当前位置:网站首页>(7) Web security | penetration testing | how does network security determine whether CND exists, and how to bypass CND to find the real IP
(7) Web security | penetration testing | how does network security determine whether CND exists, and how to bypass CND to find the real IP
2022-07-02 13:04:00 【Black zone (rise)】
CDN The full name is Content Delivery Network, The content distribution network .CDN It is an intelligent virtual network based on the existing network , Rely on edge servers deployed everywhere , Load balancing through the central platform 、 content distribution 、 Scheduling and other functional modules , Let users get the content they need nearby , Reduce network congestion , Improve user access response speed and hit rate .
The above comes from :CDN_ Baidu Encyclopedia (baidu.com)
Personally feel cdn In short : Through the nearby temporary storage of information CDN Node sends information to users
cdn Will hide the server's real ip Address , Unable to penetrate the operating system of the target website ,cdn The site is virtual , Have the same website architecture , And cdn The server can interact with the site server , therefore sql The mining of injection and other vulnerabilities is not greatly affected .
Through the tool ping, Look at the display ip Is the address unique , If it's not the only one , Then these ip The address is CDN The address of
Using tools :
IP/IPv6 Inquire about , Server address query - Webmaster Tools (chinaz.com)
( Take Baidu for example )
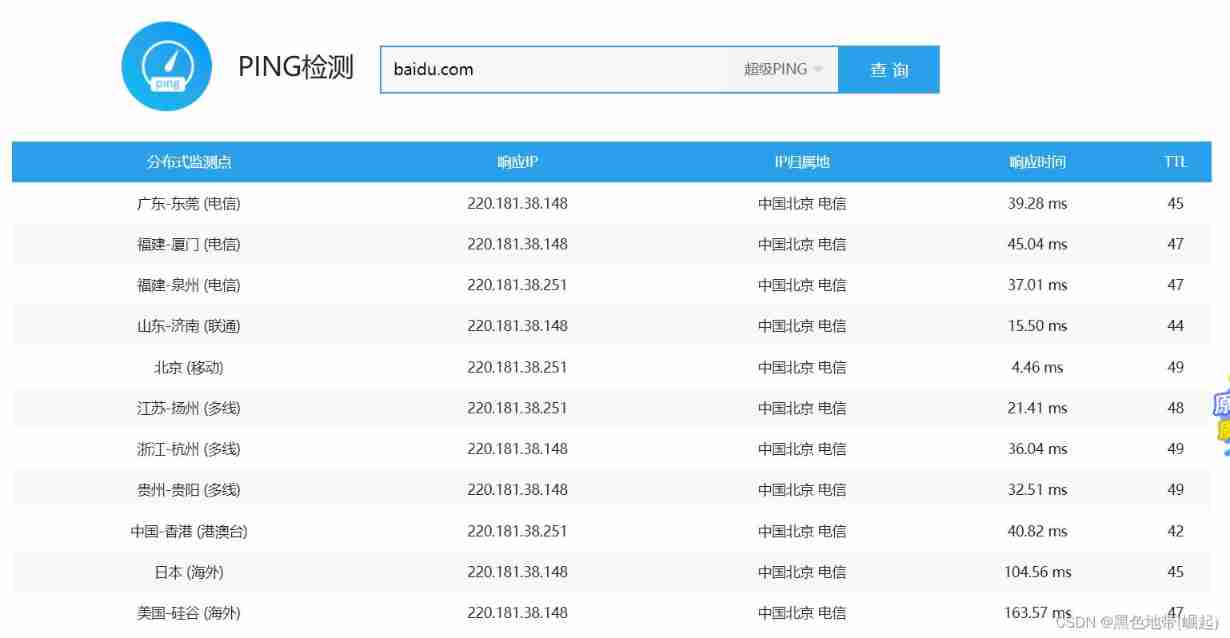
You can see it in many places ip Address , It can be determined that this is its CDN node
There is also a tool to check authenticity ip:
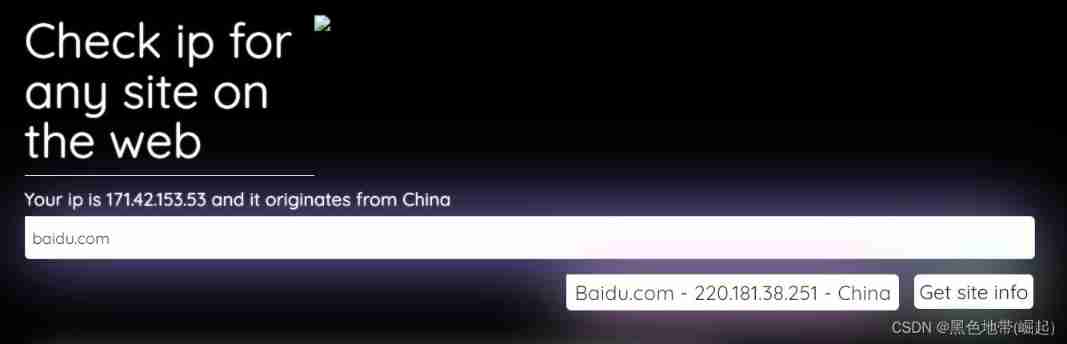
But you can't determine this with tools ip Is it true
If you are not at ease, you can also use manual search , Combined with practice , Analyze the location of the company and ip Continue to analyze the location
When some websites register , Will pass email authentication , Or send an email message , At this time, analyze the... In the email data ip Address , The first ip It was sent by Tencent as a transit
Subdomain query :
Because some main stations do CDN Service and the sub station didn't do CDN service
Subdomain excavator :
link :https://pan.baidu.com/s/1otbSIrRVIYotbB3VVeCSlw
Extraction code :hj12
Mail service query :
Most mailboxes are accessed by insiders , And the number of visits is generally not very large , So I don't usually do CDN.
Foreign address request :
CDN Generally, it is arranged nearby according to the user group
example : The users of a website are all in China , For economic reasons , Then the website administrator will not be deployed abroad CDN node , Visiting abroad may directly access the truth IP. Choose more unpopular countries to visit , If IP All the same , It's probably true ip.
( This will use related tools )
Legacy documents :
example :php Of phpinfo.php, You may see the truth IP
Scan the whole network :
May get all IP, And then analyze it
Dark engine search : May get google Specific search for
fofa、shodan、 To listen attentively 、zoomeye、censys
( We should conduct an artificial analysis by ourselves )
Specific documents dns Historical record :
The website may not have CDN, So through the search of the new website CDN Historical record , You may find what was resolved at that time IP, This IP It may be the reality of the current website IP.
Look at :
One CDN Node traffic, such as 1G, So many people visit , Run out of wandering , After that, it may be true IP 了 .( Also known as traffic exhaustion attack ).
real IP After obtaining the address, the binding points to the address change local HOSTS Parse point to file
边栏推荐
- Linear DP acwing 895 Longest ascending subsequence
- std::vector批量导入快速去重方法
- 腾讯三面:进程写文件过程中,进程崩溃了,文件数据会丢吗?
- Jerry's watch delete alarm clock [chapter]
- VLAN experiment
- Wechat official account payment prompt MCH_ ID parameter format error
- 基于STM32的OLED 屏幕驱动
- Redis transaction mechanism implementation process and principle, and use transaction mechanism to prevent inventory oversold
- 阿里发布的Redis开发文档,涵盖了所有的redis操作
- 软件测试面试题-2022年大厂面试题合集
猜你喜欢

