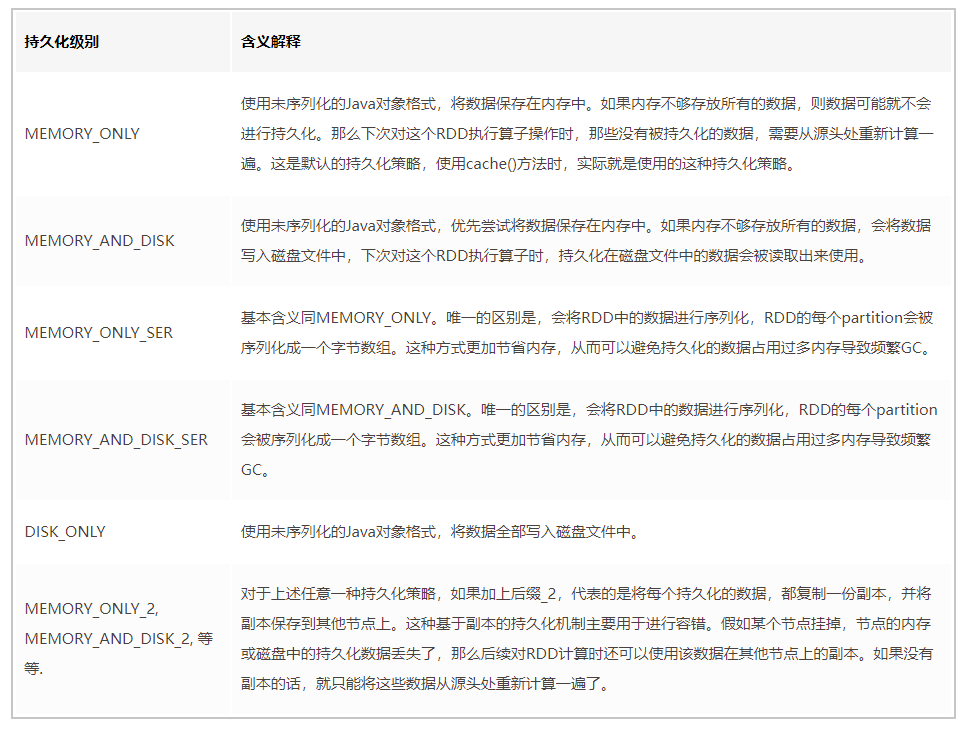
I was on the Internet before , I have also read some SAP ABAP Colleagues introduce how to pass ABAP Step by step debugging , Bypass SAP Standard permission check “ Tips ” The article , For example, modify the permission check statement in the debugger AUTHORITY-CHECK The return value of sy-subrc, Or simply use the debugger “ Jump to a statement ” This function , Bypass permission check statements directly .
Although said in SAP In the production system , By convention , Ordinary business users will never have the permission to debug , Let alone modify the value of variables in the debugger , But if it is in the development system , Modify the value of variables directly in the debugger , Or skip the execution of some statements , Is it really possible not to be discovered by others ?
The answer is No . Look at an example :
