当前位置:网站首页>Information Security Experiment 1: implementation of DES encryption algorithm
Information Security Experiment 1: implementation of DES encryption algorithm
2022-07-07 09:22:00 【Not enough to eat】
One 、 Purpose and requirements of the experiment
1. Familiar with encryption 、 Decryption algorithm ; Understand the important role of encryption in communication ;
2. Encrypt the entered hexadecimal number ( Convert the input characters into integers ), Compare input and output , When changing the input number by one bit , Compare changes in output , Explain why .
3. Realize the encryption and decryption of a file , Submit program code and execution results .
Two 、 Experimental content
This experiment uses DES The algorithm encrypts and decrypts the actual data to gain a deep understanding DES Operating principle . Analyze according to the program provided DES The realization process of the algorithm . In analyzing the key generation function 、 Encryption function (8 byte )、 Decryption function 、 Test function and key length test function , use C/VC++ or Java Language programming to encrypt and decrypt text files .
3、 ... and 、 Experimental environment
function windows or Linux Operating system PC machine , have VC(windows)、gcc(Linux) etc. C Language compilation environment or Java Environmental Science .
Four 、 Experimental steps and result analysis
- Running results
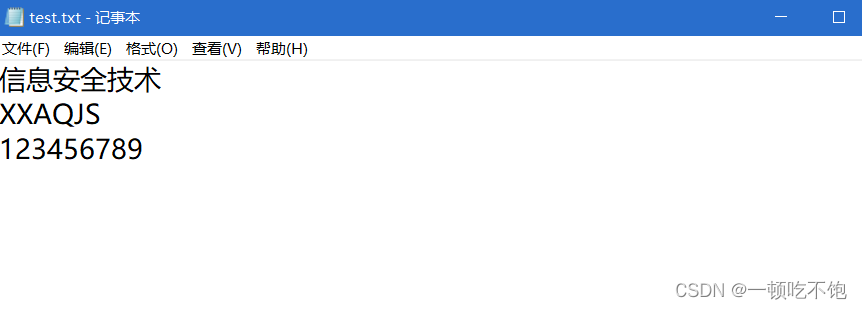
1.1、 The original document
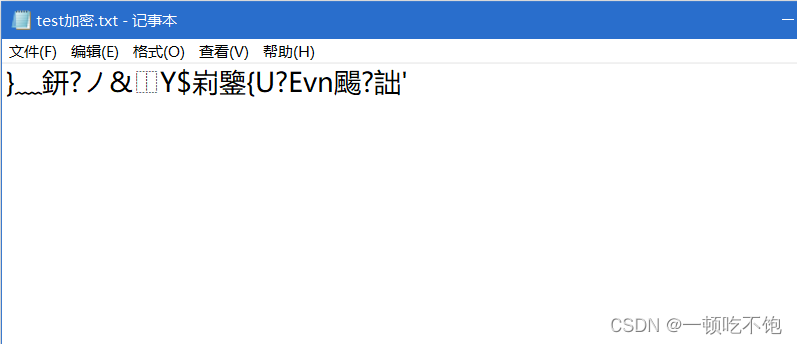
Encrypted file
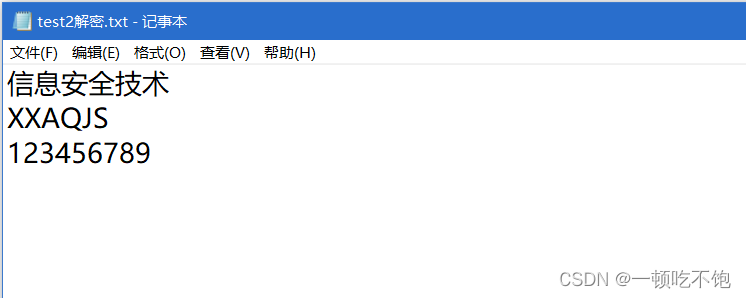
Decrypted file
- Code
public class TestDES {
Key key;
public TestDES(String str) {
getKey(str);// Generate key
}
// Generate... Based on parameters KEY
public void getKey(String strKey) {
try {
KeyGenerator _generator = KeyGenerator.getInstance("DES");
_generator.init(new SecureRandom(strKey.getBytes()));
this.key = _generator.generateKey();
_generator = null;
}
catch (Exception e) {
throw new RuntimeException("Error initializing SqlMap class. Cause: " + e);
}
}
public void encrypt(String file, String destFile) throws Exception {
Cipher cipher = Cipher.getInstance("DES");
// cipher.init(Cipher.ENCRYPT_MODE, getKey());
cipher.init(Cipher.ENCRYPT_MODE, this.key);
InputStream is = new FileInputStream(file);
OutputStream out = new FileOutputStream(destFile);
CipherInputStream cis = new CipherInputStream(is, cipher);
byte[] buffer = new byte[1024];
int r;
while ((r = cis.read(buffer)) > 0) {
out.write(buffer, 0, r);
}
cis.close();
is.close();
out.close();
}
public void decrypt(String file, String dest) throws Exception {
