当前位置:网站首页>How to implement safety practice in software development stage
How to implement safety practice in software development stage
2022-07-07 17:40:00 【Huawei cloud developer Alliance】
Abstract : Do a good job of safety release. We focus on the incident response plan 、 Safety inspection 、 Look at the software signature certificate from three aspects .
This article is shared from Huawei cloud community 《DevSecOps Software development security practice —— Release 》, author : Hua Wei Yun PaaS Little helper .
Preface
When it comes to publishing , Will think of deployment , The deployment release discussed in this article is based on DevOps The background of . stay 《DevOps Practice Guide 》 These two words are clearly defined in , Deployment refers to installing a specified version of software in a specific environment , Publishing is to provide a feature or group of features to all customers or some customers . One is environment oriented technology operation , One is user oriented business decision . thus it can be seen , Deployment is the premise of release , Through continuous deployment , To support the on-demand release of business .
After software release , Software security problems caused by errors in the running phase account for a large proportion of all security problems . Release is the last security line before the software goes online , Have a pivotal position .
How to do a good job of safety release
Do a good job of safety release. We focus on the incident response plan 、 Safety inspection 、 Look at the software signature certificate from three aspects .
Event response plan
In the software release stage , Enterprises need to establish a set of safety release Standards , There are corresponding release safety procedures and specifications , Safety incident response plan and release decision , Ensure that the release activities can be carried out safely and orderly .
Event response plan , Including but not limited to standard safety incident response process 、 Emergency safety incident response process , Person in charge of safety and contact information . Even products that do not contain any known vulnerabilities at the time of release , It may also face emerging threats in the future . It should be noted that , If the product contains third-party code , You also need to leave the contact information of the third party and join the event response plan , So that when a problem occurs, you can find the corresponding person .
Perfect safety incident response plan , After the software is released, the software supply chain security events 、 Software security vulnerability disclosure events can carry out rapid security response , Control and eliminate security threats and adverse effects caused by security incidents , Then trace and solve the root cause of the security incident .
Safety inspection
Before release , You need to use security analysis tools to conduct a comprehensive vulnerability scan , Execute the corresponding vulnerability repair plan according to the vulnerability scanning results . Vulnerability scanning can be done from the host 、 Mirror image 、Web、 Terminal applications 、 Scan multiple dimensions of network and database , Ensure full scene coverage .
Security check includes but is not limited to environment security deployment verification 、 Security configuration baseline detection 、 Image security scan 、 Virus scanning 、 Host vulnerability scanning and other activities , If possible, we can conduct a secondary review of all previous work , Conduct the final safety assessment according to the inspection results , Take the evaluation results as a precondition for release .
The security problems solved in the release phase are all security problems in the real production environment , Therefore, we should thoroughly check the configuration differences between the production environment and the development environment . Studies have shown that , Security vulnerabilities caused by security configuration errors in existing application systems have become one of the main sources of system vulnerabilities . Configuration management tools are a key factor in ensuring security during the release phase , Configuration management tools provide visibility into infrastructure configuration , Then you can audit and check the system configuration , Protect the runtime environment infrastructure . Common configuration management tools in the industry include Chef、Ansible、Puppet、Terraform and SaltStack.
During the release , Conduct security check at the security check node , There is a corresponding alarm mechanism , If you encounter problems and risks in the release, you can implement the security fallback and backup mechanism , Follow the safety incident response plan . At the same time, it is suggested to adopt a low-risk release strategy , Such as Canary release and blue-green release .
Software signatures and certificates
In order to prevent the software package from being maliciously tampered with during delivery or after release , Enterprises will add digital signatures to software codes , To ensure the authenticity and integrity of the code , Authenticity is to convince users of the source of this software , Integrity is to ensure that the software is not tampered with after it is released .
The code signing certificate is usually issued by a trusted third party CA Issued by , Compared with unsigned code , Code with certificates has higher reliability . Software developers can use code signing certificates to sign kernel code .sys file 、ActiveX file 、 .exe 、 and dll Documents and mobile application software developed by smart phones . Digital signatures protect users from viruses 、 By malicious code and spyware , It also protects the interests of software developers , So that the software can be released quickly and safely on the Internet .
