当前位置:网站首页>6-6 vulnerability exploitation SSH security defense
6-6 vulnerability exploitation SSH security defense
2022-07-07 02:33:00 【Mountain Rabbit 1】
SSH Modify the default port
By default ,SSH Use 22 port . For the sake of safety , Generally, the default port will be modified .
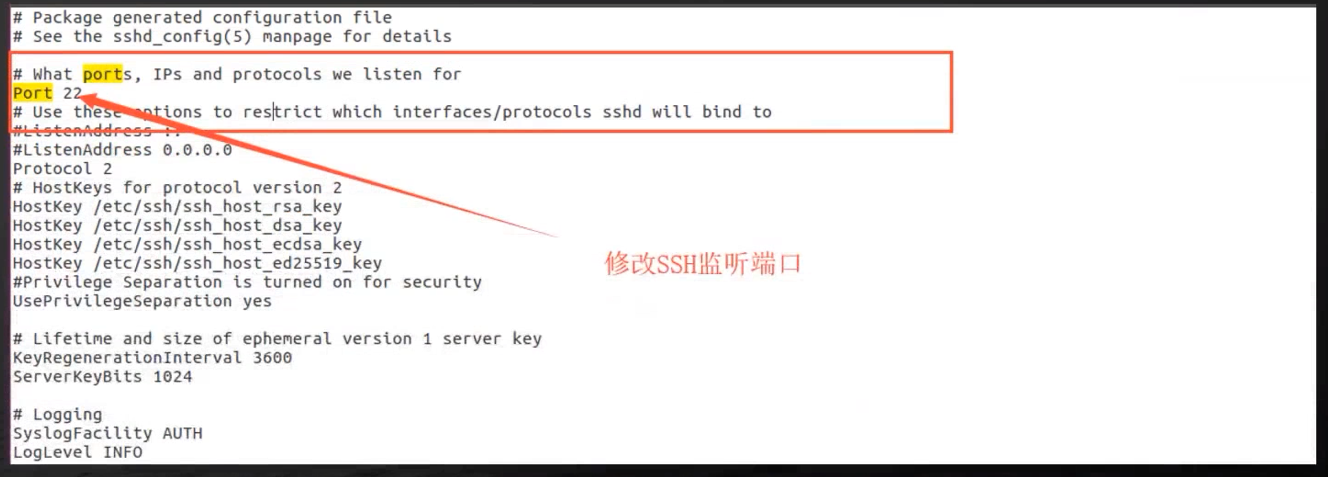
modify 22 For other port numbers , Thus, our listening port is modified
Be careful : You must restart after modification SSH service , Only in this way can our configuration file , In the process of restarting , Reload , Thus effective .
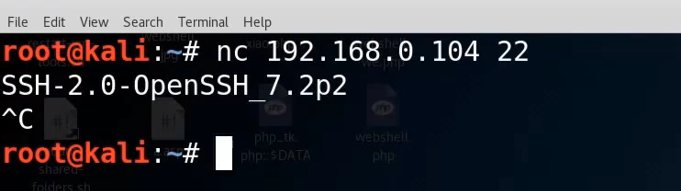
Turn on ubuntu Of ssh service function , stay kali Detect in the middle
nc 192.168.0.104 22
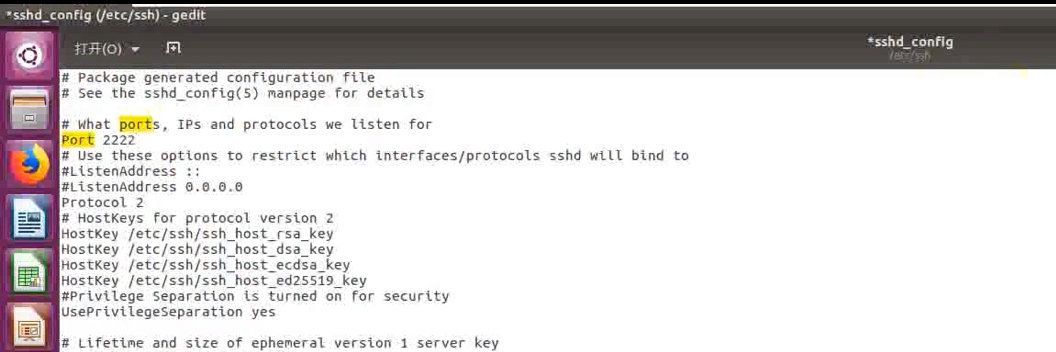
stay ubuntu among , Modify port number
cd /etc/ssh/
ls
sudo gedit sshd_config
2222
service ssh restart
service ssh status

netstat -pantu
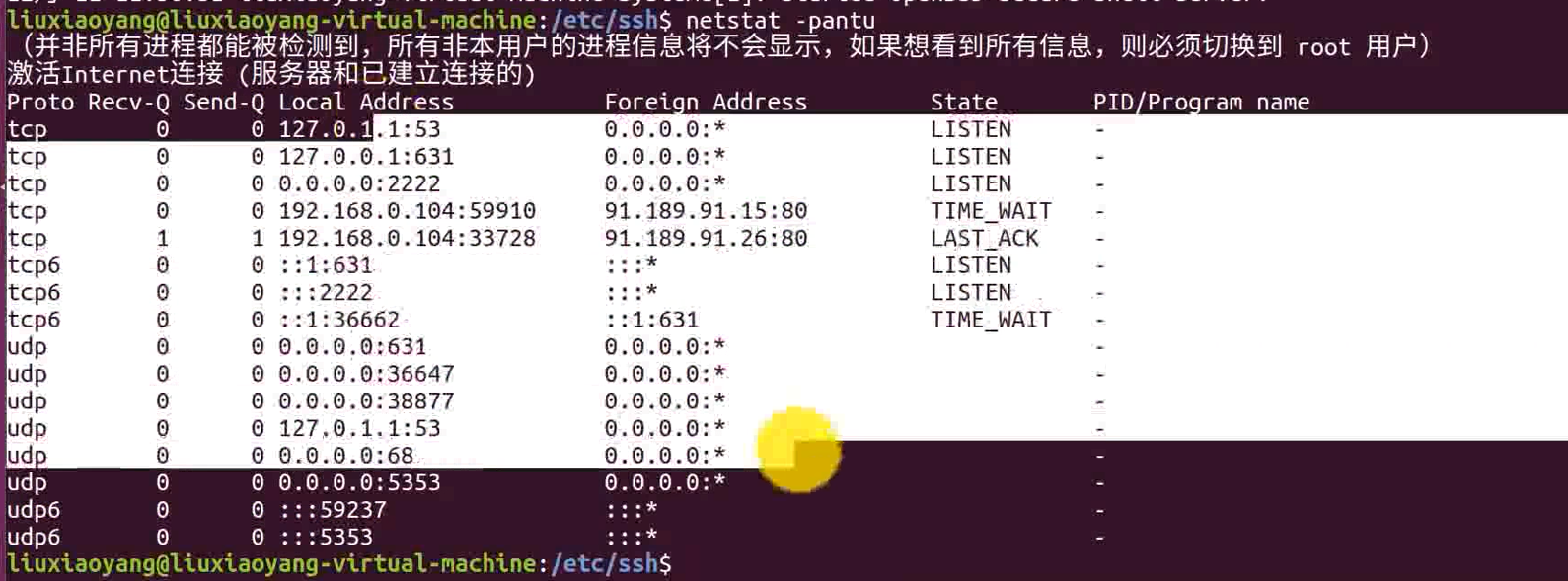
nc 192.168.0.104 22
nc 192,168.0.104 2222
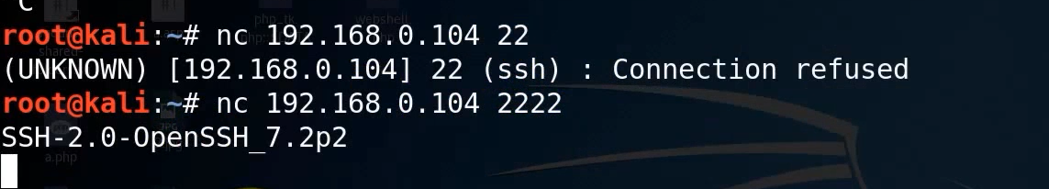
Modify the function of the default port , So we can't use it directly 22 Port number connection , Further detection is needed , Detection ssh Listening port , To make the corresponding connection
