当前位置:网站首页>Function analysis and source code of hash guessing game system development
Function analysis and source code of hash guessing game system development
2022-07-04 20:36:00 【VC_ MrsFu123】
Hash (Hash) Algorithm , Hash function . It's a one-way cryptosystem , That is, it is an irreversible mapping from plaintext to ciphertext , Only the encryption process , No decryption process . meanwhile , Hash function can change the input of any length to get fixed length output . This one-way feature of the hash function and the fixed length of the output data make it possible to generate messages or data .
The hash algorithm ( Hash algorithm or message digest algorithm ) It is a basic technology used in information storage and query , It is based on Hash File construction method of function , Map a given key value of any length to a hash value of fixed length , Generally used for authentication 、 authentication 、 encryption 、 Index, etc. . Its main advantage is that the operation is simple , Short pretreatment time , Low memory consumption , Matching search speed is relatively fast , Easy to maintain and refresh , Support more matching rules .
Hash Methods of constructors
1. direct addressing :
Direct addressing is based on data element keywords k Itself or its linear function as its hash address , namely :H(k)=k or H(k)=a×k+b;( among a,b Constant )
2. Digital analysis :
Suppose that every keyword in the keyword set is created by s Digit composition (u1,u2,…,us), Analyze the whole set of keywords , And a number of evenly distributed bits or their combination are extracted as addresses .
Numerical analysis is a method of taking some digits with uniform values in the keywords of data elements as hash addresses . That is, when there are many digits of keywords , You can analyze the keywords , Lose the unevenly distributed bits , As Hashi is worth . It is only suitable for all cases where the keyword value is known . By analyzing the distribution, the keyword value range is transformed into a smaller keyword value range .
3. Folding method :
Split keywords into parts , Then take the sum of them as the hash address . Two methods of superposition processing : Shift stacking : Align and add the low order of the divided parts ; Boundary overlay : Fold back and forth along the division boundary from one end , And then align and add .
The so-called folding method is to divide keywords into parts with the same number of digits ( The number of digits in the last part can be different ), And then you take the sum of these parts ( Give up the carry ), This method is called folding method . This method is applicable to keywords with many digits , And the number distribution on each digit in the keyword is roughly uniform .
In the folding method, digital folding is divided into two methods: shift superposition and boundary superposition , Shift superposition is to align the lowest bit of each part after segmentation , Then I add ; Boundary superposition is folding back and forth along the division boundary from one end to the other , And then align and add .
Hash property :
(1) One way .That is,given an input number,it is easy to calculate its hash value,but given a hash value,the original input number cannot be obtained according to the same algorithm.
(2) Weak anti-collision .That is,given an input number,it is computationally infeasible to find another hash value to get a given number when using the same method.
(3) Strong collision resistance .That is,for any two different input numbers,it is not feasible to calculate the same hash value according to the same algorithm.
边栏推荐
- 更强的 JsonPath 兼容性及性能测试之2022版(Snack3,Fastjson2,jayway.jsonpath)
- Talking about cookies of client storage technology
- PHP pseudo original API docking method
- 更强的 JsonPath 兼容性及性能测试之2022版(Snack3,Fastjson2,jayway.jsonpath)
- 【深度学习】一文看尽Pytorch之十九种损失函数
- Installation and use of VMware Tools and open VM tools: solve the problems of incomplete screen and unable to transfer files of virtual machines
- Application practice | Shuhai supply chain construction of data center based on Apache Doris
- 1500万员工轻松管理,云原生数据库GaussDB让HR办公更高效
- Crystal optoelectronics: ar-hud products of Chang'an dark blue sl03 are supplied by the company
- Practical examples of node strong cache and negotiation cache
猜你喜欢
Small hair cat Internet of things platform construction and application model

What does the neural network Internet of things mean? Popular explanation
Dynamic memory management
Pointnext: review pointnet through improved model training and scaling strategies++
So this is the BGP agreement
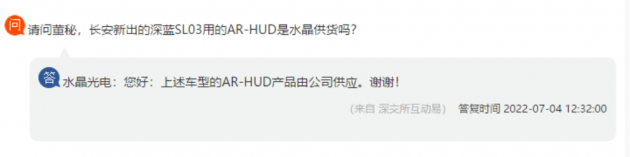
水晶光电:长安深蓝SL03的AR-HUD产品由公司供应
Every time I look at the interface documents of my colleagues, I get confused and have a lot of problems...
Multi table operation inner join query
New wizard effect used by BCG
QT writing the Internet of things management platform 38- multiple database support
随机推荐
左右最值最大差问题
Pytoch learning (4)
B2B mall system development of electronic components: an example of enabling enterprises to build standardized purchase, sale and inventory processes
Delete the characters with the least number of occurrences in the string [JS, map sorting, regular]
Pointnext: review pointnet through improved model training and scaling strategies++
Detailed explanation of Audi EDI invoice message
Prometheus installation
FS4061A升压8.4V充电IC芯片和FS4061B升压12.6V充电IC芯片规格书datasheet
In operation (i.e. included in) usage of SSRs filter
The company needs to be monitored. How do ZABBIX and Prometheus choose? That's the right choice!
On communication bus arbitration mechanism and network flow control from the perspective of real-time application
Length of the longest integrable subarray
Six stones programming: about code, there are six triumphs
Win11无法将值写入注册表项如何解决?
CANN算子:利用迭代器高效实现Tensor数据切割分块处理
泰山OFFICE技术讲座:关于背景(底纹和高亮)的顺序问题
What ppt writing skills does the classic "pyramid principle" teach us?
Creation of JVM family objects
Regular replacement [JS, regular expression]
ICML 2022 | meta proposes a robust multi-objective Bayesian optimization method to effectively deal with input noise