当前位置:网站首页>Xin'an Second Edition; Chapter 11 learning notes on the principle and application of network physical isolation technology
Xin'an Second Edition; Chapter 11 learning notes on the principle and application of network physical isolation technology
2022-07-06 17:34:00 【Moon Dream Studio】
One 、 The outline of this chapter requires
11、 Principle and application of network physical isolation technology
11.1 Overview of network physical isolation
• The concept of network physical isolation • Working principle of network physical isolation
11.2 Network physical isolation system and type
• Composition of network physical isolation system • Two way network physical isolation system
• One way network physical isolation system • Terminal physical isolation system
11.3 Network physical isolation mechanism and Implementation Technology
• Special purpose computers • many PC• Internet proxy service • Internal and external network line switcher
• Internal and external partitions of a single hard disk • Dual hard disk
• Gatekeeper • Protocol isolation technology • Unidirectional transmission unit • Information ferry Technology • Physical disconnection Technology
11.4 Main technical indicators and products of network physical isolation
• Main technical indicators of network physical isolation ( Understanding of functional technical indicators 、 Understanding of performance and technical indicators 、 Understanding of safety technical indicators )
• Analysis of working mechanism of network physical isolation products 、 Understanding of network physical isolation product standards 、 Applicable scenarios of network physical isolation products
11.5 Network physical isolation Application
• Intranet users can safely access the Internet
• The business production network is isolated from the Internet
• Internal and external network security physical isolation
• Information exchange in different security areas
Two 、 List of important and easy knowledge points in this chapter
11.1 Overview of network physical isolation
In order to achieve a higher level of network security , Network security experts suggest ,“ Internal and external networks and online computers realize physical isolation , In order to reduce the threat from the Internet ”.《 Regulations on the confidentiality management of the international networking of computer information systems 》 Article 6 of Chapter II stipulates ,“ A computer information system involving state secrets , It shall not be directly or indirectly connected with the Internet or other public information networks , Physical isolation must be carried out .”
It can meet the information and data exchange needs of internal and external networks , Security technology, which can prevent network security incidents, came into being , This technology is called “ Physical isolation
边栏推荐
- Wu Jun trilogy insight (IV) everyone's wisdom
- Solrcloud related commands
- Redis快速入门
- 自动答题 之 Selenium测试直接运行在浏览器中,就像真正的用户在操作一样。
- Development and practice of lightweight planning service tools
- 自动化运维利器ansible基础
- Concept and basic knowledge of network layering