SSH Set up PGP Sign in
By default ,SSH Use user name and password for remote login , Will cause violent cracking , Keep trying user names and passwords , So as to log in to the system , In order to prevent this process , adopt putty This software , To generate the corresponding private key , Configure the private key , Authentication , So that we can log in without user password , More secure , Prevent violent cracking
Generate SSH Key pair , Use puttygen.
Download link :https://www.chiark.greenend.org/~sgtatham/putty/latest.html
Click on Generate Generate the private key
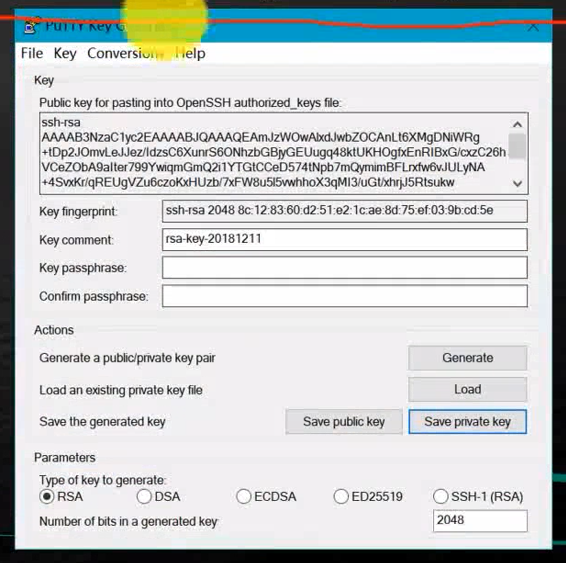
Click on save private key, It will be generated on the desktop .ppk, This name can also be named by yourself
SSH Set up PGP Sign in
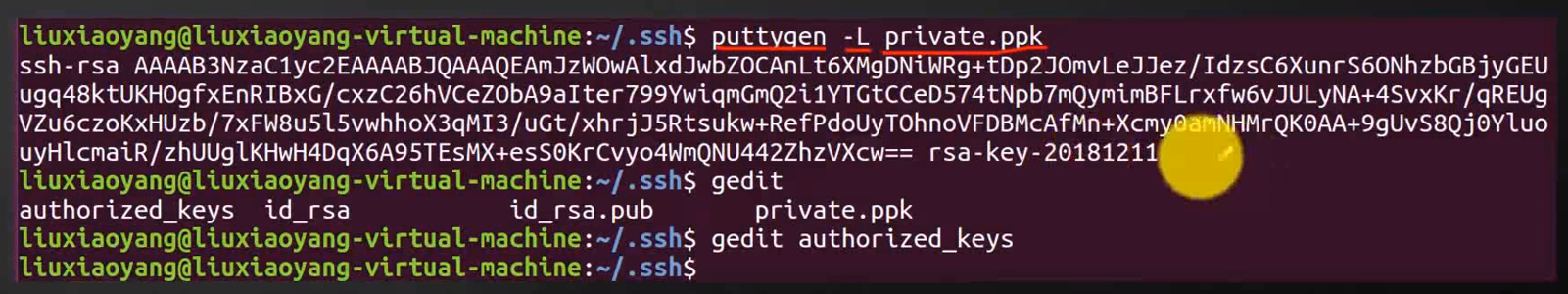
Use ssh-keygen Command in Linux Generate .ssh Catalog , stay .ssh Create a new key storage file authorized_keys, And copy the private key file to .ssh Under the table of contents . Use command puttygen -L “ Copy the private key file ”, Copy content to authorized_keys In file .
