当前位置:网站首页>Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
Summary of Shanghai Jiaotong University postgraduate entrance examination module firewall technology
2022-07-04 11:13:00 【loveCC_ orange】
Since I opened this series last time , Simply introduce the mainstream technology of information security . The last blog talked about cryptography , Today, let's talk about firewall technology .
Firewall technology
Firewall technology is a combination of software or hardware equipment between two networks with different degrees of newcomers , In essence, it is a control isolation technology . It requires :
- All data flows in and out of the network should pass through it , And all data flows through it must pass the audit and authorization of security policies .
- Record information about connections and server traffic .
- Record any attempts of intruders , So that the administrator can detect and track .
The firewall itself is not a separate computer program or device , But a complete system that can provide security policies and their implementation .
Main functions of firewall
- Restrict people from entering from a specific point
- Prevent intruders from approaching other defense facilities
- Restrict people from leaving a characteristic point
The purpose of setting a firewall is to set up a unique channel between the internal network and the external network , Do not let those redundant unauthorized information from unprotected networks enter the private network , Users on the local network can still be allowed to access Internet, And it can simplify the security management of the network .
Classification of firewall technology
One 、 Technical classification
At present, the main technologies used by firewalls are Packet filtering 、 Application gateway and Agency service .
Packet filtering technology
Packet filtering is Earliest use A kind of firewall technology , It works in Network layer and transport layer , Take the data of these two layers as the monitoring object . Packet filtering and interception All flowing IP package , From its IP Packet header information 、 Get the relevant information required for filtering in the header of the transport layer protocol and the application layer protocol data .系统内设置有 Access control table Packet filtering firewall according to the control table Filtering rules , For each received and sent IP The package applies these rules , Then decide whether to send the packet or discard it . Firewalls are generally configured as Two way filtering , The filtering rule is based on the information contained in the network package , Such as source IP Address 、 Purpose IP Address ; Destination port number , Source port number ;IP Protocol stack and interface .
Defensible attack means : Can prevent a type of IP cheating , namely The external host disguises the internal host IP.
in application , Usually, packet filtering firewall is regarded as the first security line of the network !
advantage :- For a small 、 Less complex sites , Packet filtering is easier to implement .
- Because filtering Router works in IP Layer and the TCP layer , therefore Processing packets faster than proxy servers .
- Filter router provides users with a transparent service , Users do not need to change Any application on the client , There is no need for users to learn anything new .
- Filter Router in Price Generally, it is better than proxy server cheap .
shortcoming :
- Some packet filtering gateways do not support valid User authentication .
- The rule sheet will soon become large and complex , Rules are hard to test . As tables grow and complexity increases , The possibility of loopholes in the rule structure Sex will also increase .
- The biggest drawback of this firewall is that it relies on a single component to protect the system . If something goes wrong with this part , Will open the door to the Internet , And users may not even know .
- In general , If external users are allowed to access internal host , Then it can access any host on the intranet .
- Packet filtering Firewalls can only block one type of IP cheating , That is, the outside The host camouflages the internal host IP, Camouflage external host for external host IP Deception cannot stop , And it can't prevent DNS cheating .
Application gateway
Application gateway firewall in Network application layer complete Protocol filtering and forwarding function . It uses specified data filtering logic for specific network application protocols , And at the same time of filtering, the necessary registration of data packets 、 Statistics and analysis , Form log report . What packet filtering firewall and application gateway firewall have in common is that they only rely on specific logic to judge whether to allow packets to pass . Once the logic is satisfied , Computers inside and outside the firewall will Direct contact , Users outside the firewall may directly understand the structure and running state of the intranet . therefore , This method cannot effectively organize illegal access and attacks .