Cipher cipher = Cipher.getInstance("DES");
cipher.init(Cipher.DECRYPT_MODE, this.key);
InputStream is = new FileInputStream(file);
OutputStream out = new FileOutputStream(dest);
CipherOutputStream cos = new CipherOutputStream(out, cipher);
byte[] buffer = new byte[1024];
int r;
while ((r = is.read(buffer)) >= 0) {
cos.write(buffer, 0, r);
}
cos.close();
out.close();
is.close();
}
public static void main(String[] args) throws Exception {
TestDES td = new TestDES("24234");
td.encrypt("D:/Desktop/test.txt", "D:/Desktop/test1.txt"); // encryption
td.decrypt("D:/Desktop/test1.txt", "D:/Desktop/test2.txt"); // Decrypt
}
}
边栏推荐
- How does the project manager write the weekly summary and weekly plan?
- Windows starts redis service
- How to use Arthas to view class variable values
- External interrupt to realize key experiment
- STM32 clock system
- 徽商期货公司评级是多少?开户安全吗?我想开户,可以吗?
- NVIC中断优先级管理
- sqlplus乱码问题,求解答
- DRF authentication, permissions, and flow restrictions (only for views in DRF)
- What is the use of PMP certificate?
猜你喜欢
![Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]](/img/5f/a3e7ed3617f1fec024eaba086ddd2a.jpg)
Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]

Expérience de port série - simple réception et réception de données
Mysql:select ... for update
浏览器中如何让视频倍速播放
Connecting mobile phone with ADB

Common short chain design methods
Mysql database transaction learning notes
Do you have any certificates with high gold content?
Error: selenium common. exceptions. WebDriverException: Messag‘geckodriver‘ execute
sqlplus乱码问题,求解答
随机推荐
[chaosblade: node CPU load, node network delay, node network packet loss, node domain name access exception]
How to pass the PMP Exam in a short time?
JWT certification used in DRF
信息安全实验三 :PGP邮件加密软件的使用
When inputting an expression in the input box, an error is reported: incorrect string value:'\xf0\x9f... ' for column 'XXX' at row 1
Jmeters use
端口复用和重映像
Locust performance test 3 (high concurrency, parameter correlation, assembly point)
Run can start normally, and debug doesn't start or report an error, which seems to be stuck
Leetcode daily questions (2316. count unreachable pairs of nodes in an undirected graph)
C language pointer (Part 1)
DRF defines views and routes
What is MD5
Using JWT to realize login function
Two schemes of unit test
(3/8) method parameters of improper use of enumeration (2)
Common short chain design methods
PMP examination experience sharing
Druid monitoring - Introduction to JMX usage and principle
Pytest+request+allure+excel interface automatic construction from 0 to 1 [five nails / flying Book notice]