当前位置:网站首页>Wireshark grabs packets to understand its word TCP segment
Wireshark grabs packets to understand its word TCP segment
2022-07-06 07:52:00 【Taylor lance】
First, let's grab the bag , Because we have to analyze TCP, therefore wireshark Set it up in , hold http and tls Analytical removal , Specific operation :
Analyze->Enabled Protols-> Cancel http\http2\Tls, Then the packet capture image as shown in the figure below appears :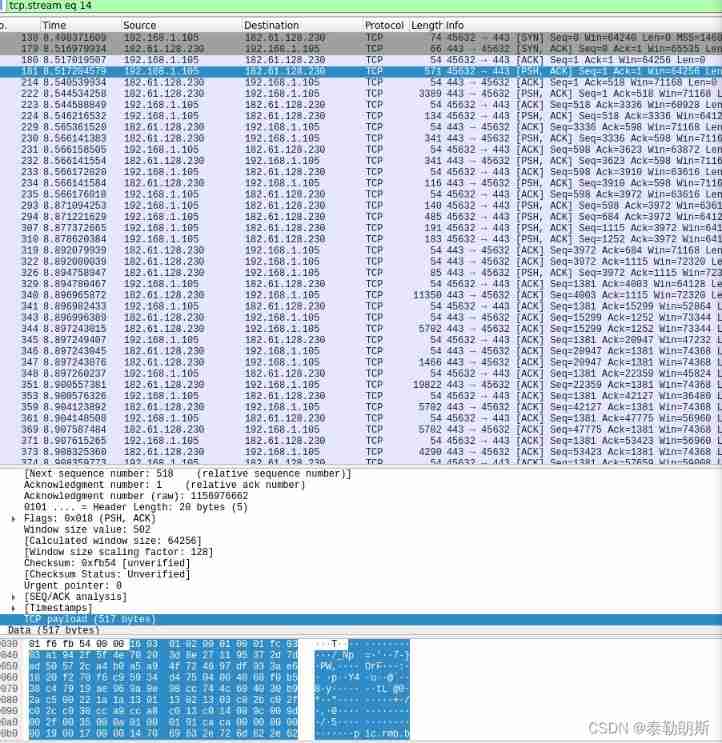
It is clear that this is a bag with three handshakes .
1、 First, let's look at two points when shaking hands three times :a) Confirmation of initial serial number b)Mss confirm
The picture below is TCP Header of message , It's usually 20 Bytes ( Does not contain option data )
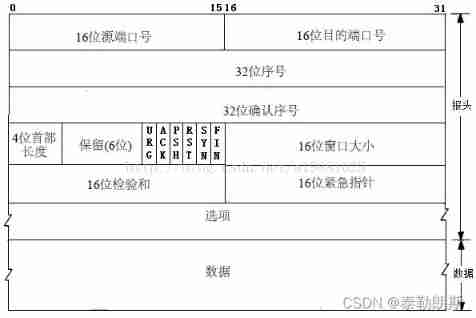
First we see the port , The port is TCP/UDP A very important field in the Protocol , This is a very important sign of communication between the transport layer and the network layer , With the port transport layer, you know which application to send the data of this layer .