ssh-keygen
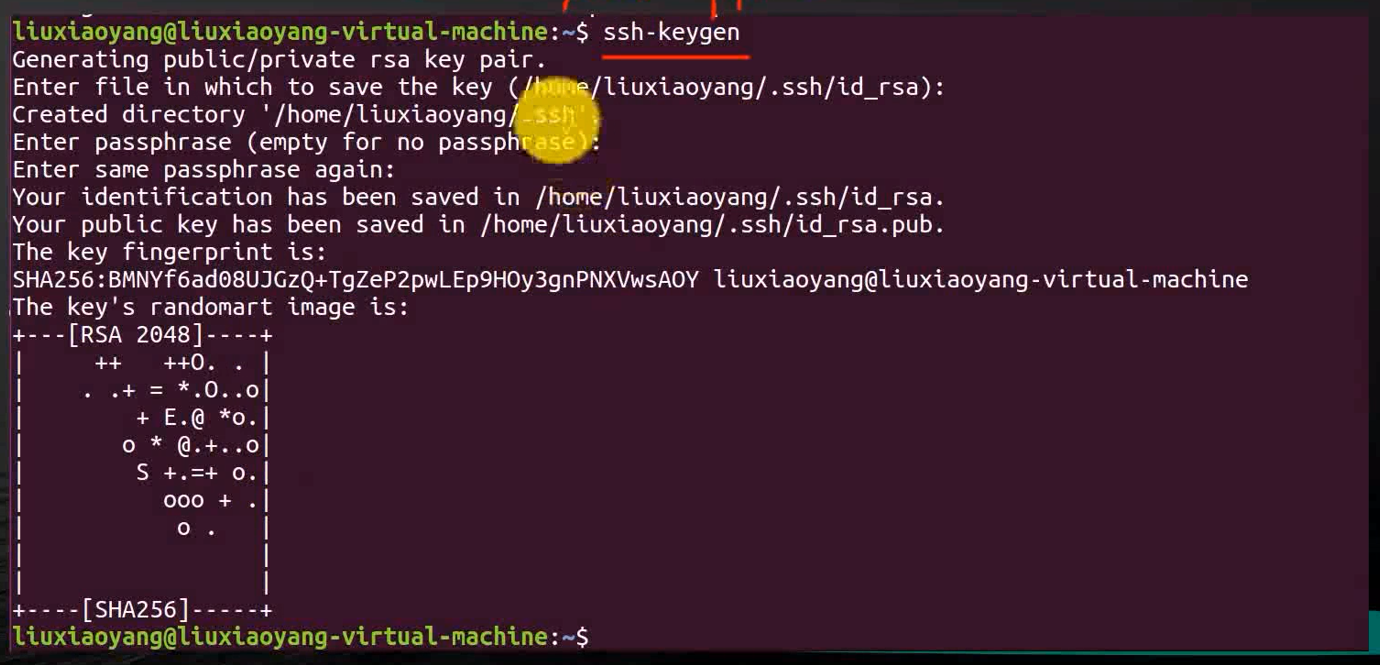
This time will be in /home/liuxiaoyang/ Generate hidden directory under .ssh, Switch to .ssh, new directory authorized_keys
SSH Set up PGP Sign in
Use Putty The client loads the private key file to connect .