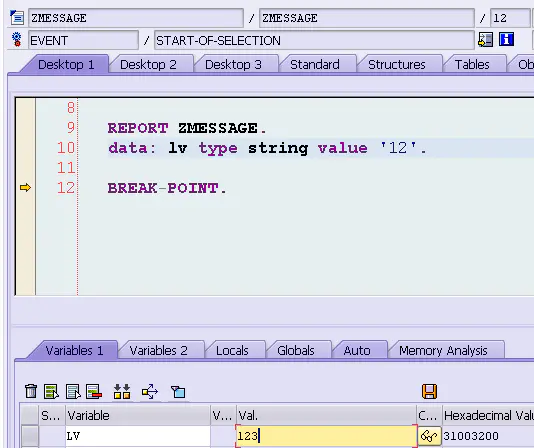
I am here ABAP The debugger changes the value of the variable from 12 Change to 123, Enter to make the change effective . Then the transaction code SM21, Open the system log viewing tool :
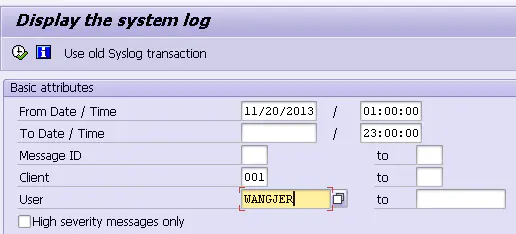
I was just ABAP The behavior of modifying variable values in the debugger , On record :
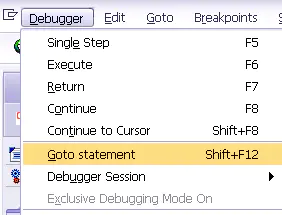
Try again in ABAP In the debugger , Use “Goto statement”, Skip some statements directly :
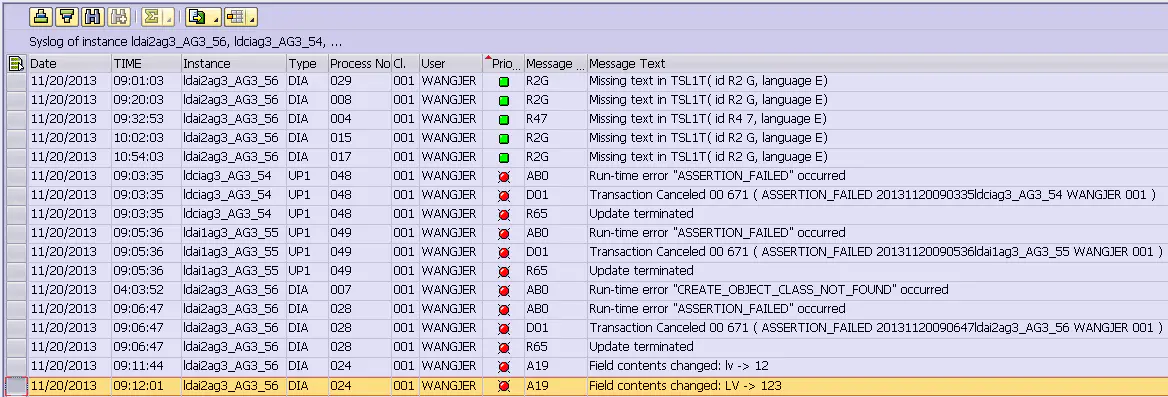
This behavior can not escape the record of the system log , Even from the first few lines ABAP The code jumps to another line , Are clearly recorded .
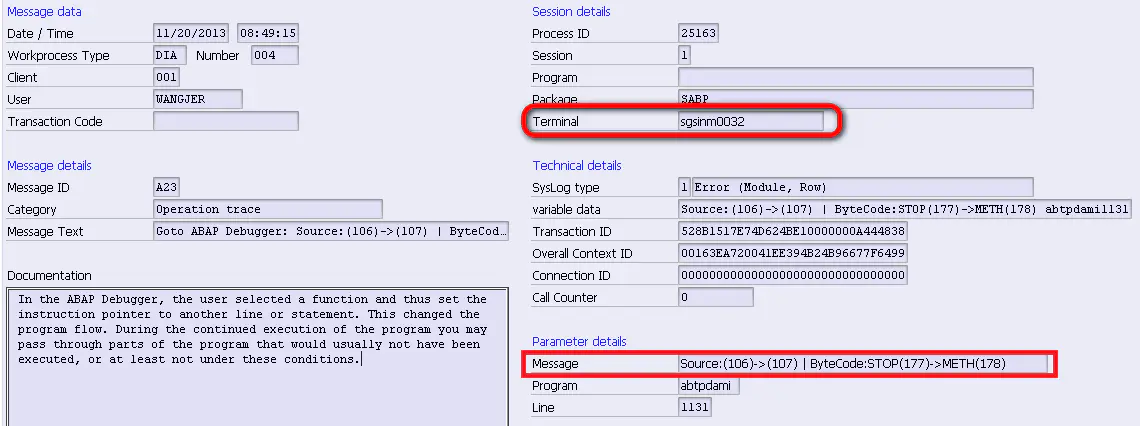
Terminal Field is the terminal machine used by the user who executed the statement jump in the debugger ID, Each connected to ABAP Netweaver Each machine on the server has a unique terminal ID.
