当前位置:网站首页>What is web application security testing technology?
What is web application security testing technology?
2022-07-01 17:58:00 【Yisixun College】
In order to find software vulnerabilities and defects , Make sure Web The application is secure before and after delivery , We need to make use of Web Apply security testing techniques to identify Web Weaknesses and vulnerabilities of the architecture in the application , And before hackers can find and use them .
Web After years of development, applied security testing technology , At present, the commonly used technologies in the industry are mainly divided into 3 Major categories .
DAST:
Dynamic application security testing (Dynamic Application Security Testing) Technology analyzes the dynamic running state of an application in the test or run phase . It simulates hackers to attack applications dynamically , Analyze the response of the application , To determine the Web Whether the application is vulnerable .
DAST It is a black box testing technology , Is currently the most widely used 、 Use the simplest one Web Apply security testing methods , Tools commonly used by safety engineers, such as AWVS、AppScan Waiting is based on DAST Principle products .
SAST:
Static application security testing (Static Application Security Testing) Technology usually analyzes the syntax of the application's source code or binary files in the coding phase 、 structure 、 The process 、 Interface to find the security vulnerabilities in the program code .
exceed 50% The security vulnerability of is caused by wrong coding , Developers generally lack safety development awareness and skills , Pay more attention to the realization of business functions . If you want to control vulnerabilities from the source, you need to develop a code detection mechanism ,SAST It is a kind of test plan to test the source code and find security vulnerabilities in the development stage .
IAST:
Interactive application security testing (Interactive Application Security Testing) yes 2012 year Gartner A new application security testing solution proposed by the company , Through agency 、VPN Or deploy on the server side Agent Program , collect 、 monitor Web Application runtime function execution 、 The data transfer , And interact with the scanner in real time , Efficient 、 Accurately identify security defects and vulnerabilities , At the same time, it can accurately determine the code file where the vulnerability lies 、 Row number 、 Functions and parameters .IAST Equivalent to DAST and SAST An interrelated runtime security detection technology combined with .
IAST Interactive application security testing technology is a hot new application security testing technology in recent years , Ever been Gartner The consulting company is listed as a leader in the field of network security Top 10 One of the technologies .IAST Integrated DAST and SAST The advantages of , The vulnerability detection rate is very high 、 False positives are extremely low , At the same time, you can locate API Interfaces and code snippets .
边栏推荐
- Redis master-slave realizes 10 second check and recovery
- Gameframework eating guide
- Redis -- data type and operation
- Is the software of futures pioneer formal and safe? Which futures company is safer to choose?
- Oracle TRUNC function processing date format
- Apk signature process introduction [easy to understand]
- transform. Forward and vector3 Differences in the use of forward
- Redis主从实现10秒检查与恢复
- Why should you consider using prism
- 網上股票開戶安全嗎?是否可靠?
猜你喜欢
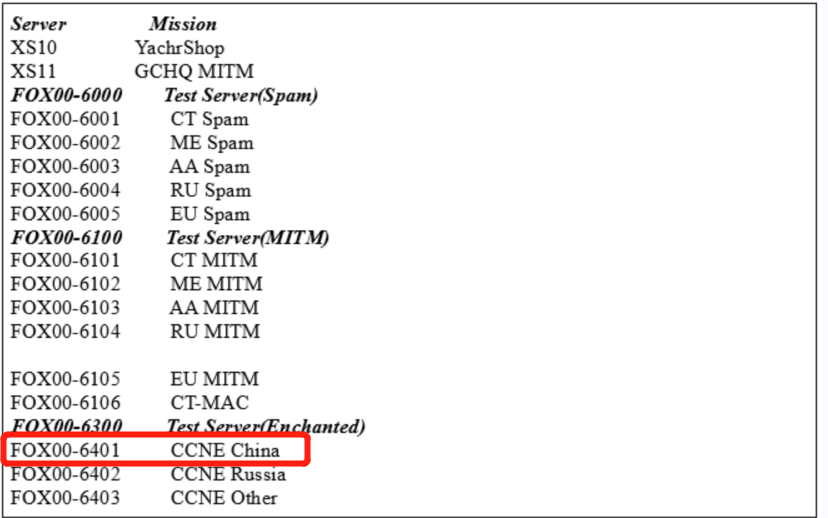
Heavy disclosure! Hundreds of important information systems have been invaded, and the host has become a key attack target
New 95 community system whole station source code

