当前位置:网站首页>Final review of information and network security (based on the key points given by the teacher)
Final review of information and network security (based on the key points given by the teacher)
2022-07-06 17:22:00 【bestkasscn】
The final chapter Key points sorted out by the teacher
1.1 Advantages and disadvantages of symmetric cryptosystem
advantage : Algorithm disclosure 、 A small amount of calculation 、 Fast encryption 、 High encryption efficiency .
shortcoming : How to securely transfer keys ( If the key is intercepted on the network GG)、 The number of keys needed for multi person distribution will increase rapidly .
1.2 AES The encryption process of the algorithm
To be improved ..
1.3 DES The encryption process of the algorithm
To be improved ..
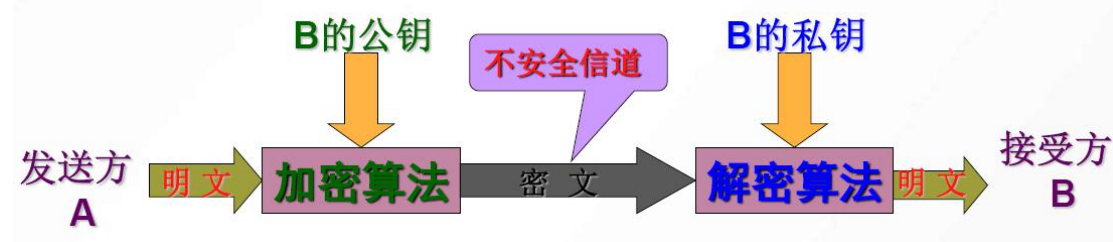
1.4 The running process of public key cryptosystem model
- The sender A Find the receiver B The public key
- A Using public key encryption algorithm B Encrypt plaintext with your public key
- A Send ciphertext to via insecure channel B
- B After receiving the ciphertext, decrypt the ciphertext with your own private key to restore the plaintext
1.5 The main functions of intrusion detection system
- Monitor and analyze user and system activities
- Check system configuration and vulnerabilities
- Evaluate the integrity of key resources and data files of the system
- Identify known attacks
- Statistical analysis of abnormal behavior
- Operating system log management , And identify user activities that violate security policies
1.6 The encryption process of a data encryption system
A password ( encryption ) The system consists of plaintext 、 Ciphertext 、 encryption algorithm 、 Decryption algorithm 、 The key consists of five parts .
- Plaintext M: The original information as encrypted input , That is, the original form of the message
- Ciphertext C: The result of encrypted transformation of plaintext , That is, the form of the message after being encrypted
- secret key K: Is the parameter involved in password transformation
- encryption algorithm E: Is a transformation function that transforms plaintext into ciphertext , The corresponding transformation process is called encryption , That is, the process of coding
- Decryption algorithm D: Is the transformation function that restores the ciphertext to plaintext , The corresponding transformation process is called decryption
The encryption process is plaintext M Encrypted algorithm E( Some encryption algorithms require a key K As a parameter ) After transformation, we get the ciphertext C.
1.7 intrusion detection system IDS Signal analysis methods and their advantages and disadvantages
- Pattern matching : Compare the collected information with the known database of network intrusion and system misuse patterns .
- advantage : accuracy 、 Efficient
- shortcoming : Need to keep updating , Unable to detect an attack that has not occurred
- Statistical analysis : First, create a statistical description for the system object , Count some measurement properties in normal use . Any observation outside the normal range , It is considered that an invasion has occurred .
- advantage : Unknown and more complex intrusions can be detected
- shortcoming : False positives 、 High underreporting rate
- Integrity analysis : Integrity analysis focuses on whether a file or object has been changed , Strong encryption mechanisms are usually used ( Such as Hash function ) To identify small changes .
- advantage : Can detect any changes to files or objects caused by the attack
- shortcoming : Unable to respond in real time , Can only be analyzed afterwards
1.8 What is an attack 、 Common attack methods
attack : Only when the intrusion is completely completed , And the behavior that the intruder has entered the target network is called attack . But a more positive view is : All actions that may damage a network are called attacks . That is, from the moment when an intruder starts working on the target plane , The attack begins .
