当前位置:网站首页>Zhou Yajin, a top safety scholar of Zhejiang University, is a curiosity driven activist
Zhou Yajin, a top safety scholar of Zhejiang University, is a curiosity driven activist
2022-07-07 04:32:00 【qubit 】
AMiner × qubits Co-produced
Editor's note :
Zhou Yajin , Now he is the school of computer science and technology and the school of Cyberspace Security of Zhejiang University “ Hundred people plan ” researcher .
2010 year , In the first year of mobile security , He happened to be a doctoral student and turned from computer underlying technology to mobile security , He studied under Professor jiangxuxian, a famous scholar of computer security .
From then on, I started my career in safety research , from 0 Participated in the rise of a field .
He described his love for computers —— In fact, there is no need for external support or conditions , Just a refrigerator full of coke and pizza , A computer , Some courage to move forward , You can use computers to create what you want to create .
Now , As a researcher of Zhejiang University, he is still enjoying the fun of safety research , It is pointed out that at present, we overemphasize new attack scenarios and attack vectors , Instead, it ignores the construction of systematic security system and defense .
The latter is what should be done with great effort .
This year, 1 month , stay AMiner The team launched AI 2000 In the list , Zhou Yajin was selected 2022 The most influential scholar of artificial intelligence in the world .
AMiner I also had the honor to have an in-depth dialogue with him .
△ Picture source CCF Blockchain Technology Conference
During the doctor's period, turn the track , Make top groundbreaking research
2010 Is considered the first year of mobile security .
At that time, smart phones were just beginning to mature and popularize , Existing Apple releases iOS 4, And then there is Google One after another Android 2.1、2.2 and 2.3.
But the world is beginning to open , Inevitably, there are also chaotic corners .
Soon , The piracy and cracking of mobile games are in full swing ,iOS Prison break is recognized as legal in some countries , Malware has become “ Homely food ”.
In the same year , Zhou Yajin entered the Department of computer science at North Carolina State University to study for a doctorate , He studied with Dr. jiangxuxian, a famous computer security scholar .
At that time, the research team mainly studied security issues related to the research and development of underlying system technology , This research direction is new to Zhou Yajin , It also inherits his previous research background of computer operating system , therefore , Zhou Yajin started his safety research career .
Zhou Yajin's research team is one of the earliest mobile security research teams in the world .
For researchers , from 0 Start to participate in the rise of a field , Is a kind of luck , It is also a new challenge .
Zhou Yajin's research team started from mobile APP Study these phenomena from the perspective of ecological security .
They noticed , At that time, the mobile ecosystem was very chaotic , There are many malicious applications entering the third-party market , Even the official market of Google has many malicious applications , Third party mobile phone manufacturers can even pre install at will APP, And pre installed APP Cannot uninstall .
besides , There are also many advertising platforms that steal users' privacy 、 Pirate APP etc. .
that , Where exactly do these malicious applications come from ? How it's spread ? What is the specific working method ?
Although there is no person in the industry to entrust or exchange these issues with the research team , But Zhou Yajin's research team judged , These questions are very important .
And at this time, there is no research on the market that can well answer these questions . Although some scholars are also aware of the seriousness of these problems , But I still don't know where to start .
Start with the above questions , from 2010 Year begins , Under the leadership of Professor jiangxuxian, Zhou Yajin's research team has been collecting data about mobile phones in the market APP Software samples .
As the number of samples increases , The samples they collected were even more complete than some professional security companies at that time .
Of course , Just collecting samples is not enough .
On this basis , They have developed new technology , To detect and understand the complete working mode of these mobile malicious applications , Finally formed 2012 This article was IEEE S&P Received groundbreaking research in the field .
In the largest study at that time , They shared the underlying technology architecture and complete APP sample , This is also one of the early important open source practices in the field of mobile security .
Take this study as the starting point , stay 2010 Year to 2018 Year of 8 Within a year , The whole industrial chain of industry has joined , The scale of research on malicious applications is growing , More and more R & D engineers have collected more data , And then develop more advanced technology , Top academic conferences also appeared in large numbers Android Various papers on safety .
at present , according to AMiner data display , The citation rate of this study has reached 2679, And the paper is related Android Malware Genome Project, It is also one of the most valuable reference projects for Android security researchers , It has benefited the global security industry .