Where are these system log files stored ? Click on Display Components, stay Component trace In the panel , Can selectively view certain types of system logs :
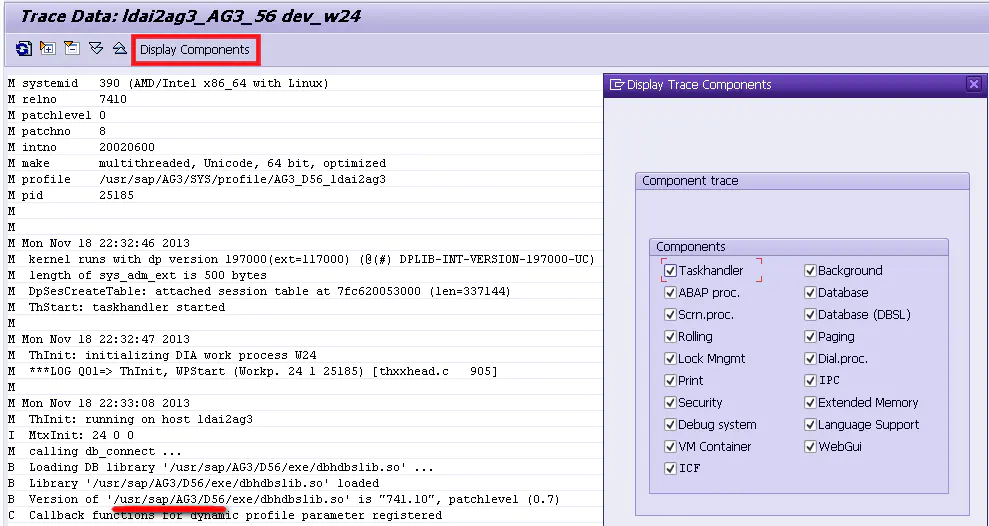
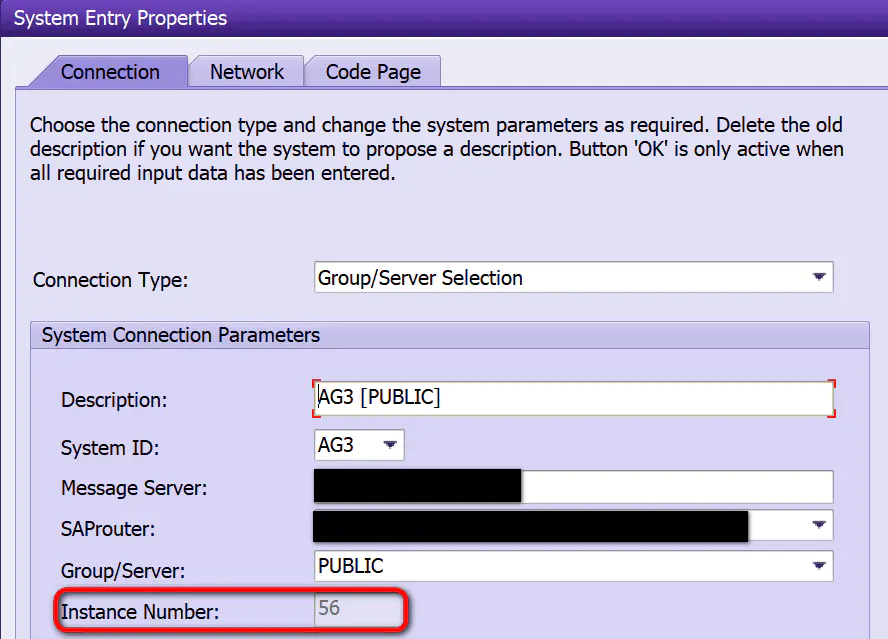
among /usr/sap/AG3/D56 Path at the beginning , That is, I am currently logged in Application Server,ID by AG3,instance numeber by 56 The working directory of this server :
Use transaction code AL11 Follow this path , stay work These system log files can be found in subdirectories :
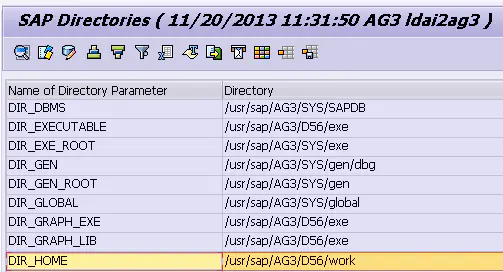
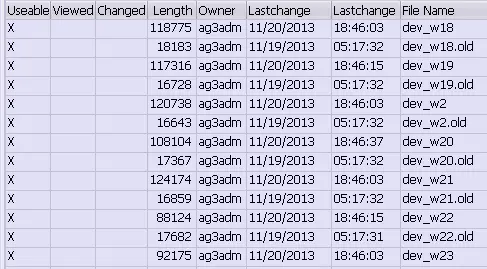
Ordinary ABAP The user does not have access to the operating system , You cannot write to these system log files .
To make a long story short , Once you use the method of single step debugging to bypass some permission checks or perform other dangerous operations , These behaviors are immediately recorded in the system log , Ordinary users cannot delete these log files .
SAP The authority control system of the system is well designed , When you find that you lack the authority to execute a certain transaction in your actual work , Please follow SAP Standard process of authority control to solve problems . adopt ABAP Single step debugging bypasses permission checking , In no case SAP Recommended solutions . Even before you want to do this on the development system , Be sure to think twice before you act .
It's over SAP ABAP Authority control in the system , Let's take a look at the implementation of its transaction recording function .
Used to “ Plague bar ” After 70, after 80 , about Windows The registry must be familiar . At that time, it seemed a little distant , There are even many specially published books , Professor how to modify Windows Registry to improve system performance , Or enable some Microsoft defaults disable The hidden function of .


We know Windows The registry is used to store the setting information of the system and Applications , from Windows 95 Enable the Windows10.

that SAP GUI List of transaction codes used in the command line , Will it also be saved in Windows Somewhere in the system registry ?