After software release , Archive all kinds of problems and documents encountered , Help with emergency response and product upgrades .
Huawei cloud security release practice
Huawei cloud's multi scenario high-precision vulnerability scanning capability , It is a powerful guarantee to walk the last mile before the software goes online .
- Full scenario vulnerability coverage : Cover Web、 host 、 Mirror image 、 Binary system 、 Full scenario vulnerability scanning capability of terminal applications , Support for HUAWEI 、OWASP And so on , Support the insurance 0 Equal standard .
- Professional repair advice : Provide a typical Web Precise vulnerability detection , stay CVE Vulnerability assessment is closer to the real threat ; stay APK Open source component scanning and information leakage detection , With more accurate detection ability , Therefore, more professional repair suggestions can be provided .
- Scalable vulnerability detection capabilities : Focus on the latest security vulnerabilities , Dynamically expand scanning capabilities ; Flexible integration of third-party vulnerability scanning engine , Unified report presentation , Support loopholes to duplicate , It can also be integrated into third-party continuous integration / In the continuous release pipeline .
meanwhile , According to the release and deployment regulations of Huawei cloud , Developing 、 Deploy 、 In the process of going online , Self check must be completed , And promise to meet the operational requirements of online . For low-risk cloud services , Go online after passing the self inspection . The self inspection results are also submitted to the audit synchronously . Self inspection includes but is not limited to integrity verification 、 Engineering Baseline Review 、 Service self check 、 Promise safety and credibility 、 Container and infrastructure security, etc , At the same time, it will conduct retrospective analysis on safety problems , Rectify safety problems , Ensure the safety and credibility of the released products . For high-risk cloud services , Through more investment 、 In a short time to implement more stringent online testing and approval , Make sure it goes online in time and safely , Protect the interests of tenants .