Driven by various forces , Currently mobile APP Most of the problems in security have been alleviated , The whole ecosystem has also become more mature and orderly , The ultimate benefit is hundreds of millions of smart phone users around the world .
Security Research “ Broken and standing ” Unique experience of
When asked whether it is a kind of “ Dimension reduction blow ” when , Zhou Yajin denied this statement .
But he also stressed , In his early years, he benefited a lot from the research and development of the underlying technology of computer systems , It is precisely because of the foundation of basic theory , So in the study of mobile security and other security issues , To be more handy , Energy sources constantly absorb nutrients .
Zhou Yajin said , No matter what direction of safety research , Or make application products , The underlying technology is important , We need to lay a good foundation .
For example, the subject of information security , Part of its root is in Computer Science , Understand how the whole computer system works , In this way, no matter what application direction is studied , Can provide better support .
therefore , If you want to engage in the field of safety , He felt that he might need several qualities :
1、 Curiosity . When we discuss a new problem or see a new thing , You will deconstruct its principle from all aspects , Want to know urgently how it works . After knowing how it works , You will want to know whether some assumptions in the system are not tenable in the actual process , In this way, you can think of points and angles that others may not think of . So curiosity is very important ;
2、 Lay the foundation . As mentioned above , There is system security in computer security 、 Password security and other fields , But most of the roots in the field of system security are still in Computer Science , Like the operating system 、 Architecture 、 Compiler principle , These are the three core courses of computer , So we must lay a good foundation ;
3、 At ordinary times, you can cultivate more skills with both attack and defense .
in fact , These characteristics are also Zhou Yajin's personal experience in safety research for many years .
On his homepage , There is such a bold English :
If you want to set off and go develop some grand new thing, you don’t need millions of dollars of capitalization. You need enough pizza and Diet Coke to stick in your refrigerator, a cheap PC to work on, and the dedication to go through with it.
This passage comes from the big bull in the game industry John Carmack.
The reason why Zhou Yajin showed this passage on his homepage , On the one hand, he is right John Carmack The feeling of appreciation , On the other hand , It is also because this passage shows his love for computers ——
You don't really need external support or conditions , Just a refrigerator full of coke and pizza , A computer , Some courage to move forward , You can use computers to create what you want .
“ As long as you are curious, you will want to practice something by yourself ,Make your hands dirty To experience a lot of fun in the process .
This passage actually has a great impact on me , Until today, , I will still practice some ideas by myself .
This is also the charm of computer security research , If you are just a system builder , Then you will never have the fun and experience of being a system breaker .
Of course, this does not mean that we are encouraged to be the destroyer of the system , But do it safely , Destructive thinking is needed , It can let you feel the fun of destruction by a reasonable and legal means , And in this process, you can get the pleasure of system construction , Because after destruction, we need to think about the problem of construction .
After the destruction, we can draw inferences from one instance , Can better understand the weakness of the system , Consider safer situations , This is the greatest pleasure for me to do safety research .
You can experience the pleasure and freshness of destruction , You can also feel the sense of success in building the system , This is what makes security research different .”
In the field of security , Innovation is not necessarily a commendatory word
Now? , With the maturity of mobile security research , Zhou Yajin, a researcher in the school of Cyberspace Security of Zhejiang University , It mainly carries out research in the following two directions .
First of all , Blockchain security , Including the understanding of criminal acts related to cryptocurrency 、 Expose and detect .
second , Develop a security platform for software and hardware collaboration .
He thinks that , The whole security field can be simply divided into attack and defense , But security is also hierarchical .
The underlying operating system needs security , After the operating system is secure , To protect the security of the upper system framework . After the security of the upper system framework , To protect the security of higher-level applications .
therefore , He hopes to start from the bottom CPU And hardware , Propose a complete set of hardware system supporting the upper security mechanism .