Common means
- Password intrusion
- Backdoor software means
- Monitoring method
- E-mail technology
- Electronic deception
- DoS attack ( Denial of service attacks )
1.9 Basic measures for network security protection
Install firewall 、 Set access control 、 Using data encryption 、 Strengthen intrusion detection 、 Blocking the route of transmission 、 Improve the quality of personnel
1.10 Common password attack techniques
Weak password 、 Dictionary attack 、 Blast 、 Trojans steal
1.11 Commonly used DoS Attack methods
- TCP SYN Flood attack ( Flooding attacks learned in Computer Networks , utilize TCP defects , Send a lot of fake TCP Connection request , Instead, it is an attack method of resource exhaustion )
- IP Deceptive attack ( Use IP cheating , Force the server to reset the connection of legitimate users , Affect the connection of legitimate users .)
- Bandwidth attack ()
1.12 The working principle and process of intrusion detection system
information gathering
Location : Several different key points in computer network system ( Different network segments and different hosts ) To collect information .
(1) Expand the detection range
(2)“ Uniformity ” testing
Content : Including systems 、 The Internet 、 Status and behavior of data and user activities
quality : Information correctness and reliability
Intrusion detection information source
System and network log files : The use of system and network log file information is a necessary condition for intrusion detection .
Undesired changes in directories and files : Restrict access to or modify system log files under normal circumstances .
Unexpected behavior in program execution
Intrusion information in physical form
(1) Unauthorized connection to network hardware
(2) Authorized access to physical resources
Data analysis
- Pattern matching : Compare the collected information with the known database of network intrusion and system misuse patterns .
- advantage : accuracy 、 Efficient
- shortcoming : Need to keep updating , Unable to detect an attack that has not occurred
- Statistical analysis : First, create a statistical description for the system object , Count some measurement properties in normal use . Any observation outside the normal range , It is considered that an invasion has occurred .
- advantage : Unknown and more complex intrusions can be detected
- shortcoming : False positives 、 High underreporting rate
- Integrity analysis : Integrity analysis focuses on whether a file or object has been changed , Strong encryption mechanisms are usually used ( Such as Hash function ) To identify small changes .
- advantage : Can detect any changes to files or objects caused by the attack
- shortcoming : Unable to respond in real time , Can only be analyzed afterwards
- Pattern matching : Compare the collected information with the known database of network intrusion and system misuse patterns .
1.13 intrusion detection system IDS Common response processing
- Warning and event reporting .
- Terminate the process , Force user to exit .
- Cut off the Internet connection , Modify firewall settings .
- Disaster assessment , Automatic recovery .
- Find and locate attackers .
1.14 Characteristics of computer virus
- Cannot be run as a stand-alone executable
- Copy yourself
- Activate the virus by executing the host program
- Cross platform
1.15 Common network virus prevention measures
- anti-virus software
- Don't browse irregular websites
- Cultivate a conscious awareness of information security
- use Windows Update The function is patched in the whole system
1.16 The characteristics and main research contents of information hiding
Robustness
The effect of camouflaged objects on hidden information “ Compatibility ”
Non detectability
Good statistical properties , Unable to determine whether there is hidden information
transparency
The target data has not changed significantly
Security
The hiding algorithm has strong anti attack ability
Self recovery
A small amount of data information , Recover hidden information
1.17 Characteristics and application of digital watermarking technology
characteristic
Security
Difficult to tamper with or falsify ; Low false detection rate ; The digital watermark changes with the content .
Concealment
Imperceptible , Do not reduce the use value .
Robustness
After going through a variety of unintentional or intentional signal processing processes , The digital watermark can still maintain partial integrity and be accurately identified .
Watermark capacity
Sufficient watermark capacity , That is, the amount of watermark information that the carrier can embed without deformation .
application
- copyright protection
- Digital fingerprinting
- Certification and integrity verification
- Content identity and hidden identity
- Use control
- Content protection
1.18 Performance evaluation of digital watermarking
- Imperceptibility
- Damage to the carrier
- Subjective evaluation
- objective evaluation
- Watermark capacity 、 Imperceptibility 、 The balance between robustness
1.19 Functions and functions of firewall
Network security barrier
Strengthen network security strategy
Based on the following four technologies
- Service control —— Determine the types of network services that can be accessed . The firewall can be in IP Address and TCP Filter traffic based on port number .