At the end
Completing the security release is not the last step , Once the application is deployed in the online production environment and stabilized , It is necessary to start safety monitoring and operation and maintenance . As more and more development teams continue to improve their processes and adopt new tools , Security issues are becoming more and more important , Enterprises need to take it seriously .DevSecOps It's a circular process , It should be iterated continuously and applied to every new code deployment . Exploits and attackers are evolving , The development of security skills of software teams is also crucial .
Refer to appendix
1.《 Huawei cloud security white paper 》. Huawei Technology Co., Ltd .
2.《 R & D white paper on operational security 》. Cloud computing Open Source Industry Alliance .
3.《DevOps Practice Guide 》.Gene Kim,Jez Humble,Patrick Debois,John Willis. People's post and Telecommunications Press .
4. Scan more than... Every day 300 One hundred million lines of code ,DevSecOps Landing and practice in Huawei _DevOps
Click to follow , The first time to learn about Huawei's new cloud technology ~
边栏推荐
猜你喜欢
Matplotlib绘图界面设置
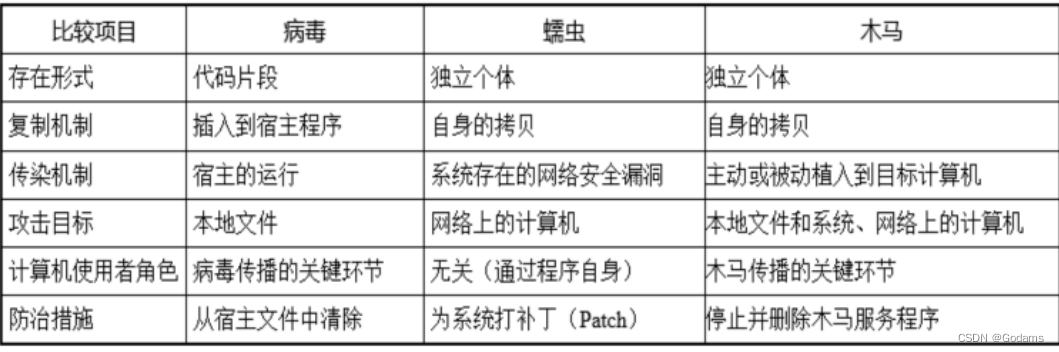
【网络攻防原理与技术】第6章:特洛伊木马

【TPM2.0原理及应用指南】 12、13、14章
机器人工程终身学习和工作计划-2022-

专精特新软件开发类企业实力指数发布,麒麟信安荣誉登榜

A tour of grpc:03 - proto serialization / deserialization
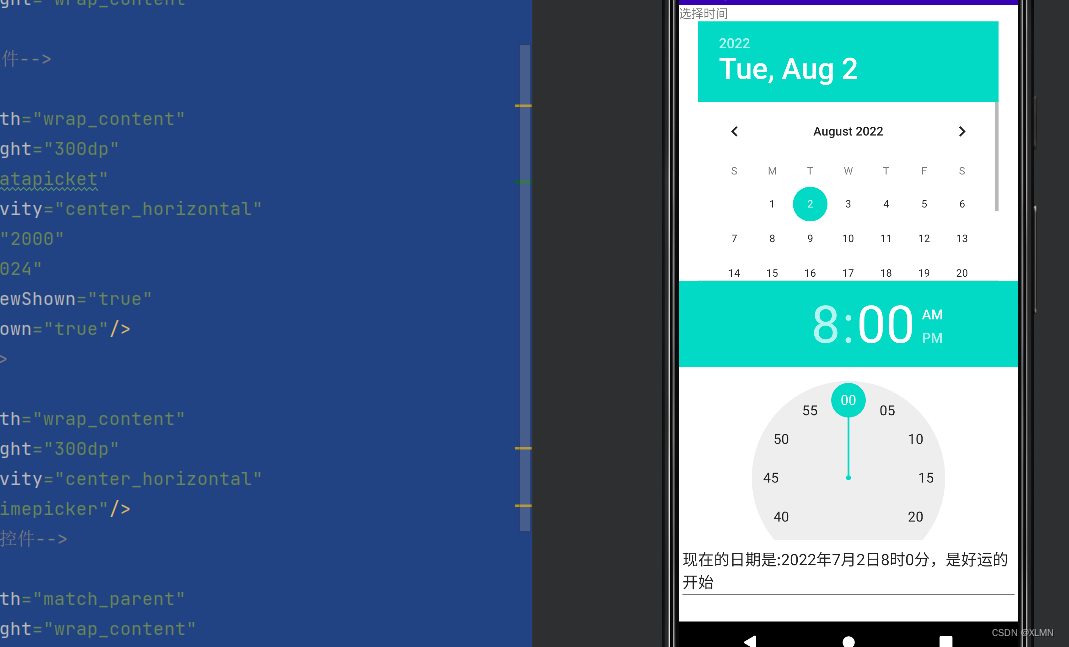
Dateticket and timeticket, functions and usage of date and time selectors
Toast will display a simple prompt message on the program interface
Biped robot controlled by Arduino
责任链模式 - Unity
随机推荐
使用OneDNS完美解决办公网络优化问题
Matplotlib绘图界面设置
【可信计算】第十二次课:TPM授权与会话
calendarview日历视图组件的功能和用法
Functions and usage of serachview
企业经营12法的领悟
LeetCode 648(C#)
网络攻防复习篇
Establishment of solid development environment
第二十四届中国科协湖南组委会调研课题组一行莅临麒麟信安调研考察
【可信计算】第十三次课:TPM扩展授权与密钥管理
【分布式理论】(一)分布式事务
【重新理解通信模型】Reactor 模式在 Redis 和 Kafka 中的应用
【OKR目标管理】案例分析
深度学习机器学习各种数据集汇总地址
Pytorch中自制数据集进行Dataset重写
手机app外卖订餐个人中心页面
【网络攻防原理与技术】第6章:特洛伊木马
Function and usage of calendar view component
大笨钟(Lua)