当前位置:网站首页>I What is security testing
I What is security testing
2022-07-04 10:48:00 【weixin_ thirty-four million three hundred and twenty-two thousa】
1. What is security testing doing ?
scanning ? In the eyes of many people , What's safe is where the tool scans all day , Scanning with a variety of different tools .
Yes , Scanning is an important part of security testing , Scanning can quickly and effectively find problems . The ease of use of scanning tools , Convenience determines its important position . But the limitations of scanning tools , It is also obvious that the program is not flexible enough . Whether it's the analysis of the scan report 、 Deep mining of loopholes 、 The organization of testing and other work are inseparable from security testers , So it can only be said that the scanning tool reduces the workload of testers , It's a means of security testing
2. How do security testers position themselves ?
We often hear some names about security , Like software security 、 Information security 、 Network security 、 Computer security and so on , These areas are all about security , Which one do we belong to ?
【 software security 】 At a small scale, it's a software product , In addition to hardware, it's software .
【 Information security 】 Look at the name, we know that the key is information , But what is information , Customer data is all useful data ?
【 Network security 】 What is the Internet , Network system hardware 、 Software is a kind of vague concept
【 Computer security 】PC? The server ? Router ?
We can see that these concepts have become all kinds of devices that make up our Internet today, including all kinds of embedded machines 、 external USB、 Hardware and software of Bluetooth and other devices , And the use of 、 maintain 、 Managing these things, the whole security of people
Looking at the difference between them , They focus on different places , Or say something , They have no obvious boundaries, but they have their own priorities
What's our focus , What kind of product is our product ? We have web service 、 Interface services 、 File service 、 Video and other services , We call them our system , So we are doing the security test of this system , So I think we should position it as system security testing
Of course, our system also involves people 、 When it comes to hardware , This is not our focus , We only recognize it from the perspective of software technology . that , System security testing is different from functional testing , Like performance testing , Special tests listed separately
3. What is the essence of security ?
trust 、 The human nature ( The biggest loophole in network security is people )、 Stop loss 、 defense
These are some of the main arguments on the Internet today , Trust or distrust is the essential starting point of the mainstream
4. Concept definition