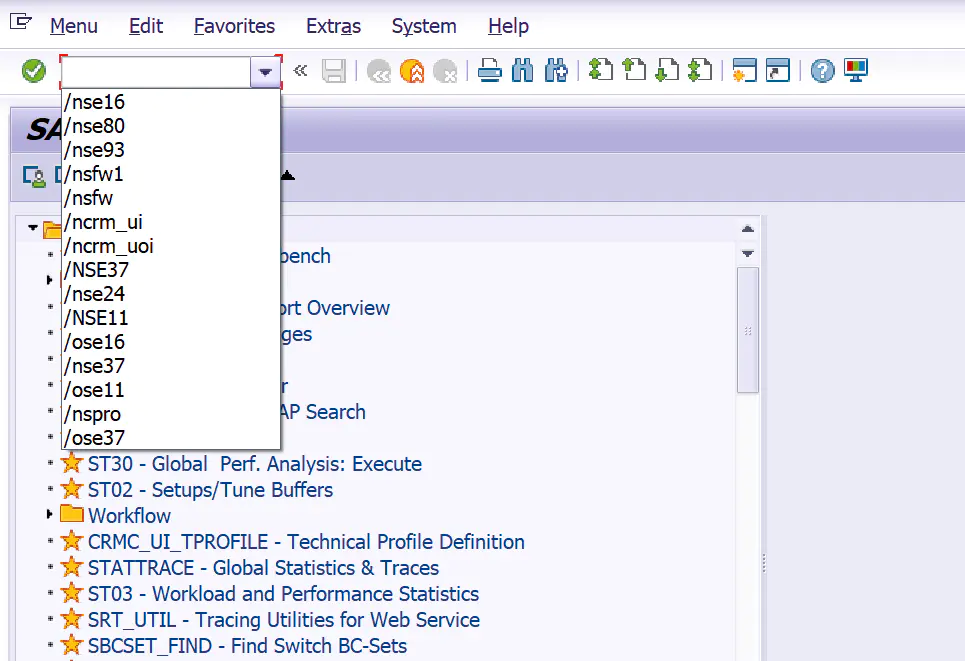
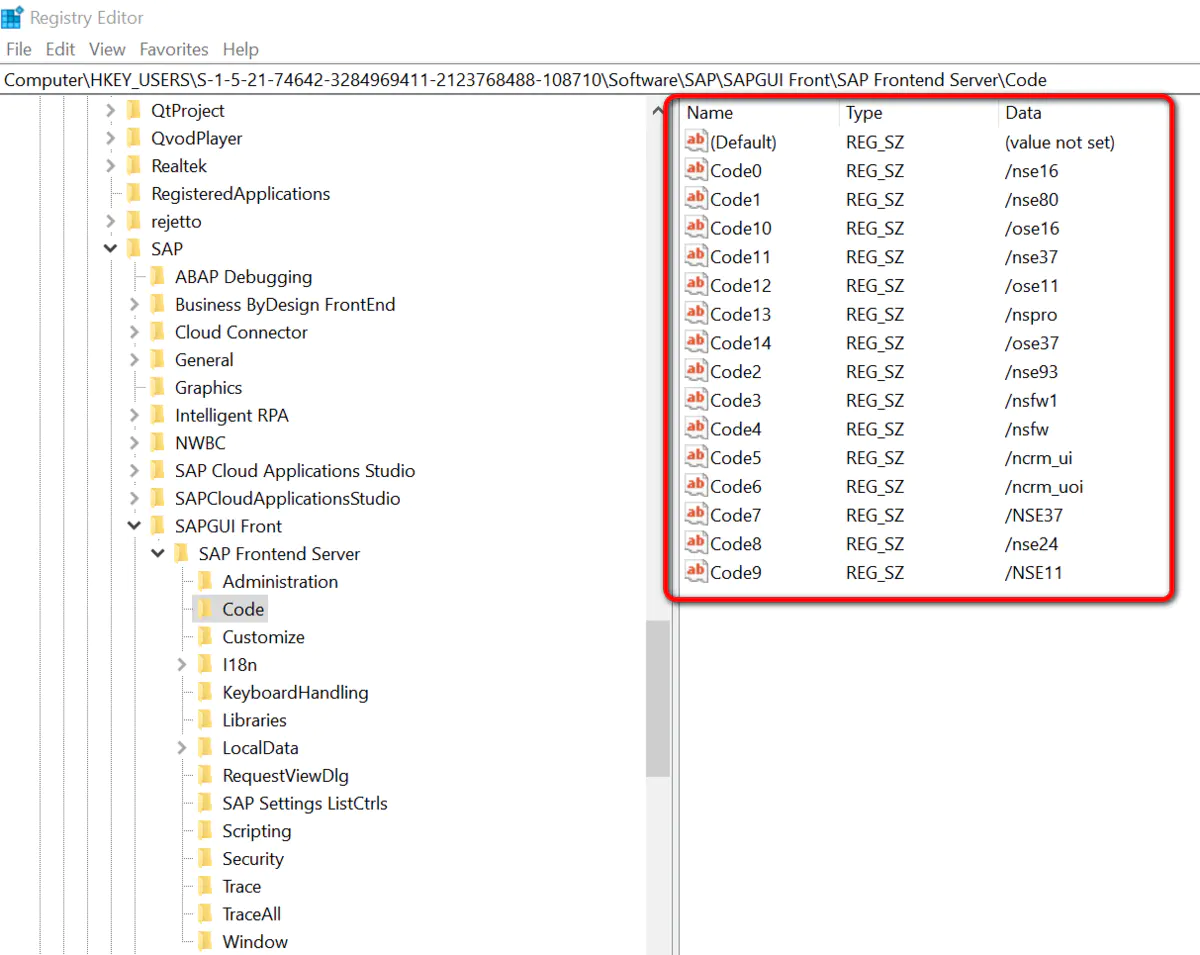
Windows In the operating system ,Win + R, perform regedit Open the registry , Along the path HKEY_USERS\Software\SAP\SAPGUI Front\SAP Fronted Server\Code an , You can see a list of these used transaction codes .