Now let's look at the serial number and confirmation serial number ,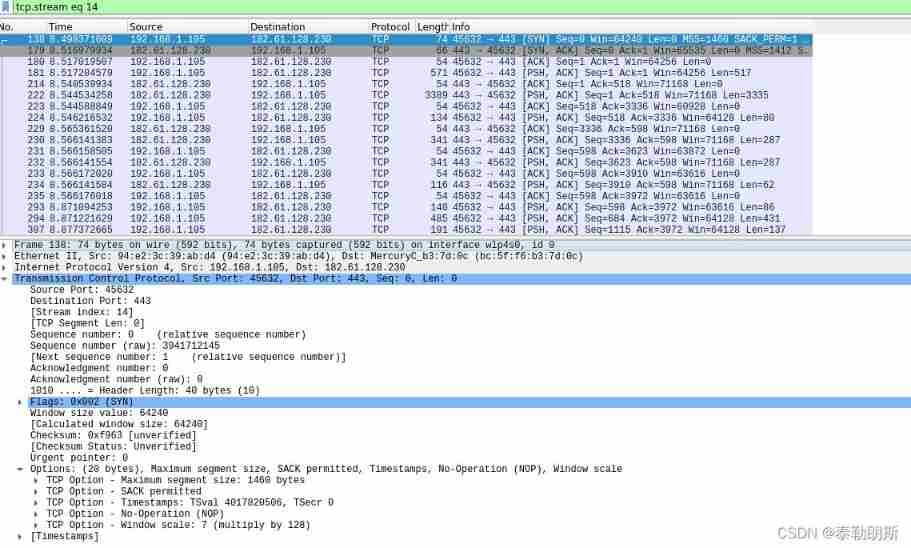
The screenshot above is the first one in the handshake stage TCP The message TCP Screenshot of agreement section , From the way we saw , The source port is 45632, The target port is 443, See below [] The internal data is wireshark Auxiliary information of parsing , We can leave it alone , The next step is Sequence number:0 This is a relative serial number , You can see one below (raw) Express TCP The real serial number of the package , The relative need is wireshark Set up , The real serial number is usually a random value , Indicates the starting serial number when I contract , next AcknowledgeMent Indicates that you expect to receive the serial number of the other party , The back is FLags, Window size , The checksum , Pointer to an emergency , Options , For this package, we found that the options are 20 Bytes , After expansion, you can see, for example SACK( Option confirmation ) Options ,Window scal etc. ( These parameters are very useful ), We see that the size of this bag is 74 Bytes , So how did this byte come from :TCP+IP+Eth=20+20+20+14,TCP head 40 Bytes ,IP head 20 Bytes , Ethernet 14 Bytes .
Serial number Description : The first serial number I sent is 3941712145, The expected serial number is 0, Because it's the first handshake , Don't know the starting serial number of the other party , So set to 0
Next :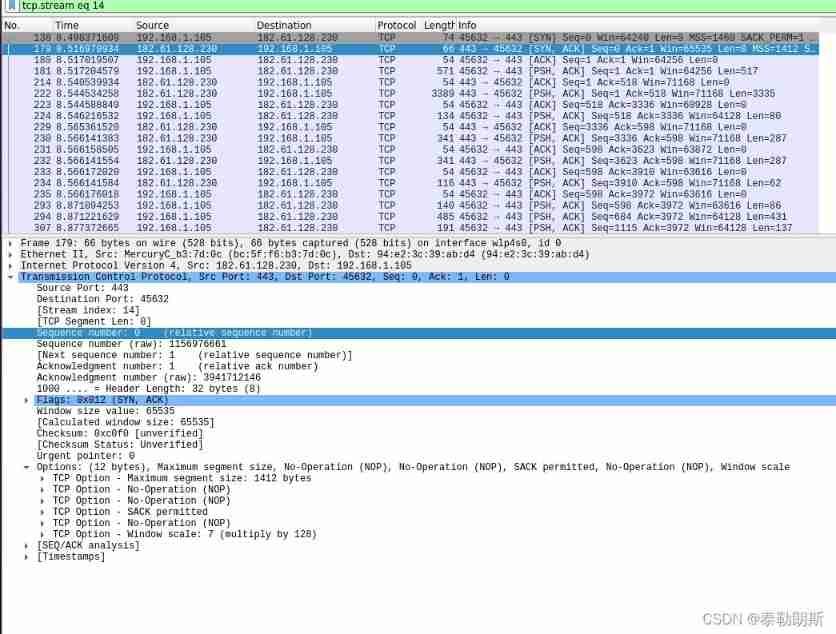
Serial number : My starting number is 1156976661, Expect to receive 3941712145+1
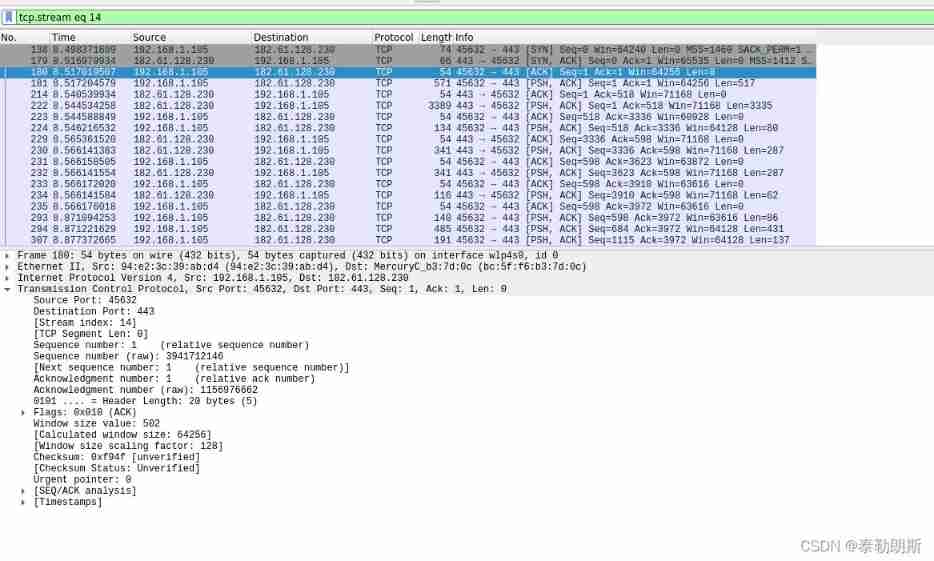
Serial number : The serial number I sent is 1( relative ), Expect to receive 1( relative )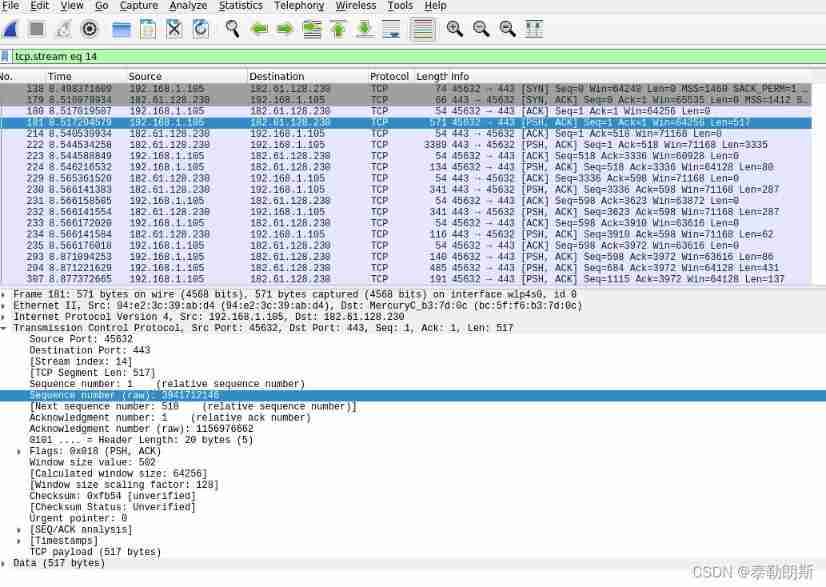