Click on auth
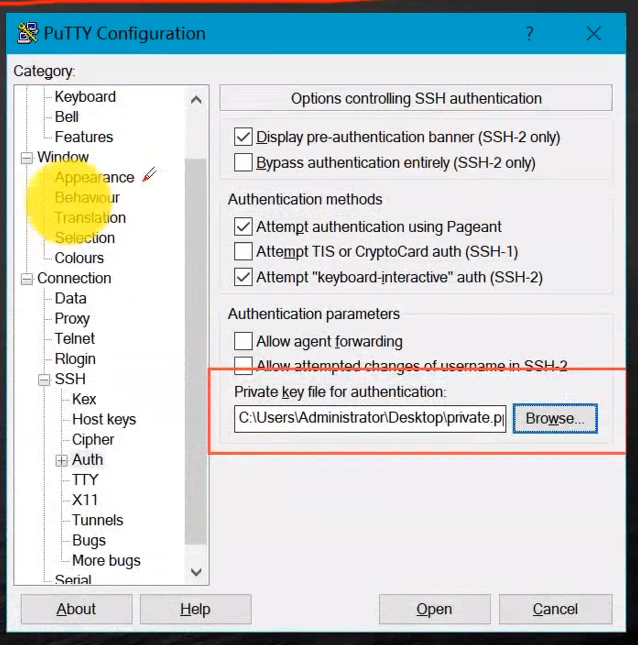
After loading , We are connecting , You don't need to enter the corresponding connection password , Only need Data Enter the user name in
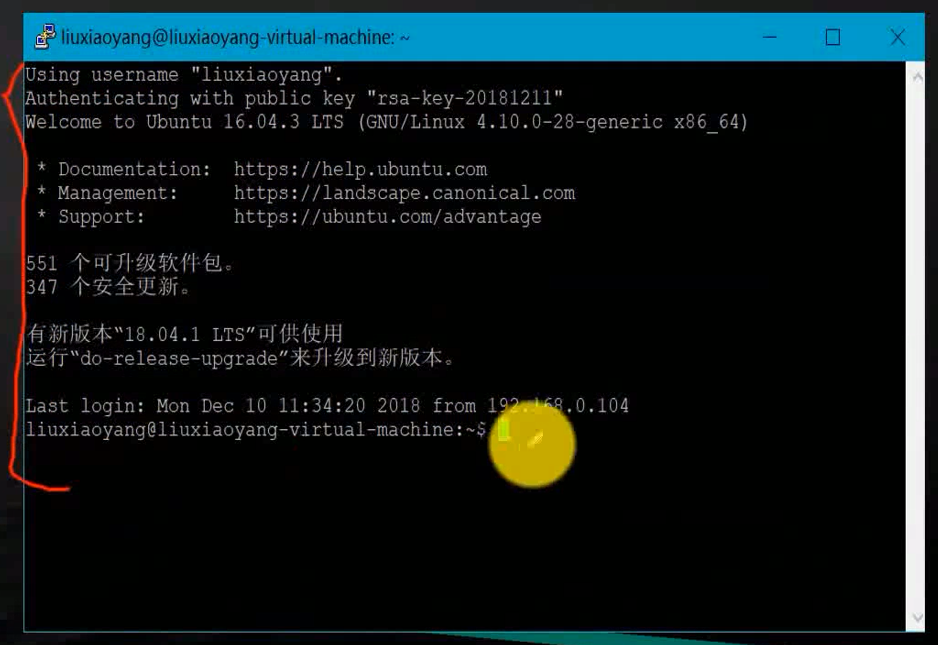
cd ~
pwd
ls -alh
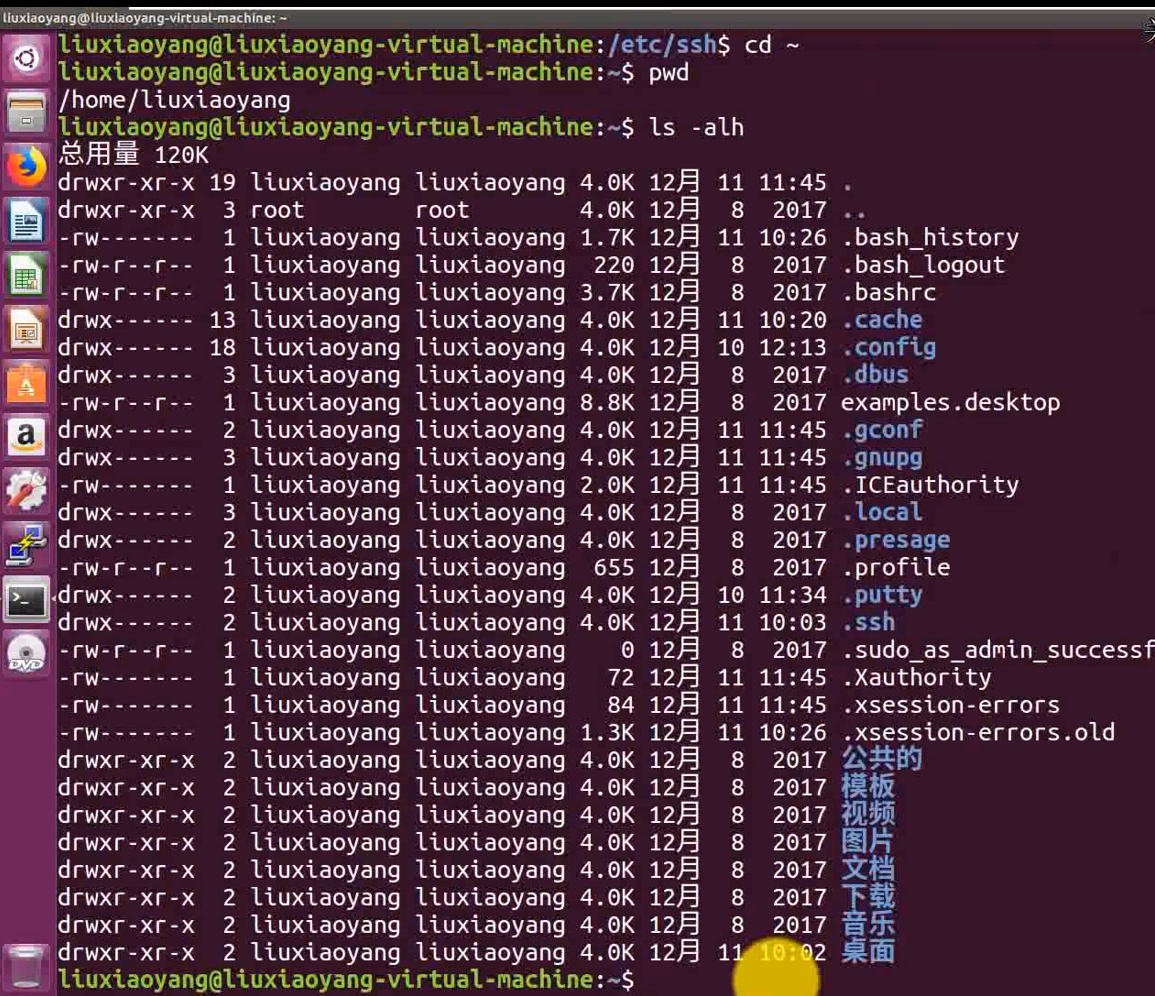
cd .ssh/
ls
puttygen -L private.ppk
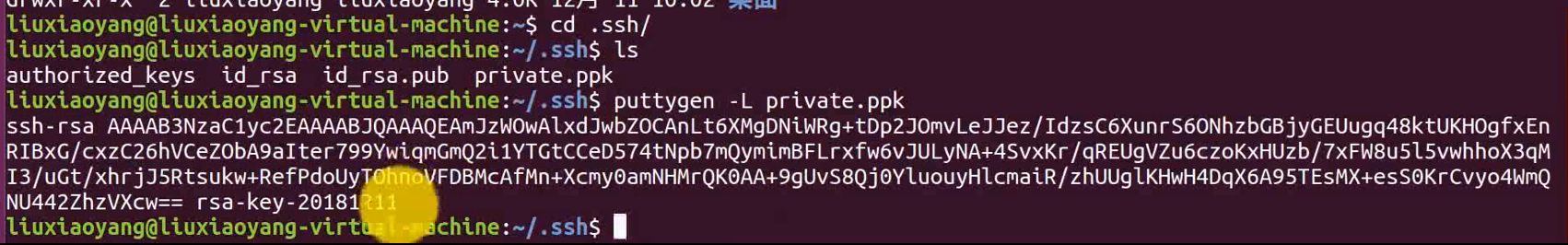
gedit authorized_keys
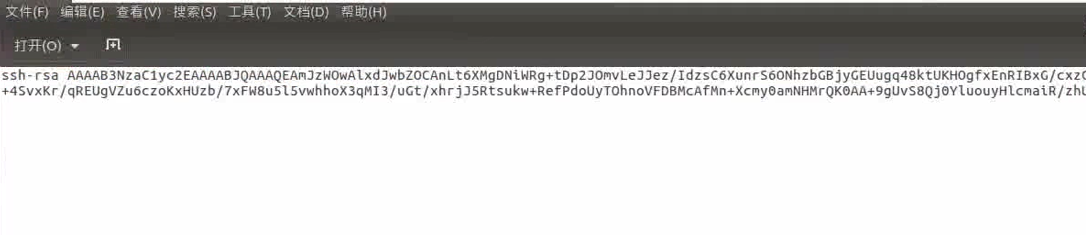
Paste the content here , Preservation , After saving , We have one aythorized_keys file
This is the time , We can do that windows Next , Or installed under other systems ppy, Under the client software , Connect ssh, It uses PGP Connect
SSH Defend against brute force cracking user accounts
Set up pgp To prevent violent cracking , But we can still log in with account and password
stay linux You can configure that you cannot log in with user name and password , Use only SSH PGP How to verify login . Evaded SSH Brute force .