- Direction control —— Determine the direction in which specific service requests flow through the firewall .
- User control —— Access to a service is controlled according to which user tries to access the service .
- behavior control —— Control how specific services are used .
Monitor and audit network access and access
Prevent internal information leakage
Protect Intranet Security
1.20 What are the advantages of Distributed Firewalls
- Applicable to server hosting ( Big data center )
- Enhanced system security ( Intrusion detection )
- Eliminate structural bottlenecks , Improved system performance ( A single access point )
- Expand with the system ( Distributed features )
- It is more widely used and supports VPN signal communication
1.21 VPN The key technology
- Tunneling Protocol
- Certification Technology
- Encryption technology
- Key exchange and management
边栏推荐
- When it comes to Google i/o, this is how ByteDance is applied to flutter
- 吴军三部曲见识(七) 商业的本质
- JVM之垃圾回收器上篇
- 唯有学C不负众望 TOP2 p1变量
- On the clever use of stream and map
- Train 100 pictures for 1 hour, and the style of the photos changes at will. There is a demo at the end of the article | siggraph 2021
- 8086 segmentation technology
- 服务器端渲染(SSR)和客户端渲染(CSR)的区别
- Activit零零碎碎要人命的坑
- Akamai talking about risk control principles and Solutions
猜你喜欢
随机推荐
JVM 垃圾回收器之Garbage First
Alibaba cloud server builds SVN version Library
Some feelings of brushing leetcode 300+ questions
List set data removal (list.sublist.clear)
mysql 基本增删改查SQL语句
连接局域网MySql
JS garbage collection mechanism and memory leakage
[VNCTF 2022]ezmath wp
程序员定位解决问题方法论
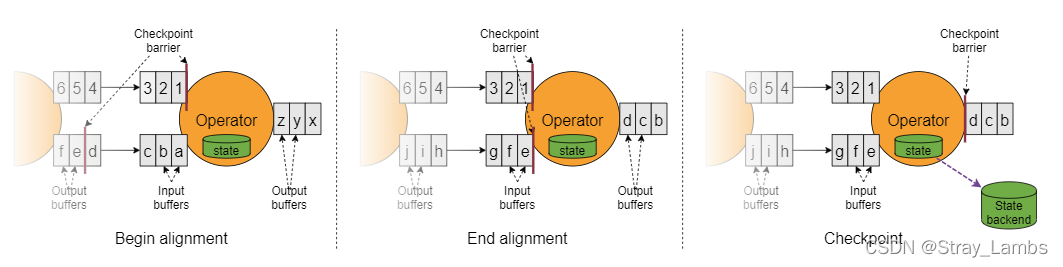
Flink 解析(五):State与State Backend
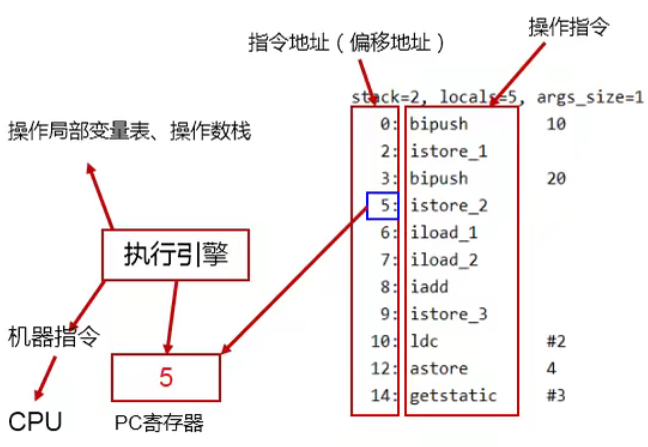
DOS function call
GCC error: terminate called after throwing an instance of 'std:: regex_ error‘ what(): regex
暑假刷题嗷嗷嗷嗷
Akamai浅谈风控原理与解决方案
Activiti directory (V) reject, restart and cancel process
Instructions for Redux
Activiti directory (IV) inquiry agency / done, approved
吴军三部曲见识(七) 商业的本质
關於Stream和Map的巧用
唯有学C不负众望 TOP4 S1E6:数据类型