of responsibilities in application , For example, data types , Division of transaction execution types
- Z Axis extension —— Focus on prioritizing services and data , Such as the division of regions
The whole extended model , Use the figure below to show , Where the origin represents the state of complete no expansion .

5、 ... and 、 Scalability
Services should be isomorphic .DB、cache When considering distribution, try to design the expansion scheme in advance . You can also use some mainstream ones that support horizontal scaling better nosql、memcached、hbase etc. .
(1) Lateral separation : Separate and deploy different business modules , Realize the scalability of the system ;

(2) Vertical separation : Separate and deploy different parts of the business process , Realize the scalability of the system ;

边栏推荐
猜你喜欢
Preliminary practice of niuke.com (9)
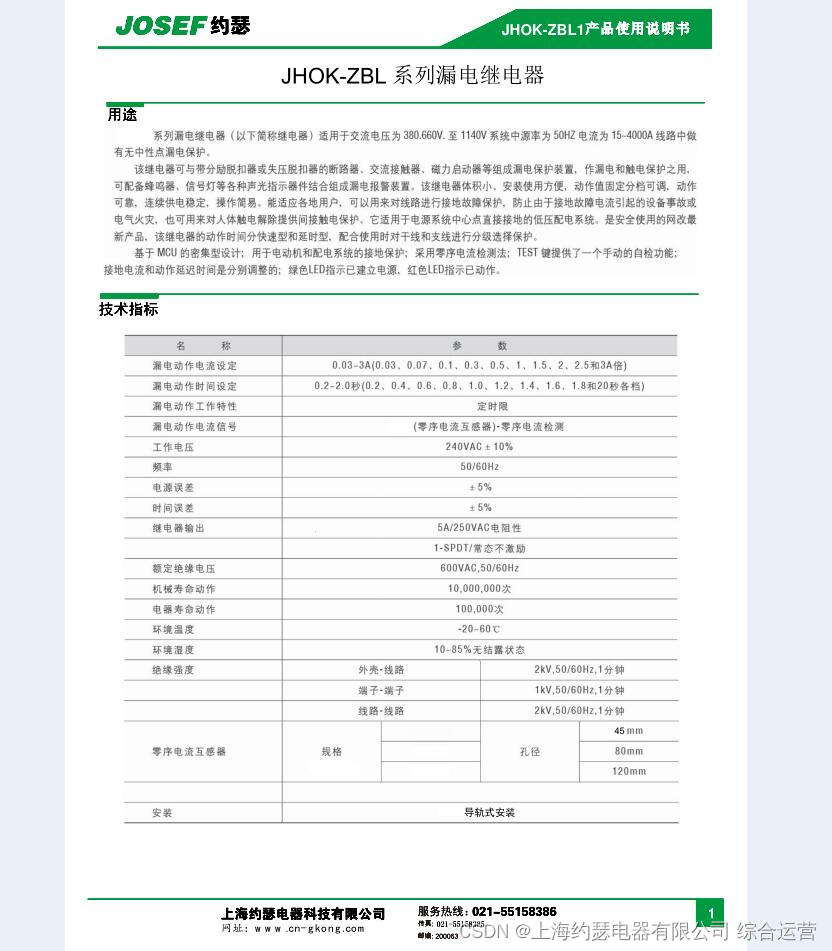
Jhok-zbl1 leakage relay
Annotation初体验
The navigation bar changes colors according to the route

导航栏根据路由变换颜色
论文阅读【MM21 Pre-training for Video Understanding Challenge:Video Captioning with Pretraining Techniqu】
1. AVL tree: left-right rotation -bite
Phenomenon analysis when Autowired annotation is used for list
4. Object mapping Mapster
《5》 Table
随机推荐
sql查询:将下一行减去上一行,并做相应的计算
Is the human body sensor easy to use? How to use it? Which do you buy between aqara green rice and Xiaomi
TabLayout修改自定义的Tab标题不生效问题
Design, configuration and points for attention of network specified source multicast (SSM) simulation using OPNET
Codeforces Round #416 (Div. 2) D. Vladik and Favorite Game
5. 数据访问 - EntityFramework集成
Leakage relay jelr-250fg
How Alibaba cloud's DPCA architecture works | popular science diagram
Writing process of the first paper
《4》 Form
一条 update 语句的生命经历
不同网段之间实现GDB远程调试功能
分布式全局ID生成方案
什么是依赖注入(DI)
Unity keeps the camera behind and above the player
Dj-zbs2 leakage relay
Taobao store release API interface (New), Taobao oauth2.0 store commodity API interface, Taobao commodity release API interface, Taobao commodity launch API interface, a complete set of launch store i
High voltage leakage relay bld-20
DOM-节点对象+时间节点 综合案例
论文阅读【Semantic Tag Augmented XlanV Model for Video Captioning】