Defensible attack means : It can prevent some disallowed network services and infrequent applications from connecting with the internal network , Cause the leakage of sensitive information on the intranet .Agency service
Proxy service is introduced for the shortcomings of packet filtering firewall and application gateway firewall . It divides all network communication links across the firewall into two sections , Then use proxy server to realize the connection of application layer between computer systems inside and outside the firewall by software .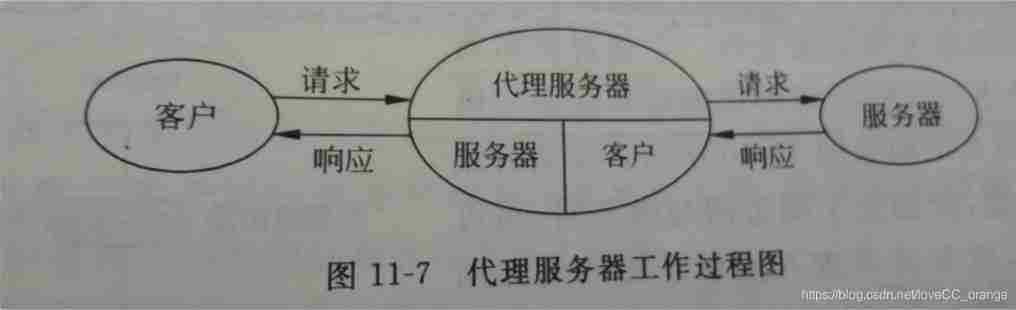
Inferior attack means : It can effectively prevent illegal access and attacks .
Generally, the ideal firewall does not rely on a technology , Instead, it combines packet filtering technology with proxy server technology , Realize both in network security 、 Performance and transparency complement each other . So as to obtain higher network security performance and system performance .
Two 、 Structure classification
From the application system The angle of structure , Firewalls can be divided into Dual host architecture 、 Shield host Architecture and Shield subnet Architecture .
- Dual host architecture
Dual host hosts have Two interfaces : An interface is connected to the internal network ; the other one Interface and external network connection . Direct communication between internal and external networks is not allowed , But you can use application layer proxy ( Run in the host proxy server ) The way to communicate . Dual host firewall has simple structure , Easy to implement . But also very fragile , Once invaded , The internal network opens the door to intruders .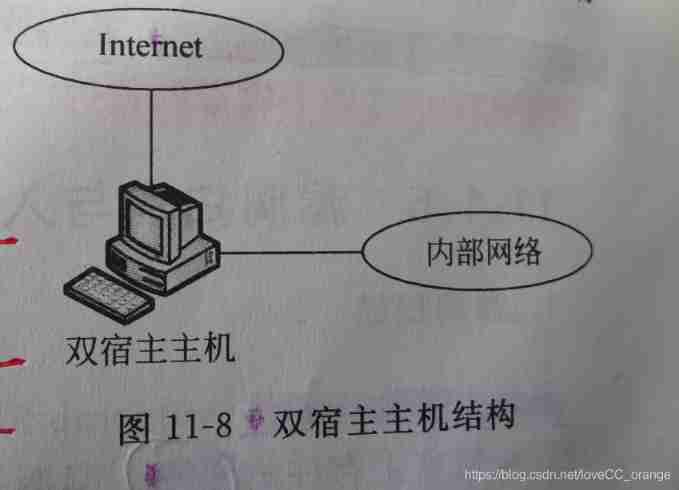
- Shield host Architecture
The shield host architecture uses a shield router and a fortress host to form a firewall . Fortress host is a kind of reinforced and defensible Attacking computers . The shielding router should ensure that all input information must be sent to the fortress host first , And only receive the output information from the fortress host . Other sites on the internal network can only access the fortress host . If the shielded router is penetrated , The whole network will be open to intruders .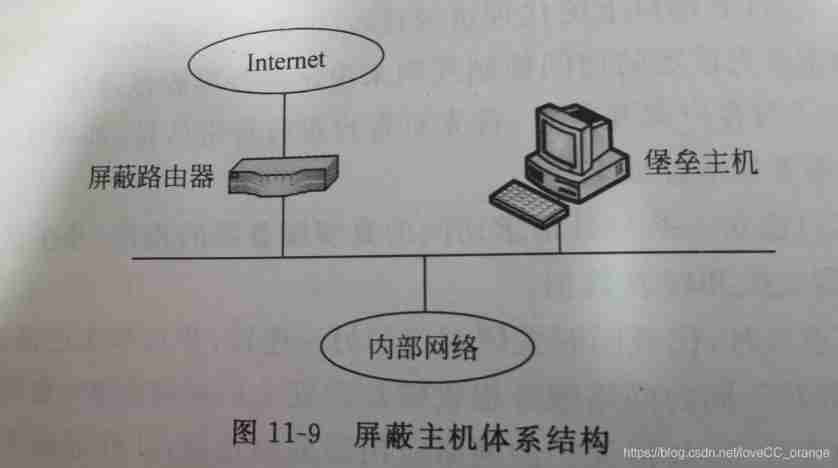
