当前位置:网站首页>The boss is quarantined
The boss is quarantined
2022-07-07 02:18:00 【Ma Nong turns over】
1
Telecommuting
As a small and medium-sized company IT Head of department operation and maintenance , Zhang Dafu has been under great pressure recently .
Under the epidemic , Several people in the company have been isolated as close contacts , The voice of other employees for home telecommuting is getting louder .
Zhang Dapu also wants to work remotely at home , Safe and free , But the company's customer management system ,OA The systems are deployed in the company's own computer room , It is an internal LAN , How can I visit at home ?
Cannot access , How to telecommute ?
Obviously , The simplest way is to build a set VPN System , Everyone is assigned an account , This solves the problem . however VPN The configuration is complex and expensive , It's not suitable for this small company .
Zhang dafun is bored searching on the Internet , I found a man called “ Dandelion Yi Lian ” Office platform , No need for a private network 、 There is no need for the public network IP, There is no need to change the existing network structure , You can easily build a virtual LAN , Let employees visit the company at home IT System .
This “ The dandelion ” It works like this :
First step , Operations staff ( That is, oneself ) Create a dandelion management platform “ virtual network ”.
The second step , Create a member account for each employee in the virtual network , Each member will be assigned one ID、 Passwords and virtual IP Address .
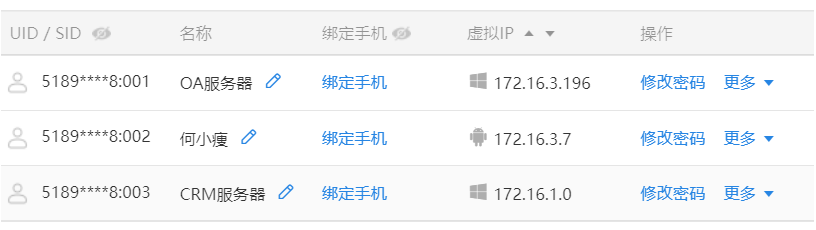
( Click to see a larger image )
The third step , Each employee downloads and installs dandelion client .( Of course , It also needs to be installed on the company's server )
In addition to supporting Windows outside , Dandelion client also supports almost all other mainstream operating systems on the market :
then , Employees can log in with the previously created account and password .
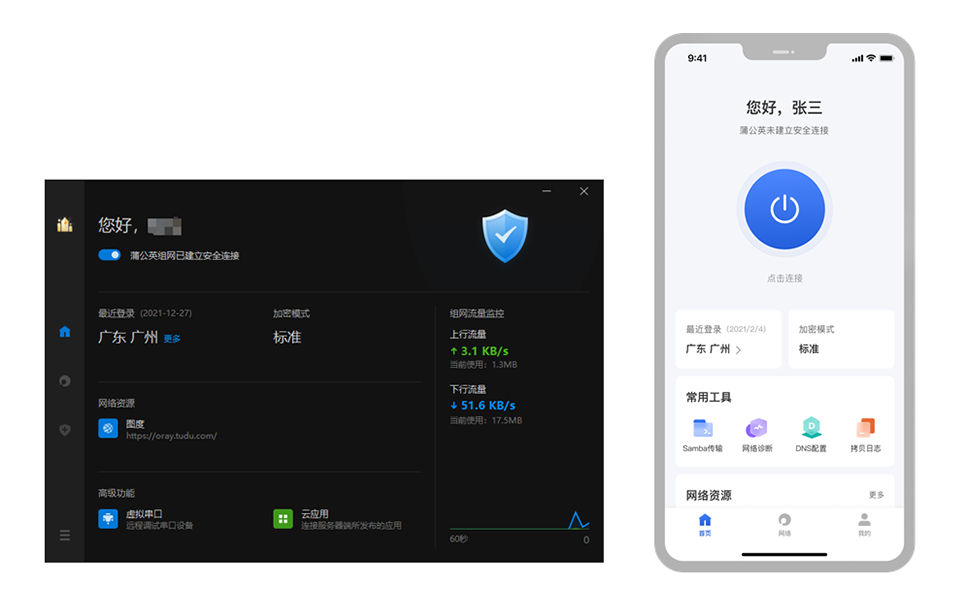
Now every machine has a virtual IP, Employees can not only use it to access OA and CRM System , Machines among employees can also be interconnected .