The security of the operating system must be protected by the underlying hardware , Otherwise, the operating system itself is unsafe . If you need to lose in order to make the operating system more secure , such as 30% Performance overhead , No manufacturer will use such a scheme . therefore , From the bottom CPU Starting from the mechanism of , Define some simple modifications in the hardware that can make the operating system more secure , At the same time, the performance overhead becomes very small .
Although software security itself has also made great progress , But Zhou Yajin believes that there is a difference between researchers in the safe community and researchers in the system direction .
for example , The former is often able to deal with “ spot ” React to attacks and defenses on , But the latter may be more inclined to “ Noodles ” Think about how to develop an efficient and safe system as a whole .
In the past, security research in academia actually aimed more at publishing papers , Relatively few have been industrialized .
But for Zhou Yajin and his team , Such as how to be in CPU Add a new security attribute in , How to implement new security functions in a chip architecture , How to transform research into actual products , Need to think as a whole .
At present, they have had in-depth cooperation with domestic manufacturers in software and hardware collaborative security .
Although it has shifted from mobile security to blockchain, software and hardware collaborative security and other emerging security directions , But Zhou Yajin believes , Look at the whole security field , The demand for security has not changed significantly , Just the security scene is changing , The emergence of every emerging field , There will be accompanying security needs .
besides , How to propose a more complete defense system from the perspective of the overall situation or system , It is still the weakness of the whole field .
“ Our country has invested a lot in the field of security , Especially in recent years , The subject of Cyberspace Security has received attention .
But I think , At present, we overemphasize the new attack scenarios and attack vectors , Instead, it ignores the construction of systematic security system and defense , The latter is what should be done with great effort .
Whether it's academia or industry , Many studies are about how to break a system , Or what new methods and vulnerabilities have been used to break the system , But there are few that can put forward what the defense system of the system should be .
We usually talk about , Attacks are like acupoints , Point to an acupoint , It may be paralyzed by the attacker . But defense is not like this , Defense means wearing protective clothing at every acupoint of the body 、 magic ability to sustain the thrusts of sharp weapons on one's bare skin , As long as there is any point not taken into account , Or not so thoughtful , You may be attacked .
This kind of research is very deficient , Nor is it valued . At present, the two types of research are unbalanced ”.
As a researcher with rich experience in both industry and academia , Zhou Yajin also has different views on innovation in the field of security .
as everyone knows , Innovation is highly respected in academia , But he believes that innovation is not entirely a commendatory word :
We often talk about innovation , But innovation will also go to some extreme , Is to innovate for the sake of innovation , At this point, you will put forward some very fancy、 Very cool , But in fact, it is difficult to land things , The assumption required is completely unfounded in practice . therefore , On the one hand, we need to have a cutting-edge vision of academia , Be able to stand high , Can be separated from the industry and the small problems solved , Jump out and look at the trends of the entire security industry . On the other hand, be down-to-earth , You can't just pursue academic fancy Things that are , Only by combining the two , It is possible to make influential research .
About Zhou Yajin
Zhou Yajin , College of computer science and technology and College of Cyberspace Security, Zhejiang University “ Hundred people plan ” researcher ,2015 Received a doctorate from North Carolina State University in .
Engaged in system security research for a long time , Current research focuses on real-world threat perception 、 Analysis and defense , Focus on the safety of software and hardware collaborative system , Hardware based trusted secret Computing ( Such as Trustzone and SGX) Other fields .
Zhou Yajin has 10 This paper was published at four top-level conferences in the field of security , Two of the papers are selected from 1980 The most cited since 100 List of safety papers ( Ranking the first 13 and 86).
As a co-author, he has won the best paper award many times ( Include IEEE EURO S&P 2019, IEEE ICPADS 2018 etc. ), He has also served as a top safety academic conference for many times ( Include ACM CCS 2019, IEEE EURO S&P 2019, 2020, IEEE S&P 2021) A member of the procedure Committee .
Personal home page : https://www.aminer.cn/profile/562b0a5145cedb339896b6f7
About AI 2000 The list :
This year, 1 month ,AMiner Team launch AI 2000 The list , To pass through AMiner Academic data selected globally over the past decade , Artificial intelligence is the most influential discipline 、 The most dynamic top scholars , Praise their outstanding contribution to the field of artificial intelligence research .