This TCP Marked as PSH ACK , because TCP It is two-way connected , So each packet is connected by another ACK, That is, every packet is ACK Why , that PSH What does that mean . This is what the book says PSH -[ The receiver should pass this data to the application as soon as possible ], To put it bluntly, the data in the network card is not uploaded to the application layer every time a little data comes , So when is the application layer recv To receive data , You guessed it , This is the sign , Or the cache is full . Received this sign TCP After package , The application layer can read all the data in the cache to the application layer . therefore PSH It probably means that the sender indicates that there is no data later , Please deal with it as soon as possible . Sometimes there is a sign in the fourth wave stage 【PSH FIN ACK】
Serial number : The starting sequence number of the data I send is 1, Expect to receive serial number 1 My bag
We found that , This TCP The data length in is 517 byte , Then we predict what the other party will send ACK Should be seq=1,ACK=157+1=158
It's true
Then look at :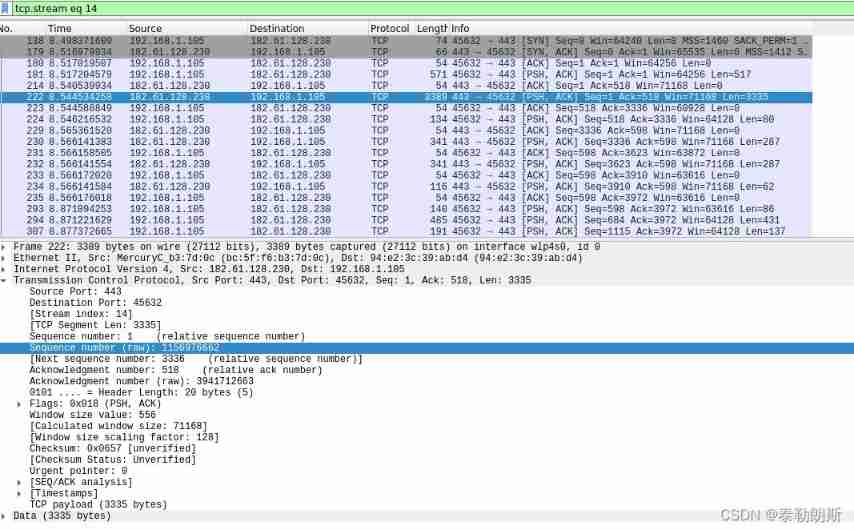
Serial number : The serial number I sent is 1, Data length is 3335, Expect to receive 518 Serial number data of
The other side replied : I sent 518 Start packet , expect 3336 Data packets
And so on , occasionally TCP It's not like replying to a package ACK, Instead, it will reply to a final serial number package after accumulating a certain amount , This shows that the previous packets have been received , And it will increase ACK The robustness of , For example, a certain ACK Have not received , Just the last one ACK received , Then it will not lead to repeated data transmission .