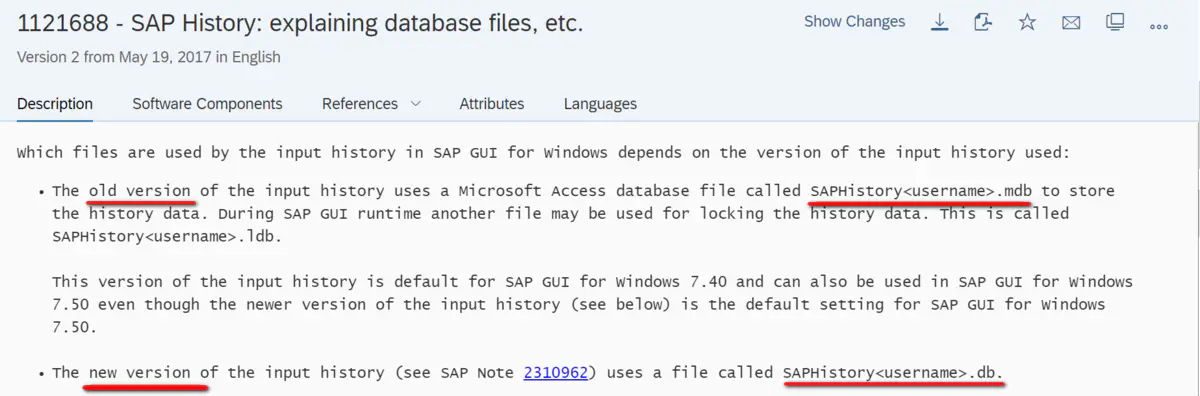
Again , In the local SAP GUI Under the table of contents , Yes SAPHistory<User Name>.db and SAPHistory<User Name>.mdb These two documents :
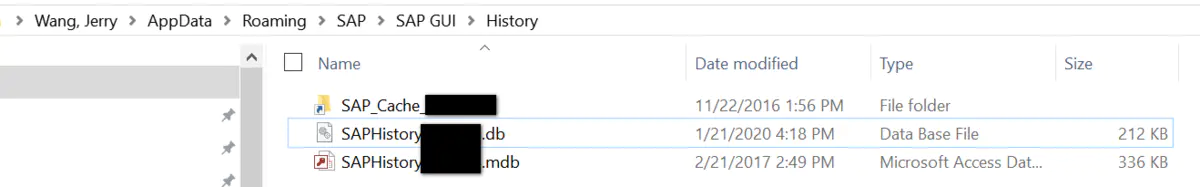
according to SAP note 1121688 - SAP History: explaining database files, etc That's what I'm saying , Extension .mdb The file is an old version SAP GUI Use , and .db Corresponding to the new version .
Teaching a man to fish is better than giving him a fish , How to find SAP GUI The registry location where this local information is stored ?