- Shield subnet Architecture
Shield subnet Architecture Add a peripheral network that separates the intranet from the Internet ( Also known as the demilitarized zone ,DMZ), So as to further enhance the security of the fortress host . it By using the surrounding network to isolate the fortress host, the attack of the external network on the fortress host can be weakened .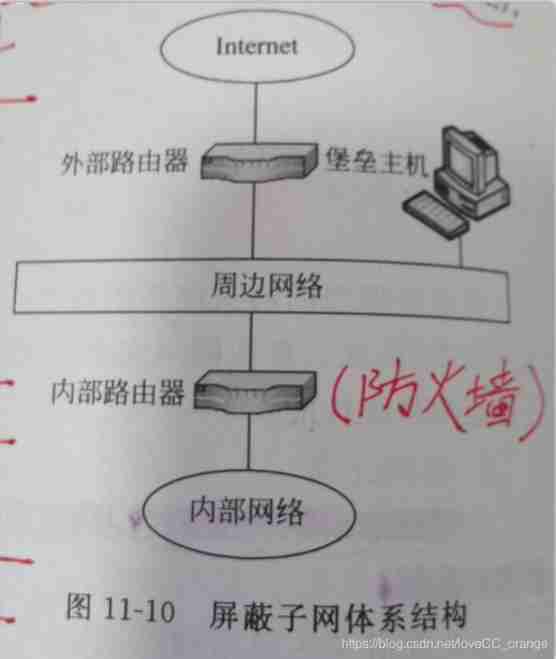
Demilitarized areas DMZ It is the network administrator who ensures the network security at the same time , A measure taken to maintain communication with the outside world .DMZ Is part of the company network , But it is placed outside the firewall , It is the entrance to the network . We usually put those who often need to communicate with the outside world Internet Connect , A server that provides external access , such as web The server ,E-mail Servers, etc. are placed in DMZ Area . This can ensure external access requirements , It can also avoid the security problems caused by the frequent access of the external network to the internal network .
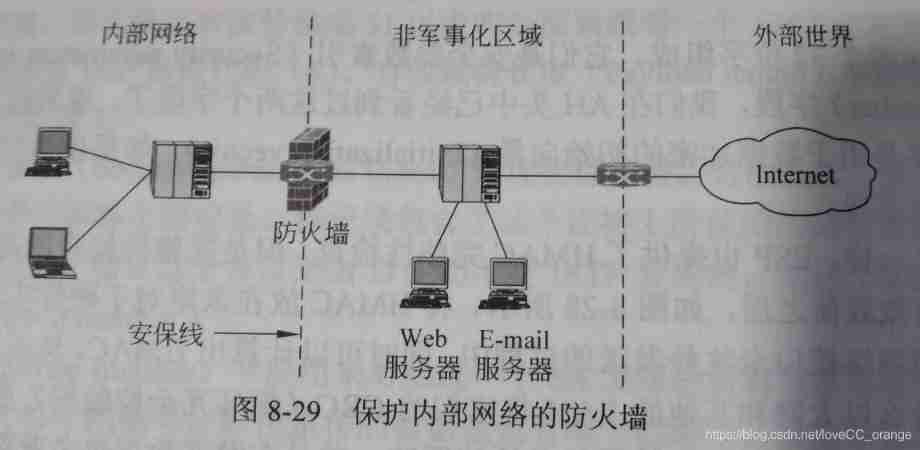
The advantages of firewall
- The firewall defines a containment point to prevent unauthorized users from being outside the protected network , Prevent services with potential security threats from entering or leaving the network , And provide various prevention IP Impersonation attack and routing attack . Using containment points simplifies security management , Because the security of single system or multi system is consolidated .
- The firewall provides a place to monitor security related events . The firewall system can perform audits and warnings .
- Firewall is a convenient platform that can be used for some Internet functions that are not related to security .
- Firewall can be used as IPsec platform .
The disadvantages of firewalls
- Firewalls cannot prevent attacks that bypass firewalls .
- Firewalls cannot completely prevent internal threats .
- A wireless LAN with improper security may be accessed from outside the system .