边栏推荐
- Luogu p4127 [ahoi2009] similar distribution problem solution
- [CF Gym101196-I] Waif Until Dark 网络最大流
- TS 体操 &(交叉运算) 和 接口的继承的区别
- Compliance and efficiency, accelerate the digital transformation of pharmaceutical enterprises, and create a new document resource center for pharmaceutical enterprises
- edge瀏覽器 路徑獲得
- 08- [istio] istio gateway, virtual service and the relationship between them
- Transformer principle and code elaboration
- 数据治理:微服务架构下的数据治理
- 继电反馈PID控制器参数自整定
- Typescript interface and the use of generics
猜你喜欢
Sanzi chess (C language)
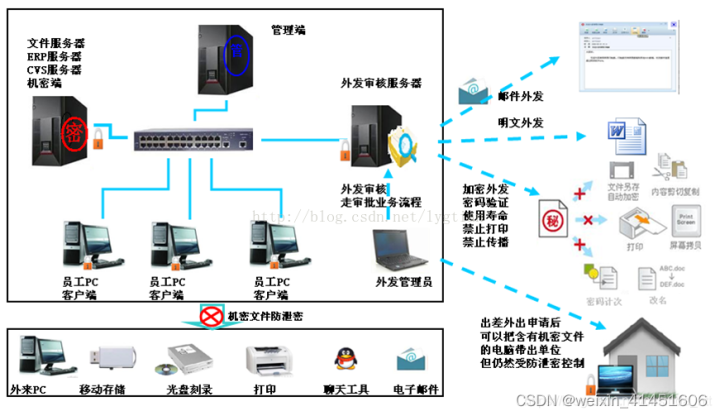
烧录场景下的源代码防泄密方案分享

Mex related learning
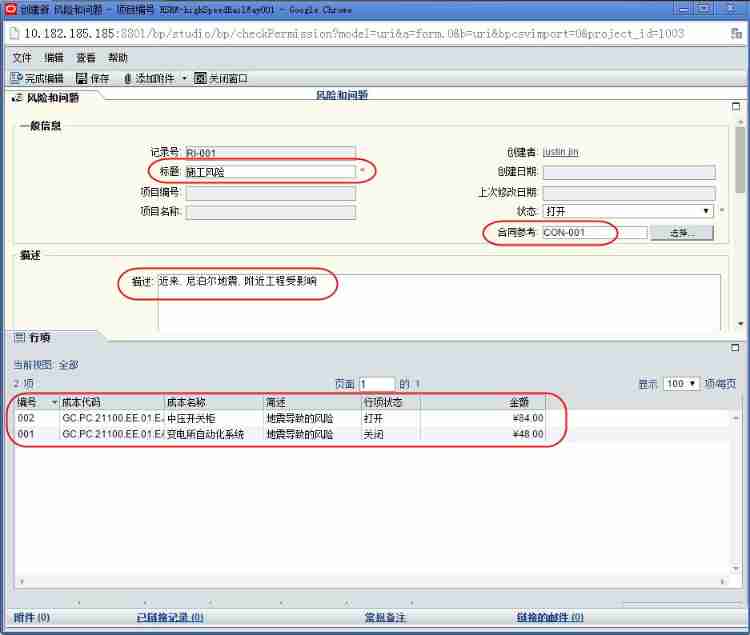
Risk planning and identification of Oracle project management system

Interview Reply of Zhuhai Jinshan
![[nonlinear control theory]9_ A series of lectures on nonlinear control theory](/img/a8/03ed363659a0a067c2f1934457c106.png)
[nonlinear control theory]9_ A series of lectures on nonlinear control theory
21. Delete data

Simulation of Teman green interferometer based on MATLAB