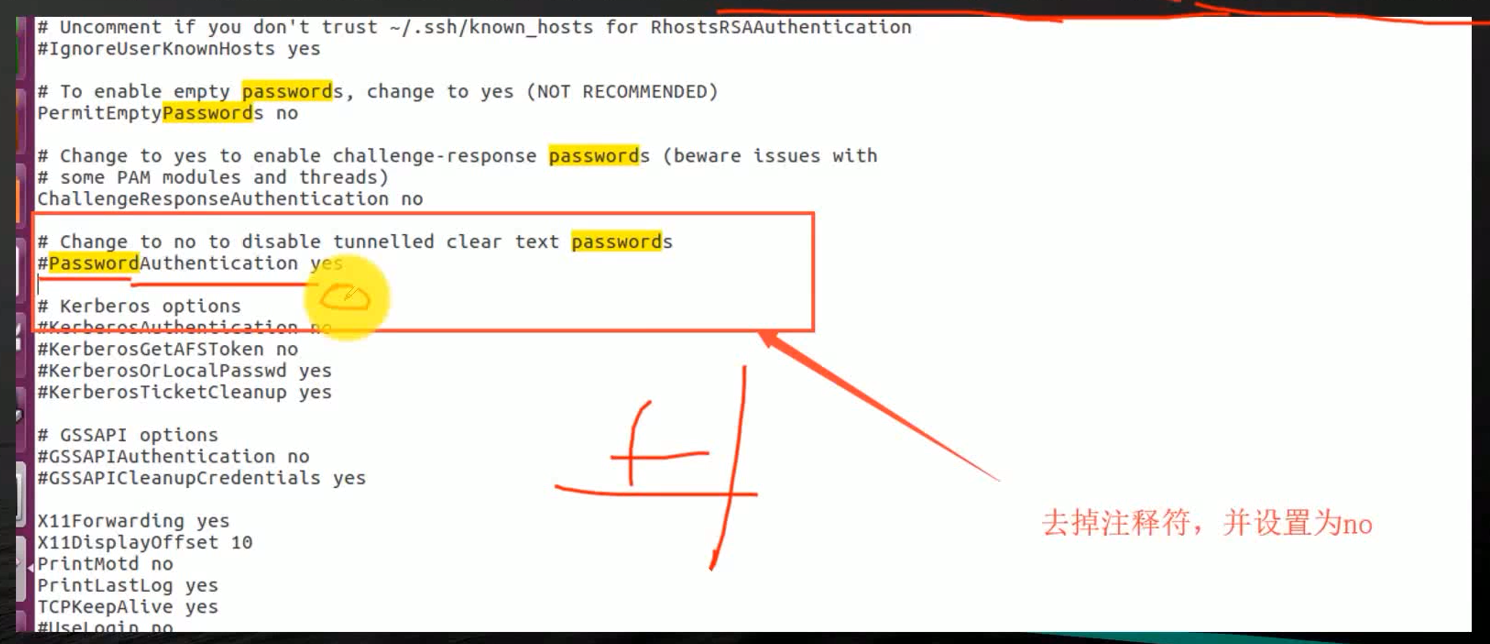
Problems arise : Cannot log in with user password , There are complex operations to a large extent .
for instance , There are many administrators in our current system , Cannot log in with user name and password , Everyone needs PPT file , To log in , It will be a lot of work and operation
cd /etc/ssh/
sudo gedit sshd_config
service ssh restart
service ssh status
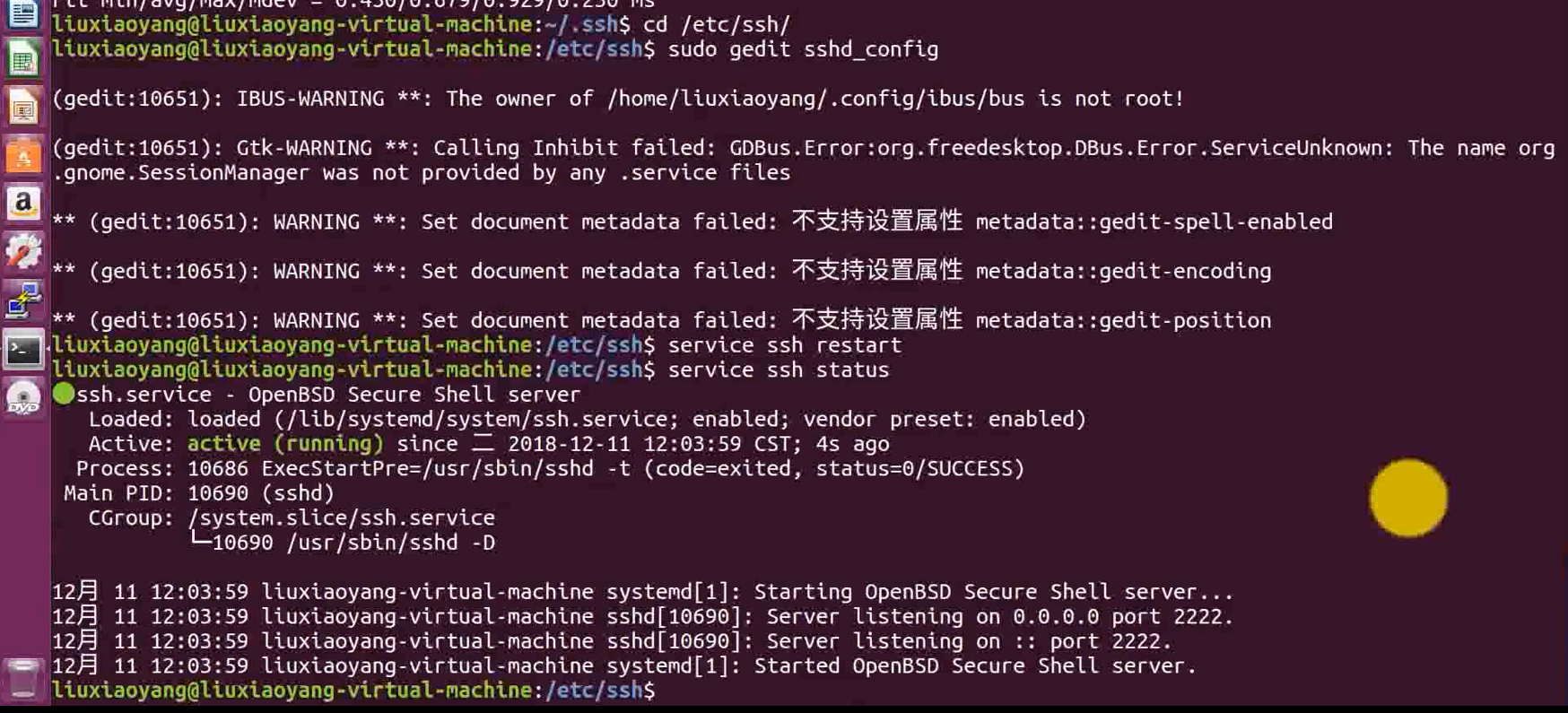
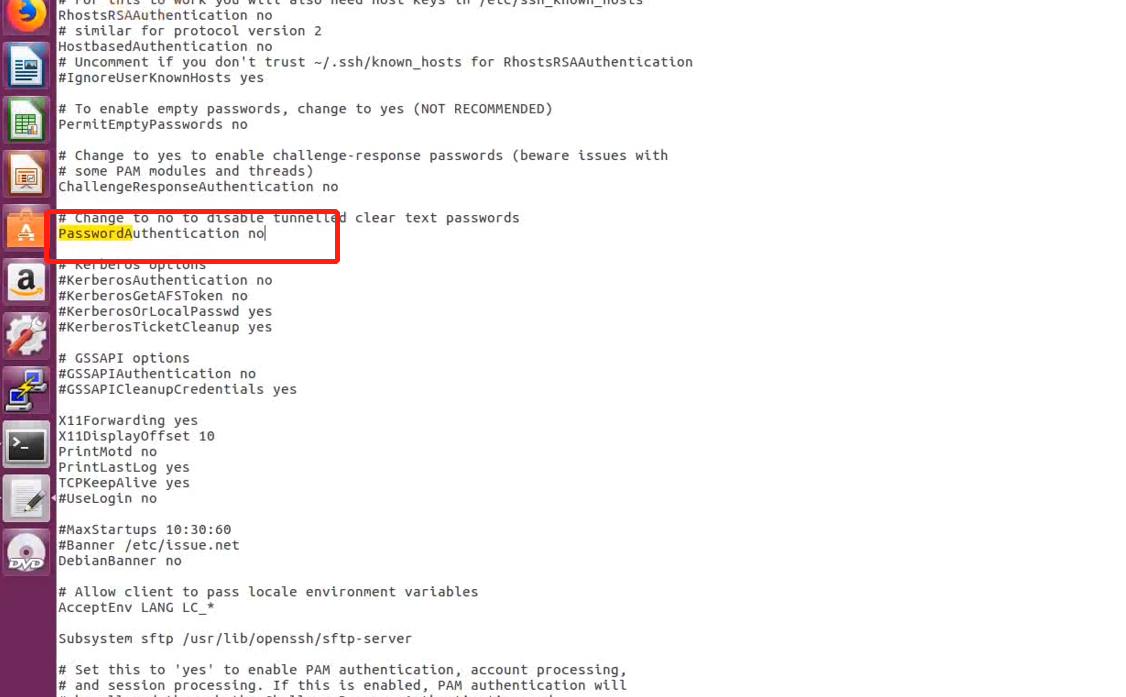
below , We are kali Login with user name and password , To verify that
ssh [email protected]
ssh [email protected] -p 2222
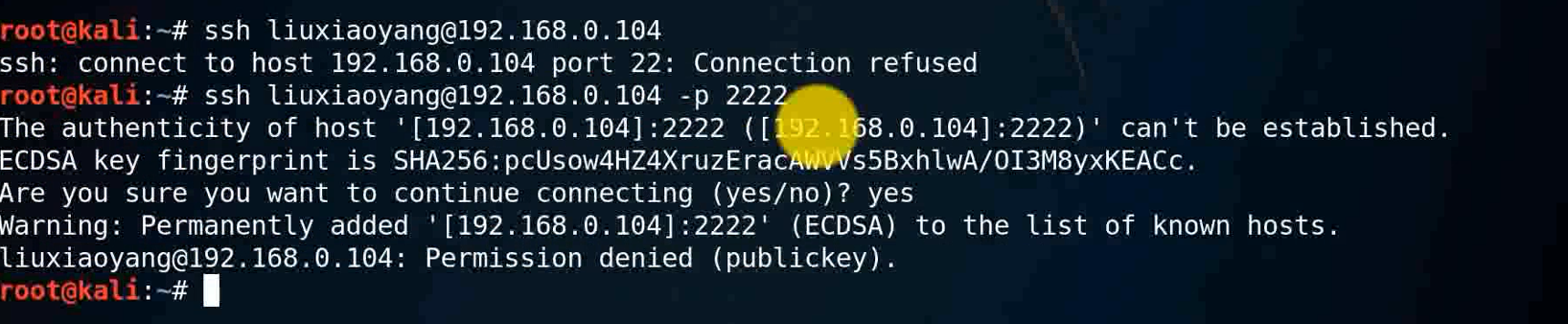
Because we can't log in , So brute force software , Is failure
iptables Set threshold to prevent brute force cracking
use iptables Firewall to prevent brute force cracking , We can set the corresponding threshold , After we try to login three times , Just lock the login , Makes it impossible for him to log in
utilize Iptables Error validating multiple connections , Lock the account 120 second .
sudo iptables -l INPUT -p tcp --dport 22 -i eth0 -m state --state NEW -m recent --set
sudo iptables -l INPUT -p tcp --dport 22 -i eth0 -m state --state NEW -m recent --update --seconds 120 --hitcount 3 -j DROP
After setting , Reboot required SSH service .