【 sensitive data 】 The specific scope depends on the specific application scenarios of the product , The product should be analyzed and judged according to the risk
Typical sensitive data includes passwords 、 Bank Account 、 Mass personal data 、 User communication content and key, etc
【 Personal data 】 It refers to directly passing the data or combining the data with other information , Information that identifies a natural person
【 Anonymity 】 Changes to personal data ( Separate one-way hashing 、 Truncation 、 Replacement, etc , To preserve the correspondence between the true value and the replacement value of personal data , Symmetric encryption or mapping table can be used , But the key / The mapping table must be controlled by all the data ), So that the original personal information can no longer be attributed to an identifiable natural person , Or it costs too much to reason 、 It's a disproportionate time 、 Cost and energy
边栏推荐
猜你喜欢
XMIND installation
Evolution from monomer architecture to microservice architecture
The most detailed teaching -- realize win10 multi-user remote login to intranet machine at the same time -- win10+frp+rdpwrap+ Alibaba cloud server
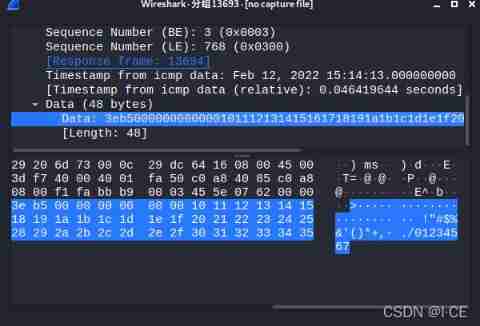
Hidden C2 tunnel -- use of icmpsh of ICMP

The bamboo shadow sweeps the steps, the dust does not move, and the moon passes through the marsh without trace -- in-depth understanding of the pointer
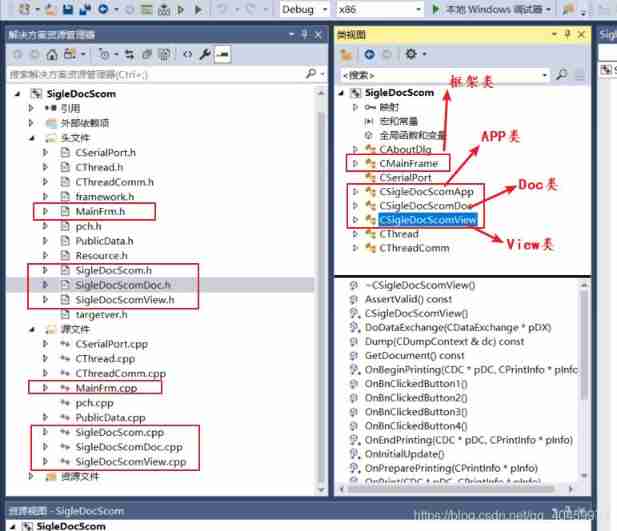
MFC document view framework (relationship between classes)
![[Galaxy Kirin V10] [server] NFS setup](/img/ed/bd7f1a1e4924a615cb143a680a2ac7.jpg)
[Galaxy Kirin V10] [server] NFS setup
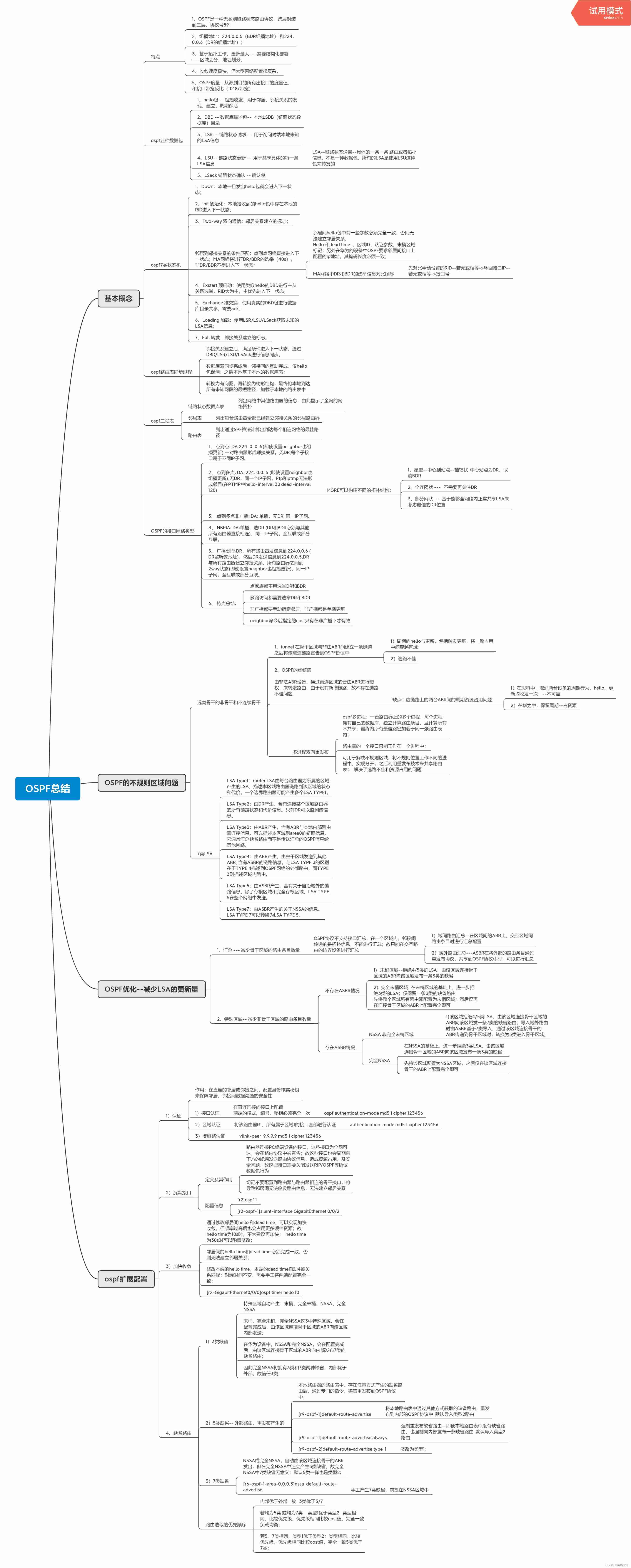
OSPF summary
20 minutes to learn what XML is_ XML learning notes_ What is an XML file_ Basic grammatical rules_ How to parse
Si vous ne connaissez pas ces quatre modes de mise en cache, vous osez dire que vous connaissez la mise en cache?
随机推荐
Discussion | has large AI become autonomous? Lecun, chief scientist of openai
DML statement of MySQL Foundation
Student achievement management system (C language)
[testing theory] thinking about testing profession
Realsense of d435i, d435, d415, t265_ Matching and installation of viewer environment
Write a program to define an array with 10 int elements, and take its position in the array as the initial value of each element.
How do microservices aggregate API documents? This wave of show~
Aike AI frontier promotion (2.14)
Advanced order of function
RHCE - day one
Recursion and divide and conquer strategy
OSPF comprehensive experiment
[Galaxy Kirin V10] [server] NUMA Technology
Remove linked list elements
IPv6 comprehensive experiment
Latex insert picture, insert formula
Jianzhi offer 04 (implemented in C language)
Basic function exercises
183 sets of free resume templates to help everyone find a good job
2020-03-28