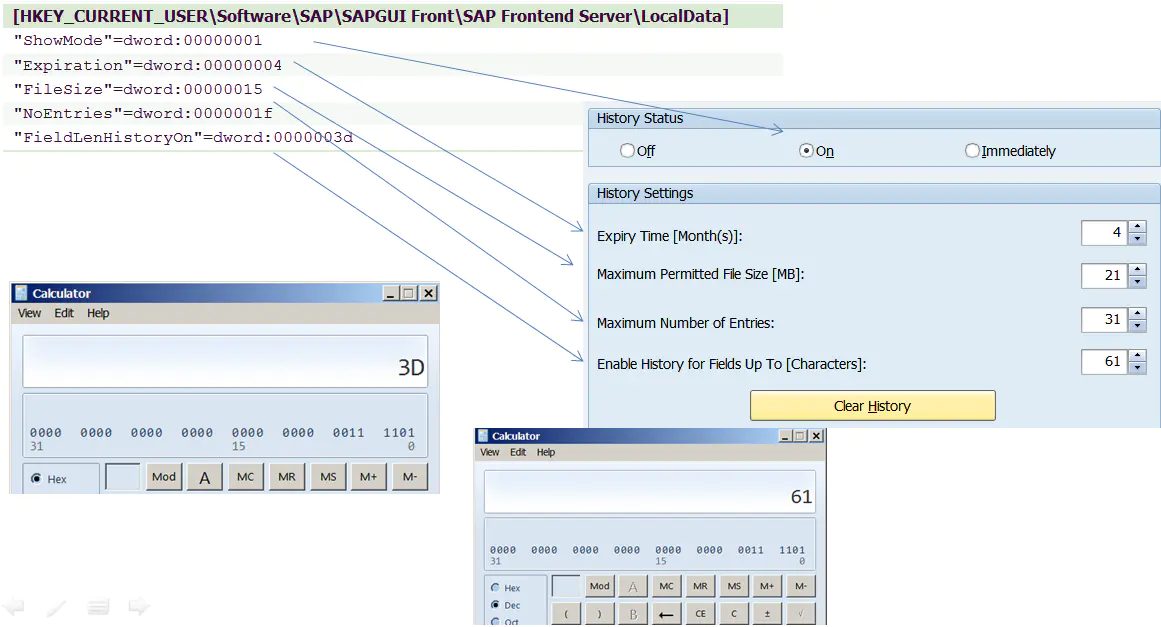
Suppose you want to know the following History Settings Whether the value of is maintained in Windows In the registry ,
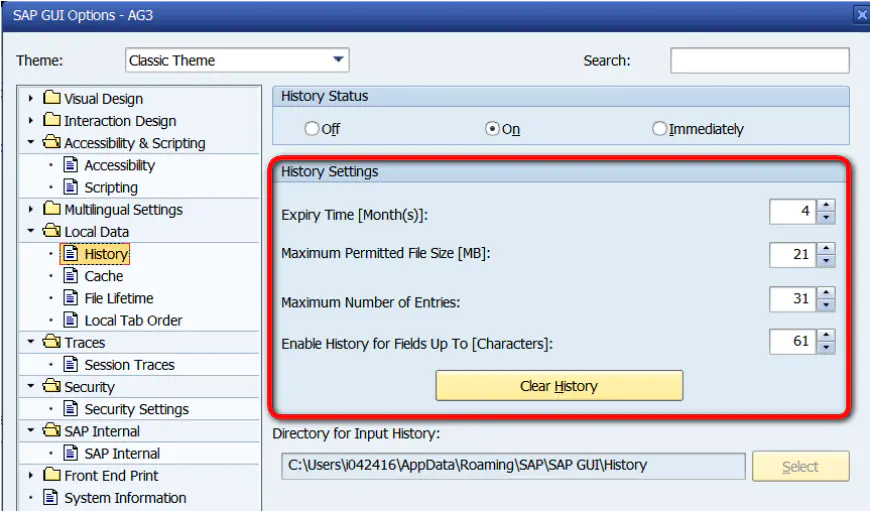
First , Before modifying the settings , Export a registry image file before.reg:
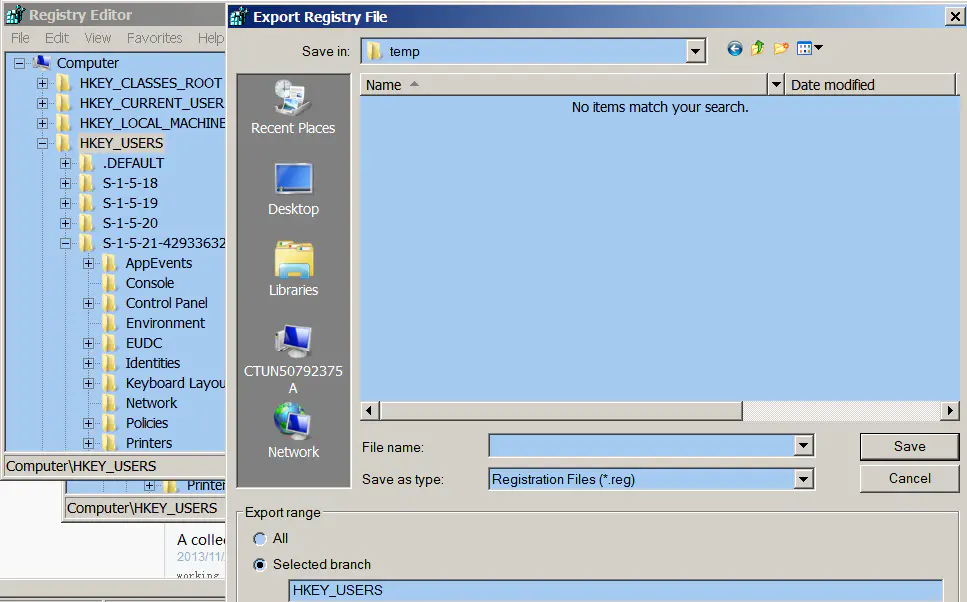
stay SAP GUI Modify the settings in , After the save , Export the second registry image file after.reg, And then use Windows Self contained file comparison tool fc Compare the differences between the two image files , The result is SAP GUI These settings are in Windows Location in the registry .