Zhang Dapu really didn't expect , It's so simple to build a virtual LAN !
He excitedly went to the boss to report the good news , Expect the boss to give an order , Everyone can go home and work remotely .
The boss listened to the report , be noncommittal , Just a faint question : How safe ? If an employee's account is compromised , our OA and CRM The system is not equivalent to running naked on the Internet ?
Zhang Dafu's head was suddenly covered , I'm too impulsive , Report to the boss before considering improvement , I made a big mistake .
Zhang Dafu apologized repeatedly : I don't think well , Go back and study , Come back and make a report .
2
Secure access
Back to your seat , Zhang Dafan thought carefully : Is the boss too demanding ?!
Now even VPN System , The account has been leaked , Isn't the intranet system also exposed ? Also streaked ? The same problem !
If you make an analogy ,VPN The gateway is like a guard , Legal users have passed the inspection of the guard , Enter the community , He will only go where he wants to go 1 building .
But for hackers who steal other people's identities , Once he enters the community , Just go 1 building , I will definitely go 1,2,3... Stroll around building , See if there is anything valuable , Steal it , Or ambush a back door or something .
Can't even a user who logs in to the system through the account password be trusted ? What should I do ?
Zhang Dafu was stunned .
Is this time , Go to the tea room to fetch water CTO Lao he saw Zhang Dafu in a daze , Gently patted him on the shoulder : What do you daydream in broad daylight ?
Zhang Dafu told Lao he about his experience and confusion , Lao he laughed :“ Your problem is also easy to solve , Use your example to compare , We first check at the gate of the community , But even if a person passes the guard's inspection , Enter the community , When he is doing something , And continue to be checked , See if his identity is right , Do you have permission to , If an exception is found , Just kick him out .”
“ That is to say, the principle of minimum permission should be used , Implement refined authority control ?” Zhang Da Pang asked .
“ Children can teach !” Old he left with a cup .
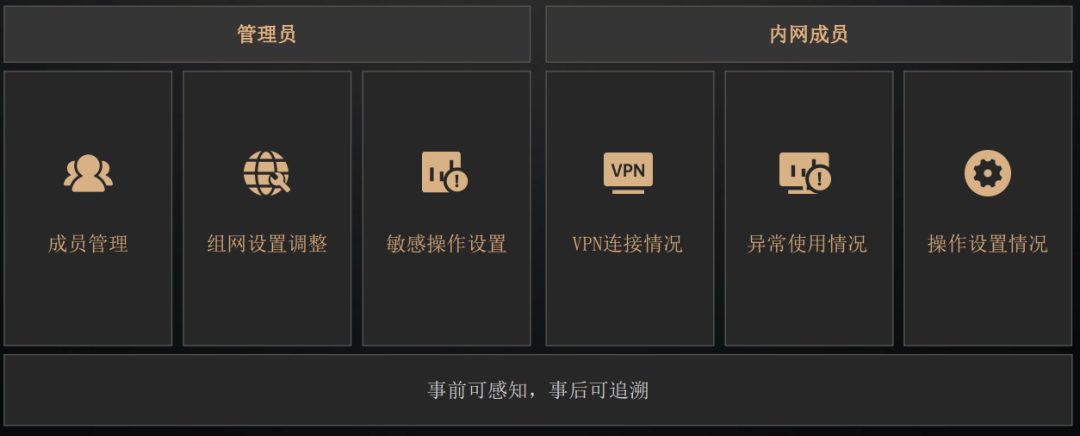
Zhang Dafu immediately went to check the dandelion easy plan , It is found that it supports custom setting of access permissions between members , So as to realize the refined access strategy .