Click on 【 Read the original 】 Learn more about AI 2000 The complete contents of the list .
— End —
「 qubits · viewpoint 」 Live registration
What is? “ Intelligent decision making ”? What is the key technology of intelligent decision ? How will it build a leading enterprise for secondary growth “ Intelligent gripper ”?
7 month 7 On Thursday , Participate in the live broadcast , Answer for you ~
Focus on me here , Remember to mark the star ~
One key, three links 「 Share 」、「 give the thumbs-up 」 and 「 Looking at 」
The frontier of science and technology meets day by day ~
边栏推荐
- Unit test asp Net MVC 4 Application - unit testing asp Net MVC 4 apps thoroughly
- leetcode 53. Maximum subarray maximum subarray sum (medium)
- NFT meta universe chain diversified ecosystem development case
- [team learning] [34 issues] scratch (Level 2)
- 每人每年最高500万经费!选人不选项目,专注基础科研,科学家主导腾讯出资的「新基石」启动申报
- Digital chemical plant management system based on Virtual Simulation Technology
- Optimization of channel status offline of other server devices caused by easycvr cluster restart
- 軟件測試之網站測試如何進行?測試小攻略走起!
- 未婚夫捐5亿美元给女PI,让她不用申请项目,招150位科学家,安心做科研!
- Complimentary tickets quick grab | industry bigwigs talk about the quality and efficiency of software qecon conference is coming
猜你喜欢

科兴与香港大学临床试验中心研究团队和香港港怡医院合作,在中国香港启动奥密克戎特异性灭活疫苗加强剂临床试验
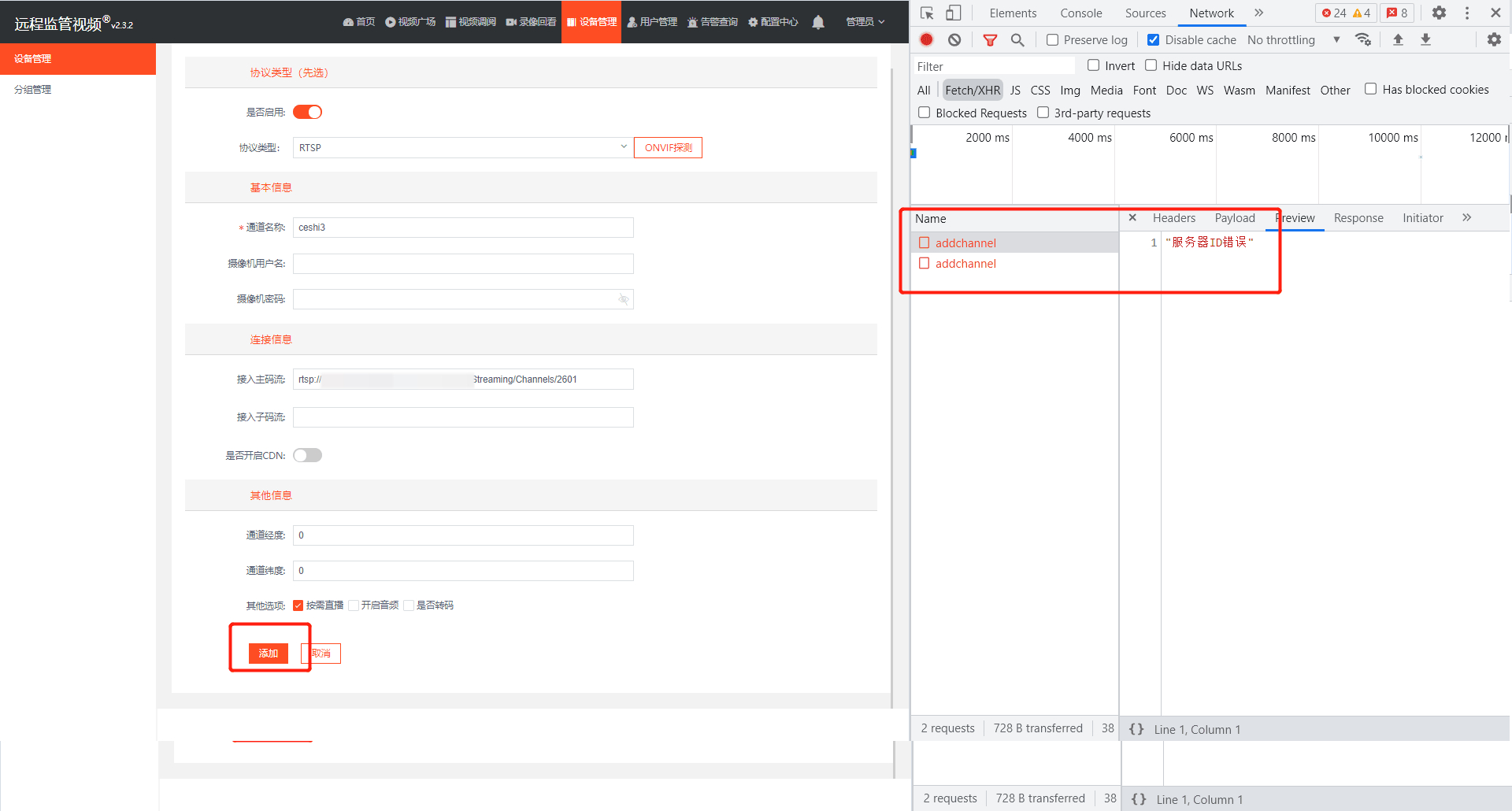
How to solve the problem of adding RTSP device to easycvr cluster version and prompting server ID error?
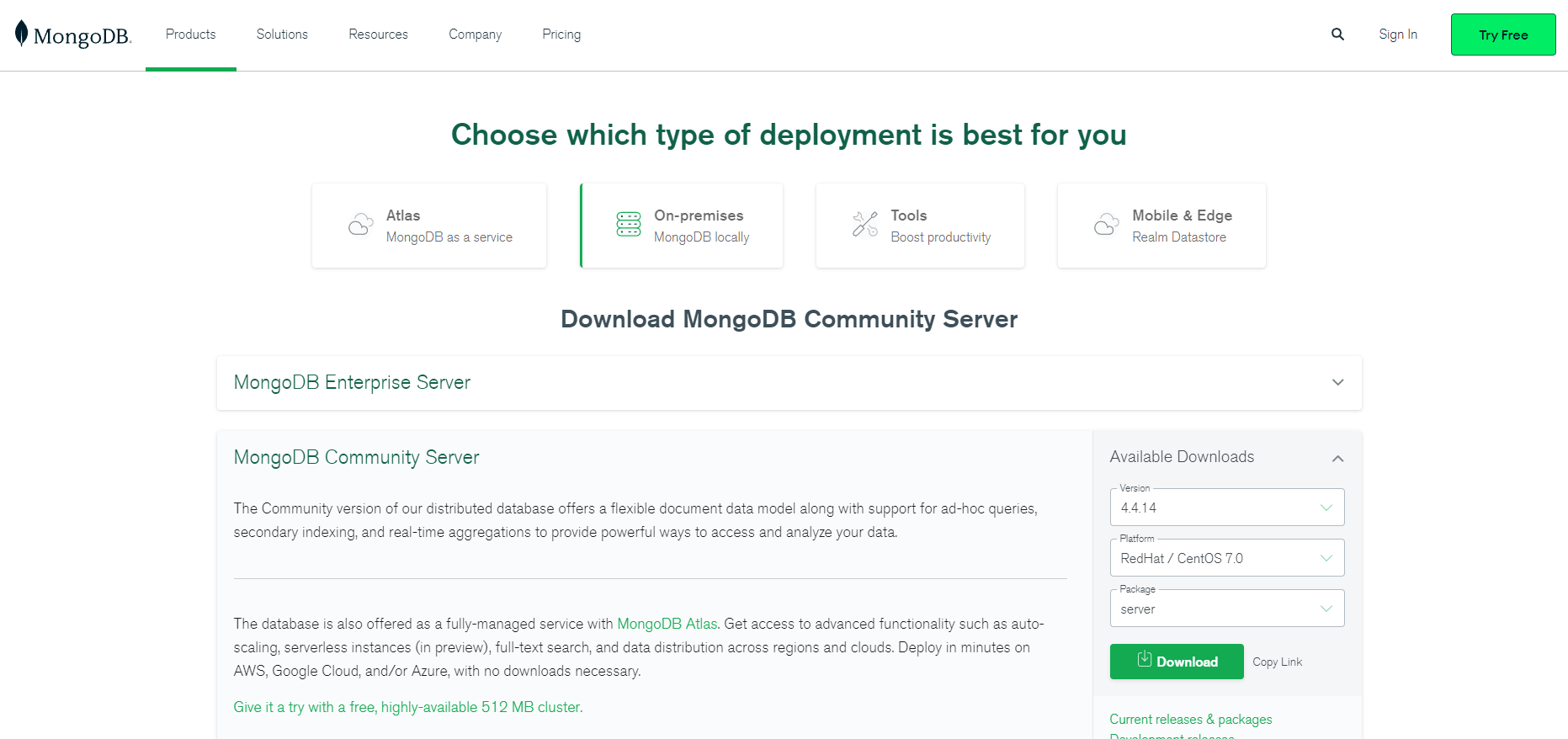
The most complete deployment of mongodb in history

【实践出真理】import和require的引入方式真的和网上说的一样吗

用CPU方案打破内存墙?学PayPal堆傲腾扩容量,漏查欺诈交易量可降至1/30