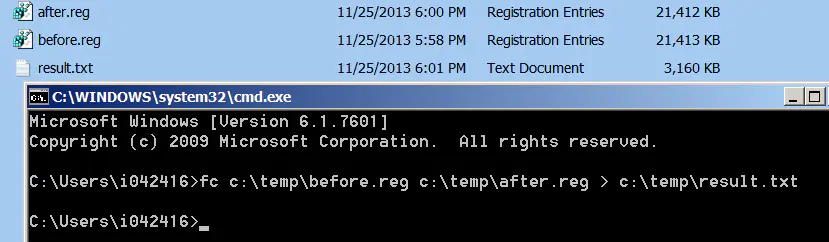
give the result as follows :
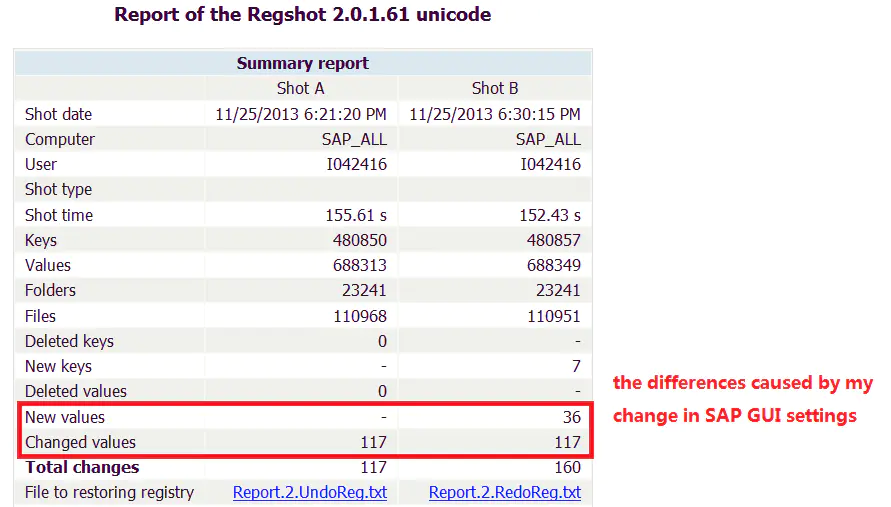
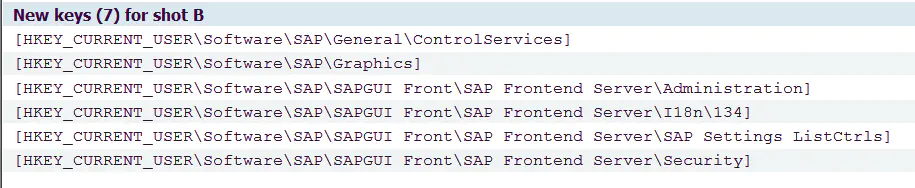
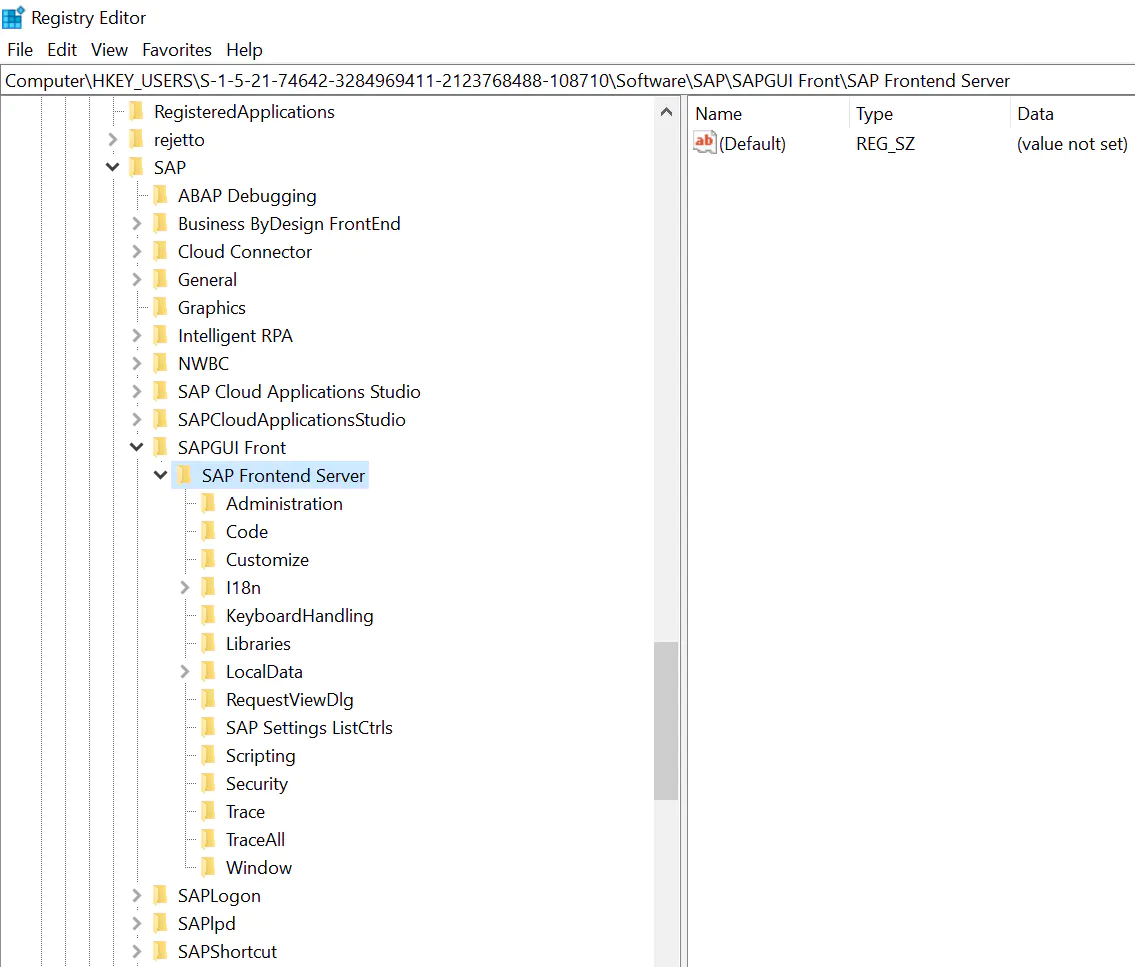
Most registry entries are located in SAPGUI Front Under this node , And trace upward from this node , You can also find others SAP The value written by the software in the registry , such as SAP Cloud Connector,SA Cloud Application Studio,SAP Intelligent Robotic Process Automation Kit, etc .
SAP GUI In the setup checkbox If you tick , Corresponding Windows The value in the registry is maintained as 00000001:
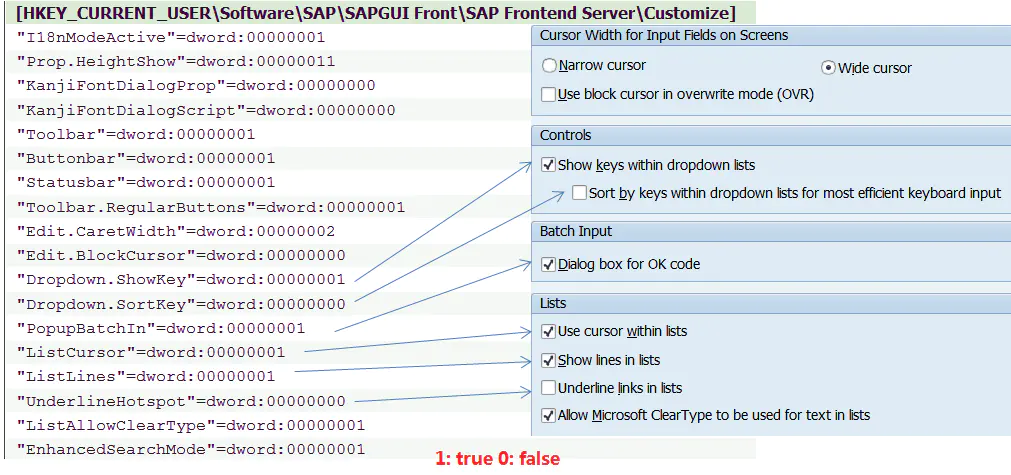
And in the SAP GUI The value stored in decimal system , Stored in Windows It will be automatically converted to hexadecimal in the registry :
summary
This paper starts from SAP System developers try to bypass the monitoring of system permissions by means of one-step debugging, and analyze the behavior itself and its consequences , It introduces SAP Complete realization of system authority control , Then from Windows Registry expansion category of the operating system , It introduces SAPGUI How the transaction logging function works .
原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/188/202207071443222535.html