Managers can meet different job requirements 、 Working hours , Set different access permissions for resources in the network . for example : Ordinary employees can only access OA System 、 Finance can access the corresponding financial system , R & D visit git、SVN etc. , Implement the minimum permission principle , High precision protection of sensitive data access security .
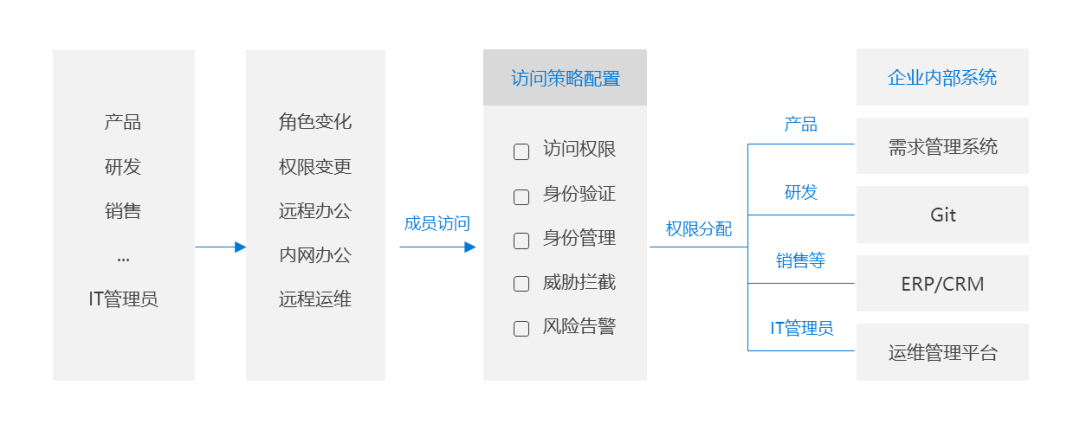
( Click to see a larger image )
This solves the problem ?
3
In depth research
however , This time, Zhang Dafang learned well , We must do in-depth research , Then you can report to the boss .
This time when Zhang Dafu was creating the network , I chose “ Custom network ”:
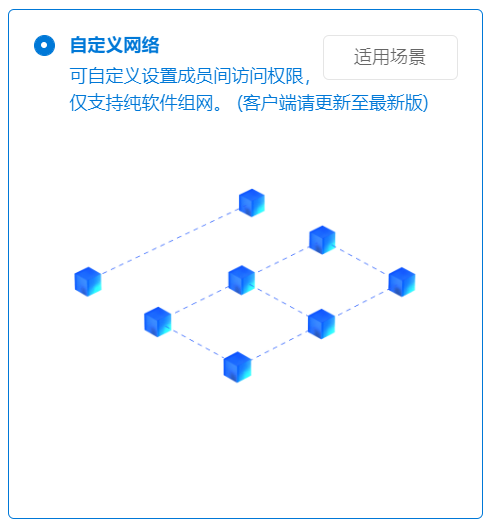
Assign account numbers to employees , When creating network members , Specify the role of the employee :
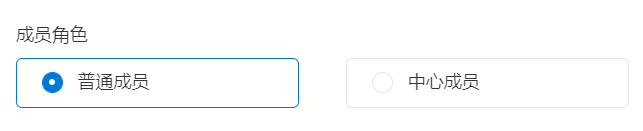
By default , Ordinary members cannot communicate with each other , Only with center members ( For example, server ) Interworking .