- laptop , Handheld computer (PDA), Or handheld storage devices may be used outside the network in use 、 infection , Then it is connected to the intranet and used in the intranet .
- Firewalls cannot prevent the transmission of software or files infected with viruses .
- Firewalls cannot prevent data-driven attacks .
Finally, one more small question : Draw a diagram and briefly describe the symmetric key distribution process using public key encryption
【 analysis 】
The topic means to distribute symmetric keys , In order to ensure the security of symmetric key , Therefore, the public key is used to encrypt the symmetric key , Prevent symmetric key disclosure . The distribution process is shown in the figure below :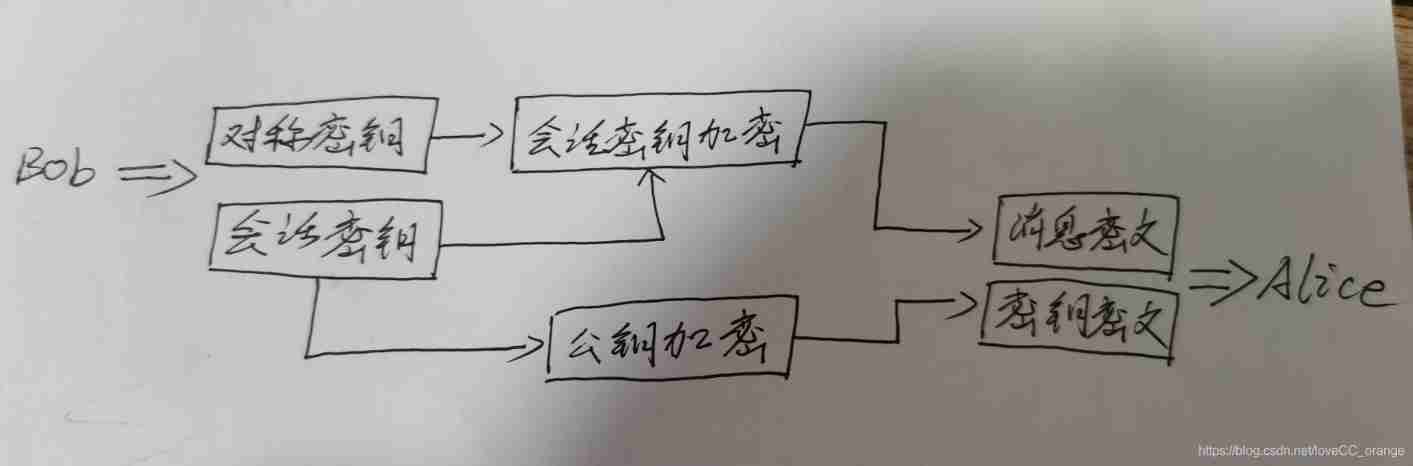
When Bob And Alice When communicating ,
- Prepare the news , That is, the symmetric key that needs to be transmitted
- Use the one-time traditional session key to encrypt the symmetric key to be transmitted
- utilize Alice The public key , Use the public key encryption method to encrypt the session key
- Attach the encrypted session key to the message , Send one piece to Alice
Welcome to WeChat official account. : Honey orange ! You can talk about electronic products and postgraduate entrance examination , Welcome to play with me !

