当前位置:网站首页>Database postragesq peer authentication
Database postragesq peer authentication
2022-07-05 01:13:00 【wx5d0241bb88268】
20.9. Peer authentication
Peer The authentication method obtains the operating system user name of the client from the kernel and uses it as the allowed database user name ( And optional user name mapping ) Come to work . This method only supports... On local connections .
The following supported configuration options are used for peer:
map
Allow mapping between system and database user names . See Section 20.2.Peer Certification is only available getpeereid() function 、SO_PEERCRED Socket parameters or similar mechanisms are available on the operating system . these OS The present includes Linux、 Most of BSD Include OS X as well as Solaris.
边栏推荐
- “薪資倒掛”、“畢業生平替” 這些現象說明測試行業已經...
- Take you ten days to easily complete the go micro service series (IX. link tracking)
- Basic operations of database and table ----- delete index
- 107. Some details of SAP ui5 overflow toolbar container control and resize event processing
- Global and Chinese market of portable CNC cutting machines 2022-2028: Research Report on technology, participants, trends, market size and share
- [Yocto RM]11 - Features
- 無心劍英譯席慕容《無怨的青春》
- 揭露测试外包公司,关于外包,你或许听到过这样的声音
- If the consumer Internet is compared to a "Lake", the industrial Internet is a vast "ocean"
- Take you ten days to easily complete the go micro service series (IX. link tracking)
猜你喜欢
![[wave modeling 2] three dimensional wave modeling and wave generator modeling matlab simulation](/img/50/b6cecc95e46fe1e445eb00ca415669.png)
[wave modeling 2] three dimensional wave modeling and wave generator modeling matlab simulation

Les phénomènes de « salaire inversé » et de « remplacement des diplômés » indiquent que l'industrie des tests a...
![[development of large e-commerce projects] performance pressure test - Optimization - impact of middleware on performance -40](/img/e4/0bdee782a65028b2bc87db85d48738.png)
[development of large e-commerce projects] performance pressure test - Optimization - impact of middleware on performance -40
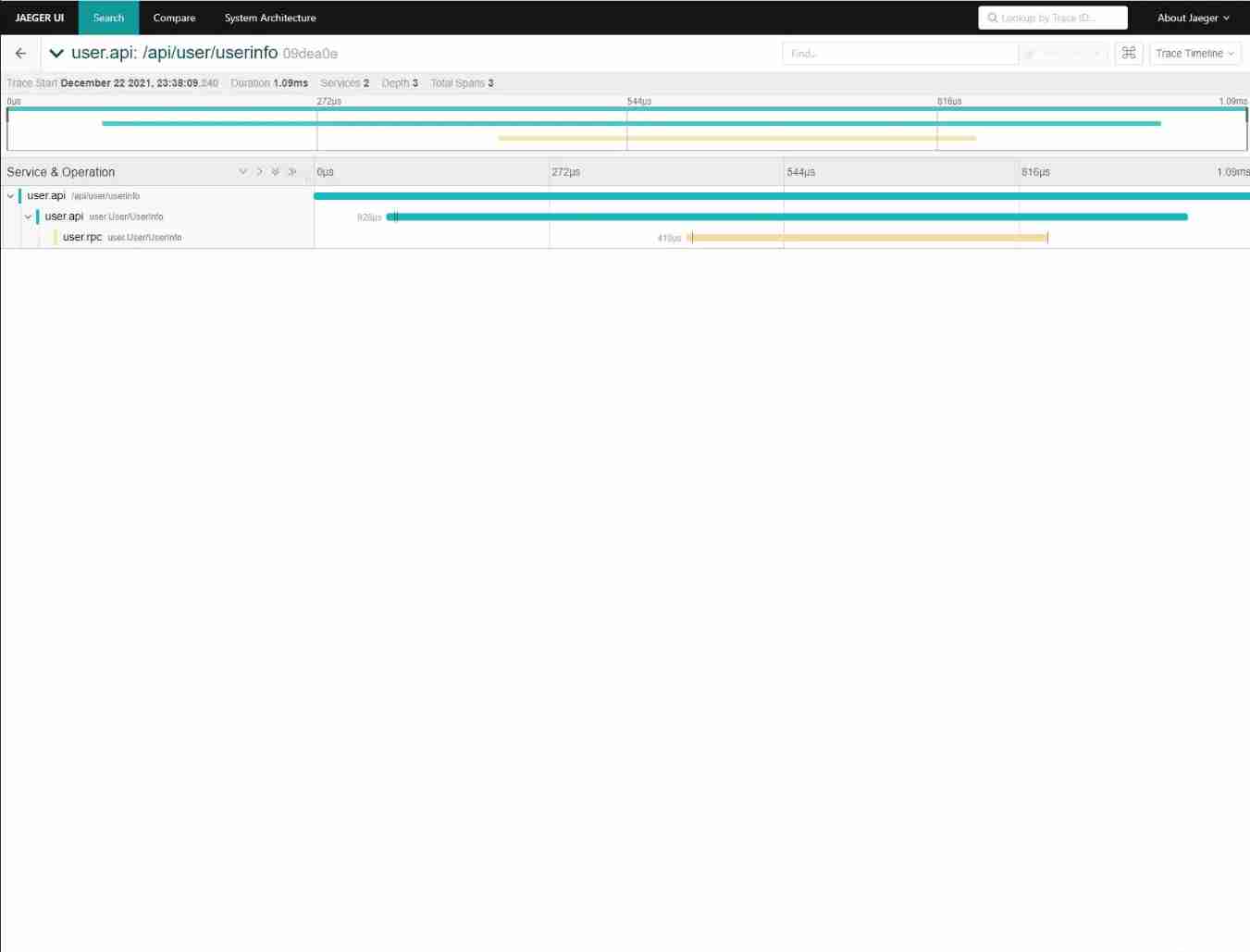
Take you ten days to easily complete the go micro service series (IX. link tracking)