“ Dandelion Yi Lian ” There is also a very powerful access strategy , Fine authorization , For example, you can specify that certain users can only access certain machines , It can only be accessed at a certain time :
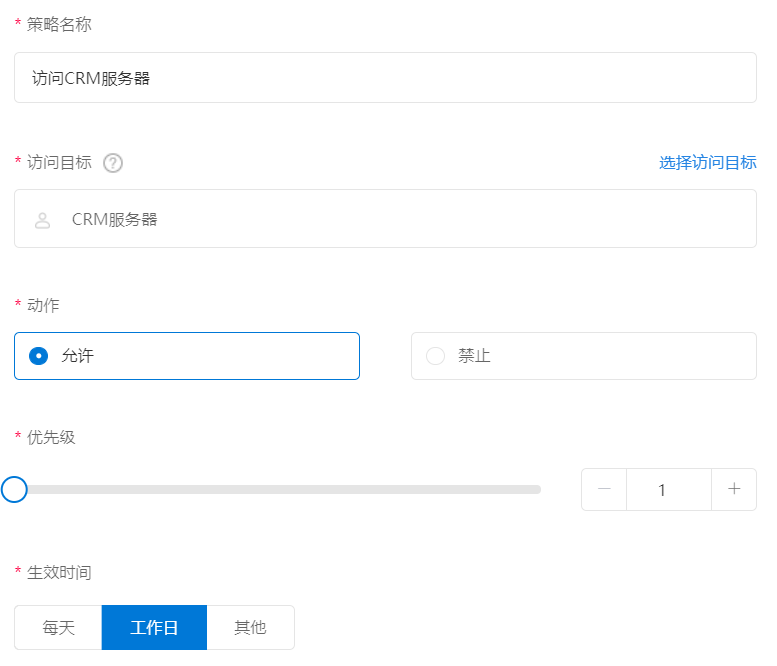
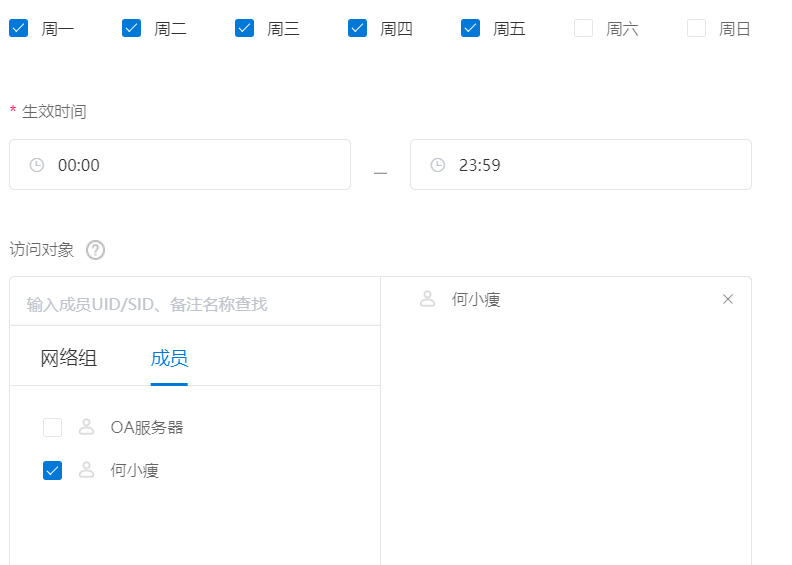
( Click to see a larger image )
For example, he Xiaoheng's machine in the above figure can only be accessed from Monday to Friday CRM The server .
Zhang Dafan is very satisfied , With refined authorization , It solves the boss's requirements .
In addition to the prior permission configuration ,“ Dandelion Yi Lian ” It also supports post event log auditing , Who logged in to the client at what time and where , Have you done anything , You can check . The so-called prior perception , Ex post facto .
He continued to try , I also found several very good functions , For example, data transmission adopts RSA/AES Hybrid asymmetric encryption algorithm , It's kind of like Https The implementation of , Very safe .
There is also device terminal verification , If this device is not a trusted terminal like a private computer ,“ The dandelion ” It will be continuously verified , It is required to provide dynamic verification code .
This is equivalent to security guards everywhere in the community , To thieves ( Untrusted terminals ) Keep checking , Exception found , Alarm immediately .
What's more useful is , It also supports third-party data access , You can put enterprise wechat 、 nailing 、 Flying book, etc IM Get your address book data , Real time synchronization , Staff entry 、 quit 、 Permission changes are updated in real time , Greatly improve the convenience of member management .