- [mmdetection] solves the installation problem
- How does wechat prevent withdrawal come true?
- [reverse primary] Unique
猜你喜欢
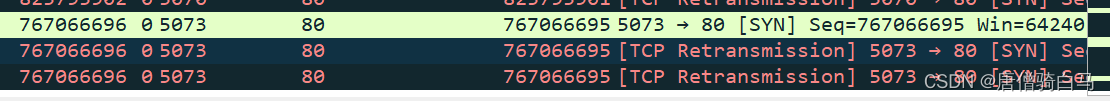
TCP connection is more than communicating with TCP protocol

The most complete tcpdump and Wireshark packet capturing practice in the whole network
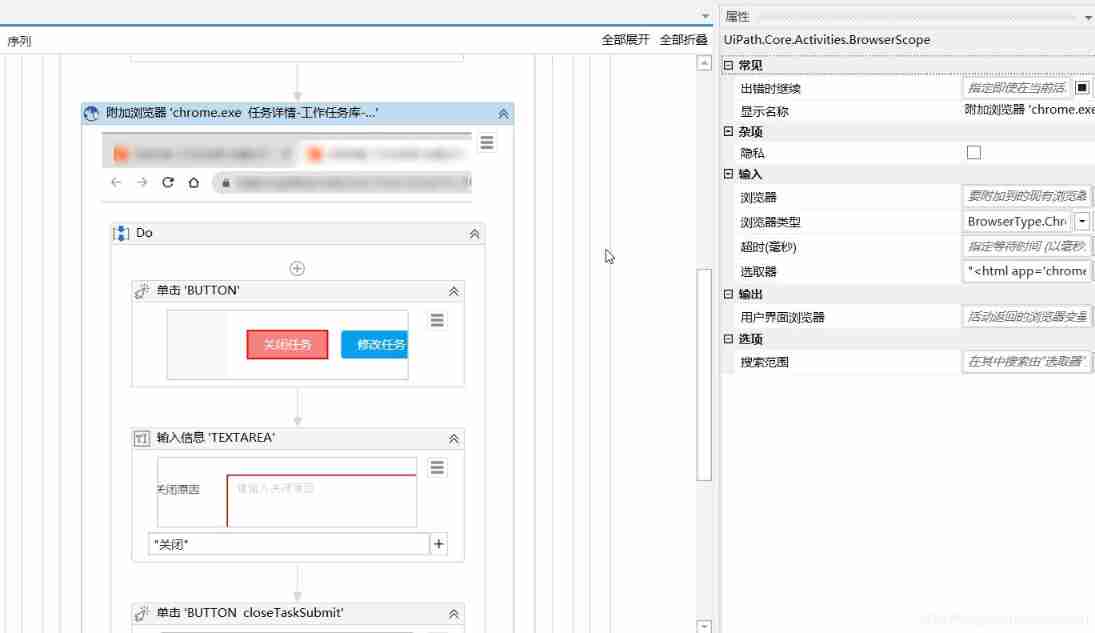
Uipath browser performs actions in the new tab

关于Selenium启动Chrome浏览器闪退问题
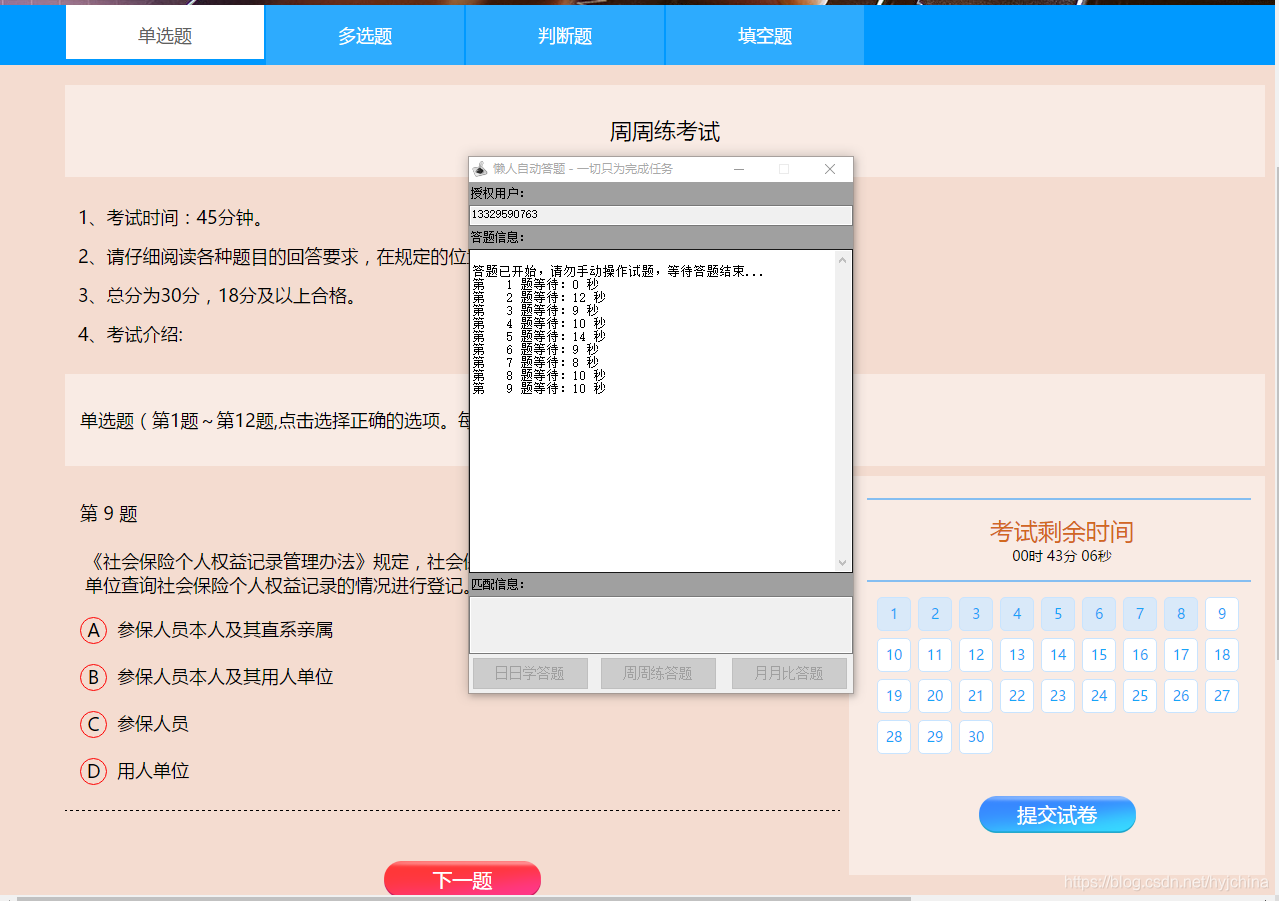
自动答题 之 Selenium测试直接运行在浏览器中,就像真正的用户在操作一样。
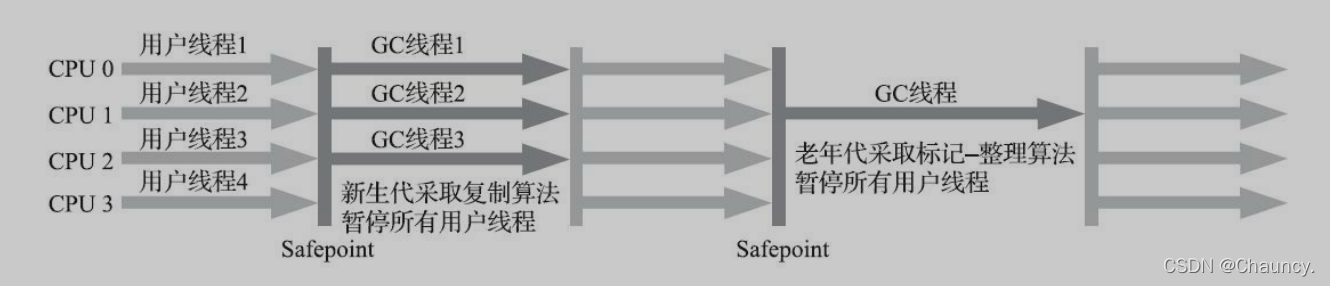
JVM 垃圾回收器之Serial SerialOld ParNew
Application service configurator (regular, database backup, file backup, remote backup)
Automatic operation and maintenance sharp weapon ansible Foundation
Garbage first of JVM garbage collector
Akamai talking about risk control principles and Solutions
随机推荐
C version selenium operation chrome full screen mode display (F11)
List集合数据移除(List.subList.clear)
案例:检查空字段【注解+反射+自定义异常】
Shawshank's sense of redemption
数据仓库建模使用的模型以及分层介绍
[ciscn 2021 South China]rsa writeup
Wu Jun's trilogy insight (V) refusing fake workers
2021-03-22 "display login screen during recovery" can't be canceled. The appearance of lock screen interface leads to the solution that the remotely connected virtual machine can't work normally
TCP连接不止用TCP协议沟通
mysql 基本增删改查SQL语句
Some feelings of brushing leetcode 300+ questions
SQL调优小记
Akamai 反混淆篇
手把手带你做强化学习实验--敲级详细
JVM之垃圾回收器下篇
CTF reverse entry question - dice
【MMdetection】一文解决安装问题
信息与网络安全期末复习(完整版)
Flink 解析(六):Savepoints
Flink parsing (IV): recovery mechanism