service ssh restart
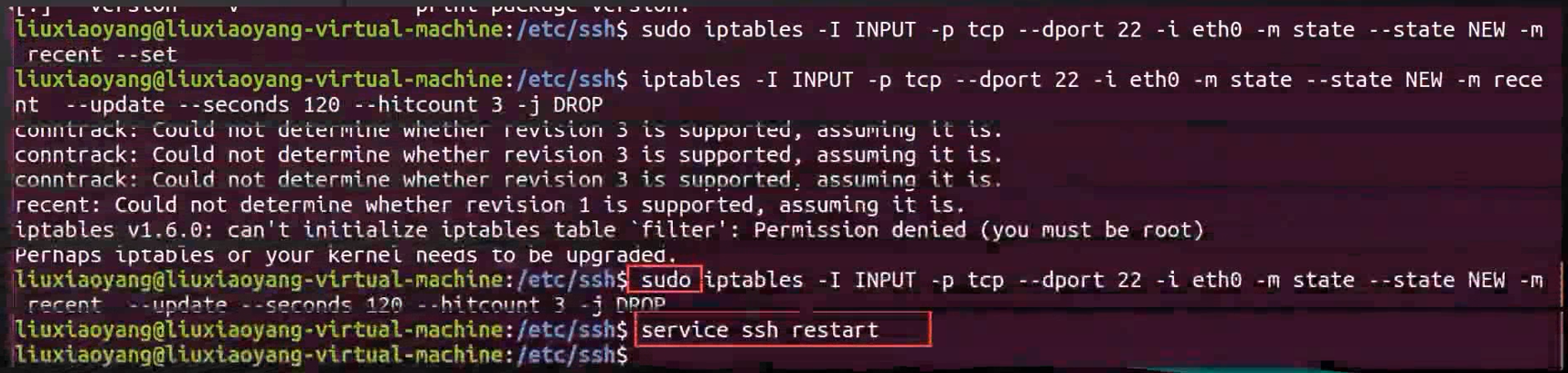
We can set a longer time , You can only try three combinations in a day , You can only try 1000 combinations a year , When our password setting is complex , Brute force cracking is also a very slow situation , Brute force cracking cannot take effect , Or say , It takes a lot of energy , several tens of years , It may be tens of thousands of years , Can the current dictionary , Guess and solve
边栏推荐
- 3 -- Xintang nuc980 kernel supports JFFS2, JFFS2 file system production, kernel mount JFFS2, uboot network port settings, and uboot supports TFTP
- C#/VB.NET 删除Word文檔中的水印
- The boss is quarantined
- The third season of ape table school is about to launch, opening a new vision for developers under the wave of going to sea
- Zhang Ping'an: accelerate cloud digital innovation and jointly build an industrial smart ecosystem
- PostgreSQL图形化界面工具之pgAdmin4
- C#/VB.NET 删除Word文档中的水印
- 所谓的消费互联网仅仅只是做行业信息的撮合和对接,并不改变产业本身
- MetaForce原力元宇宙佛萨奇2.0智能合约系统开发(源码部署)
- Recommended collection!! Which is the best flutter status management plug-in? Please look at the ranking list of yard farmers on the island!
猜你喜欢
unity 自定义webgl打包模板
![[unity notes] screen coordinates to ugui coordinates](/img/e4/fc18dd9b4b0e36ec3e278e5fb3fd23.jpg)
[unity notes] screen coordinates to ugui coordinates
C # / vb. Net supprime le filigrane d'un document word
Lumion 11.0软件安装包下载及安装教程

Zhang Ping'an: accelerate cloud digital innovation and jointly build an industrial smart ecosystem

FLIR blackfly s usb3 industrial camera: how to use counters and timers
进程管理基础
B站6月榜单丨飞瓜数据UP主成长排行榜(哔哩哔哩平台)发布!
![leetcode:736. LISP syntax parsing [flowery + stack + status enumaotu + slots]](/img/0d/e07fe970167368040eb09b05c3682e.png)
leetcode:736. LISP syntax parsing [flowery + stack + status enumaotu + slots]

【森城市】GIS数据漫谈(二)
随机推荐
Compress JS code with terser
PostgreSQL图形化界面工具之pgAdmin4
Alibaba cloud middleware open source past
Leetcode:minimum_depth_of_binary_tree解决问题的方法
Decryption function calculates "task state and lifecycle management" of asynchronous task capability
CDB PDB user rights management
How do I dump SoapClient requests for debugging- How to dump SoapClient request for debug?
leetcode:736. LISP syntax parsing [flowery + stack + status enumaotu + slots]
PCL 常用拟合模型及使用方法
leetcode:5. Longest palindrome substring [DP + holding the tail of timeout]
4--新唐nuc980 挂载initramfs nfs文件系统
安全巡检的工作
[unity] upgraded version · Excel data analysis, automatically create corresponding C classes, automatically create scriptableobject generation classes, and automatically serialize asset files
pgpool-II和pgpoolAdmin的使用
Here comes a white paper to uncover the technology behind Clickhouse, a node with 10000 bytes!
3D laser slam: time synchronization of livox lidar hardware
Sensor: DS1302 clock chip and driver code
[C # notes] reading and writing of the contents of text files
1--新唐nuc980 NUC980移植 UBOOT,从外部mx25l启动
Draco - gltf model compression tool