英特尔David Tuhy:英特尔傲腾技术成功的原因

The easycvr platform is connected to the RTMP protocol, and the interface call prompts how to solve the error of obtaining video recording?
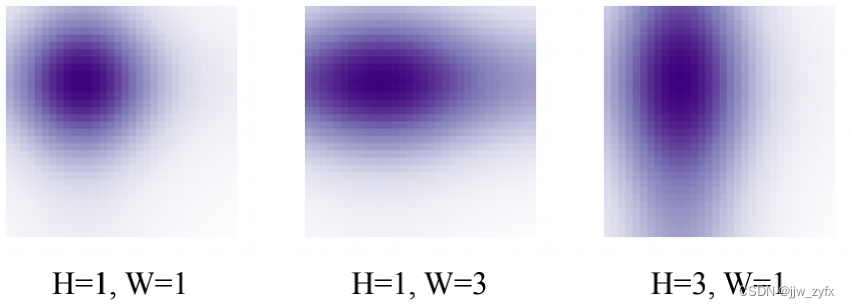
DAB-DETR: DYNAMIC ANCHOR BOXES ARE BETTER QUERIES FOR DETR翻译
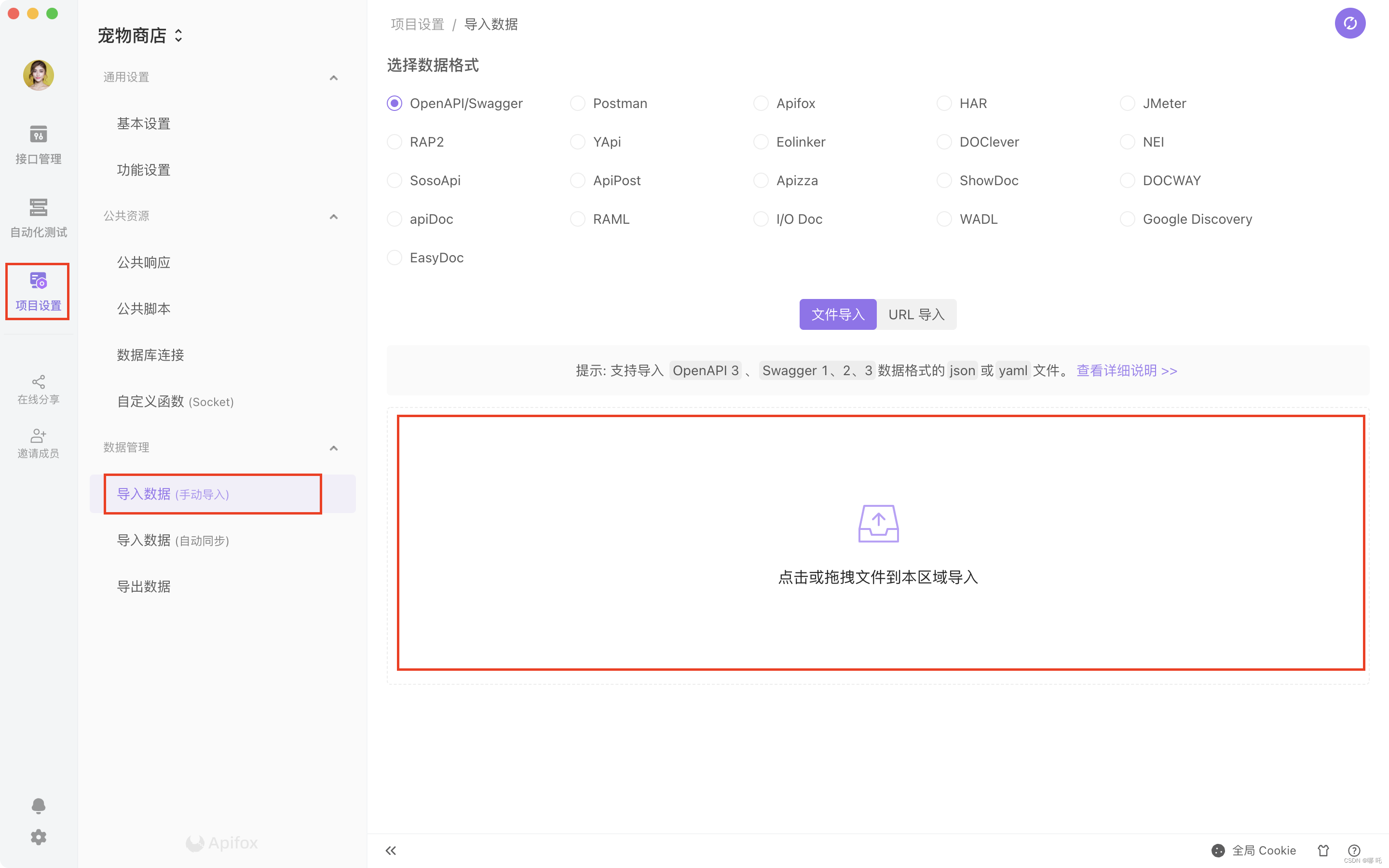
超越Postman,新一代国产调试工具Apifox,用起来够优雅
Kivy tutorial of setting the size and background of the form (tutorial includes source code)
随机推荐
Continuous learning of Robotics (Automation) - 2022-
buildroot的根文件系统提示“depmod:applt not found”
The root file system of buildreoot prompts "depmod:applt not found"
EasyCVR集群重启导致其他服务器设备通道状态离线情况的优化
[untitled]
JS form get form & get form elements
2022 electrician cup a question high proportion wind power system energy storage operation and configuration analysis ideas
Complimentary tickets quick grab | industry bigwigs talk about the quality and efficiency of software qecon conference is coming
Hangzhou Electric 3711 binary number
kivy教程之设置窗体大小和背景(教程含源码)
Digital chemical plant management system based on Virtual Simulation Technology
Golang calculates constellations and signs based on birthdays
SSM+JSP实现企业管理系统(OA管理系统源码+数据库+文档+PPT)
On the 110th anniversary of Turing's birth, has the prediction of intelligent machine come true?
Surpassing postman, the new generation of domestic debugging tool apifox is elegant enough to use
EasyCVR集群版本添加RTSP设备提示服务器ID错误,该如何解决?
硬件开发笔记(十): 硬件开发基本流程,制作一个USB转RS232的模块(九):创建CH340G/MAX232封装库sop-16并关联原理图元器件
Fix the problem that the highlight effect of the main menu disappears when the easycvr Video Square is clicked and played
两个div在同一行,两个div不换行「建议收藏」
Use facet to record operation log