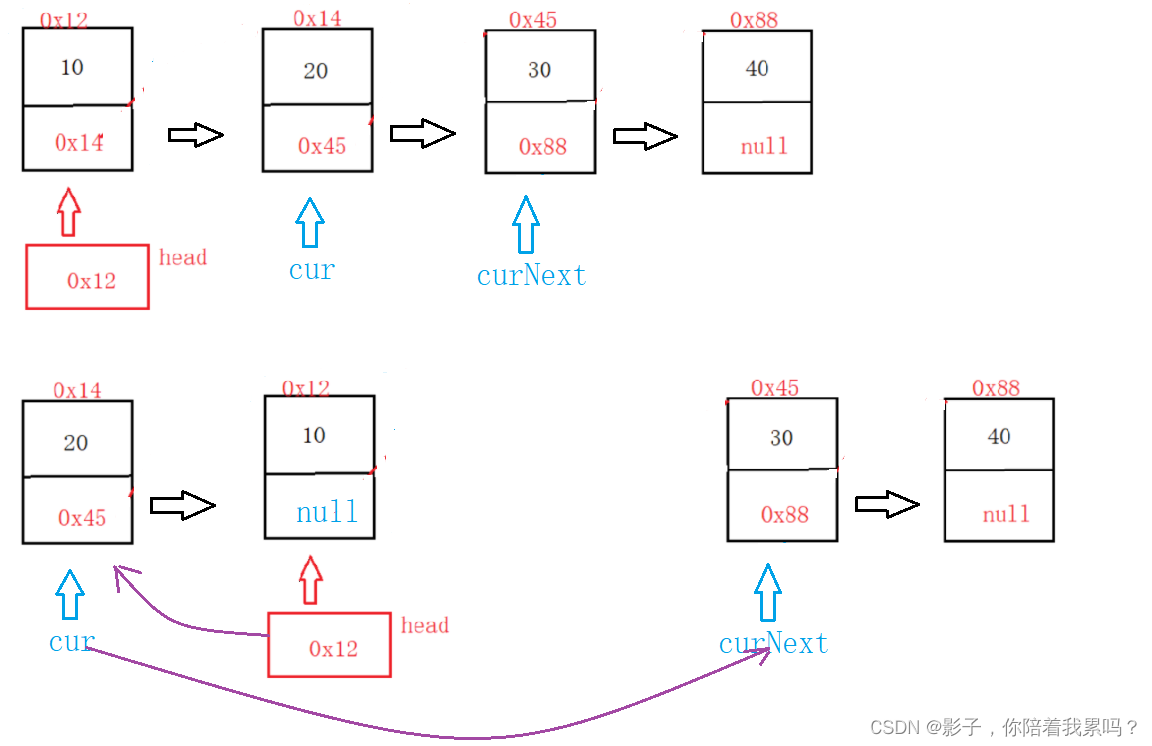
Linked list interview questions (Graphic explanation)

How to delete all the words before or after a symbol in word
随机推荐
Uibehavior, a comprehensive exploration of ugui source code
Data governance: metadata management
P3047 [usaco12feb]nearby cows g (tree DP)
智能终端设备加密防护的意义和措施
Methods for JS object to obtain attributes (. And [] methods)
烧录场景下的源代码防泄密方案分享
Typescript interface and the use of generics
Leecode-c language implementation -15 Sum of three ----- ideas to be improved
Simulation of holographic interferogram and phase reconstruction of Fourier transform based on MATLAB
[非线性控制理论]9_非线性控制理论串讲
opencv学习笔记九--背景建模+光流估计
TS 体操 &(交叉运算) 和 接口的继承的区别
Force buckle day31
[nonlinear control theory]9_ A series of lectures on nonlinear control theory
Pangolin Library: control panel, control components, shortcut key settings
[window] when the Microsoft Store is deleted locally, how to reinstall it in three steps
C intercept string
PHP Coding Standard
Pre knowledge reserve of TS type gymnastics to become an excellent TS gymnastics master
珠海金山面试复盘