Gold, silver and four job hopping, interview questions are prepared, and Ali becomes the champion
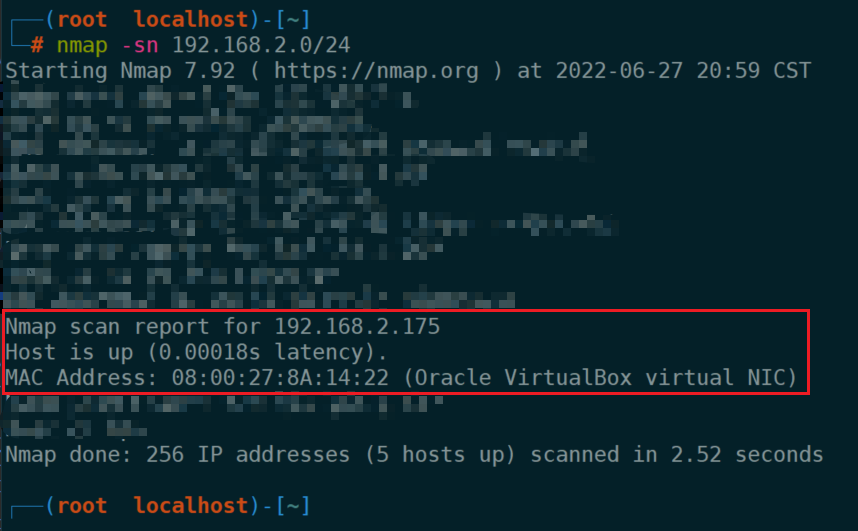
Vulnhub range hacksudo Thor
Apache iceberg source code analysis: schema evolution
Product service, operation characteristics
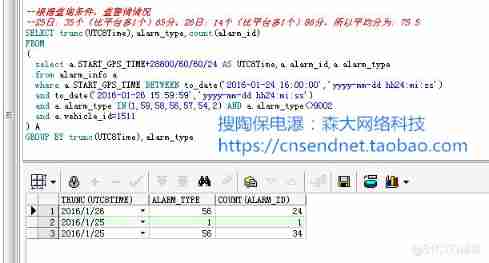
Oracle TRUNC function processing date format

Good looking UI mall source code has been scanned, no back door, no encryption

Cassette helicopter and alternating electric field magnetic manometer DPC
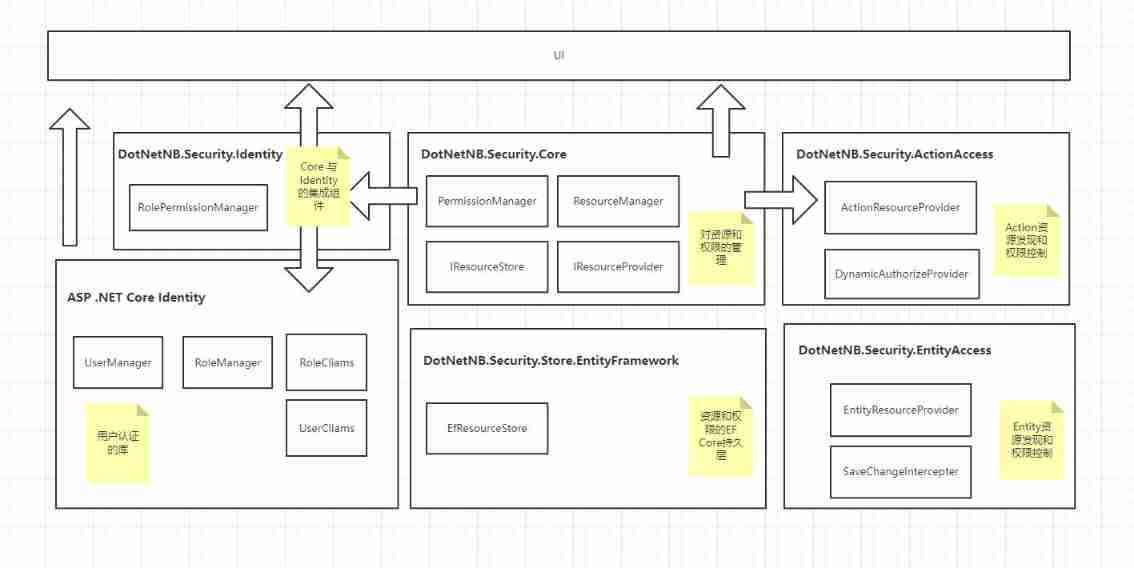
. Net cloud native architect training camp (permission system code implements actionaccess) -- learning notes
随机推荐
At present, where is the most formal and safe account opening for futures speculation? How to open a futures account?
传感器尺寸、像素、DPI分辨率、英寸、毫米的关系
C language implementation of sum of two numbers [easy to understand]
EasyCVR通过国标GB28181协议接入设备,出现设备自动拉流是什么原因?
APK签名流程介绍[通俗易懂]
Why should you consider using prism
MFC obtains local IP (used more in network communication)
An example of data analysis of an old swatch and an old hard disk disassembly and assembly combined with the sensor of an electromagnetic press
Work and leisure suggestions of old programmers
Check log4j problems using stain analysis
Rotation order and universal lock of unity panel
Common design parameters of solid rocket motor
Kernel stray cat stray dog pet adoption platform H5 source code
golang中的select详解
Intel's open source deep learning tool library openvino will increase cooperation with local software and hardware parties and continue to open
China biodegradable plastics market forecast and investment strategy report (2022 Edition)
Small exercise -- subnet division and summary
Kia recalls some K3 new energy with potential safety hazards
What are the six steps of the software development process? How to draw software development flow chart?
Blackwich: the roadmap of decarbonization is the first step to realize the equitable energy transformation in Asia