Async/await you can use it, but do you know how to deal with errors?
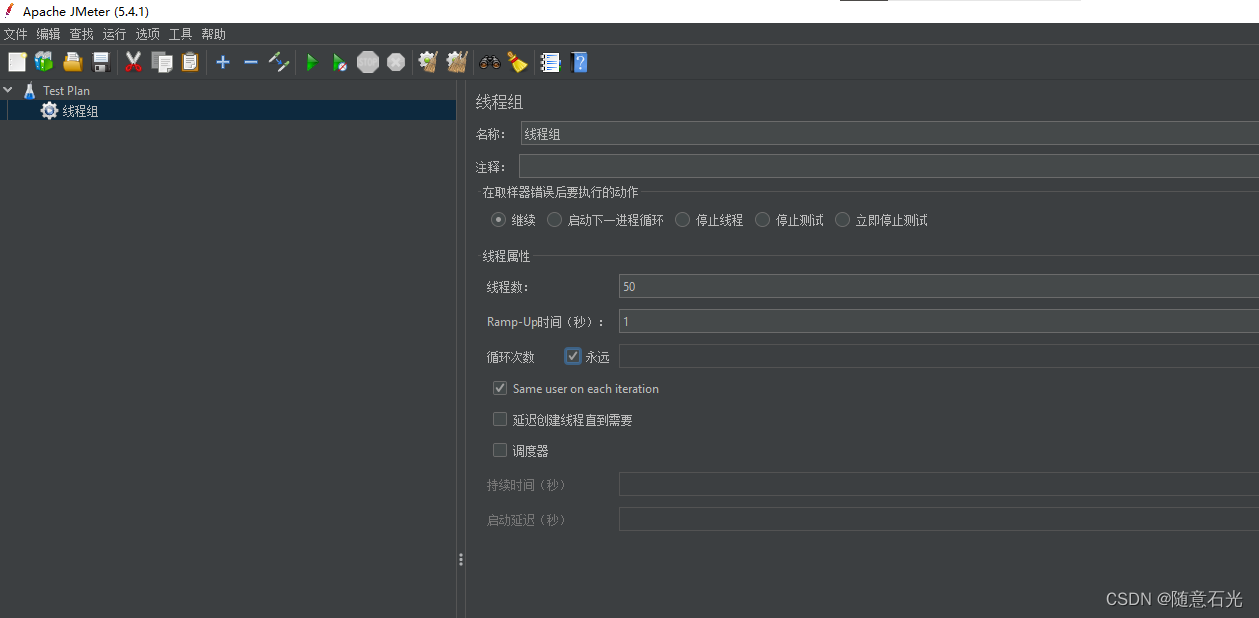
【大型电商项目开发】性能压测-优化-中间件对性能的影响-40

那些一门心思研究自动化测试的人,最后都怎样了?

微信小程序;胡言乱语生成器

Innovation leads the direction. Huawei Smart Life launches new products in the whole scene
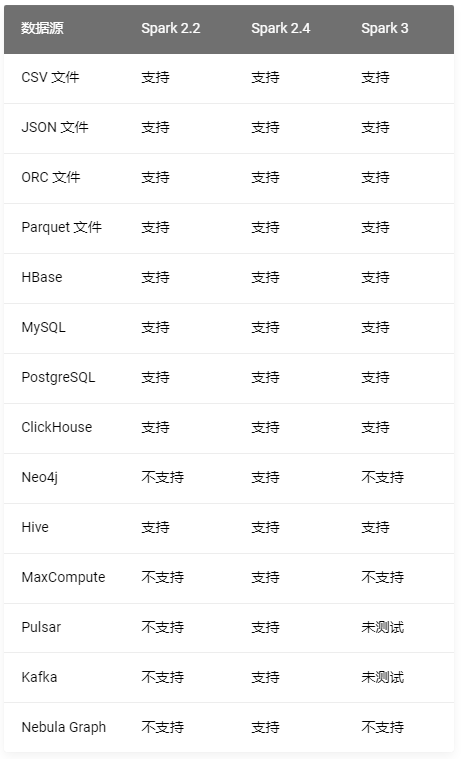
Nebula Importer 数据导入实践
随机推荐
[untitled]
Jcenter () cannot find Alibaba cloud proxy address
潘多拉 IOT 开发板学习(RT-Thread)—— 实验4 蜂鸣器+马达实验【按键外部中断】(学习笔记)
Pycharm professional download and installation tutorial
【海浪建模3】三维随机真实海浪建模以及海浪发电机建模matlab仿真
Les phénomènes de « salaire inversé » et de « remplacement des diplômés » indiquent que l'industrie des tests a...
College degree, what about 33 year old Baoma? I still sell and test, and my monthly income is 13K+
Summary of the function and usage of const, volatile and restrict
Introduction to the gtid mode of MySQL master-slave replication
There is a new Post-00 exam king in the testing department. I really can't do it in my old age. I have
Basic operation of database and table ----- phased test II
Liangzai's first program life and annual summary in 2022
Digital DP template
[Chongqing Guangdong education] National Open University spring 2019 1042 international economic law reference questions
7. Scala process control
FEG founder rox:smartdefi will be the benchmark of the entire decentralized financial market
Global and Chinese market of optical densitometers 2022-2028: Research Report on technology, participants, trends, market size and share
Database postragesql client authentication
Apifox (postman + swagger + mock + JMeter), an artifact of full stack development and efficiency improvement
Global and Chinese market of network connected IC card smart water meters 2022-2028: Research Report on technology, participants, trends, market size and share