bellman-ford AcWing 853. 有边数限制的最短路

JS iterator generator asynchronous code processing promise+ generator - > await/async

Async/await asynchronous function
腾讯三面:进程写文件过程中,进程崩溃了,文件数据会丢吗?
上手报告|今天聊聊腾讯目前在用的微服务架构

线性DP AcWing 895. 最长上升子序列
Direct control PTZ PTZ PTZ PTZ camera debugging (c)
Package management tools

三面阿里,有惊无险成功拿到offer定级P7,只能说是真的难

Day4 operator, self increasing, self decreasing, logical operator, bit operation, binary conversion decimal, ternary operator, package mechanism, document comment
随机推荐
Linear DP acwing 899 Edit distance
移动式布局(流式布局)
Rust language document Lite (Part 1) - cargo, output, basic syntax, data type, ownership, structure, enumeration and pattern matching
线性DP AcWing 895. 最长上升子序列
Js6day (search, add and delete DOM nodes. Instantiation time, timestamp, timestamp cases, redrawing and reflow)
OLED screen driver based on stm32
Jerry's watch time synchronization [chapter]
Does C language srand need to reseed? Should srand be placed in the loop? Pseudo random function Rand
Tencent three sides: in the process of writing files, the process crashes, and will the file data be lost?
Js10day (API phased completion, regular expression introduction, custom attributes, filtering sensitive word cases, registration module verification cases)
Linear DP acwing 895 Longest ascending subsequence
阿里初面被两道编程题给干掉,再次内推终上岸(已拿电子offer)
JS6day(DOM结点的查找、增加、删除。实例化时间,时间戳,时间戳的案例,重绘和回流)
Linear DP acwing 902 Shortest editing distance
Js1day (syntaxe d'entrée / sortie, type de données, conversion de type de données, Var et let différenciés)
Traverse entrylist method correctly
Package management tools
Explain in detail the process of realizing Chinese text classification by CNN
[opencv learning] [image histogram and equalization]
Browser storage scheme