边栏推荐
- QQ get group member operation time
- What if the book written is too popular? Author of "deep reinforcement learning" at Peking University: then open the download
- Unittest+airtest+beatiulreport combine the three to make a beautiful test report
- QQ group administrators
- OSI model notes
- Day06 list job
- Application of slice
- Basic function exercises
- Attributes and methods in math library
- I What is security testing
猜你喜欢
Take advantage of the world's sleeping gap to improve and surpass yourself -- get up early
VI text editor and user rights management, group management and time management
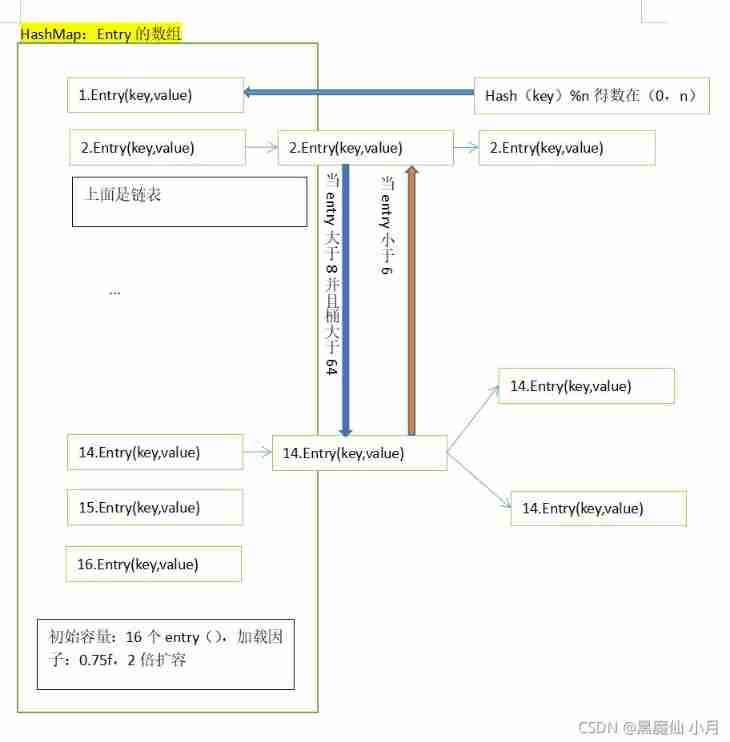
Summary of collection: (to be updated)
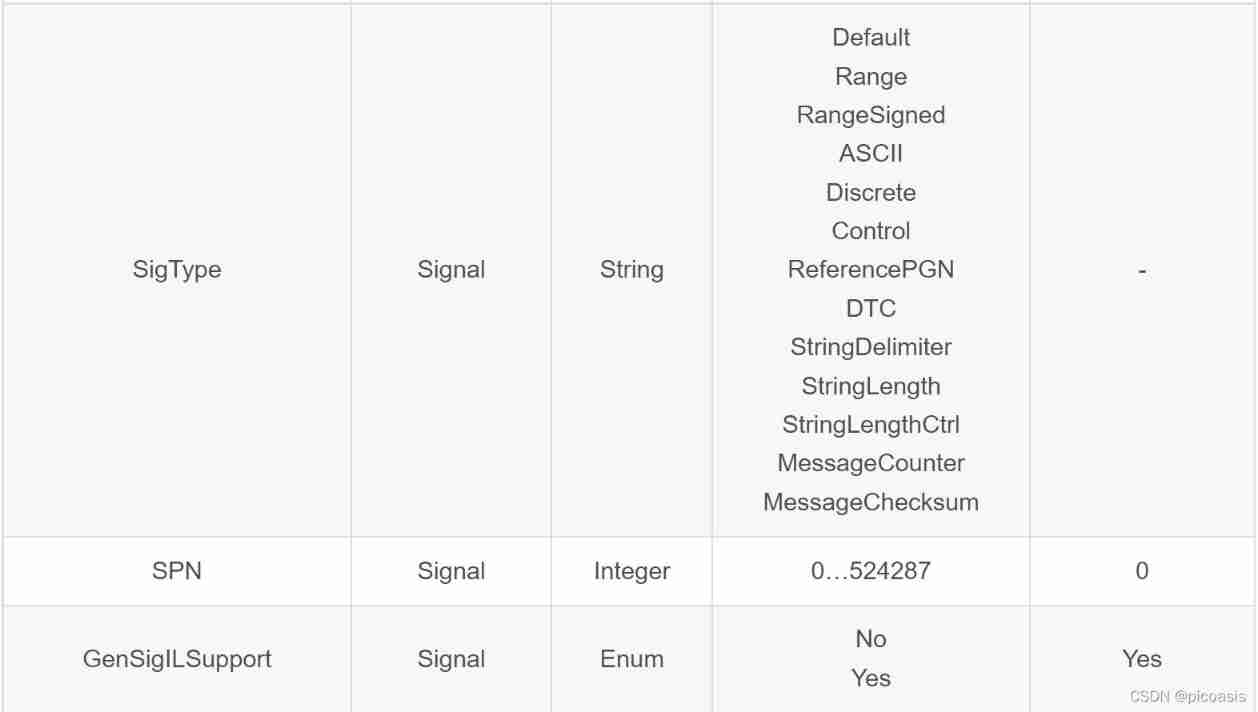
Canoe - description of common database attributes
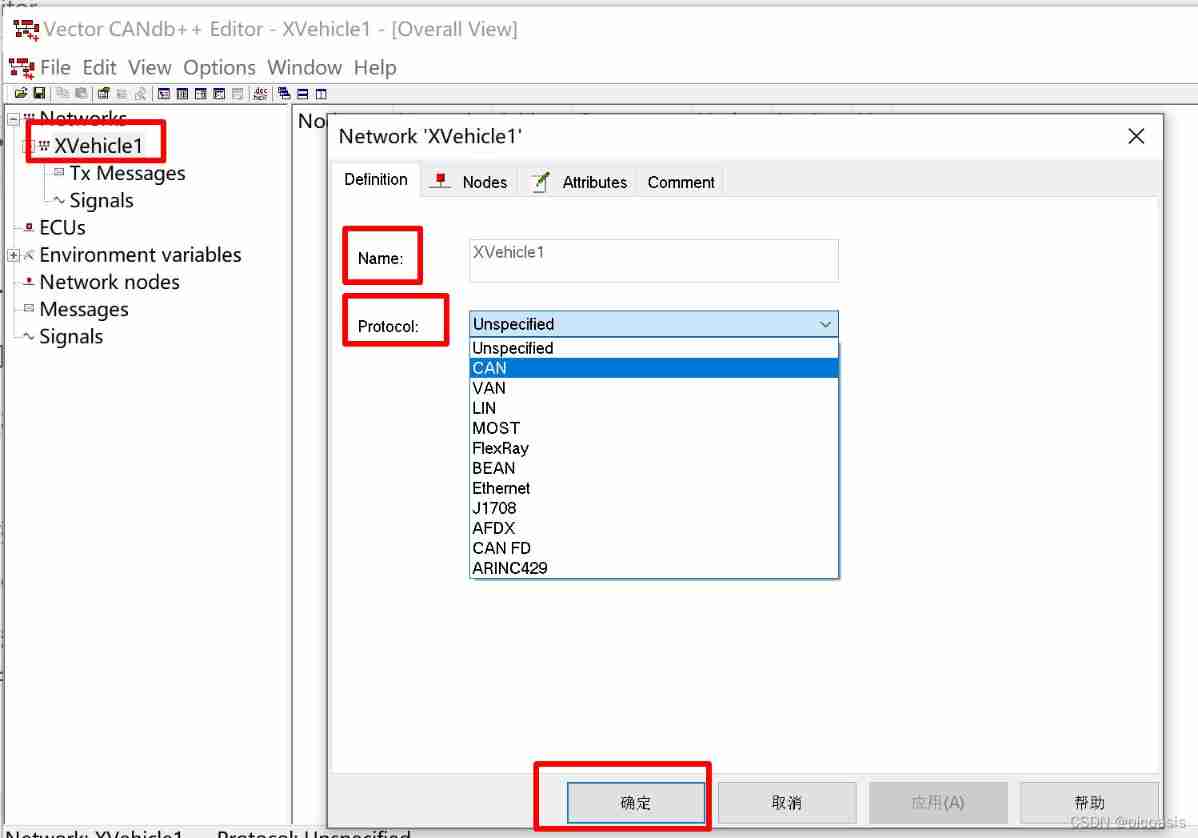
Canoe - the second simulation project -xvihicle1 bus database design (operation)
Installation of ES plug-in in Google browser
Personal thoughts on the development of game automation protocol testing tool
Performance test method
Canoe test: two ways to create CAPL test module
Canoe - the third simulation project - bus simulation - 3-1 project implementation
随机推荐
Heartbeat报错 attempted replay attack
[test theory] test phase analysis (unit, integration, system test)
Xiaobing · beauty appraisal
F12 clear the cookies of the corresponding web address
Getting started with window functions
JMeter common configuration components and parameterization
Polymorphic system summary
Installation of ES plug-in in Google browser
Application of slice
[test theory] test the dimension of professional ability
Exceptions and exception handling
thread
Summary of automated testing framework
Login operation (for user name and password)
Function introduction of canbedded component
No response after heartbeat startup
2022 AAAI fellow release! Yan Shuicheng, chief scientist of sail, and Feng Yan, Professor of Hong Kong University of science and technology, were selected
Test question bank management system - database design [easy to understand]
For and while loops
Canoe: the fourth simulation project -- bug debugging experience