4
The end of the
Before reporting , Zhang Dafan made one PPT, Count it “ Dandelion Yi Lian ” Several advantages of :
1. Support pure software solutions , Not limited by hardware , Do not change the existing network structure
2. Efficient and easy to use , Low threshold for use , One click networking 、 One click connection
3. Low cost , High cost performance , There is no need for special line and public network IP
4. The most important , Very safe
Zhang Dafu is full of confidence this time , He was preparing to report , In wechat, the boss suddenly called him crazily :
Da Pang Zhang , I was quarantined ! How come the network of remote office hasn't been set up yet ?!
Zhang Dafu was surprised and delighted , Hurry up PPT Transfer the past : Boss, don't worry ,“ Dandelion Yi Lian ” Do it right away , You can access the Intranet in a moment !

Welcome to scan the code and consult dandelion Yilian

边栏推荐
- SchedulX V1.4.0及SaaS版发布,免费体验降本增效高级功能!
- ROS学习(24)plugin插件
- 猫猫回收站
- Zabbix 5.0:通过LLD方式自动化监控阿里云RDS
- 阿里云中间件开源往事
- FLIR blackfly s industrial camera: auto exposure configuration and code
- Shortcut keys commonly used in idea
- 强化学习如何用于医学影像?埃默里大学最新《强化学习医学影像分析》综述,阐述最新RL医学影像分析概念、应用、挑战与未来方向
- 一片葉子兩三萬?植物消費爆火背後的“陽謀”
- Analyze "C language" [advanced] paid knowledge [i]
猜你喜欢
使用Ceres进行slam必须要弄清楚的几个类和函数
SchedulX V1.4.0及SaaS版发布,免费体验降本增效高级功能!
New generation cloud native message queue (I)
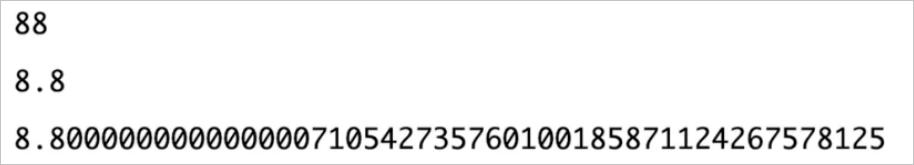
Correct use of BigDecimal
ROS学习(23)action通信机制

Flir Blackfly S USB3 工业相机:白平衡设置方法
Recommended collection!! Which is the best flutter status management plug-in? Please look at the ranking list of yard farmers on the island!
Infrared camera: juge infrared mag32 product introduction

强化学习如何用于医学影像?埃默里大学最新《强化学习医学影像分析》综述,阐述最新RL医学影像分析概念、应用、挑战与未来方向
豆瓣平均 9.x,分布式领域的 5 本神书!
随机推荐
The last line of defense of cloud primary mixing department: node waterline design
Introduction to microservice architecture
CISP-PTE实操练习讲解(二)
ROS学习(24)plugin插件
FLIR blackfly s industrial camera: configure multiple cameras for synchronous shooting
ROS learning (26) dynamic parameter configuration
[leetcode] day97 remove linked list elements
Sensor: DS1302 clock chip and driver code
#yyds干货盘点# 解决名企真题:最大差值
Command injection of cisp-pte
FLIR blackfly s usb3 industrial camera: white balance setting method
Schedulx v1.4.0 and SaaS versions are released, and you can experience the advanced functions of cost reduction and efficiency increase for free!
UC伯克利助理教授Jacob Steinhardt预测AI基准性能:AI在数学等领域的进展比预想要快,但鲁棒性基准性能进展较慢
centos8安裝mysql報錯:The GPG keys listed for the “MySQL 8.0 Community Server“ repository are already ins
MySQL execution process and sequence
ROS learning (23) action communication mechanism
建议收藏!!Flutter状态管理插件哪家强?请看岛上码农的排行榜!
Cisp-pte practice explanation (II)
新一代云原生消息队列(一)
微服务架构介绍