当前位置:网站首页>Haproxy cluster
Haproxy cluster
2022-07-04 12:03:00 【Feather weaving song】
Occupy the pit , Subsequent updates
One 、Haproxy brief introduction
Haproxy It's a use C Free and open source software written in language , It provides high availability 、 Load balancing , And based on TCP and HTTP Application proxy for .
1.1Haproxy Applied analysis
LVS In enterprise application, it has strong anti load ability , But there are shortcomings
LVS Regular processing is not supported , Can't achieve the separation of static and dynamic
For large websites ,LVS The implementation configuration of is complex , Maintenance costs are relatively high
Haproxy Is a high availability 、 Load balancing 、 And based on TCP and HTTP Application agent software
Suitable for heavy load web Site
Running on hardware, it can support tens of thousands of connection requests for concurrent connections
1.2Haproxy Characteristics of
Very good reliability and stability , Can work with hardware level F5 Load balancing devices
It can be maintained at the same time 40000-50000 Two concurrent connections , The maximum number of requests processed per unit time is 20000 individual , The maximum processing capacity can reach 10Git/s
Support up to 8 A kind of load balancing algorithm , It also supports session keeping
Support virtual host function , So as to achieve web Load balancing is more flexible
Support connection rejection 、 Unique functions such as fully transparent agent
Have a strong ACL Support , For access control
Its unique elastic binary tree data structure , The complexity of data structure is raised to 0(1), That is, the query speed of data will not decrease with the increase of data items
Support client side keepalive function , Reduce client and haproxy Multiple handshakes and three handshakes lead to resource cost , Let multiple requests in one tcp In connection
Support TCP Speed up , Zero copy function , Be similar to mmap Mechanism
Support response pooling (response buffering)
Support RDP agreement
Source based stickiness , Be similar to nginx Of ip_hash function , Scheduling requests from the same client to the same server upstream in a certain period of time
Better statistical data interface , Its web The interface displays the acceptance of each server in the backend 、 send out 、 Refuse 、 Statistics of errors, etc
Detailed health status testing ,web Interface for health detection status of upstream servers , And provides a certain management function
Traffic based health assessment mechanism
be based on http authentication
Command line based management interface
Log Analyzer , The log can be analyzed
1.3 Common load balancing strategies
Haproxy Support a variety of scheduling algorithms , The most commonly used ones are 8 Kind of
1)RR(Round Robin)
RR Algorithm is the simplest and most commonly used algorithm , Polling scheduling
Understand examples : There are three nodes A、B、C
The first user access is assigned to the node A
The second user access will be assigned to the node B
A third user access is assigned to the node C
The fourth user access continues to be assigned to the node A, Polling allocates access requests to achieve load balancing
2)LC(Least Connections)
Minimum number of connections algorithm , Dynamically allocate front-end requests according to the number of nodes connected to the back-end
Understand examples : There are three nodes A、B、C, The number of connections of each node is A:4 B:5 C:6
First user connection request , Will be assigned to A On , The number of connections becomes A:5 B:5 C:6
The second user request will continue to be assigned to A On , The number of connections becomes A:6 B:5 C:6; A new request will be assigned to B, Each time a new request is assigned to the client with the smallest number of connections
Because of the actual situation A、B、C The number of connections will be released dynamically , It's hard to have the same number of connections
This algorithm is compared with rr The algorithm has been greatly improved , It is an algorithm that uses more rice money
3)SH(Source Hashing)
Source based access scheduling algorithm , For some Session The session is recorded on the server , Can be based on the source of IP、Cookie Wait for cluster scheduling
Understand examples There are three nodes A、B、C, The first user's first access was assigned to A, The second user's first access is assigned to B
When the first user accesses the second time, it will be assigned to A, The second user will still be assigned to B, As long as the load balancer does not restart , The first user will be assigned to A, The second user access will be assigned to B, Realize the scheduling of clusters
The advantage of this scheduling algorithm is to keep the session , But some IP When the traffic is very large, it will cause load imbalance , Some nodes have a large number of accesses , Affect business use
4)uri
Means according to the request URI, do cdn Need to use
5)url_param
Express basis HTTP Request headers to lock each One Time HTTP request .
6)rdp—cookie(name)
According to cookie (name) To lock and hash every time TCP request .
7) source
Indicates that according to the source of the request IP, similar Nginx Of IP hash Mechanism .
8) static-rr
According to the weight , polling
边栏推荐
- Install freeradius3 in the latest version of openwrt
- TCP slicing and PSH understanding
- Cacti主机模板之定制版
- Digital simulation beauty match preparation -matlab basic operation No. 6
- Xshell's ssh server rejected the password, failed to skip publickey authentication, and did not register with the server
- Data transmission in the network
- Data communication and network: ch13 Ethernet
- QQ one click cookie acquisition
- Four sorts: bubble, select, insert, count
- Source code analysis of the implementation mechanism of multisets in guava class library
猜你喜欢
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9](/img/ed/0edff23fbd3880bc6c9dabd31755ac.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 9
Lecture 9
![[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20](/img/d5/4bce239b522696b5312b1346336b5f.jpg)
[Yunju entrepreneurial foundation notes] Chapter II entrepreneur test 20
Using terminal connection in different modes of virtual machine
OSI model notes
Reptile learning winter vacation series (2)
Take advantage of the world's sleeping gap to improve and surpass yourself -- get up early
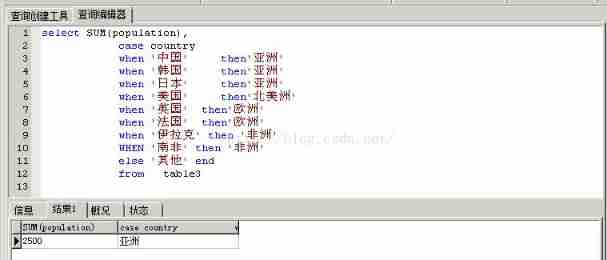
Usage of case when then else end statement
(August 10, 2021) web crawler learning - Chinese University ranking directed crawler
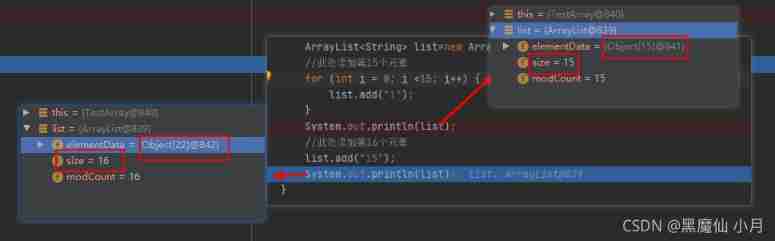
Detailed array expansion analysis --- take you step by step analysis
随机推荐
LxC shared directory permission configuration
Simple understanding of generics
Reptile learning winter vacation series (2)
Practical dry goods: deploy mini version message queue based on redis6.0
Btrace tells you how to debug online without restarting the JVM
(2021-08-20) web crawler learning 2
Process communication and thread explanation
OSI seven layer reference model
Number and math classes
QQ get group link, QR code
QQ get group settings
Lvs+kept realizes four layers of load and high availability
In 2022, financial products are not guaranteed?
Local MySQL forget password modification method (Windows) [easy to understand]
Usage of case when then else end statement
Usage of with as
Test question bank management system - database design [easy to understand]
Alibaba cloud server connection intranet operation
Is Sanli futures safe? How to open a futures account? How to reduce the handling charge of futures at present?
First knowledge of spark - 7000 words +15 diagrams, and learn the basic knowledge of spark